Microsoft SmartScreen Filter gets Drive-By Attack Protection
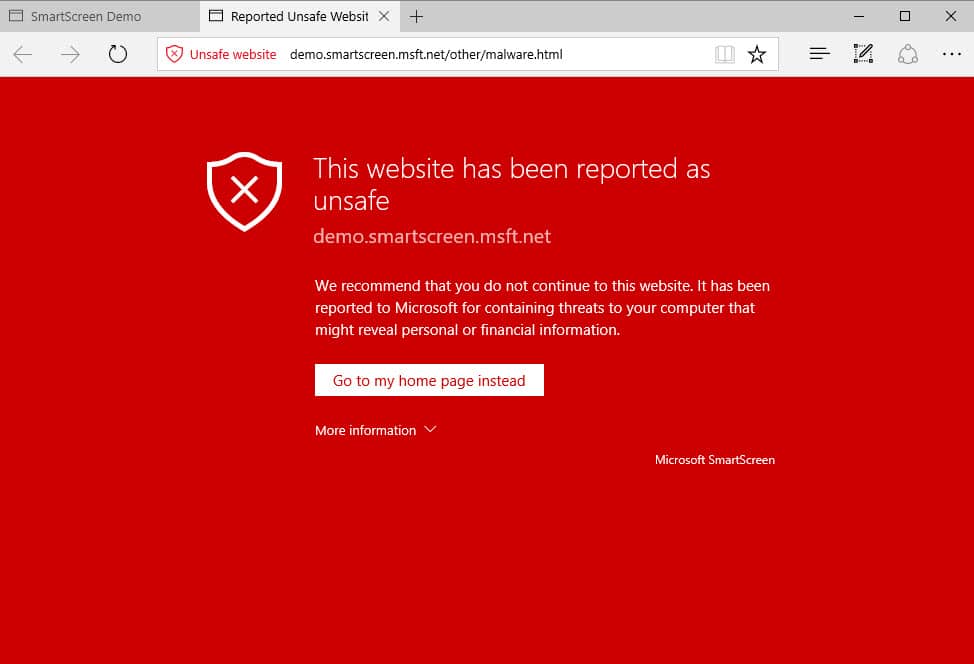
Microsoft SmartScreen Filter is a protective feature integrated into the Windows operating system as well as Microsoft's web browsers Internet Explorer and Microsoft Edge that protects computer users from certain kinds of Internet-based attacks.
It works similar to Google's SafeBrowsing feature but is broader in scope as it is not limited to a single program but works system-wide.
Microsoft updated SmartScreen's set of security features recently by adding protection from drive-by attacks to the service.
Drive-by attacks originate often on trusted websites where they are executed through third-party scripts such as advertisement or hacks. If it often the case that they don't require user interaction for execution and that is it enough for the user to visit a website to be exposed to the attack.
SmartScreen Filter
Microsoft notes that drive-by attacks make use of exploit kits for scaling purposes that target vulnerabilities in software such as the web browser itself or plugins such as Flash or Java that are commonly used.
The time to exploit has decreased in 2015 according to Microsoft with exploit kits exploiting patched vulnerabilities as early as the day patches were released for them giving users and system administrators less time to apply security patches and updates to operating systems or programs.
So how is SmartScreen Filter's drive-by attack working?
Unlike existing SmartScreen protection from socially engineered attacks, drive-by attacks need to be detected and prevented before any web content is parsed and rendered. To avoid impacting browsing performance, SmartScreen helps protect against drive-by attacks by using a small cache file created by the SmartScreen service. This cache file is periodically updated by your browser to help keep you protected and to ensure that calls to the SmartScreen service are only made if we believe there’s a high probability of malicious content on a page
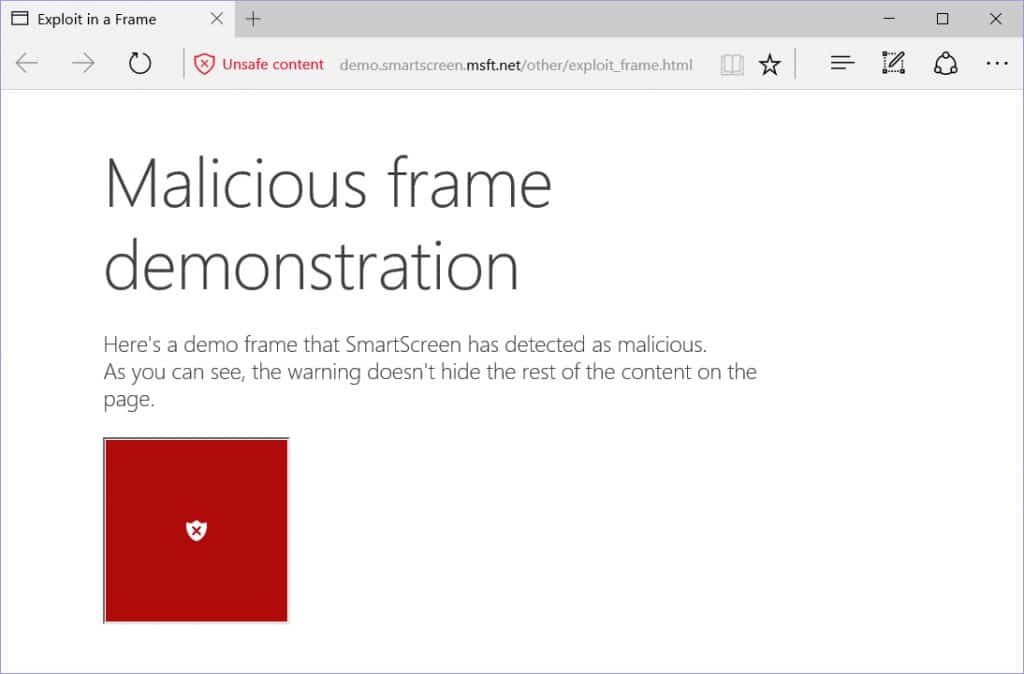
Another improvement that goes along with the new security feature is that SmartScreen may now show warnings for contents in frames on sites only. Previously, SmartScreen would display full page warnings on malicious pages even if the attack was carried out using framed content.
The new feature will block only the malicious content on the page allowing users to interact with the safe parts of the page.
The company notes on the official Microsoft Edge blog that the new feature is only available in Microsoft Edge and Internet Explorer 11.
The decision to limit the new feature to Microsoft's two recent browsers falls in line with the company's decision to phase out older versions of Internet Explorer on Windows 7 and Windows 8 systems.
It does mean however that the feature won't be available on all versions of Windows still supported by Microsoft (including Windows Vista which is stuck with Internet Explorer 9).
Now You: Do you have SmartScreen turned on or off?













I may be totally missing the technical point here, but wouldn’t it be more useful to implement this concept in DNS server environments, rather than just two browsers Microsoft promotes?
“The time to exploit has decreased in 2015 according to Microsoft with exploit kits exploiting patched vulnerabilities as
early as the day patches were released”
When did Microsoft announce this. Do you happen to have a link to this statement.
Microsoft mentions this in the linked article.
Thank You.
“The company notes on the official Microsoft Edge blog that the new feature is only available in Microsoft Edge and Internet Explorer 11.”
I don’t use Edge or Internet Explorer so this means nothing to me.
Do you post what you do and don’t use on every article? No one cares, this is a news article. Seriously, get over yourself.
It would be informative if you advised us what browser if any that you use.
Maybe you do not use windows at all