A second look at VeraCrypt, an unofficial TrueCrypt successor
When the TrueCrypt developers announced that they would quit developing the encryption software because of it not being secure, many users of the software did not know what to make of the announcement.
What became clear quickly was that TrueCrypt development would not continue in this form and that others would have to take over for development to continue.
A couple of projects were announced shortly after the dust settled and one of them was VeraCrypt by IDRIX. It was not the only project, Ciphershed is another, but one of the first to produce a program that users could download and make use of to encrypt their hard drives.
While based on TrueCrypt, the format used by VeraCrypt is not compatible with that of TrueCrypt. Users who want to move from TrueCrypt need to decrypt their drives and partitions first before they encrypt them again using VeraCrypt.
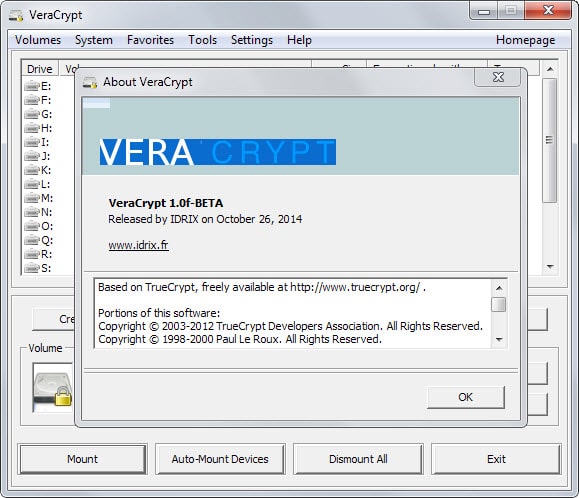
The most recent stable version of VeraCrypt, version 1.0e was released on September 4, 2014. It corrected security vulnerabilities found by the Open Crypto Audit Project. The project's goal is to audit TrueCrypt thoroughly to make sure it is secure.
In addition to that, it also fixed security issues detected by code analysis and fixed several minor bugs.
A beta version of the upcoming VeraCrypt 1.0f was released on October 26, 2014. The version introduces a number of changes affecting all supported operating systems and changes that only affect select systems.
All operating systems benefit from support for SHA-256 for volume encryption, SHA-512 as the default key derivation algorithm and a change of the order of preference of derivation algorithms to SHA-512 --> Whirlpool --> Sha-256 --> RIPEMD160.
A vulnerability in the bootloader was fixed on Windows and various optimizations were made to it as well. The developers added support for SHA-256 to the system boot encryption option and fixed a ShellExecute security issue as well.
Linux and Mac OS X users benefit from support for hard drives with sector sizes larger than 512. Linux on top of that got support for NTFS formatting of volumes.
It is not clear yet when the final VeraCRypt 1.0f version is released but if the developers keep the three month development cycle it will be release in December.
VeraCrypt development is progressing nicely with new versions being released regularly by the developers. The final verdict on TrueCrypt's security is still out as the second part of the audit has not been completed yet. Judging from the past, it is likely that IDRIX will resolve the majority of issues discovered during the second part of the audit quickly since they have done so before for the first part.
Now You: Are you encrypting your date/drives? If so, which software are you using for that?





















The ideal situation will be where very many encryption packages become available either as open source or out of jurisdiction of UK and USA.
I will be pleased when there are comparison tables of many such packagess, too many for the pond-life at GCHQ and NSA to keep tabs on.
TrueCrypt developers were bought by Apple
Is there a source for this?
I’m using DiskCryptor at the moment and have no complaints.
I don’t feel any less secure than I did with TrueCrypt after doing a ton of reading.
What I really need is an open-source solution to handle UEFI since I’m not willing to shell out for the paid solution from Jetico.
I’m avoiding Vercrypt because the license is Ms-PL, which I tend to avoid because it can go commercial at any time. Hoping Ciphershed (GPL and more likely to get integrated into Linux) does a better job, though I’m not seeing a lot of movement there.
The main problem here isn’t about coding – it’s about trust.
I more or less trusted Truecrypt – especially as I didn’t feel that attention to my files might ever come from other than nosey parkers – official or otherwise. Here in the UK almost every government or local government petty clerk now has official access without due process. You can be prosecuted for refusing to provide passwords, and prosecuted too for telling anyone you’ve been asked. But I’m not so much worried about their reading my files as about what they might do afterwards – the small Scottish local authority under which I live has an appalling record of lost and compromised data – mainly because they employ college-educated ‘IT specialists’ who are quite clearly not half as clever as they think they are.
It’s widely held that security services can’t crack Truecrypt – but I take that with a pinch of salt – if they had succeeded, they would hardly tell us about it – far more likely they’d leave us with a sense of false security. But for most ordinary folks, Truecrypt was still the preferred encryption system – and frankly I don’t believe a word about the reason for its abandonment. Just smells that the author was either paid off or frightened off.
Trouble is – how far can we trust the new offerings? Applications like VeraCrypt need to do more than assure us about their algorithms – they need to show that their code can be trusted.
For myself, I’m still using the last complete version of TrueCrypt. If that can’t be assured to be 100% safe, I’m not sure there’s anything to date I’d trust to be better.
Exactly how I feel. If VeraCrypt gets a full audit then I’m in, until then TrueCrypt is still fine.
My take on TrueCrypt is it was coerced into providing backdoor access to the NSA and they refused thus pulling the plug on their own software. There’s some decent evidence to back this up. If you’re interested start with this thread: https://www.livebusinesschat.com/smf/index.php?PHPSESSID=ni88052n5o14i7i6u2abq9tif5&topic=5629.0
If you check the thread that Andrew’s link points to, you’ll see that this theory was disproved (the author admits it himself). See: http://www.theguardian.com/technology/2014/jun/17/truecrypt-secret-message-nsa-spying.
My sentiment exactly!
If TrueCrypt -WAS- in fact taken down because of a U.S. (or other) government threat because it was too strong, then anything that’s still left standing in the open is automatically discredited in terms of trust, at least in my eyes. And since we don’t KNOW what happened precisely……
Though, truthfully, ANYTHING you download over the internet COULD be tainted. We take so much for granted.
I see no reason to switch from TrueCrypt 7.1
This is how I felt too. Though it is a bit concerning when the developers of a ‘security’ application quit working on it because they say it isn’t secure… Which of course without development will mean over time it will continue to get ‘less secure’.
The good news about a TrueCrypt successor, is that new security flaws can be fixed in the future. Though I’m not dealing with protecting governmental secrets, so my benefit and need for foolproof encryption, isn’t a matter of national security.
Agreed, normal users doesn’t need to worry about the turecrypt’s security issue.
I have always wanted to try Truecrypt but never did – I have used Axcrypt for many years to encrypt certain data.