Chrome 56: HTTP sites marked as not secure

Google announced plans today to increase the pressure on sites not yet offering their content over secure https connections.
Starting with Chrome 56 Stable, out January 2017, the company plans to list some HTTP sites as not secure in the browser.
Chrome uses a neutral listing for non HTTPs sites currently. All sites, HTTP and HTTPS sites with mixed content, fall into that category.
Starting with Chrome 56, some of those sites may be listed as not secure in the browser instead.
Any non-HTTPS page -- and mixed content pages fall into that category -- with a password field or credit card form fields will be marked as not secure in Chrome 56.
Google's plans don't end there though. The company plans to extend the warning to all non-HTTPS sites in the browser's Incognito Mode, and later on to all non-HTTPS sites displayed in the browser.
The indicator's color remains gray for the time being during that transition phase.

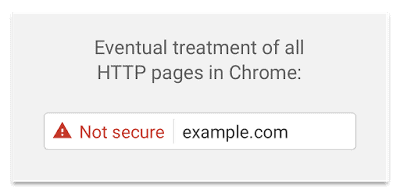
In the end, all HTTP pages are shown as not secure with a red exclamation mark and text in the browser's address bar.
Some sites or pages benefit more from others. While it makes sense to enforce HTTPS usage on financial sites and sites that deal with personal information, others may not benefit from it nearly as much.
There are valid arguments against enforcing HTTPS on all Internet sites. They range from increased handshake times to making it harder for users to publish sites on the Internet. Previously, all you had to do was create a HTML page and publish it. With HTTPS being enforced, you need to find a way to get a certificate for your site.
This has gotten easier and cheaper thankfully thanks to Lets Encrypt. It still means that you have to understand how to generate a certificate for your site and spend time understanding the process.
It seems a given that the web is moving towards HTTPS, and that HTTP or mixed content HTTPS sites will have an outlaw status one day.
You are probably wondering what we have planned in regards to HTTPS. I'm testing the implementation on two test URLs and the backend currently. Getting mixed content warnings because of the newsletter form currently but that seems to be the only issue right now.
You can check out one of the test pages here. Note that it shows up fine right now, but that is because the newsletter sign-up won't work on that page.
Now You: What's your take on marking non HTTPS sites as not secure?






















I am starting to hate chrome.
They do not show protocol anymore and they do not allow you to see certificate if it’s bad in their opinion.
Technical information is replaced with meaningless labels.
Ok, they put these labels as they believe in them but why cannot I see the bloody certificate if it’s “Not trusted”?
Would it hurt my mind?
Used to be right click on padlock, now I should run something like “echo |openssl s_client -prexit -showcerts -connect example.com:443 |sed -n ‘/BEGIN CERT/,/END CERT/p;’|openssl.exe x509 -noout -text ” just to see what’s wrong with cert.
I dont see the logic in google doing this.They already mark HTTPS sites as secure so common sense would dictate that if a site does not display as secure then it must be not secure lol.
What’s the cost(dollars) to a small website owner?
Well you can get a free certificate at Lets Encrypt, but you will spend quite some time making changes to your site, and making sure everything works fine.
About darn time somebody did something about the current state of the Internet. I was shocked in 2010 when I learned the huge prevalence of http over https, even on webpages that were *supposed* to be secure (logins, etc.) My shock has turned into despair and disgust, as even companies, let alone individuals, refuse to implement https on their websites.
My dream is that one day the entire web will be https, and no web browsers will allow a connection to an unsecured page (probably not gonna happen, but one can dream right?)
1. I’m sure no hosting provider, large and small, will want to be left behind, so nobody will be discriminated.
2. Widespread HTTPS adoption will also enable transition to HTTP/2 (only supported over TLS by browsers) so web performance will actually increase.
I’m sure hosting providers will support this. Some may offer it for free, others for an extra. But enforcing https limits the Web in other areas. I can publish a HTML page currently on my own computer and make it available. Once HTTPS is enforced, that page shows up as insecure unless I somehow manage to get a certificate for that self-hosted site.
I understand that self-hosting is often not suitable for offering permanent information or services, but if you just start out, this may be all you need.
I welcome this change coming to Google Chrome. I currently use WOT: Web of Trust, Website Reputation Ratings 3.0.6 as a Chrome Browser extension. WOT color codes all web sites from green (good) to red & orange (hazardous). This is very helpful when discriminating websites. I use the same browser extension in Firefox.
Firefox nightly show insecure if there is a login form.
Martin, the Let’s Encrypt folks launched Let’s Monitor a while back ;)
Do somebody share or have any suspicions in mind about what is really hiding behind good intentions?
Yes, https / ssl / tls all of these are supposed to be for good and for your protection (remember heart bleed?), BUT what if there is a catch? It can be used by mega corporations against you – all users!
If interested I’m able to give you many examples and facts.
For an example in all modern web browsers very …. very useful and DEFAULT and hidden mega popular feature is “safe web browsing”. Soooo, safe web browsing, reporting / blocking suspicious web sites – for that reason and for good intentions all is fully automated and that means whatever you type in address bar, whatever site, links you are visiting – everything is sent in real time to Google Servers to analyze http requests, carefully process, store data and identifying and profiling you and of course only with good intensions and your data and privacy all for charity in other hands relying on just someone good will – you are secure, you are safe and your private data is stored in secured place.
So you have a clues what is really hiding behind good intentions and aggressive Google like corps practice and actions.
Dear user, You must trust in mega and giga corps and think that you are safe, but you are not safe and you have been tricked again and again.
Wow, the web will become a slower web if encryption is enabled on every site. Why do I need https on a sport news site?
Because that way they can track you with a fingerprint instead of being more anonymous. (IP, persistent storage etc. aside)
HTTPS being slow is a debunked myth.
https://istlsfastyet.com/
Ha, i forgot to say, don’t forget to disable your antivirus (like for example ESET NOD 32 v9) scanning https connexions by default, which is real bad idea TOO.
In future if you don’t want to be scared unnecessarily by devils’ companies, use Pale Moon:
https://forum.palemoon.org/viewtopic.php?f=26&t=8913
Scared because they are putting an end to misinformation? Interesting.
>SSL
I’m sure the Pale Moon guy means HTTPS. No one wants SSL everywhere because it’s deprecated, flawed, and increasingly unsupported. TLS has already replaced SSL.
Obviously on the SSL part nit. Encryption will always be slower to process and should only be used when/where you need it and of course utilize more bandwidth for sure rather than clear text.
I have a small 3 page site, a hobby. No cookies, request for location, etc.. No information can be input by viewer, other then page selection. No classified information, or “adult” content. A “G” rated site. For me, this is overkill. It is putting a pad lock on a foot high fence. Unneeded.
Dick move by Google. I don’t need HTTPS for my personal webpages. The NSA will not do MITM attacks against visitors to my page to see pics of my desktop or anime. Google, you’re being evil again.
It’s not about the NSA or about protecting you, it’s about protecting the people who visit your site.
Although HTTPS prevents MITM traffic snooping, it’s more than that. If all websites were HTTPS, it would provide a way for people to know that the websites they were viewing (such as yours) were the actual websites they were supposed to be and also that intermediaries aren’t intercepting and modifying/injecting the pages that the end user is requesting. I don’t think most users would notice if the hotel, airport or McDonalds Wi-Fi they think they’re connected to was modifying the pages they were viewing. Without HTTPS the website owner and the end user would be completely oblivious to it. In addition, with the way the web is at the moment, it’s left to users to remember to check for a padlock, which is just plain idiocy.
I hope the owner of gHacks doesn’t mind me using this website as an mock example, but would you notice that the page in the below pic had been modified before it got to you if it wasn’t made so deliberately obvious? Would you notice that the URL in the address bar wasn’t pointing to the real IP address? That’s what this is about.
http://s17.postimg.io/pkngfn1j1/image.png
HTTPS is important for any website because traffic injecting can cause harm to other websites. See China’s attack on Github.
“And I’m saying this as an EFF supporter”
Towards the end of this post https://www.eff.org/deeplinks/2015/04/china-uses-unencrypted-websites-to-hijack-browsers-in-github-attack is this sentence: “Sysadmins can deploy HTTPS, making it harder for malicious agents to modify traffic in-transit.” If the Baidu analytics code had been encrypted it would have been harder. However, the EFF does admit that the Chinese government could force Baidu to facilitate the attack even so.
The lesson does apply outside of China though. Any non-HTTPS website can be “hacked”, not by modifying the website itself but by modifying the connection.
Also, Google is offering plenty of time to migrate. Maybe in the future, hosters will generate certificates automatically. This doesn’t help current sites though. I would not be surprised at all if Let’s Encrypt or an equivalent program develops a point-and-click way of upgrading to HTTPS.
Agreed. With HTTP, there is a theoretical chance that data is manipulated or recorded, and that is obviously bad. I don’t know how big of a chance that is, I suppose a higher probability in some regions than in others but overall it is probably pretty low.
I understand the thrust of the article, I even understand the motives that Google may have considered, but that is still overkill.
MITM is MITM. It is not just traffic snooping. It is also tampering en route, which is what the rest of your post is saying. And I still think it is overkill. I post my desktop screenshots. I post things about anime. My visitors (basically my wife and friends) won’t care if the traffic is being snooped by the NSA, nor are they important targets for tampering. Google is not my net nanny, nor should they be allowed to act like one. Stick to flagging malware sites and hacked websites. The bulk of the worldwide web will still function with HTTP and don’t need to be flagged as “DANGER INSECURE CONNECTION”.
And I’m saying this as an EFF supporter, a big Edward Snowden fan, and has taken network security and cryptography training. I understand the arguments quite well.
You’re completely missing the point. Currently, HTTP sites are marked as neutral, which is incorrect because they offer no security at all. This change fixes that by marking HTTP sites as not secure and getting rid of the “neutral” label.
Mozilla will do it too. And no, HTTP is never neutral, it is always insecure by definition.
HTTP has always been neutral. Not secure, not compromised. It’s silly and heavy handed for Google to flag plain HTTP as “OMG INSECURE SECURITY RISK!”.
I don’t have an all encompassing view on the topic, so I can only try and guess stuff.
Short term consequence: Because certificate authorities’ servers can’t handle the huge increase in OCSP load fast enough, browser will fallback way more often to less secure mechanisms more vulnerable to attacks.
Medium term consequence: More servers could implement OCSP must-staple, increasing security. Short-lived certificates may become the norm.
Forcing HTTPS on everyone everywhere is only really good if you also force OCSP must-staple at the same time, IMHO, *and* make short-lived certificate mandatory. Both measures instead of just one because when HTTPS is ubiquitous, everyone will be actively trying to find loopholes to abuse…
Sounds like a good idea. Basically all webpages being served over HTTPS to not only provide website authentication, but to prevent pages being modified/tampered with by third-party intermediaries before they reach the end user. And then reversing the way things currently are so that instead of people needing to look for the padlock symbol to make sure their connection is secure (which the majority of people never do anyway), it works the opposite way. Almost like whitelisting, with all connections being secure, unless you’re warned otherwise.
It’s long overdue IMO. SSL connections should really have been the standard right from the beginning of the World Wide Web and then we wouldn’t be faced with the problem rectifying it now, but I guess it’s easy to say that today where the TLS overhead is minimal with todays speeds and infrastructure. Even though the computational cost of HTTPS is already negligible to the average user with today’s hardware, as technology moves on and the web moves to HTTP/2, encryption will be even faster than conventional non-secure HTTP connections anyway (as demonstrated on the http://www.httpvshttps.com/ test site).
They need to move on to making end-to-end secure email the de facto standard next.
Than we will have more problems like this:
https://www.ghacks.net/2015/02/19/lenovo-pcs-ship-with-preinstalled-adware-and-root-certificate/
https://www.ghacks.net/2015/02/23/privdog-is-superfish-all-over-again/
https://www.ghacks.net/2015/11/25/give-your-windows-certificate-store-a-thorough-scan-for-suspicious-certs/
That’s not an argument against HTTPS. That’s an argument against the hijacking of it. Without HTTPS, malware wouldn’t even need to install the local decrypting proxy. It only does so because it can normally read only unencrypted traffic.
“and later on to all non-HTTPS sites displayed in the browser.”
When i read on http papers Laurel will be President, of course i need to be warned in red.
Probably another idea for Mozilla.
Horrified.
I’m against that since it will restraint the ability to share/publish information on the net, moreover it’s not done by some impartial organization but by a private one (Google).
It’s especially true for non tech savy people, I will have no real problem myself to generate a certificate but lot of users will be discriminated.
Now the question is: when is ghacks going to become https?
When it is ready ;)
@Tony, here are my NoScripts preferences.
http://www.mediafire.com/download/8jf2fu4q56m7a3j/noscript_prefs.txt
If the link is blocked, I can post the whole prefs list later.
@All Things Firefox
How does that work?
Currently, https://www.ghacks.net/ is configured to respond to requests with a 301: Moved Permanently (to https://www.ghacks.net/).
How does NoScript change this?
@Tony, yep. I use NoScript to do so.
I just discovered that feeds won’t serve over HTTPS though.
In Chrome, check Extensions after installing and click “Repair” if necessary. The blue S icon will now show as installed in the Chrome browser. Be aware HTTP Everywhere is currently a beta.
Thanks for the reference; I added HTTP Everywhere updated Version: 2016.9.1 Updated: September 1, 2016
Size: 1.71MiB to Chrome version 53.0.2785.101 m (64-bit). It’s also available for Firefox and Opera.
@All Things Firefox
Are you sure? Currently, for everything except test pages, https redirects back to http for gHacks.
I already force Ghacks be served over HTTPS with this method.
https://www.ghacks.net/2010/10/31/how-to-force-https-connections/