Activision employee data published on the Internet after cyber intrusion

Last week, Call of Duty maker Activision confirmed that it suffered a security breach in December 2022. According to information published by a third-party with knowledge of the attack, SMS phishing was used to gain access to the system of an Activision employee.

SMS Phishing, or short smishing, is usually used in targeted attacks against individual users. The attacker managed to obtain two-factor verification codes from the targeted employee to breach the system and obtain the data.
Some documents, copied during the attack, were published by the third-party on Twitter as verification for the claim. Insider Gaming obtained a copy of the entire data dump and confirmed that information about existing and upcoming Call of Duty games was found in the files.
According to the posted information, Activision plans to release a new DLC for Modern Warfare 2 and two Call of Duty games in the coming two years.
The leak included employee information as well. According to Insider Gaming, data included "full names, emails, phone numbers, salaries, places of work, and more" of thousands of Activision employees.
Activision published a statement in response last week in which the company claimed that "no sensitive employee data, game code, or player data was accessed" by the threat actor in the December 2022 breach. Activision refuted the claim that sensitive employee information was copied by the threat actor.
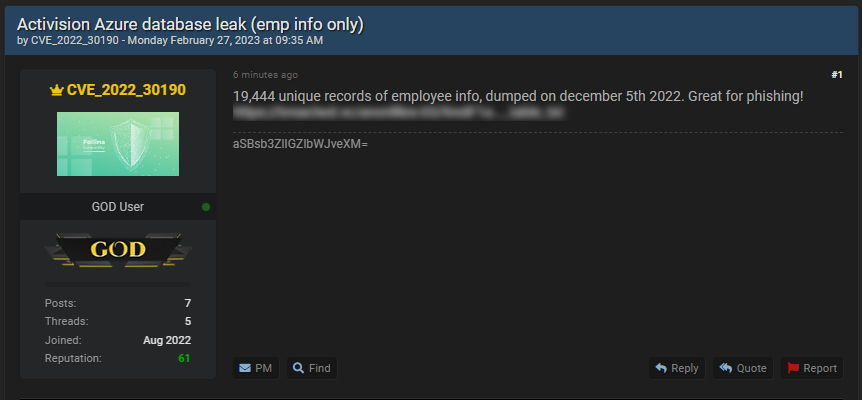
Now, cyber criminals have published employee data in an underground Internet forum. According to the information, 19444 unique records of employee is included in the file that is publicly available on the forum. They further note that the data is "great for phishing".
The text file has a size of less than 5 Megabytes. Many of the included records are incomplete. For most, only an email address and name is provided. For others, job titles, departments, phone numbers and other information is also available.
Core Activision employee data appears to be included the most. For the majority, names, email addresses and positions are listed. For some, location information and phone numbers are also listed in the dump.
Name and email are sufficient for targeted phishing campaigns. A quick check on LinkedIn confirmed the validity of the information. Searches for a sample of employee names on LinkedIn returned them as employees of Activision or partners.
An IT security researcher published a screenshot of the underground forum post on Twitter. The data includes email addresses, names, phone numbers and other employee-specific data. Threat actors could use the information for targeted phishing campaigns to gain access to other Activision systems.
Activision has not responded yet to the leak on the underground forum.





















as I said many times before, “‘nothing on the internet is safe”” . If the systems are strong than the people working with the systems are weak, anyway take care for you digital info.
Surprised that the data in the folders/files was not encrypted, than the data can be stolen but encrypted data is still hard to decode and make useful.
Nonsense, it was a classic phishing attack. It is known since years that SMS is a terrible 2FA method, easily defeated by SIM swapping attacks.
HOWEVER:
A 2FA hardware dongle can only authenticate at a physical machine in its direct location. You cannot send that info to someone else. The protocol runs over USB directly between client app and authenticator dongle.
They used insecure outdated methods that can be phished. A FIDO2 dongle cannot even work on a phishing site since it also checks origin of the request. And then I still need to push a button here as a 3rd security factor, besides password and account name.
You need physical access with FIDO2. Leave security to the PROS.