How to detect the Windows Tarrask Malware that uses a bug to avoid detection
Microsoft published information about a new malware on its security website on April 12, 2022. The malware, named Tarrask, exploits a bug in Windows' task scheduling system to evade detection.

Tarrask is used by the hacking group Hafnium, which targeted telecommunication, Internet Service Providers and the data services sector in the past.
The group uses zero-day vulnerabilities for its attacks to get into computer systems. Once a system has been attacked successfully, a bug in Windows is used to hide traces of the malware and make detection harder. Tarrask uses the bug to create scheduled tasks that are hidden to avoid detection and likely also for persistency.
The Windows Task Scheduler is used by the system and by applications to launch tasks, e.g., to check for updates or run maintenance operations. Applications may add tasks to the Task Scheduler, provided that they are executed with sufficient rights to do so. Malware uses tasks often, according to Microsoft, to "maintain persistence within a Windows environment".
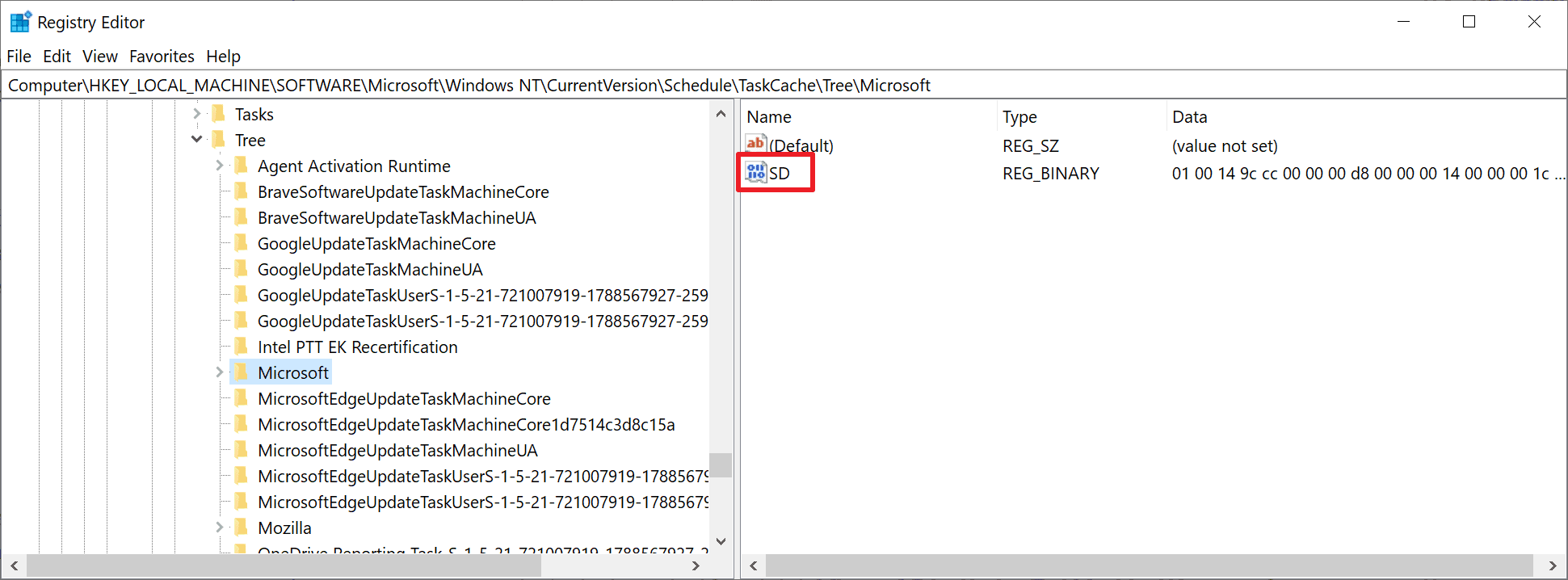
Tasks may be analyzed by launching the Task Scheduler tool on Windows. Tarrask uses a bug to hide its task from the tool and also the command line option "schtasks /query", which returns a list of scheduled tasks that exist. To avoid detection, Tarrask deletes the Security Descriptor value of the task in the Windows Registry; this results in the task's disappearance from the Task Scheduler and from the command line tool. In other words: careful inspection of all tasks using either of the tools won't reveal the malicious tasks.
Detecting Tarrask on Windows systems
The malware does not remove task information entirely, as traces of it are still recorded in the system Registry. Microsoft suspects that the hacking group left the data in the Registry to make the malware persistent, or, that the group was unaware that the task would "continue to run" after removal of the SD component.
Windows administrators may analyze the scheduled task information in the system Registry to find out if a system is infected with the Tarrask malware:
- Use the keyboard shortcut Windows-R to display the run box.
- Type regedit.exe and hit the Enter-key.
- Navigate to the path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\. You get the list of scheduled tasks that exist on the system.
- Go through each task to determine if one is listed without SD value.
If a task without SD value is found, it is a hidden task that is not displayed in the Task Scheduler or the command line utility. The task can't be deleted normally, as it is running within the context of the SYSTEM user. Attempts to delete the task will fail with an access denied error message.
The last version of Microsoft's Windows Defender security application detects the malware. Microsoft added a new observation event to Windows Defender that detects hidden tasks; these are flagged as Behavior:Win32/ScheduledTaskHide.A then by the application.
Microsoft recommends that system administrators adopt the following recommendations and security guidelines to detect malware that is using the attack vector:
Enumerate your Windows environment registry hives looking in the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree registry hive and identify any scheduled tasks without SD (security descriptor) Value within the Task Key. Perform analysis on these tasks as needed.
Modify your audit policy to identify Scheduled Tasks actions by enabling logging “TaskOperational” within Microsoft-Windows-TaskScheduler/Operational. Apply the recommended Microsoft audit policy settings suitable to your environment.
Enable and centralize the following Task Scheduler logs. Even if the tasks are ‘hidden’, these logs track key events relating to them that could lead you to discovering a well-hidden persistence mechanism
Event ID 4698 within the Security.evtx log
Microsoft-Windows-TaskScheduler/Operational.evtx logThe threat actors in this campaign used hidden scheduled tasks to maintain access to critical assets exposed to the internet by regularly re-establishing outbound communications with C&C infrastructure. Remain vigilant and monitor uncommon behavior of your outbound communications by ensuring that monitoring and alerting for these connections from these critical Tier 0 and Tier 1 assets is in place.
Other malware may exploit the bug as well to avoid detection.
Now You: which security software do you use?



















At the indicated location I find two entries:
The first, under Name, has an “ab” icon in red letters and then “(Default)”; under Type, it says “REG_SZ”; and under Data, it says “(value not set)” … There is no mention of “SD”
The second has an icon in blue letters saying “0II” above and “II0” below, and then SD
Should I be concerned about the “(Default)” entry which has no “SD”?
@Martin,
I don’t understand this at all. None of the tasks on my Windows 8.1 system include the SD value in the registry at the location mentioned in the article.
Yet they all seem to be bona fide entries such as HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{0AD47C1C-75EE-47A2-8C5E-597743903B81} for example which performs the Windows update service according to the description.
Both a Malwarebytes Premium and an ESET (free) scan report the system as clean.
I just found this article and checked my registry, and I also don’t see a single SD entry on my W8.1 system. Must be a W9+1 and W9+2 exclusive value. Can’t tell if I’m infected or not. Defender is up2date and didn’t find anything, so… whatever I guess.
Tarrask malware uses scheduled tasks for defense evasion – Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/04/12/tarrask-malware-uses-scheduled-tasks-for-defense-evasion/
Yes, I understand that aspect, but not the part where the article states that tasks without the SD value are malicious.
As already mentioned earlier none of the registry tasks on my system contain that value. That would imply that they’re all malicious right?
Here’s a pix of one with the description “Nvidia crash reporter”: https://i.postimg.cc/FRbZGMPr/sd-value-missing.png
So are we saying that this task is malicious because the SD value is missing?
@TelV:
Same as you. I do not understand what is this article is talking about. I could not find any tasks with “SD”. I am on Windows 7 instead of 8.1 (your case.) Maybe is a Windows 10 thing? If somebody care to explain, because the Microsoft article in the link above your post has the same info.
Grandma can’t be expected to do all of this shit.
This is further proof that Windows is not ready for the desktop.
> Grandma can’t be expected to do all of this shit.
When everyone is born, they cannot speak, cannot walk, and are ignorant of everything.
They are acquired through learning, and “vigorous curiosity” and “trial and error” enhance skills (knowledge and experience).
If you give up from the beginning, you will never accomplish anything, even if it is possible.
If it is truly impossible, then unfortunately, a decision should be made to “break off relations (abandon)” the relationship.
By the way, the gHacks Tech News article gives end-users a rundown of how to inspect their systems.
By following this procedure, you can discover if your system has been compromised by the “Malware Tarrask”.
However, the latest “Windows Defender” will detect this malware and flag it as “Behavior:Win32/ScheduledTaskHide.A” and quarantine it.
In short, if you cannot inspect it yourself, let the “latest Windows Defender” do it for you.
Where on my Zorin OS can I check this?
This bug should be fixed and also MS should take some measures to avoid such these situations in the future. Thanks for the article. :]
Can Sysinternals Autoruns detect these hidden scheduled tasks?
> Can Sysinternals Autoruns detect these hidden scheduled tasks?
Good question. Backtracking a few versions to Win7… it doesn’t have the `SD` or value associated with it (or on any subkeys for that matter). Win10 denies regedit access to delete it… so that leaves programmatic removal which I’m not inclined to test out due to lack of time.
However Win7 with latest AutoRuns v14.09 lists 4 items only under scheduled tasks here and the Edge updater is missing from a search of `Everything` (MicrosoftEdgeUpdateTaskMachineCore, MicrosoftEdgeUpdateTaskMachineUA, and the like) but visible with `schtasks /query`… so I would make an educated guess that it does not… much like Task Scheduler (taskschd.msc) doesn’t show it either.
Since Microsoft took over AutoRuns it’s usefulness seems to have gotten less developed over the decades… but still a tool to check in tandem with all the rest.
Delete locked registry items (be very carefull, make a registry-backup):
https://www.novirusthanks.org/products/registry-deleteex/
Search with RegEdit, copy the adress of the registry-item into deleteex, and delete.
I repeat: Be very carefull, take care that you have a registry-backup.
Have MS fixed this bug or are they planning to do it?
Patch Tuesday patches are said to contain the fix.
Microsoft 365 Defender:
https://www.microsoft.com/security/blog/2022/04/12/tarrask-malware-uses-scheduled-tasks-for-defense-evasion/
I can’t find an article that says my AV contains a patch but the vendor normally react faster than Microsoft and anyone with a little PC experience would recognise the importance.
Not mentioned above, Malware doesn’t just appear on computers out of the ether. You need to do something that delivers it. Also, if you have a good firewall that restricts outwards traffic that does not have approval, you will need to allow it. For example, if Windows update has approval to access internet but suddenly asks for outward internet access, you need to think whether Windows updated components recently. You also need to think if a program that normally works without internet access suddenly starts asking. For example, the Windows calculator.
Are these branches due to Malware or to MS’s historic campaign to get me to update to Win10?
Neither have a DM entry nor do any of their sub-nodes:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\Setup\GWXTriggers
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\Setup\gwx
@Gavin B,
Your comment is not to the point, what version of Windows are you using?
By the way, “Windows NT” refers to Windows 10.
For example, earlier versions have different search locations.
You will not get proper advice from anyone unless you comment specifically so that a third party can understand.
Windows NT refers to all Windows NT versions and not just limited to Windows 10
> Are these branches due to Malware or to MS’s historic campaign to get me to update to Win10?
>> You will not get proper advice from anyone unless you comment specifically so that a third party can understand.
I think this is actually a valid question even if it is taken in parallel context from my perspective. My first thought on this article is why wouldn’t they just fix this bug instead of pawning it off on system admins?
Then I read the above gwx (get windows 10 registry voodoo) comment, a similar use case, with the predatory/forced migrations Microsoft (MS) has tried on everyone in the past/present/future. The question posed could be interpreted as it might be a feature that MS has wanted to keep quiet until they got caught.
In short while other systems aren’t perfect either I’m super glad I’ve dumped Windows (one of the closed micro ecosystems) many years ago. Unfortunately I do have to maintain some for others since most of these duties are ignored by MS themselves… MS isn’t doing what they are paid for… usually that means they shouldn’t be in the game imho.
Regardless thanks for the article and the additional viewpoints.
> why wouldn’t they just fix this bug instead of pawning it off on system admins?
> the predatory/forced migrations Microsoft (MS) has tried on everyone in the past/present/future. The question posed could be interpreted as it might be a feature that MS has wanted to keep quiet until they got caught.
> MS isn’t doing what they are paid for… usually that means they shouldn’t be in the game imho.
If there’s a problem with the status quo, then there is a need to address it.
Rather than complaining about whom (Microsoft) is to blame and how quickly it should be fixed, what needs to be done is to take immediate action.
If this can be done by the end-user, it would be more appropriate for the system administrator (end-user) to address this issue since the system configuration is unique.
In general, most malware infections are caused by the ignorance and indifference of end users. Shifting the blame to others without remorse will not make things better.
Instead of lamenting calamity, the end-users themselves need to learn from it, and lessons should be applied to future use cases.
https://www.ghacks.net/2022/04/12/microsoft-windows-security-updates-april-2022-overview/#comment-4519338
https://www.ghacks.net/2022/04/02/microsoft-update-catalog-downloads-are-now-using-https/#comment-4518804
https://www.ghacks.net/2022/04/01/opera-gx-video-pickup-and-gx-profiles/#comment-4518631
https://www.ghacks.net/2022/03/30/chrome-100-with-security-updates-released/#comment-4518493
https://www.ghacks.net/2022/03/27/microsoft-releases-emergency-security-update-for-edge/#comment-4518266
https://www.ghacks.net/2022/03/31/adduplex-windows-11s-usage-share-rise-slowed-down-to-a-crawl-in-march-2022/#comment-4518530
https://www.ghacks.net/2022/01/30/what-happens-to-all-the-windows-10-devices-that-are-incompatible-with-windows-11-in-2025/#comment-4514402
> If there’s a problem with the status quo, then there is a need to address it.
Agreed.
> Rather than complaining about whom (Microsoft) is to blame and how quickly it should be fixed,
Observations are never complaining especially when offering valid perspectives that you seem to have clearly missed due to perceived inexperience. Gavin may also have just blindly hit the first REPLY on this forum too… who knows for sure. Timing on approved REPLIES here can also be a factor.
> what needs to be done is to take immediate action.
Yesterday (or zero day as the nomenclature is sometimes called now)… yes rather than the 2nd Tuesday of each month. I just had an end user update a git-scm for a some CVE’s and he’s oblivious to what it meant… but I’m not going to go around to every end user I deal with and do it for them. It’s not my product nor my service. I don’t sell Windows nor is not Microsofts duty to fix these in a timely manner. We are in agreement there.
> If this can be done by the end-user, it would be more appropriate for the system administrator (end-user) to address this issue since the system configuration is unique.
Most private users outweigh commercial entities in numbers and not everyone is a sys admin. So this point is moot. I know of Windows users that wouldn’t have a clue nor would some of them care to know.
You may also want to examine the AutoRuns commenter below and what I replied. This is not complaining either. This is defacto testing from a seasoned Windows beta tester including all versions of Windows.
This also falls within Microsoft dumbing down management tools too much including the .msc’s. I’ve been in this industry way too long to rely completely on old data and also only new data… cumulative from day one is my experience… so the proof is in the pudding as the aphorism goes.
I inspected my system as soon as I received this article.
Thanks to the article, it was very helpful to understand how to inspect the system.
When I actually inspected it,
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree
there were so many task items (files) under the “Tree” that it took me about an hour to check if “SD” existed for all of them.
I was concerned about infringement, but found no anomalies.
I express my appreciation for the article and the clear explanation of such a “serious” cases.
> Now You: which security software do you use?
Tasks always on from system startup to shut-down:
VoodooShield
simplewall
Unchecky
Manual tasks at irregular intervals:
Start Emergency Kit Scanner
Malwarebytes
EmoCheck
https://www.ghacks.net/2022/04/02/microsoft-update-catalog-downloads-are-now-using-https/#comment-4518804
https://www.ghacks.net/2022/04/02/microsoft-update-catalog-downloads-are-now-using-https/#comment-4518855
https://www.ghacks.net/2022/04/11/symantec-says-that-hackers-distributed-a-modified-version-of-vlc-and-exploited-it-for-malware-attacks/#comment-4519247
https://www.ghacks.net/2022/04/12/microsoft-windows-security-updates-april-2022-overview/#comment-4519338
Hey, Yes Absolutely MS should take care of any of these issues and No MS should not be foisting any fixes onto the administrators and regular home computer users. Microsoft destroyed, destroyed the windows operating systems with Windows 10 and 11 especially and they should be held accountable to fix their crap, backdoored, vulnerable operating systems. Not everybody wants to be a geek IT head, all they want to do is be able to use their computers without having to worry about registries and hacks and malware and all the rest of the crap that comes with especially Windows 10 and Windows 11. MS knows for the average home computer user that MS and Apple are the only games in town that’s why they leave the consumers to fix up their mess.