Microsoft pushes out emergency patch MS15-093 for critical Internet Explorer vulnerability
Microsoft published a new out of band security bulletin today that informs about a newly detected critical security vulnerability in the company's Internet Explorer web browser.
The vulnerability, which is already exploited in the wild according to the company, affects Internet Explorer 7 to 11 on client and server operating systems. Microsoft Edge, the default Windows 10 web browser, is not listed on the page and thus not affected by the vulnerability.
The vulnerability is rated critical for all client operating systems and moderate for all server operating systems of the company.
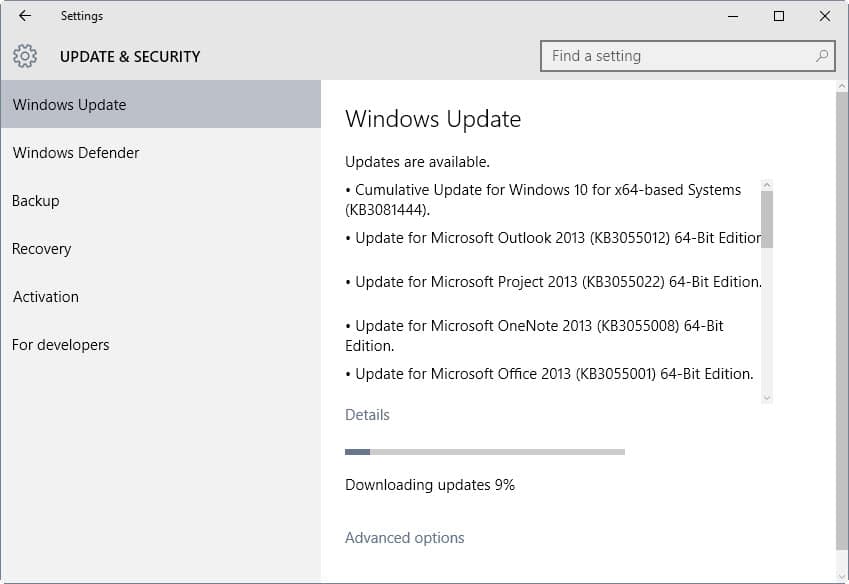
Microsoft released patches for all affected (and supported) versions of Windows. These patches are already available via Windows Update and via Microsoft's Download Center.
The update is listed as "cumulative update for Windows 10 (KB3081444)" for Windows 10 systems, and listed with the code KB3087985 on previous versions of Windows. The update KB3078071 is a prerequisite for that update on Windows 8.1 and 7, and Windows Server 2008 R2 and 2012 R2.
Attackers can exploit the vulnerability by through various means, for instance by creating web pages that exploit the vulnerability, HTML emails or web advertisement. All that is needed to trigger the vulnerability is that these contents get loaded in an affected version of Internet Explorer, an interaction with the site is not required apart from that.
Attackers gain the same rights as the current user on the system. If the logged in user has administrative rights, a complete takeover of the system is possible as it would allow the attacker to modify system settings, create or modify user accounts, install or remove software, and more.
Microsoft mentions two mitigating factors in the security advisory. A non-administrative user level of the logged in user may impact the effect on the system. In addition, Microsoft EMET, the company's Enhanced Mitigation Experience Toolkit, helps mitigate the attack according to Microsoft provided that it is configured correctly to work with the Internet Explorer web browser.
Download links for all supported operating systems are listed on the security bulletin page on the Microsoft website. To download the update manually, locate the installed version of Internet Explorer under affected software, and click on the link next to the operating system the computer us running on.
This is the second emergency patch released in the past couple of weeks. Microsoft released the bulletin MS15-078 in late July for all supported operating systems that addresses a critical vulnerability in Microsoft Font Driver.














I find it funny that Windows 10 still has IE, like it’s still important somehow. :P
Edge, from my experience, is a far superior browser. They should just dump IE (so they wouldn’t have to worry about constant updates and exploits) and stick with Edge.
Course IE, a lot of business use it for their systems, it’s kind of depressing.
Edge does not yet allow extensions. Norton anti-virus uses browser extensions. I trust Norton more than Microsoft’s “antivirus” provisions. Thus I will use IE at least until Edge is fully operational.
Seems like there is an emergency patch every week from Microsoft. They should declare an Emergency Monday$.
Help. I think my system may have been compromised. I think this may be it. I got a notice about unusual traffic on my windows 7 boot and blocked me from using the internet on it. I promptly uninstalled windows 7. I only kept it because my graphics card just got working windows 10 drivers.
Using windows 10. Facebook warned me someone was trying to login to my Facebook from Taiwan. I changed that pass. As well, all the passes I could think of. Wiped my entire system and updated. There’s no telling what they could have gotten as I do order things through amazon, and do freelance online through paypal. Luckily I disabled everything privacy related.
Is there anything more I should do?
Install a better virus/malware detector.
I stopped updating my Win7 system a couple of months b4 Win10 launch. Don’t really care how critical the update is as I don’t use IE as my main browser. I’m avoiding ALL Win7 updates until well past the FREE Win10 upgrade period as I don’t want them to sneak any updates onto my system that has anything to do with Win10!
1. you don’t have to use IE for the vulnerability to be used because a lot of programs use the IE engine for things.
2. Win10 upgrade is actually just one KB that you need not install, anything else would be related to Windows 7.
3. Your logic is seriously off the wall as you are making your system completely vulnerable to any new security holes that will go unpatched.
4. If you wait until after the free Win10, then it is no different if you installed durring the time, except that you are leaving yourself vulnerable for a year. Doesn’t make any sense. It’s not like they will force you to upgrade.
5. Anti-Win10 much?
Sigh… Example of not the case, I use winamp on my system. Winamp used the system browser for its web portion or to get band information. Therefore Winamp is vulnerable as well due to IE security flaws.
I also like how you ignored my other points. Are you just completely anti-trust microsoft, or are you completely tin-foil hat everyone is watching you and you live without a cellphone, no gmail/outlook/yahoo email account, and no social network whatsoever.
The thing is this day and age, you can’t just shun one company and not others unless you have a legitimate reason. It’s all about balance of privacy and capability.
False again. Any windows version is only as secured as you not using IE as the default browser. I’m not updating my Win7 system until 6 months well past the end of the FREE Win10 upgrade period b/c
1. They will pull the KB’s related to Win10 upgrade from their server
2. All the KB’s (like the ones that add telemetry to Win7/8) will be known in a comprehensive list published on a forum somewhere.
Makes my job easier manually selecting each individual Win7 KB to update then…
But what I don’t get is that your perfectly good windows 7 system will become vulnerable if you are avoiding ALL updates, and even if you wait until after Windows 10 Free Upgrade, then you will still be installing the updates that ‘add telemetry’ as you put it. I would at least understand if you read up and selectively installed the updates.
Mind you that Windows is used around the world at the enterprise and government level. If the company was “stealing your secrets”, or whatever you’re paranoid about, then they would be stealing everyone’s secrets, which would cause distrust of the company and the essential downfall of the microsoft corporation. If you’re THAT paranoid, then switch to a secure distribution of Linux, but then I would also hope you’re not using a smartphone, or even a cell phone at that matter because of the level of tracking implemented, and you don’t have an email account on any major service or have a social network account.
false. If you search the net, you see there are three KB’s required in order for the “Get WX (Windows 10)” thing to work in Win7.
also, I’m hearing they’re even sneaking in a KB that add telemetry to Windows 7 and 8 now. No way I’m letting them get their grubby hands on my perfectly good Win7 system updated to a few months pre Win10 launch!
What about if one doesn’t use IE at all. Does one still need to update as perhaps underlying Win programs use IE?.
Would be appreciated if someone could please explain this to me.
Thanks.
Wybo, yes you should update regardless of actual use of IE. While you may not use Internet Explorer, other system components may use its rendering engine to display web contents. I cannot really say if this vulnerability in particular affects third-party applications that use the rendering engine, but it is better to be safe than sorry in my opinion.
I did some basic research and just wanted this confirmed by an expert. So indeed I will let my devices digest IE updates.
Thanks so much Martin. It is appreciated.