Your installed browser extension may be used to fingerprint you
Extensions installed in web browsers may be used for tracking purposes. Some extensions use resources that are accessible by sites that are loaded in the browser; the information may be used to determine if extensions are installed, and even which extensions.
Fingerprinting describes a series of tracking techniques that Internet sites and apps may use to track users. The techniques use information, either provided automatically by the browser or the operating system, or manually, through the use of scripts. Unique fingerprints are the goal, as they allow sites to distinguish between visitors accurately. Most of the time, fingerprinting is used in combination with other tracking methods.
Browser extensions may use web accessible resources; not all do, but thousands use these resources. These resources, for instance images, may be accessed by websites that are loaded in the browser. The developer of the extension needs to declare web accessible resources explicitly in the manifest.
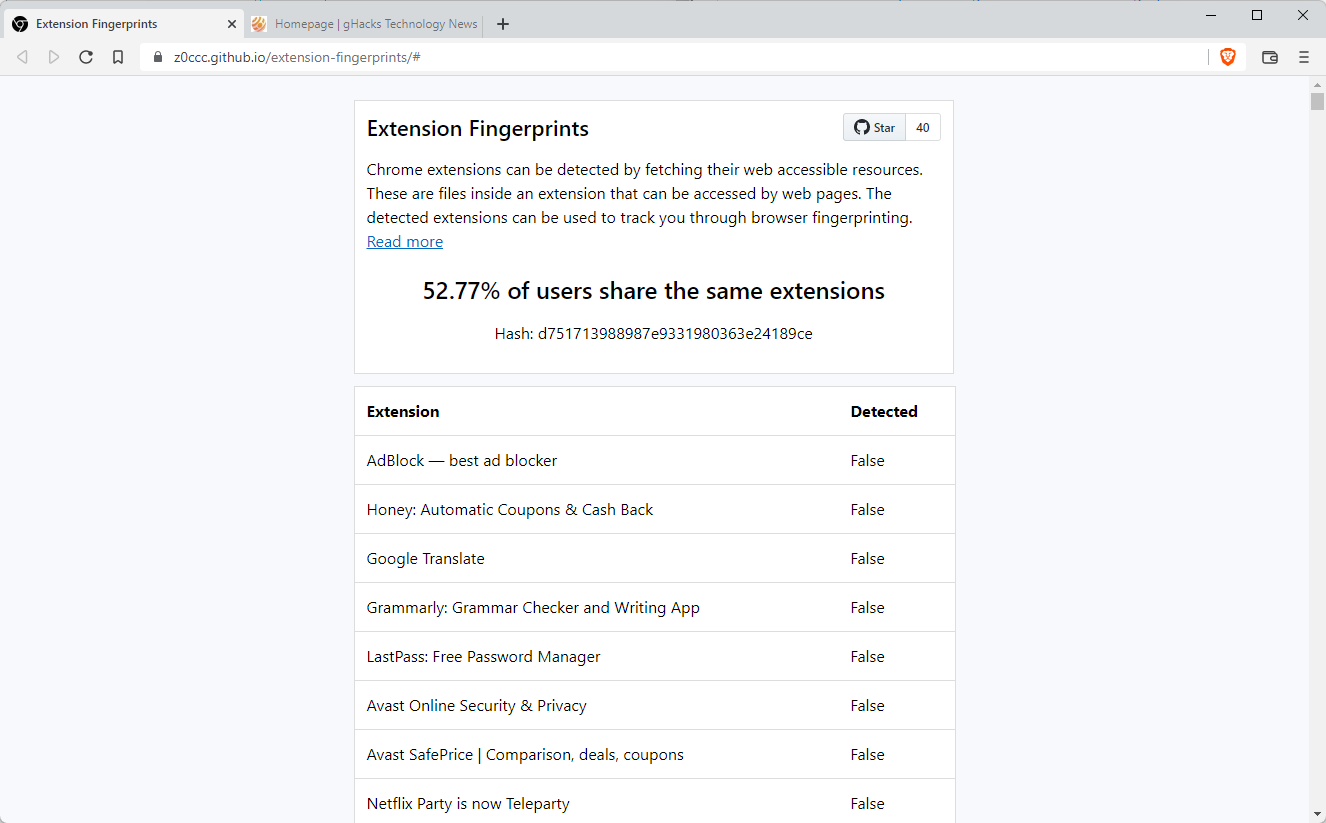
Extension Fingerprints is an open source script that checks whether these extensions are installed in the user's browser. The developer added scans for over 1000 extensions to the script, which are the most popular ones from a user installation point of view. Popular browser extensions such as Google Translate, Honey, Avast Online Security & Privacy, Malwarebytes Browser Guard, LastPass, Cisco Webex Extension, DuckDuckGo Privacy Essentials, or Amazon Assistant for Chrome use web accessible resources.
The list can be extended to add extensions with less than 70,000 users to the mix, which would improve detections and fingerprinting.
Point your web browser to this page to run the browser fingerprinting test. The script that runs on the page checks for the existence of web accessible resources and uses the information to return how unique the fingerprint is.
The browser's fingerprint is shared with the majority of users if none of the extensions that the script scans for is installed.
You may check the browser extension's manifest file to determine if it leaks web accessible resources. Either download the extension, extract it and check the manifest file this way, or use the Chrome Extension Source Viewer extension to view it in the browser.
Browser extensions have been used for tracking and fingerprinting in the past. In 2017, researchers created a technique that monitored the browser's response time to determine if extensions are installed. In the same year, researchers discovered an issue with Firefox's WebExtensions IDs.
Closing Words
Internet users have no viable options to protect their identity from this fingerprinting method. Uninstallation of extensions with web accessible resources or the blocking of JavaScript by default may not be viable options.
Now You: do you use browser extensions?



















We all need to go back to the BBS’S. We’d call them Internet Bulletin Board Systems. A lot of you may be too young to know what a BBS is. I ran two of them here in Nebraska’s capital city back in my 20’s and 30’s, just one line jobs. Nothing great but it had a file section, a message section, no chat. ad’s section and a few whistles and bells it was a great time and soon practically every one had one up and running and we were exchanging information left and right
You won’t need a browser, no fancy video adapter, or e-mail program just a dial up modem and the only way you could get a “virus” is if it was embedded in the message or file you received, which today’s scanners would find. So forget all this spy vs spy BS lets just make a simpler better system where no one spies on you cause they wouldn’t find any info anyway and all the advertising is in its special part of the IBBS’S and you want a better resolution picture of the one you were just sent…adjust your monitor
Sounds too good to be true doesn’t it?
This is funny, it cannot detect any extensions without javascript being enabled, and I disable it by default. And it cannot detect noscript, which is probably the most important extension you could possibly use on a chromium based browser.
I’d say this is a pretty good fingerprinting technique for use on the people who download lots of extensions and don’t flip on any of their privacy settings. It’s almost certainly completely worthless against wise privacy buffs.
JShelter does seem to be able to stop it with the default (recommended) settings for its JS shield :
Without: 2 listed; With: none listed
The best would be (and I hate to say it):
Use Chrome. Best without any add-on.
Before I get burned to death, here’s the reason:
If fingerprints concern you, you shouldn’t try to remove them, because you can’t. Simply not possible (currently). So you have to dive in the masses. Be invisible in the crowd of data. Each extension you install will make your browser more unique, because most users simply don’t use add-ons but the plain browser (Chrome) itself. Don’t personalize it, don’t change to a dark theme, don’t login to sync data, nothing. Do like the most do and this is the only option to gain privacy in this zone. As laughable it sounds as extreme and sad it is.
Using Brave, Safari, Firefox or simply any other Browser than the masses: I have to disappoint you. You’re more prone to fingerprints than anyone else, like me as Firefox-user. We are outstanding from the masses by not using the most used browser itself. We don’t even need (much) extension-fingerprinting to be “special”. And if we use some we’re such a small percentage that tracking down to a unique profile is really easy.
Claymore Tusk, iridium and librewolf are other alternatives. They might be more secure than those browsers you mentioned.
Sadly I’m getting to a point of apathy. Feel like Sisyphus trying to stave off this stuff.
These ‘checkers’ only give you a percentage of users based on the people that have used the site.
ie it’s already an extremely small percent of browser users. It will never become significant to bother with.
Waste of time.
Disable JavaScript and *poof* the tracking is (mostly) gone.
“Only Chromium desktop browsers are supported” -> ha!
IE. sites can potentially put up anti-adblock measures for detecting that you have an ad-blocker installed and force you to disable it to visit the site, with no way to mitigate it unless the browsers themselves patch the problem.
Wonderful. Soon we’ll have sites like Twitch denying access entirely if it detects you have ABP/uBO/etc… installed.
@Anonymous
https://filterlists.com/lists/fuck-fuckadblock
This bypasses many anti-adblock warnings. Hit “Subscribe” on the left side of the screen. Thank me later.
Did I do it right? I got false for everything on the list.
So, the title of this article should really be: Your Chrome browser extension may be used to fingerprint you. Firefox extensions reported to the world what you did last night, shame on you.
I don’t think it’s a very good test. It gave a false for UBlock Origin, which I have installed and running, on both Edge and Vivaldi. My Edge install is fairly rare though, about 0.013% of all browsers, and Vivaldi setup is also rare at the same 0.013%. The only extension on the list that I have is PrintEdit WE (well, other than the not detected UBlock Origin). Of course that could be do to another extension, as I use LocalCDN and ClearURLs on both installs (neither of which are on the list). And it could be due to the various security settings I have enabled.
Also, I loaded the page on my tablet and phone using Bromite. The results were interesting. On the tablet with Android 9, it’s like 57.9525% of all users. On the phone with Android 11, it’s like 58.199% of all users.
Want to partially correct my last post, in the case of ublock, that has web accessible resources protection, it’s using timing attacks to detect whether it’s installed, this method doesn’t seem to be reliable across different hardware as the author told me it works “every time” for him yet none of 3 different chromium based browsers i tested with ubo were detected.
In Vivaldi, at least, three lit up for me: uBO, Decentraleyes, and Bitwarden. I’m not concerned.
He took the most popular extensions (with more than 70.000 users) then made a list with the extension IDs of those with web accesible resources on its manifest.json and then just made a script that checked if those resources can be accessed, yet ubo is one of the few that uses a frequently randomized token to give access to its resources so without that token you can’t access its resources making this method ineffective.
Other extensions are not that good at hiding like ublock and can be detected not only on chrome but on firefox based browsers (albeit with a little different approach), so in resume for this to work the extension needs to have declared web accesible resources and not have any access control in place like uBlock has.
I dont use browser extensions willy nilly. The ones I use collect no data whatsoever, thx.
Also Ive noticed that my comments on this site even after 24hours seem to be caught in a endless totalitarianistic filter of censorship, both telling me Im posting too fast and removing my comments.
I get it the truth isn’t convenient and anonymity is just shunned here.
Where is Ironloser to come shill for Brave and insult Mozilla/Firefox?
Glad to see that I am literally living in your head rent-free.
The fact is that I am not advocating for piling on one extension after another for this exact same reason, you would know this if you actually made use of your brain and read my comments.
Further, since you mention FF: If you think that Firefox is not affected by this and if you think its extensions can’t be detected, think again. The test website only doesn’t support Firefox yet, it’s 100% possible to detect extensions there.
“The test website only doesn’t support Firefox yet, it’s 100% possible to detect extensions there.”
Not true. Stop spreading information that is not supported by facts.
“Detecting extensions using web accessible resources is not possible on Firefox as Firefox extension ID’s are unique for every browser instance. Therefore the URL of the extension resources cannot be known by third parties.”
https://github.com/z0ccc/extension-fingerprints#firefox
[Editor: removed, be polite, and your comments will be published. Calling moderations censors is not polite.]
‘Tor (based on Firefox) recommends not to install extensions in order to preserve its common fingerprint. Do you think the Tor devs are misinformed or stupid?’
Whatever your other views on other topic I don’t care. But this has to be addressed. Tor recommends against extensions not because all are bad. But some extensions aka Privacy Badger were found to be abused to make fingerprinting easier. And this is true for other extensions. Problem is not the installation of extensions but rather their workings which makes fingerprinting easier. So you have to decide whether benefits of using an extension are worth the fingerprinting risk? To eliminate this Tor doesn’t encourage to install and use extensions for normies. Simple. But if someone knows what they’re doing they can do whatever they want. Ublock Origin can’t be detected in Firefox, filter lists can. Same for Brave’s internal adblocker. So its up to user – either use Tor in its default config or install an adblocker, don’t change its default config too much and enjoy the clean web, albeit dark one.
Some privacy conscious users(one Edward Snowden in particular) install adblocker even in Tor. Some even consider adblocker the most important tool in any browser.
* [Editor: removed, be polite, and your comments will be published]
lol BAT lost 45% of its value in one year
https://www.coinbase.com/price/basic-attention-token
@Anonymous
As did the rest of crypto = bear market.
Tell me you are not an investor withput telling me you are not an investor, lol.
*without
I am getting really tired about all this shame about privacy and about tweaking the OS to get this or to get that or to get everything at the same time. Imho each extension, each addon, each tweak you will apply is a gold nail in the coffin of general performance and stability. My sister has plain W10, plain FF, plain everything because she knows nothing about Windows and her computer is always good with zero problems. The less she looks the system the better the system works. On the opposite side I have W11 tweaked to the maximum with all the possible tricks, with some third party software to get W10 behaviour (taskbar, start menu, file explorer). I spend too time weekly to update those several third programs that I have found over the Internet and day after day I got a new problem, it’s a pain in the back, seriously. Valinet’s Explorer Patcher made my computer useless to work in this June cumulative update, a complete nightmare to solve the problem. So before the end of this month I will reinstall W11 in a complete clean installation, deleting everything including all useless W10 partitions that still remains from the factory settings. And I will use everything to just work, to just see a movie or to read newspapers. Ok, the only thing I will add is Ublock Origin. Nothing more. Thanks for the article! :]
5 years and counting, firefox leaks Unique IDs if you are using certain extensions, that are worse than exntension ids are they’re unique and don’t even reset on session https://bugzilla.mozilla.org/show_bug.cgi?id=1405971
Also daily reminder that web accessible resources are needed on extensions cause sh%t extensions api limitations that let you no other way to achieve certain functionality than having to have some resources exposed on the web scope.
And this goes for both, chromium and firefox based browsers (since 57+).
I remember a couple videos a made a few years ago of bugs that, afaik, still works and were caused by this limitations, letting you tampering a bit with extensions installed on the users browsers, even with ubo that it’s pretty well made and has mitigations for that, if someone is interested i can try find them i should have them stored somewhere.
Tor Browser’s devs even claimed uBlock, Adblock can be used to fingerprint user, tbf I think this is bullshit.
@G
Your adblock lists leak. Extension ID may leak as well and is, in Firefox’s and thus Tor’s case, unique.
Test the list leak here:
https://browserleaks.com/proxy
“Only Chromium desktop browsers are supported”
don’t waste my time
Do you actually believe FF is immune to this?
Yes it is.
https://github.com/z0ccc/extension-fingerprints#firefox
@Aluminium
You wish, but your wishes are not matched with reality:
https://www.cs.uic.edu/~skarami/files/carnus/carnus-ndss20.pdf
https://www.ndss-symposium.org/wp-content/uploads/2017/09/crossfire-analysis-firefox-extension-reuse-vulnerabilities.pdf
Soon, brother, soon we will be saved!
https://blog.mozilla.org/addons/2022/05/18/manifest-v3-in-firefox-recap-next-steps/
@Haakon
That‘s very interesting, provided that your browser doesn‘t ship a native adblocker, which Brave does…
Not one ‘true’. I have 50+ extensions running here on Firefox 101.0.1. Didn’t check all these extensions occurrences on the testing page but I noticed that at least uBlock Origin, Singlefile were labeled as ‘False’ … there must be an angel, a mysterious guardian, but I have to find out which one hides my extensions from the testing page …
EDIT : “Only Chromium desktop browsers are supported” … I tested blindly and omitted to read that information.
That doesn’t defeat the idea of a guardian angel, does it?
I had that to “The blindly thing” and I was also astounded about uBlock Origin.
The good news is that upcoming Manifest V3 will have two new features to mitigate this issue.
1. extensions will have to specify which hosts can access their web_accessible_resources (but they can still choose all hosts if it’s needed for the extension)
2. extensions will be able to enable “use_dynamic_url” option, which will change the resource URL for each session (so browser restart). Safari is already doing this mandatory for all their extensions.
“Only Chromium desktop browsers are supported”
goodbye
“Firefox
Detecting extensions using web accessible resources is not possible on Firefox as Firefox extension ID’s are unique for every browser instance. Therefore the URL of the extension resources cannot be known by third parties.”
Brave is also vulnerable to this as well, so I would guess this won’t be fixed unless the underlying chromium engine is fixed.
@Steve
> Detecting extensions using web accessible resources is not possible on Firefox as Firefox extension ID’s are unique for every browser instance.
That makes it worse, not better. Unique extension IDs, if leaked, can be enough to track you with accuracy. Non-unique extension IDs (Chromium), not so much.
> Brave is also vulnerable to this as well, so I would guess this won’t be fixed unless the underlying chromium engine is fixed.
Yes. You should not pile on extensions for no reason if you care about not being tracked. Firefox is not immune to this either, it’s just not supported by the test website yet.
@ IH
According to the author, yes it is.
“Detecting extensions using web accessible resources is not possible on Firefox as Firefox extension ID’s are unique for every browser instance. Therefore the URL of the extension resources cannot be known by third parties.”
https://github.com/z0ccc/extension-fingerprints#firefox
[Editor: removed, be polite, and your comments will be published. Calling moderations censors is not polite.]
* [Editor: removed, be polite, and your comments will be published]
Linkclump
SingleFile
Please advise safer alternatives for Chromium browsers.