CCleaner 5.36 Emergency Updater
Piriform released a new version of the company's popular Windows cleaning software CCleaner to the public yesterday.
The new version ships with two major changes, namely a new Emergency Updater feature, and new default cleaning rules for some programs.
CCleaner 5.36 is available for download from the official company website, and also available as an in-program update for CCleaner Professional customers.
Free users can download the portable version from the builds page which comes without adware.
CCleaner 5.36: Emergency Updater

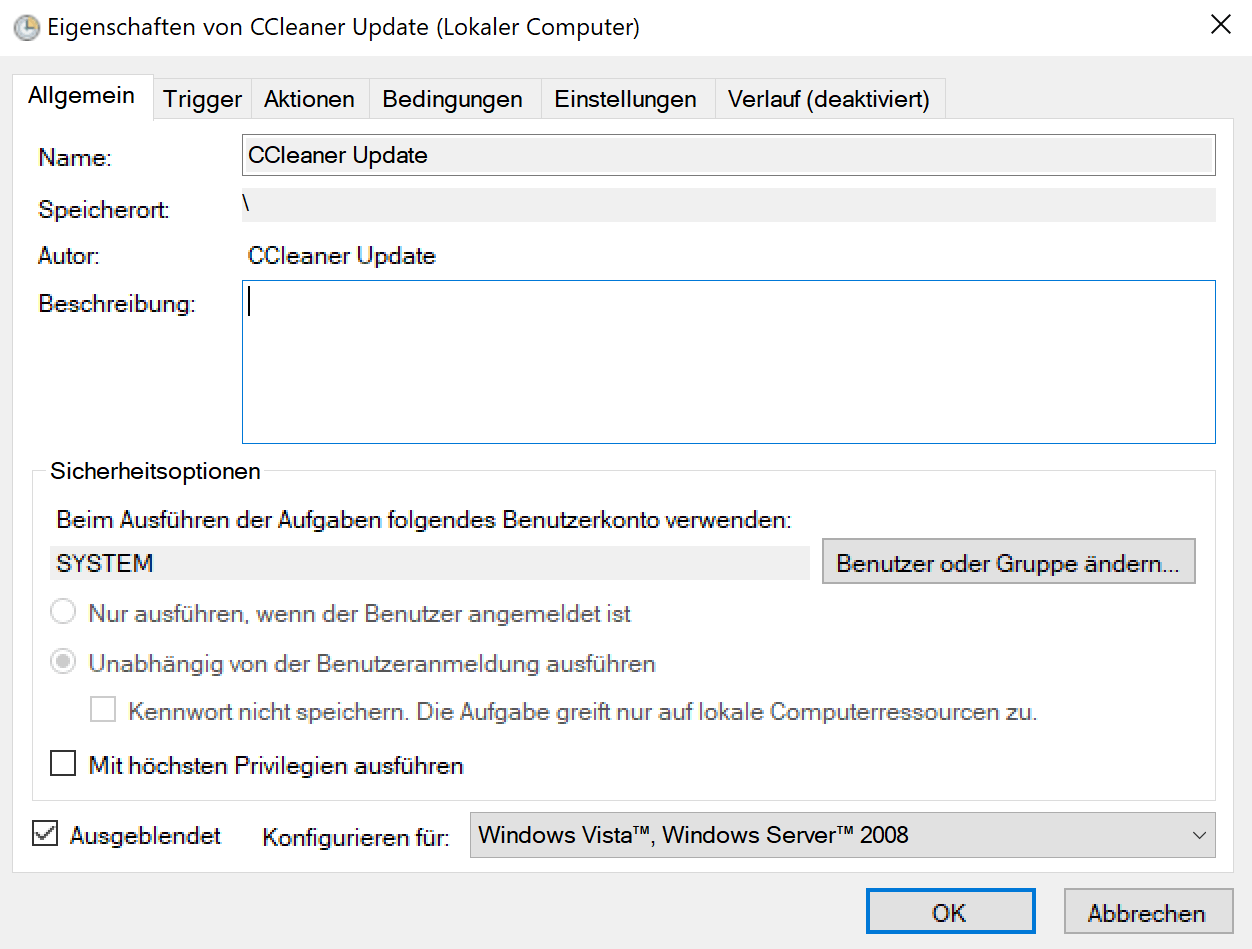
Emergency Updater is a new feature of CCleaner that comes with its own executable file -- CCUpdate.exe -- and a new scheduled task called CCleaner Updater.
The integration of the Emergency Updater component in CCleaner is likely a response to the recent hack of the company's infrastructure. Attackers managed to plant malicious code in CCleaner which was distributed for about a month from the official company website.
Piriform released a new version of the program with a new digital signature, but could not distribute it to free users due to a lack of automatic update functionality.
Piriform, which was acquired by Avast in 2017, probably used Avast's Emergency Updater as a blueprint for CCleaner's Emergency Updater functionality.
Avast released the feature back then as an alternative method to update the company's security programs if the default update function failed to do so.
The scheduled task is only added to the Windows machine if you install CCleaner. It is added for users of the free version as well however.
This means that Piriform may push out updates to the program to user machines even if only the free version of CCleaner is installed on these machines.
The task is set to run on system start, and once a day as well.
CCleaner default cleaning rules changes
The second major change of CCleaner 5.36 changes some of the program's default cleaning rules. Default rules are those that are set when you run the program for the first time.
Probably the biggest change in this regard is that CCleaner won't delete browsing session data anymore by default. Users of the program who did not pay attention to the cleaning rules have had their browsing session deleted when they ran CCleaner.
The change affects Firefox, Chrome, Edge, Opera, Safari and Thunderbird.
CCleaner 5.36 does not clean Windows Defender's scan history, the MRUs of Microsoft Office, and most recently used documents and other MRU files of Windows Explorer anymore.
Closing Words
Emergency Updater is a useful feature, provided that attackers won't exploit it successfully to push malicious code to user systems. CCleaner users who install the program on their Windows PCs may want to disable the task to avoid this from happening.























I’m running CCleaner 5.41 on Windows 7,
I’ve set Firewall outbound blocking rules for all CCleaner .EXEs and just discovered that nevertheless CCleaer 5.41 established a connection — not when simply run but when cleaning — to:
ipm-provider.ff.avast.com
If you search for privacy and dislike unnecessary connections, be sure to block above address.
I remain stunned that such a connection is possible when Firewall rules are in place.
I think retrospectively of the number of times this connection was established behind my back, equal to the number of times I cleaned the system with CCleaner.
That’s Avast…
I used to trust CCleaner when it was managed by Piriform but now I don’t feel safe anymore so there is a good alternative?
Question about ccleaner portable setup
Just downloaded ccleaner portable and set it up on a flash drive. I removed ccleaner 32bit since it will be used on a 64bit system, and only need english so language folder went aswell. From here (admin account) I dropped the ccleaner folder into
C:\Program Files then created a shortcut on desktop and renamed it just simply CCleaner, then just dragged it into the same folder many of the other start menu shortcuts are located (e.g. foxit reader, libreoffice. firefox etc).
This setup seems to work good in that logging into local accounts I found they also have the start menu entry. Everything is working just like the installed ccleaner did.
Now the big question is is about putting portable apps into C:\Program Files folder, is this a good idea or not? Seems to be pros and cons on this.
@A different Martin and Clairvaux
Thank you both for the all the input. On my old rig used to add a folder at C:\Apps for ccleaner, firefox and vlc but will try this setup for now.
@Clairvaux
Even 1 degree of extra protection is worth it to me especially when there is no extra effort needed. :D
In windows 10 start menu right clicking on an icon e.g firefox > Menu > “Open file location” opens
C:\ProgramData\Microsoft\Windows\Start Menu\Programs
so figured thats where I auta put ccleaner. And like you say this being a “system-wide folder” is why the local accounts picked it up.
@leanon
My question as well. My understanding is, the Program Files and Program Files (x86) folders, created by Windows, have special properties that provide a degree of protection against malware. If you try to change a file there from a non-admin account, you’ll need to clear a UAC warning first. This, I suppose, is provided by a specific set of NTFS permissions.
I have put all my portable programs in a C:\Portable folder. This puts them at the same level as Program Files and Program Files (x86) applications, and helps me differentiate quickly between portable and installed. However, after the fact, I realised that might have been a mistake, since by so doing, I don’t benefit from the protection afforded by the specific Windows locations. This could be mitigated, I suppose, by adjusting the NTFS permissions for the Portable folder, but this is outside my realm of competence.
If you put your portable programs in a sub-folder of Program Files or Program Files (x86), then there’s the added issue of : do you separate them in 32-bit and 64-bit categories, the way Microsoft does ? If you do, you end up with 4 sets of programs (installed/portable, 64/32-bit). If you don’t, I suppose you chose arbitrarily one of the Microsoft folders, and I suppose it won’t make a difference.
So I left them in C:\Portable.
Then there’s the irritating Start Menu issue. Windows 7 has several locations for the Start Menu : one system-wide, and one per user account. What you see in the Start Menu accessed through the bottom-left button is a merge of all those locations. This makes things difficult if, like me, you work from a non-admin account, and therefore have two accounts to yourself. Then, of course, you’d like to have the same Start Menu under both accounts, without needing to replicate everything by hand.
My solution is to put all program shortcuts in the system-wide folder, here :
D:\ProgramData\Microsoft\Windows\Start Menu\Programs
All my data is on D:\, but it works the same if you left them on C:\.
And I make sure that nothing is in Microsoft-mandated Start Menu folders, which are in locations such as those :
D:\Users\Clairvaux\AppData\Roaming\Microsoft\Windows\Start Menu\Programs
Unfortunately, there are shortcuts that can’t be elsewhere than the user-specific Start Menus, and they are those located in the Startup sub-folder, which will automatically launch at startup.
In order to manage more easily this steaming pile of Microsoft nonsense, I usually access the Start Menu folder through a favorite I have set up in Windows Explorer (and Directory Opus), and not through the Start Menu button. At least when I’m installing software. So I benefit from all the normal features of file handling, as opposed to the smart-alecky way Microsoft imposes on you when you’re using the Start button, because you’re supposed to be a stupid moron going around breaking up things.
I only use the Start button for launching programs. But even for that, my Start Menu favorite in Windows Explorer is often easier. For one, it does not keep closing when you need to launch several programs in a row.
I’m not remotely a Windows guru, but I put my “all-users” portable programs in a specially created C:\Program Files (portable) folder and “user-specific, user-customized” portable programs in a specially created C:\MyUserName\Program Files (portable) folder. That way they’re easy to find in Windows Explorer and (with just one parent folder per class of portable program) easy to add to SUMo’s list of additional folders to check for updates and easy to sync across computers. There are a few exceptions for programs that seem to stumble on long pathnames, like WSUS Offline Update, and I just put those in their own folder at the root, e.g., C:\WSUS. It’s possible I’m being a security bonehead in some way, but it’s worked pretty well for me so far.
Why install it? Use the portable version.
I agree Tony. I use the portable version and there are no scheduled tasks or emergency updates,
If users have good AV and anti malware software installed, they should have very few worries.
NB How many of the posters here were affected by the hack? Judging by the lack of reaction there were none; just some Avast and CCleaner bashing.
Obviously not many people read the Bleeping Computer Blog. I recommend that they do because it is a real eye opener !
“How many of the posters here were affected by the hack ?”
I was, presumably. I put the question to Cimpanu at Bleeping Computer, an he told me that the malware was on my computer, however it was inactive because my system is 64-bit.
I’m not sure what that means exactly, however I decided against reinstalling from scratch after all. I was not aware of anything untowards, although as I’m typing this I realise I did have a few programs losing their settings unexplicably — oh well.
Oh great, another program with it’s own standalone updater…
Frankly, I don’t care if this is possible to disable or not, the simple fact that it’s there bothers me. So glad that I stopped using CCleaner since my last clean install.
It was obvious that things would go downhill after the Avast purchase.
Thank you, Martin, for this very timely article. I had just resisted from upgrading, having seen that “emergency updater” thing on the version history. That flashed big red lights in this user’s den, and blocked all urges to upgrade. I was wondering what all that was about.
I understand the intention there, and indeed it’s a proof that Piriform lessons were learned, thanks to Avast and its more robust organisation.
However, automatic, forced upgrade also opens the possibility of all sorts of marketing tricks — of which Avast is fond (“You’re not protected anymore ! Buy our super-duper VPN you don’t really need ! Let your Outlook install be broken once again by our silly, impossible to uninstall anti-spam add-ons you don’t need at all, but we need you to use in order for us to train our anti-spam filters !”). I’m not saying this will be exploited to that effect, just that it makes me uneasy.
Do we have confirmation that the emergency updater is not added to the portable version ? The tiny minority of users who regularly keep ahead of things, on sites such as this one, don’t need it as much as the wider public, I suppose.
>However, automatic, forced upgrade also opens the possibility of all sorts of marketing tricks — of which Avast is fond (“You’re not protected anymore ! Buy our super-duper VPN you don’t really need ! Let your Outlook install be broken once again by our silly, impossible to uninstall anti-spam add-ons you don’t need at all, but we need you to use in order for us to train our anti-spam filters !”). I’m not saying this will be exploited to that effect, just that it makes me uneasy.
Agree, which is why I disable that task scheduler and make sure CCleaner isn’t set to run at bootup. You can disable it in the program itself or through msconfig.
>Do we have confirmation that the emergency updater is not added to the portable version ?
As far as I know, PortableApps (as a whole) can be set to update manually, giving you a chance as to whether you want to install the latest update or not.
Thanks, [www.com]. I run the free version, so I don’t have the benefit of automatic updates anyway. I have unchecked the start at boot option, and I could also uncheck normal updates warning. However, I’ve left it activated, because otherwise you tend never to update at all.
Actually, Piriform let itself be hacked because it was a tiny company and was not prepared to the stringent security procedures that would have been necessary. Their acquisition by a much bigger business, a security business on top of that, is good news as far as security is concerned. It should entice people to use C-Cleaner more, not the other way round.
I realise that we’re drowning in a sea of stupidity because of the way the media rules, and people react like lemmings. I realise the situation looks exactly the opposite, and Avast has an uphill battle on its hands.
However, the simple truth is one should have been weary of Piriform before, not now. Piriform was hacked because it had not been acquired yet by Avast. Those are the facts.
And please don’t take me to task if, one year from now, Piriform, or Avast, are hacked again in some way. This is entirely possible, as is possible that you die tonight, you have a car accident tomorrow morning, or, to make it sound less sinister, you are infected by malware next week.
We’re talking probabilities here, and reasonable due diligence. If we applied the logic of C-Cleaner-haters, we’d forbid end users who’ve fallen victim of malware to ever use a computer again. We’d blame people who’d been involved in car accidents.
If you’ve broken your bones because you run a red light, did not wear a seat belt and drank two bottles of wine one hour before (one does not qualify in my book), people might be justified in blaming the victim. Otherwise, we usually tend to think it’s an unfortunate event, and extend our sympathies to the driver.
@ Anonymous
I’m sorry it was not obvious I was using the term “C-Cleaner haters” in jest. I’m myself a hater of all that hating the haters rigmarole. It’s perfectly a human right for anyone to hate anyone else, or any computer software, if that’s what floats your boat.
However, you’re misguided with your facts, and your trolling colleague jvjv as well, with the added problem he illustrates perfectly the boneheadedness of some individuals, who think that not hating what they hate means you’re stupid or bought out.
First of all, check all the facts, not only the most obvious ones. The actual hacking happened long before it was discovered. That was way before the acquisition.
Second, I don’t think you’re familiar with how a business works. Even if the infection had happened a few weeks after the acquisition, that still would not mean it would not be Piriform’s fault. A company is not an army of robots with a Hitler at the helm pressing buttons, and as soon as he presses one the job is done. An acquisition does not mean you replace Hitler with Stalin, and the minute he gets at his desk he presses other buttons, and all his whims are again executed magically.
What was at fault there was a job process, a method of organisation. Those things dont get designed nor deployed overnight. One week after Piriform was bought by Avast, people were presumably working exactly the way they had always done before. Except for some emergency measures which were actually implemented pronto by Avast, the main of which consisted in disconnecting Piriform employees from their (obviously unsafe) network, and integrating them in Avast’s network. It was Piriform’s network that was hacked, not Avast’s.
Also, the results of good or bad practices take some time to appear. If you were hacked at time n, it means you were doing something wrong at time n – x. If you decided then to mend your ways, better outcomes would not happen right away. That’s not how organisations work.
Hell yeah, finally someone realized the truth. It’s not that switching to alternative software totally reduce such attack but people always re-spelling everything without making their own research or experience. I think CCleaner is still a good product and there all the options given to opt-in and opt-out, not to mention about the nessesarry changes on the program recently.
We just need more attention to important security news to inform people asap.
weary == tired, fatigued
wary == cautious
leery = wary; suspicious
Personally I do not see a need for CCleaner 5.36 to run at startup, so I deleted it using Autoruns 13.80 under Windows 10 FCU. Maybe Startup would do this too.
Thanks for the article, Martin. I downloaded the update, then found and deleted the task.
Just a reminder: CCleaner version 5.32 (released on 11 July 2017) was the last good version of the program before Piriform was acquired by Avast.
The security breach and the need for an “Emergency Updater” (which wasn’t even necessary in the past) just shows that CCleaner is going to continue getting worse
Yesterday I installed the new version and then deleted the two tasks from the Task Scheduler, CCleaner Update and CCleanerSkipUAC which has never run. CCUpdate.exe was installed in the program folder. Afterwards, I re-installed the current version to see if the two tasks would be reapplied, and they were, so I ended up just disabling them instead. I installed the new version because of the cleaning improvements and settings changes otherwise I would have waited longer. So… I take it they are preparing for another software update supply chain attack? Is that supposed to inspire confidence? I’m not feeling it, sorry. :-D
Anyway, I’ve always tried to keep the number of scheduled tasks to a minimum and have somehow managed to creep up to a whopping three enabled tasks. WTH? ;)
Emergency Updater
Following the security incident in September we have taken steps to improve our security across the board. Within CCleaner, this means the addition of an ‘Emergency Updater’ security feature that allows us to force a software update in a worse-case scenario. We have ring-fenced the updater in its own executable to allow it to operate independently from the main executable. The update check runs as a scheduled task in Windows.
Emergency Updater checks regularly to see if an emergency security update is available. If one is, it applies the update immediately. Checks only transmit 1-2 KB of data and generally an emergency update will consist of a differential patch roughly 500 KB in size.
Added new executable: “CCUpdate.exe”
Added new Windows Scheduled Task: “CCleaner Update”
File Verification
Please find below the MD5 and SHA-256 file hashes for verification purposes.
CCleaner Installers
ccsetup536.exe – CCleaner Free installer
MD5: 4bee8e02687aef9c23179b7cf4954220
SHA256: 03d8b1eafddb81140afe512122c20d048863ba861f976f97d28697f9e44a9e5b
ccsetup536_pro.exe – CCleaner Pro installer
MD5: 31474d63d7b4c38706c99570b75cccf9
SHA256: 1245b8e5dd6a5df44671e968d13bda1e0cbd258325761dbabfd76ee43777f27e
ccsetup536pro.exe – CCleaner Pro Trial installer
MD5: e3f35d34de03124c02dbcef0412f0b9a
SHA256: 9456bb6b2e1796c6ed5f36576d18d943c3afd1864cf62436ebc7dacac1fdb22f
ccsetup536_te.exe – CCleaner Technician Edition installer
MD5: b4176e1f9272919a0f3228f39d3bfffb
SHA256: 03cf221dc9b397ad23e8324a383f0e01056a6a52475103b4418bafba6b1f52ce
ccsetup536.zip – CCleaner Portable (zipped)
MD5: 579defc8dac3657d3ada20acaeff84fa
SHA256: 5b295278946e43985cb53c835f499b89f7413e30c7c8bd6bbabdfe51888522ab
ccsetup536_be.exe – CCleaner Business Edition installer
MD5: 1e703d41d5efa550a2eb2ea078b3f6ec
SHA256: 7fdb17c0e7bcb9a5586ebaa5272759f8919bb1852b266eced980de6d59f1e4e2
ccsetup536_be_trial.exe – CCleaner Business Edition Trial installer
MD5: 27946048a1a95d8adf48212c8bb92442
SHA256: b76bbeebeb758766deba9ed6cee6ff95b0e90a4d6186dfd26d8cde452270daae
ccsetup536_x64_be.msi – CCleaner Business Edition 64-bit MSI installer
MD5: 968f7d74c8432208d4aa075e6a54fb7c
SHA256: 6bd8cf256bdb06e566a936b1f0c7e848018f20309dc0c4e87f2aaeeed931c569
ccsetup536_x86_be.msi – CCleaner Business Edition 32-bit MSI installer
MD5: 21f321d26e8021c4280c36217a9de310
SHA256: d0faee386265dda852a96972ff4f616584a343125c59e4f2c88e0d0747733c4a
CCleaner Application Executables
CCleaner.exe – CCleaner 32-bit binaries
MD5: cb1b3f1a1c268609344add54a0586633
SHA256: eae67b1cb15ba359b9b686c3b728f5bd47d73c4716234e8e2471fee8cf563905
CCleaner64.exe – CCleaner 64-bit binaries
MD5: ed5dee709f009cb1f9b35accaae2af0d
SHA256: c3c38be49dc8939cedff89b852632094f13ad2e569c65363bec9039c2d2382fb
CCUpdate.exe – CCleaner Emergency Updater
MD5: 3c3236e8f0c22e177752894a43b00332
SHA256: 58485fb52034e30afed91f7ec0b344bf09a19cc8073a1efaa2c96b2c3e00558a
To those who don’t want top mess with CCleaner installation but don’t want to get the emergency update can just disable it in Task Scheduler.
Task Scheduler -> Task Scheduler Library -> CCleaner Update – >in context menu[right-click] – > Disable.
emupdate.avcdn.net -> https://urlscan.io/result/1745eda3-d279-4809-b1e4-b0aef9e0d8d5#summary
ip-info.ff.avast.com -> https://urlscan.io/result/a6c0cdb5-618a-4e04-8d7a-7f2e0119c78f#summary
ccleaner.tools.avcdn.net->https://urlscan.io/result/ee63ce63-99d2-4082-84ba-cdf9ddde4f04#summary
Submitted URL: http://ccleaner.tools.avcdn.net
Effective URL: https://www.avast.com/de-de/index
Installed and there is no task in scheduled tasks. Using free version. The updater file is in the directory though.
The portable doesn’t add the updater file.
You have to run the Task Scheduler as ADMINISTRATOR. Or download and run “Autoruns for Windows” as administrator and you will see it
https://docs.microsoft.com/en-us/sysinternals/downloads/autoruns
I’ve updated CCleaner to its latest 5.36 version (freeware) this morning and, reading the article, I tried to find this new Emergency Updater feature, unsuccessfully. In what section is it located, ‘Tools’, ‘Options’?
On the other hand, I do have the new CCUpdate.exe file in CCleaner’s install folder.
CCUpdate.exe is not found in the portable version of CCleaner, only the installed from the installer.
Good. Nothing to uninstall/block.
It is an executable file in the program directory, and a task in the Task Scheduler.
I just download the portable version. No CCUpdate.exe on my PC.
I do understand that, but if I have as I said the executable (CCUpdate.exe) in CCleaner’s directory, I don’t have task in the Task Scheduler. The only CCleaner task I have is the CCleanerSkipUAC one, Odd.
Like you say at the end, it seems this could be exploited and end up being more harmful than good. I’ve been using the portable version for a while and this news adds to my reasoning behind it. Not really a fan of installing applications if I don’t have to and definitely not a fan of software that creates its own scheduled tasks.
Added benefit of the portable version is not having the upgrade button on the left.
@TekWarfare
“Added benefit of the portable version is not having the upgrade button on the left.”
I wish I could remember how I did it but I don’t have an upgrade button on my desktop but my laptop does. Registry edit or ini edit maybe? Laptop never gets any love, poor thing. Anyway… BOOM Shaka Lacka!! LoL
https://s1.postimg.org/6csf86n7tb/CCleaner_Update.png
You’d have either be a very trusting person or not that bright to use ccleaner now.
Considering they have since been bought by Avast, they might be better looked after for malware now.
I’ve been keeping a running list, kinda, sorta, of websites and software that have been hacked.
AOL, BBC, DailyMotion, Drudge Report, eBay, Equifax, FHM, Forbes, GameZone, Huffington Post, MakeUseOf, MSN, My Xfinity (Comcast), Newsweek, NFL, NYTimes, Reader’s Digest, Rotten Tomatoes, Skype, TMZ, TransUnion, Yahoo!, YouTube, answers_com, autoblog, dailymail, match_com, nydailynews, weather_com, torrent sites, porn sites and on and on have distributed malware.
Software update supply chain attacks: SWIFT Banking Software Hacked. EvLog, SimDisk and ALZip updates hacked. HandBrake distributed a malware-infected version to macOS users. Transmission BitTorrent client suffered not one, but two supply chain attacks. Hacked CCleaner update distributed for almost a month.
>There’s a big difference between simply hacked and passing on malware to customers. So you can do what you want but I’m not going to trust them again.
@anon, if you’re really worried about that sort of things, then you should stay off computers. That way you’ll never be hacked and you will live a hack-free life.
It’s illegal to spy in the United States ? I don’t think so. In fact, it would be a disaster if it were.
Add Notepad++ to the list. Hacked by the CIA. Why haven’t they been sued? You can also add pretty much every popular router (which is why it’s good to use third party open-source firmware) having been found to have suspicious “vulnerabilities” and in a couple of cases passworded backdoors. I think it was D-Link who had the password “Batman” for the NSA. Hauwei phones were also found to have backdoors. Apparently Kaspersky also involved in suspicious data collection. All the big governments are spying and hacking these days, with the help of tech companies and telecom. That might be legal in totalitarian regimes like Europe, Russia, and China but it’s supposed to be illegal in the US under the US Constitution.
@Clairvaux
You’re right, the list should be and can easily be much longer but I’ve only been keeping track of “some” of the high-traffic websites that I am familiar with and I just realized that FB is not on there and that is like a huge failure on my part but then I don’t do FB. Anyway, I agree 100% with what you’re saying. Just because website owners/publishers have relinquished control of some divs on their site to an ad network, it doesn’t absolve them of responsibility from malicious ads being distributed on their website by an ad network that they hired. And when it happens, unless they get called out on it by a security company, they will go through each day at most just thinking “Oh Well”.
The fact that I’m still using CCleaner shows that I’m willing to some degree to live dangerously. I intentionally waited two weeks after the bad version was released before updating and it ended up not being a long enough wait on my part, that was annoying! I’m also one of those idiots that is lazy and uses an admin account, never ever uses Windows auto update but then somehow has managed to not see a single virus, trojan or malware object on any of my computers in 10 years. Who says miracles don’t happen?
At the end of the day, it doesn’t matter how trusting someone is or… how frightened they are… what matters is that we have to make our choices and then live with the results. Works for me. ;)
That’s an impossible job, Richard ! Your list should be much longer. At that point, we needn’t bother about who has been hacked or not. We need to hold website owners to account as to how they manage a hack — and of course how they defend against one.
And we need to adjust our own security procedures in order to minimise the possible consequences. That’s the best we can hope for.
There’s a big difference between simply hacked and passing on malware to customers. So you can do what you want but I’m not going to trust them again.
If the Security Exchange Commission (SEC) which controls the US stock exchanges can be hacked for insider trading, are people who trade stocks and shares not that bright ??
If you browse the Bleeping Computer blog, you will find a huge number of “not so bright” Banks, Corporations and Governments which have been hacked. Here’s the link : “https://www.bleepingcomputer.com/”
Don’t forget to remove the quotes ” ” or the link will not work. :)
Are you using Windows, Apple or LInux ? Well, according to your opinion then you must be either a very trusting person or not that bright. Ccleaner had 1 incident, and the rest ?? I am not so sure if you are a trusting person ….. :)
>I don’t remember any of those being hijacked like this do you?
Uh, where’ve you been for the 25 years…
I don’t remember any of those being hijacked like this do you? Wouldn’t touch it with a barge pole.
Why shouldn’t you use it? It’s very easy to use, has a good performance.
I’m still going to keep using it. There’s isn’t another program out there that comes close to doing what it does.
The part that bothers me is:
“CCleaner 5.36 does not clean Windows Defender’s scan history, the MRUs of Microsoft Office, and most recently used documents and other MRU files of Windows Explorer anymore.”
I hope we can still create custom paths for it.
You don’t keep up with the news do you?