Microsoft Security Updates August 2017 release
Microsoft released security updates for all supported versions of Microsoft Windows and other company products on August 8, 2017.
This guide provides you with detailed information on these updates. It lists the products that are affected by vulnerabilities, and starts with an Executive Summary that highlights the most important bits of information.
The operating system and other Microsoft product distribution listing follows which highlights how Windows Client and Server products and other company products are affected this month,
The next part of the guide lists new security advisories, and non-security updates that Microsoft released this month.
You find direct links to cumulative security and monthly rollup updates for Windows 10, Windows 8.1 and Windows 7 (and server variants), and download instructions afterwards.
You can check out the July 2017 Patch day overview for information in case you missed it.
Microsoft Security Updates August 2017
You can download the following Excel spreadsheet which lists all security updates that Microsoft released since the last Patch Tuesday in July.
Just click on the following link to download the spreadsheet to your system:Â (Download Removed)
Executive Summary
- Microsoft released security patches for all versions of Microsoft Windows.
- Other Microsoft products with patched vulnerabilities are Microsoft Edge, Internet Explorer, Microsoft SharePoint and Microsoft SQL Server
Operating System Distribution
- Windows 7:Â 9 vulnerabilities of which 2 are rated critical, 7 important
- Windows 8.1: 11 vulnerabilities of which 4 are rated critical, 7 important
- Windows 10 version 1703: 14 vulnerabilities of which 5 are rated critical, 9 important
Windows Server products:
- Windows Server 2008 R2: 10 vulnerabilities, of which 3 are rated critical, 7 important
- Windows Server 2012 and 2012 R2: 11 vulnerabilities, of which 4 are rated critical 7 important
- Windows Server 2016: 12 vulnerabilities of which 4 are rated critical, 8 important
Other Microsoft Products
- Internet Explorer 11: 8Â vulnerabilities, 7 critical, 1 important
- Microsoft Edge: 28 vulnerabilities, 21 critical, 7 important, 1 moderate
Security Updates
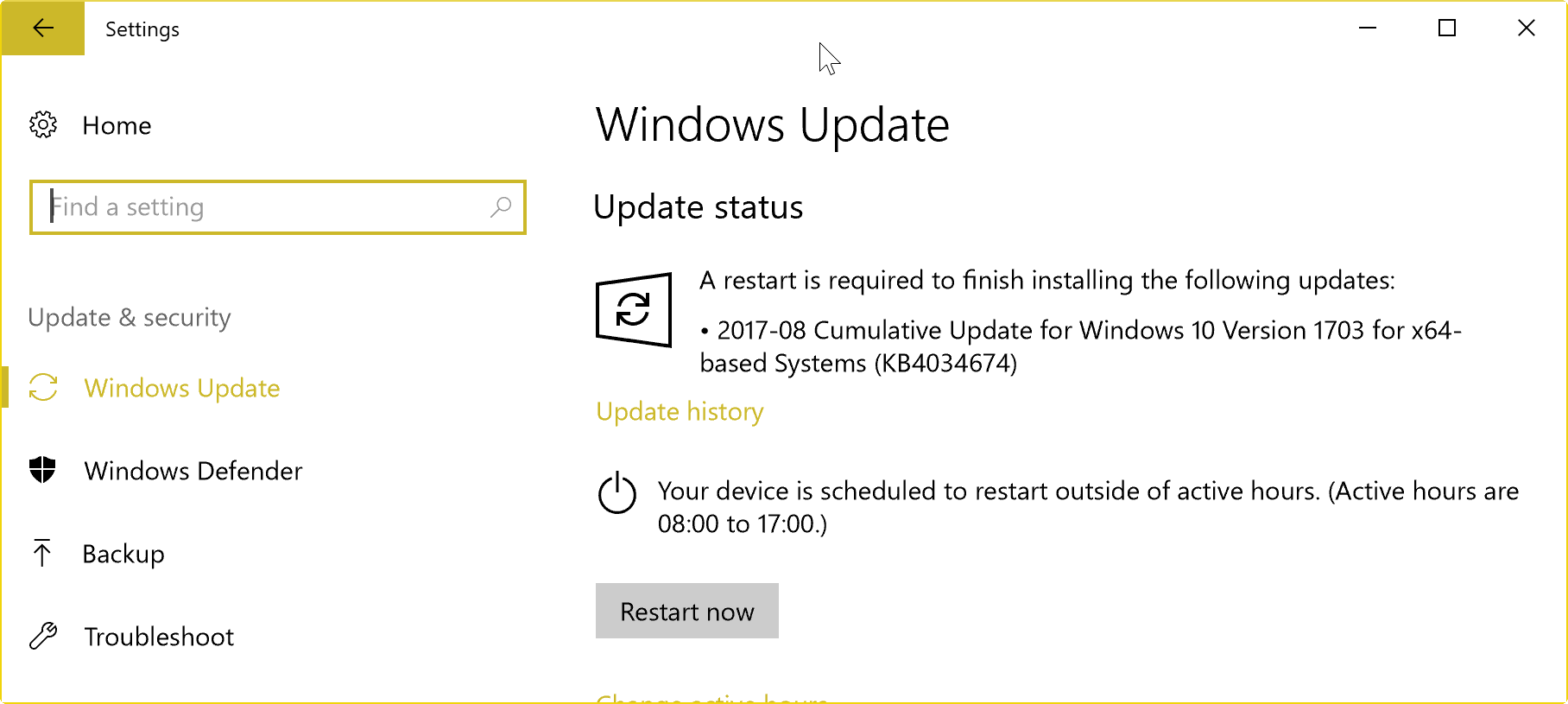
KB4034674 -- August 8, 2017 Cumulative update for Windows 10 Version 1703
- Addressed issue where the policies provisioned using Mobile Device Management (MDM) should take precedence over policies set by provisioning packages.
- Addressed issue where the Site to Zone Assignment List group policy (GPO) was not set on machines when it was enabled.
- Addressed issue where the AppLocker rules wizard crashes when selecting accounts.
- Addressed issue where the primary computer relationship is not determined when you have a disjoint NetBIOS domain name for your DNS Name. This prevents folder redirection and roaming profiles from successfully blocking your profile or redirects folders to a non-primary computer.
- Addressed issue where an access violation in the Mobile Device Manager Enterprise feature causes stop errors.
- Security updates to Microsoft Edge, Microsoft Windows Search Component, Microsoft Scripting Engine, Microsoft Windows PDF Library, Windows Hyper-V, Windows Server, Windows kernel-mode drivers, Windows Subsystem for Linux, Windows shell, Common Log File System Driver, Internet Explorer, and the Microsoft JET Database Engine.
KB4034679 -- August 8, 2017 Security only update for Windows 7 SP1 and Windows Server 2008 R2 SP1
- Security updates to Windows Server, Microsoft JET Database Engine, Windows kernel-mode drivers, Common Log File System Driver, Microsoft Windows Search Component, and Volume Manager Driver.
KB4034664 -- August 8, 2017 Monthly Rollup for Windows 7 SP1 and Windows Server 2008 R2 SP1
Same as KB4034679
KB4034672 -- August 8, 2017 Security only update for Windows 8.1 and Windows Server 2012 R2
- Addressed issue where a LUN connection that was received after the buffer allocation during iSCSI statistic collection overflowed the buffer and caused error 0x19. A UI issue that hides the iSCSI targets will be addressed in an upcoming release.
- Security updates to Windows Server, Microsoft Windows Search Component, Volume Manager Driver, Common Log File System Driver, Microsoft Windows PDF Library, Microsoft JET Database Engine, Windows kernel-mode drivers, and Windows Hyper-V.
KB4034681 -- August 8, 2017 Monthly Rollup for Windows 8.1 and Windows Server 2012 R2
same as KB4034672, plus
- Addressed issue with a port and thread leak that can cause a broad array of symptoms including unresponsive systems and iSCSI target connection failures. This occurs after installing monthly updates released between April 11, 2017 (KB4015550) through July 11, 2017 (KB4025336). This issue was called out as known issue in the corresponding release notes for these releases.
- Addressed issue where LSASS.EXE encounters a deadlock and the server must be rebooted.
- Addressed issue where the Remote Desktop idle timeout warning did not appear after setting the idle time.
- Addressed issue with MSiSCSI where the system process has a very high number of threads or the server runs out of ephemeral ports. This causes the system to stop responding or throw an error.
- Addressed issue where when a failover cluster fails over from one server to another, a clustered IP address resource does not come online and causes the failover to stop functioning.
- Addressed issue where a DNS server may crash after the import of the DSSet file when configuring secure, delegated child zones.
- Addressed issue where a LUN connection that was received after the buffer allocation during iSCSI statistic collection overflowed the buffer and caused error 0x19. A UI issue that hides the iSCSI targets will be addressed in an upcoming release..
- Addressed issue where if there was an error on a storage controller, some paths could not fail over to other paths. Instead, access to the disk was completely lost.
- Addressed issue to prevent user logon delays when processes that have registered top-level windows fail to respond to BroadcastSystemMessages sent by the Group Policy Preference client-side extensions.
- Addressed issue where Windows Server 2012R2 throws error “STOP 0XCA (Duplicate PDO)†when redirecting certain USB devices using RemoteFX. To fix this, do the following:Go to the registry location SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations.
Create a new DWORD value “fUniqueInstanceID â€.
Set the value to “1â€.
Reboot after setting this registry. - Addressed issue where enabling the policy “Display information about previous logons during user logon†prevents Remote Desktop Protocol providers from allowing logins with no user interaction.
- Addressed issue where the TsPubRPC service running in Svchost.exe experiences a memory leak when RemoteApp applications are configured with file type associations.
- Addressed issue where files and folders accumulate in the UvhdCleanupBin folder in Remote Desktop session hosts. These files are not deleted when a user logs off if the path limit is exceeded. In extreme cases, this issue can cause logon failures.
- Addressed issue where a Microsoft Enterprise CA cannot request that a Microsoft subordinate CA template be used for key encipherment. A single certificate can provide multiple usages like key encipherment and CRL signing.
- Addressed issue to allow NPS servers to accept certificates with multiple usages.
- Addressed issue where both transient and listener process TCP ports for the loopback sockets leak because of a leaked reference count. Such ports do not appear in NETSTAT.
- Addressed issue to enable logging to detect weak cryptography.
- Addressed issue with wireless network clients that disconnect from wireless access points after the EAPOL key retransmission timeout (5 minutes). This occurs because the M2 bit is incorrectly set during the four-way handshake.
- Addressed issue where a request to a website results in a 503 response when IIS runs in "Dynamic Site Activation (DSA) Mode". This occurs when the default app pool identity is a specific user/password and a specific app pool’s identity is configured to use "ApplicationPoolIdentity".
- Addressed issue where NetInfo_list may not contain all the network interfaces information. Additionally, the DNS client cannot use all the connected network interfaces while sending the query. This occurs when the host is running in low memory when the NetInfo_Build gets started.
- Addressed issue where if an interface is unavailable during the NetInfo_Build, the DNS client will not use that interface to send queries for the next 15 mins even if the interface comes back before 15 minutes.
- Addressed issue to implement a callback function to receive a notification when an interface comes back after an unavailable state. This callback prevents a host from going into the sleep state.
Known Issues
None
Security advisories and updates
Microsoft Security Advisory 4038556 --Â Guidance for securing applications that host the WebBrowser Control
Non-security related updates
KB4034335 -- Update for Windows 10 Version 1703 -- Some system applications don't work as expected after you upgrade to Windows 10 Version 1703
KB4035508 -- Update for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7 on Windows Embedded 8 Standard and Windows Server 2012
KB4035509 -- Update for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7 on Windows 8.1 and Windows Server 2012 R2
KB4035510 -- Update for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7 on Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4019276 -- Update for Windows Server 2008 --Â Update to add support for TLS 1.1 and TLS 1.2 in Windows Server 2008 SP2
KB4032113 -- July, 2017 Preview of Quality Rollup for .NET Framework 3.5.1 on Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4032114 -- July, 2017 Preview of Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.7 on Windows Embedded 8 Standard and Windows Server 2012
KB4032115 -- July, 2017 Preview of Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7 on Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2
KB4032116 -- July, 2017 Preview of Quality Rollup for .NET Framework 2.0 on Windows Server 2008
KB4033428 -- Update for Windows Server 2012 R2 -- Windows Server 2012 R2 processor generation detection reliability update: July 18, 2017
KB4032188 -- Windows 10 Build 15063.502 update July 31, 2017
- Addressed issue that causes a Microsoft Installer (MSI) application to fail for standard (non-admin) users when installed on a per user basis.
- Addressed issue to enable support in the DevDetail Configuration Service Provider (CSP) to return the UBR number in the D part of the SwV node.
- Addressed issue where NTFS sparse files were unexpectedly truncated (NTFS sparse files are used by Data Deduplication—deduplicated files may be unexpectedly corrupted as a result). Also updated chkdsk to detect which files are corrupted.
- Addressed issue where the IME pad was not launching correctly in the Microsoft Edge browser for certain markets.
- Addressed issue to allow Win32 applications to work with various Bluetooth LE devices including head tracking devices.
- Addressed issue in the Mobile Device Manager Enterprise feature to allow headsets to work correctly.
- Addressed issue where device drivers are not loading.
- Addressed a reliability issue when playing specific types of spatial sound content.
- Addressed issue with a dropped key on Microsoft Surface Keyboard and Microsoft Surface Ergo Keyboard, and addressed Wacom active pen connection failures.
- Addressed issue to improve stability for USB type C during device arrival and removal during system power changes.
- Addressed USB host controller issue where the host controller no longer responds to the attached peripherals.
- Addressed MP4 compatibility issue while playing content from a social media site in Microsoft Edge.
- Addressed issue with audio headsets connected to a PC through Xbox 360 controllers.
- Addressed a reliability issue with launching a Settings app while another application is using the camera device concurrently.
- Addressed issue with notifications (SMS, Calendar) for an activity tracker.
- Addressed issue with video playback artifacts during transitions from portrait to landscape on mobile devices.
- Addressed issue with Skype calls becoming unresponsive after about 20 minutes when using Bluetooth headsets with Hands-Free Profile (HFP) connections with negotiated mSBC codec (Wideband Speech).
- Addressed issue where a service using a Managed Service Account (MSA) fails to connect to the domain after an automatic password update.
- Addressed issue where, in some cases, a drive that utilizes on-drive hardware encryption would not automatically unlock at system startup.
- Addressed issue where “cipher.exe /u†fails on client machines that are deployed with InTune, Windows Information Protection (WIP), and an updated Data Recovery Agent (DRA) certificate. Cipher.exe will fail with one of the following errors: “The request is not supported" or "The system cannot find the file specifiedâ€.
- Addressed issue where a memory leak occurs in a nonpaged pool with the “NDnd†memory tag when you have a network bridge set up.
- Addressed issue where you cannot add Work and School accounts in Windows Store, and you may get an error that reads, “We encountered an error; please try signing in again later.â€
- Addressed issue issue where if a Surface Hub enters Sleep mode and then resumes, it may require the user to sign in to Skype again.
- Addressed issue where some Windows Forms (WinForms) applications that use DataGridView, Menu controls, or call a constructor for a Screen object experienced performance regressions in .NET 4.7. This was caused by additional Garbage Collections. In some cases, there was an empty UI because of a lack of GDI+ handles.
- Addressed issue where Magnifier Lens users cannot click on buttons or select web content in Microsoft Edge or Cortana results.
- Addressed issue introduced in the June updates where some applications may not launch when a device resumes from Connected Standby mode.
How to download and install the August 2017 security updates

PCs that run Windows are configured by default to search for, download, and install security updates automatically.
The check does not happen in real-time though, and you may run a manual check to have the updates for devices picked up as quickly as possible.
Note: it is suggested that you create a backup of your system before you install any update on it.
To run a manual check for updates, do the following:
- Tap on the Windows-key, type Windows Update, and hit the Enter-key.
- Depending on how Windows Update is configured, you either need to click on the "check for updates" button, or that happens automatically.
- Again, depending on the configuration, Windows may download and install these updates automatically when found, or on user request.
Direct update downloads
Windows 7 SP1 and Windows Server 2008 R2 SP
Windows 8.1 and Windows Server 2012 R2
Windows 10 and Windows Server 2016 (version 1703)
- KB4034674 -- Cumulative Update for Windows 10 Version 1703
Additional resources





















Users are not able to access database after installing August patch of Microsoft. Please suggest. Its urgent
Hi, thanks for all your work on this, great site!
Under Security updates section above, where it says:
KB4034681 — August 8, 2017 Monthly Rollup for Windows 8.1 and Windows Server 2012 R2, same as KB4034672, plus ……
Where did you find all the information for the 22 extra bullet points included??
Thanks!
I use Belarc frequently as a home user. I love it, but notice there is sometimes a 2-3 day delay after installing a Windows 10 update where Belarc says an update is missing. When Belarc gets around to updating their database, all is well, so their analysis has to be understood in that light.
Well, I’ve definitely noticed that Belarc takes at least a couple of days after Patch Tuesday to incorporate Patch Tuesday updates in Advisor’s database. This August, the Advisor database didn’t get updated until sometime in the afternoon on Thursday, Pacific Time. I’ve had a few positives in Belarc after patching, but they usually involve updates that WSUS has blacklisted because they have problems. And sometimes they’re just false positives. (Over the previous month, I had one “missing” security update that Microsoft itself said yielded false positives after being properly installed.)
At any rate, the delay is not a big deal for me, since I always wait for at least a few days after Patch Tuesday before installing Windows updates, to be able to check out the real-world fallout first. (Windows 7 doesn’t seem to get as many buggy updates as Windows 10 does, but it’s been known to happen.)
Win7x64 SP1 user here. I use WSUS Offline Update with the “security updates only” option enabled to keep my machine up to date. (I simply don’t trust Windows Update anymore, period.) I double-check my security status, before and after, using Belarc Advisor. Funny story:
A friend of mine who uses the same update strategy noticed that the fans on the computer closest to his bedroom were going into high gear in the wee hours of the morning. When that happened to me on my laptop, a few months before Windows 10 was released, it was because of a runaway Microsoft diagnostics utility. (It ended up melting away my thermal compound and burning out my fan, a really fun repair on most laptops, including mine /s.) So I checked, and lo and behold, a whole bunch of Microsoft diagnostics, telemetry, and “customer experience improvement” (or whatever they call it) utilities had been re-enabled, even though we had previously disabled all of them using WPD.
Moral of the story: After every Windows update run, run WPD (or your favorite anti-dickware utility) again and make sure that all of the things you thought had been disabled haven’t been re-enabled (or replaced with new dickware) by Microsoft’s “security-only” updates.
Apart from that, it was a smooth update for both me (who uses LibreOffice) and my friend (who uses MS Office). Belarc gives me a completely clean bill of health, and my friend has a missing security update that WSUS flags as problematic and that supposedly fixes a vulnerability that will never affect him in practice.
Looks like my history is gone and the machines that were updated from this month are not able to report back to WSUS. I am uninstalling KB4034658 right now. I hope this will fix my issue. Anyone got input on this?
This issue has been reported by many. Check out the askwoody web site for details.
mine aswell
Thanks Nadella (Salary US$ 18.2 million (2014), Source: https://en.wikipedia.org/wiki/Satya_Nadella) for the risk, telemetry and for the very user-friendly windows-update service.
My next step is to try out ReactOS (alpha stage), which is a Open Source Windows Replacement:
https://www.reactos.org/
https://sourceforge.net/projects/reactos/
https://github.com/reactos/reactos/pulls
https://twitter.com/reactos
https://en.wikipedia.org/wiki/ReactOS
Screenshots:
https://www.reactos.org/gallery
Changelogs:
https://www.reactos.org/wiki/Changelogs
Download ReactOS 0.4.5:
You can download ReactOS in two different flavors:
– As a Live CD so you can test it without installing into your computer.
– Or as a Boot CD so you can install ReactOS on your PC.
https://www.reactos.org/download
The ultimate goal of ReactOS is to allow you to remove Windows® and install ReactOS without the end user noticing the change:
https://web.archive.org/web/20120920030447/http://www.reactos.org/en/index.html
ReactOS, the Windows XP Alternative:
https://www.ghacks.net/2012/02/12/reactos-the-windows-xp-alternative/
ReactOS: Open source Windows:
https://www.ghacks.net/2008/10/20/reactos-open-source-windows/
The Alternatives to Windows 8:
https://www.ghacks.net/2012/02/13/the-alternatives-to-windows-8/
ReactOS Is a Promising Open Source Windows Replacement:
http://www.linuxinsider.com/story/83578.html
Sadly ReactOS will always remain a clone of XP (NT5-based operating systems) in “alpha stage”. Good luck with that.
First of all, I want to thank you, Martin, for this elaborate explanation of this months Microsoft update.
And may be I should not write this because maybe I am calling the crash ghosts back to a more active live from there not so many total systems crashes sleep who were before ( Think windows 3.1, Windows 93, Windows 95, XP and even Windows 7)?
Before those system crashes were so bad that I had to on a regular base reinstall the complete system with a backup/restore program, but maybe am I wrong?
Are there any statistical figures that Windows 10 is not so much completely crashing anymore in comparison to Windows 7, etc.? And I understand that the technical know how are decades beyond windows 3.1 but when you compare the number of users statistically speaking per 100.000 and even the numbers out how are the figures then?
That is what I am wondering.
I just want to thank Martin and express my appreciation for his work to continuously provide us with this comprehensive bulletin every month – especially with all those links to individual downloads. It makes my Patch Tuesdays so much easier and less stressful.
Many thanks Martin !
Ditto. The spreadsheet is really helpful, too.
Stop bitchin’ and start switchin’
Freedom is one linux install away. Join us.
Nice turn of phrase! (It reminds me of, “Quit yer grinnin’ an’ drop yer linen!”) I started seeing the writing on the wall when Microsoft launched the GWX program. For now, I’m puttering along with Windows 7 and WSUS Offline Update (with the security-updates-only option checked), but I’m trialing a few Linux distros in virtual machines and will make the switch at some point before Windows 7’s end of life on 14 January 2020. Probably a good deal sooner…
Internet Explorer download links: https://www.catalog.update.microsoft.com/Search.aspx?q=KB4034733
“Microsoft Edge: 28 vulnerabilities, 21 critical, 7 important, 1 moderate”
21+7+1 = 29
@CHEF-KOCH
Hope they’re (M$) paying you well for this. ^_^
Martin and I get millions to push the products /end of trolling :D
Still not ready for the desktop.
Sorry, M$, I’ve tried every version and prior to that, DOS. Guess what? Still sucks. All of it. And parrots paid to defend M$’ crap ware are everywhere on the web. Very sad.
Windows 10 has ~double security hols than Windows 7, each month.
Ikr. And to people who keep saying that 7 is more mature and 10 is new – you’re absolutely wrong. 10 will never be on par with 7 in this regard, simply due to its so much larger attack surface. 10, on top of Win32, has an entire shell that can be exploited. Shell which is not present at all in 7 and considerably smaller in 8.1. And the numbers reflect this like a mirror:
Windows 7: 9 vulnerabilities
Windows 8.1: 11 vulnerabilities
Windows 10 version 1703: 14 vulnerabilities
Windows Server 2008 R2: 10 vulnerabilities
Windows Server 2012 and 2012 R2: 11 vulnerabilities
Windows Server 2016: 12 vulnerabilities
Both on server and client AND server vs client of the same branch.
BS, on what is your stuff based?
Windows 10 has more features but less CVE’s overall than any other OS:
https://www.cvedetails.com/top-50-products.php
>> Windows 10 has ~double security hols than Windows 7, each month.
Needs to be noted that Win7 is also a good five years older than Win10. Once you take into account the total, accumulated number of patches that kind of comparison isn’t as valid. Instead of skepticism I just appreciate there are these fixes that continue to get pushed out to us.
@svim
Getting fixes being pushed to us is something to be expected from company as rich as Microsoft. It’s not like we don’t pay for this OS.
Isn’t Microsoft pushing Windows 10 as a more secure OS than Windows 7 ? So far they are failing miserably.
That’s incorrect, the thing is stuff getting changed more frequently which means you need to adjust it.
The update for version 1607 (Anniversary Update) that bumps up build version to 1593 wipes out update history in settings. Click on update history and it says no updates have been installed. The updates do show in control panel under uninstall updates. Anyone else experience this? Have not uninstalled updates to see if issue persists.
Found where you are talking about. Yep I have my all my updates showing under Control panel but no update history in settings. So it appears to me all the updates are still installed, they’re just gone. MS needs to look into this problem. I will not install creator update until all kinks are fixed. Smh
Yes happened here also. I’m not sure where you see your updates under control panel under uninstall updates though. I don’t see that on my computer.
Searched this problem just now after installing week of Aug. 8 Cumulative Update and it brought me here. Yes, I see my update history blanked. I, too have been delaying Creators Update. I had a first time fail with this cumulative (like so many earlier this year), despite the fact that the previous two months of all updates performed smoothly.
I have used “latestwu” and “wushowhide” Troubleshooting Pack Cabinets with some success for several months; but I realize “Creators” can only be delayed for so long. Thanks for the discussion here and providing context for this Win10 issue.
Yes, My updated history was also wiped out. Not sure why this happened….It also turned off the setting to give me updates for other Microsoft products.
Also, for some reason I never get the Creators Update. It just says it’s on the way, and I never bother to run the update manually….
*sigh*
me too ,
Woody on Windows blog at Computerworld and his site askwoody.com list this as a bug in the KB 4034658 update for version 1607. Uninstalling the update may bring the update history back, but I have not tried that yet. Hopefully MS will issue a fix soon (but not holding my breath). And I still haven’t gotten the Creators Update either, but the mess MS has created, that may be a good thing.
All these updates, curiously still no option to disable telemetry and data theft to microsoft and others. Pass.