Microsoft Update Catalog downloads are now using HTTPS
Microsoft's Update Catalog website is a popular destination for downloading Windows Updates from the company. While there are plenty of third-party options available, the Update Catalog website requires just a browser to download updates for Windows.

One problem that users could run into up until now was that they could not download updates anymore in their browsers, as Microsoft provided downloads via HTTP links only. Many browsers limit access to HTTP sites and resources. Some allow users to bypass access restrictions, others block access to HTTP resources outright.
Even Microsoft's own web browser Edge started to block downloads from the company's Update Catalog website recently because of the use of HTTP. Windows administrators and users had to use different web browsers or tools to download from Microsoft's official updates repository.
When you visit the Microsoft Update Catalog website now, you won't run into any resource access issues anymore as Microsoft switched downloads to HTTPS on its website. Files and resources served via HTTP may be manipulated as they are not encrypted. Windows Updates on the other hand are signed digitally and protected against these manipulations.
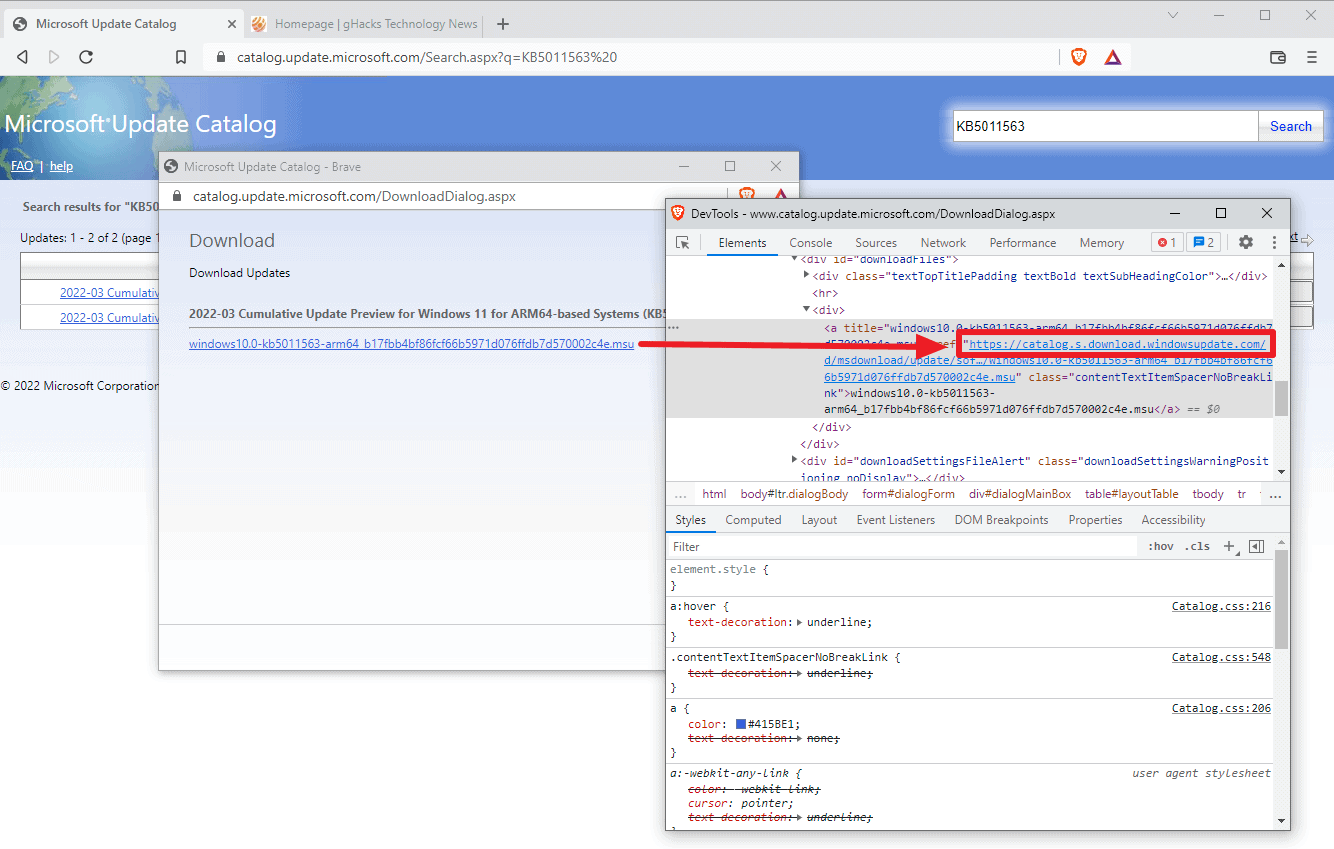
The company changed the link structure in the process as well, from download.windowsupdate.com to catalog.s.download.windowsupdate.com. Interested users may check the download links using the web browser's built in Developer Tools.
The main update page link structure remains, only the download links of individual updates changed using the new link structure. Direct links posted on the Internet should be redirected automatically, but if that is not the case, it requires just the editing of the first part of the link address to get it working again.
Example:
Old Link:
http://download.windowsupdate.com/d/msdownload/update/software/updt/2022/03/windows10.0-kb5011563-arm64_b17fbb4bf86fcf66b5971d076ffdb7d570002c4e.msu
New Link: https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/updt/2022/03/windows10.0-kb5011563-arm64_b17fbb4bf86fcf66b5971d076ffdb7d570002c4e.msu
Just replace http:// with https://catalog.s. and the download link should work again.
The change improves the accessibility of the Microsoft Update Catalog website as users should not run into secure connection warnings anymore when they try to download updates directly from the resource.
Now You: do you download updates manually from the Update Catalog? (via Deskmodder and Born)

















The vast majority of people don’t download from the website manually and use the built in WU service. This doesn’t affect most users.
Which browsers refuse to download files via HTTP? The msu link in the article works for me on Firefox and Chromium.
Anyways, I use Linux. The update manager works much better than the M$ crap.
“Therefore, I have been “blocking all telemetry and communications” related to Microsoft for some time now, and of course, updates must be done manually through the “Microsoft Update Catalog”.
Usually, these “update files” are huge, several hundred MB in size, and take tens of minutes to download.”
You think you’re blocking all telemetry and communications, yet you can not prove nor demonstrate all of what updates/patches from M$ do. It’s a proprietary OS.
It must be sad to have to use so many tools and methods to try and protect your black box OS from snitching on you.
@X
The answer, if you don’t want to use a proprietary OS that has no respect for user agency or user privacy, has always been the same: Linux
“Therefore, I have been “blocking all telemetry and communications” related to Microsoft for some time now, and of course, updates must be done manually through the “Microsoft Update Catalog”.
Usually, these “update files” are huge, several hundred MB in size, and take tens of minutes to download.”
You think you’re blocking all telemetry and communications, yet you can not prove nor demonstrate all of what updates/patches from M$ do. It’s a proprietary OS.
It must be sad to have to use so many tools and methods to try and protect your black box OS from snitching on you.
@X,
> You think you’re blocking all telemetry and communications, yet you can not prove nor demonstrate all of what updates/patches from M$ do. It’s a proprietary OS.
It must be sad to have to use so many tools and methods to try and protect your black box OS from snitching on you.
In general terms, you are right.
However, depending on business circumstances and required application software (CATIA V5-3DX, for example), I have no choice but to use Windows OS.
You don’t seem to know this, but a regular commenter on ghacks knows that “I am not using Windows in my digital detox”.
https://www.ghacks.net/2022/03/31/adduplex-windows-11s-usage-share-rise-slowed-down-to-a-crawl-in-march-2022/#comment-4518530
In short, my comment was simply an answer to “Now You: do you download updates manually from the Update Catalog?”
> Now You: do you download updates manually from the Update Catalog?
I was shocked by the “Snowden confession”, however remain suspicious that Microsoft is still “spying on end-user systems”.
Microsoft denies it, but in light of the reality of “GDPR” violations (94% of the time, they are violating it), we cannot trust what the parties say, unless it is proven by a legitimate audit by a third party.
Therefore, I have been “blocking all telemetry and communications” related to Microsoft for some time now, and of course, updates must be done manually through the “Microsoft Update Catalog”.
Usually, these “update files” are huge, several hundred MB in size, and take tens of minutes to download.
So I use a third-party downloader “Internet Download Manager”, It downloads very fast (from tens of seconds to a few minutes) and applies updates without frustration.
@owl
> I have been “blocking all telemetry and communications” related to Microsoft for some time now,
How do you do the above? Sorry I am new.
@Ashley,
> How do you do the above? Sorry I am new.
I use “Registry Editor” and “Windows PowerShell” to block the object I want to disable.
However, this method requires absolute skill (knowledge and experience) (make a mistake and your system will not boot) and is never recommended for the average user.
The following are recommended as alternative methods:
O&O ShutUp10++: easy to use for beginners > WPD > W10Privacy: for advanced users.
https://www.ghacks.net/2020/05/27/wpd-1-3-1532-adds-support-for-windows-10-may-2020-update-new-privacy-settings-and-some-minor-ui-changes/#comment-4464101
Instructions – W10Privacy
https://www.w10privacy.de/english-home/instructions-1/
In addition, the use of the firewalls “simplewall” and “VoodooShield” is recommended.
https://www.ghacks.net/2022/03/28/windows-defender-is-causing-videos-to-open-slowly-in-windows-11-beta-heres-how-to-fix-it/#comment-4518351
Using WPD and simplewall and locking the computer with VoodooShield is sufficient as a countermeasure.
By the way,
Do not neglect “vulnerability measures” for your system.
Updates to browsers and application software should be proactively applied.
If you have turned off automatic updates, disabled telemetry, etc., etc., you will need to apply updates manually.
I have been use “BelarcAdvisor” to constantly “audit” my system for vulnerabilities.
BelarcAdvisor will warn you (use that link to download from Microsoft’s Update Catalog) if it finds a “KB” that needs to be added to your system.
Belarc Advisor | Belarc, Inc.
https://www.belarc.com/products/belarc-advisor
Belarc Advisor features:
The Belarc Advisor builds a detailed profile of your installed software and hardware, network inventory, any missing Microsoft hotfixes, anti-virus status, security benchmarks, and displays the results in your Web browser.
All of your PC profile information is kept private on your PC and is not sent to any web server.
“PatchMyPC” also allows finding necessary updates to third-party application software installed on the system, silent-install them, and apply the updates.
Home Updater: Overview and Download | Patch My PC
https://patchmypc.com/home-updater
With “SUMo”, will know the status of even more updates, such as Portables.
As the Internet has become an indispensable environment for people around the world, the malicious intent targeting that environment (more than 300,000 new viruses and malware appear daily) has become more sophisticated and difficult to defend against and detect intrusions.
It has become clear that anti-virus software measures such as “filtering (pattern matching), behavior detection (heuristic), sandboxing, and virtualization” are no longer effective against unknown malicious intent and zero-day attacks, despite the excessive resource load they require.
The best perspective on security measures is the principle of “locking down external access while the computer is running a web application.
VoodooShield” is a program that “locks” a computer from outside access, and while the computer is running a web application (browser, email, etc.), all executable code (scripts, command line, .exe file execution) are all blocked, thus preventing the execution of malicious programs (e.g., viruses and malware).
VoodooShield” is only a computer “lock” function and cannot detect or remove viruses or malware.
VoodooSoft, LLC., the company that developed and supports DefenderUI and VoodooShield, is almost unknown outside of its home country of the United States, but has been identified as a legitimately licensed and patented company.
VoodooShield is patented by US Patent No. 9,197,656.
US9197656 – Computer program, method, and system for preventing execution of viruses and malware
Product Release Date: 2015-11-24
Product Concept
https://voodooshield.com/#pcmagquote
FAQ
https://voodooshield.com/#faq
Choose your browser carefully
https://www.unixsheikh.com/articles/choose-your-browser-carefully.html
A “portion” from the article is quoted below:
With all that said it is important to understand that the real problem lies with us – the Internet users. We seriously need to stop using the bad browsers and we need to either stop visiting all the bad websites or at least disable JavaScript on these websites! We need to educate ourselves and others better in the technology we’re using. This is much easier said than done, because website developers have gone crazy, but once you eliminate JavaScript from running in the browser you no longer need a complex browser like Firefox or Chromium and once you don’t need a complex browser you no longer have to worry as much about privacy issues – at least not from the browser point of view.
Split your browsing up in between a complex browser and a simple browser. Only use the complex browser when you really need it, and use the simple browser (perhaps a console based one) when you don’t require any JavaScript or other complex features.
As I said, I know that this is easier said than done, and I also know that companies will still collect as much data as possible about you (such as your IP address), but without a bad browser or JavaScript enabled the fingerprinting tactics becomes much more difficult to implement. I firmly believe that the power lies in the hands of the users and we need to make a choice every time we use technology. This is no different from boycotting harmful products because you care about yourself and your family health, or because you care about how animals are treated. We – the consumers – have the final say. When we boycott all the bad stuff, the producers have no choice but to stop the production because there are no more customers.
> “GDPR” violations (94% of the time, they are violating it),
https://karelkubicek.github.io/post/cookieblock
For supplement information:
https://www.ghacks.net/2022/04/01/opera-gx-video-pickup-and-gx-profiles/#comment-4518644
Comment section: –200 IQ once again
They didn‘t support HTTPS so far because some really old versions of Internet Explorer don‘t support HTTPS, but they still needed access to the updates.
The reason to run an old Windows with old IE? Compatibility with some applications in corporate space. Yes, really.
Both protocols are mutually inclusive, old clients can still access HTTP while newer ones use HTTPS. Is it that hard for small company to implement?
200 IQ indeed.
> Both protocols are mutually inclusive, old clients can still access HTTP while newer ones use HTTPS. Is it that hard for small company to implement?
???
HTTP was accessible by all browsers both old and new. Recently, browsers try to enforce HTTPS which may lead to some users not understanding why they fail to connect to the website, hence the HTTPS option now. The reason why they didn’t do this earlier are old versions of IE, and I guess they will retain an HTTP version of the website for quite some while because of them. HTTPS was plain unnecessary for MS before modern browsers started enforcing it more.
@Iron Heart
You can make a site accessible with both. Old clients can keep their HTTP url while newer use HTTPS URL, is it that hard to understand? You must not know about UAgent identification then? Before typing ??? try Googling first kid.
@Anonymous
My point was that they didn’t need HTTPS until recently, because only recently browsers started to enforce it more. There was no point in setting up HTTPS before.
I’d like to understand the logic of someone who continues to use IE11.
@ I’d like to understand the logic of someone who continues to use IE11.
Well let me tell you!
IE11 is perhaps the most amazing web browser due to it’s unique ability to render w… yeah I got nothing. lol
Websites can support both protocols. Microsoft was just being excessively lazy about it.
Fine, almost one hundred years later. I’m sorry, it’s a joke, as MS currently is now. :]
Cutting edge move
Wow. The Microsoft elephant has moved at last…
Absolutely breaking news! Finally, in 2022 :D
About damn time.
Was just about to post the same thing! :)