Signal says Twilio data breach resulted in 1900 users' phone numbers being exposed
A week ago, I wrote an article about a data breach that happened at Twilio. It appears that Signal was impacted by this security incident.

1900 Signal users' phone numbers exposed by Twilio data breach
The popular encrypted instant messaging service relies on a phone number to login, something which has drawn mixed reactions from users. A username and password system would be safer, in my opinion, as it would protect your privacy by not exposing your number to other users. But that's a different topic, let's focus on the issue at hand.
Since it uses a phone number login system, Signal relies on the SMS protocol to receive verification codes, and uses Twilio's servers for providing the codes. 2-factor authentication via SMS has long been criticized by security experts. It's not a very safe option, anyone who has access to your phone (and the SIM card with the registered number), can bypass the security layer. There are additional risks too, since SMS messages are not encrypted (plain text), the verification code can be intercepted by malware or hackers.
Using a local 2FA app like Aegis Authenticator for Android, or Raivo OTP for iOS, is a safer option, and in many ways the more convenient one too. Even Twilio's own 2FA app, Authy, is safe to use despite the parent company suffering a data breach, since the tokens are end-to-end encrypted before being uploaded to the cloud.
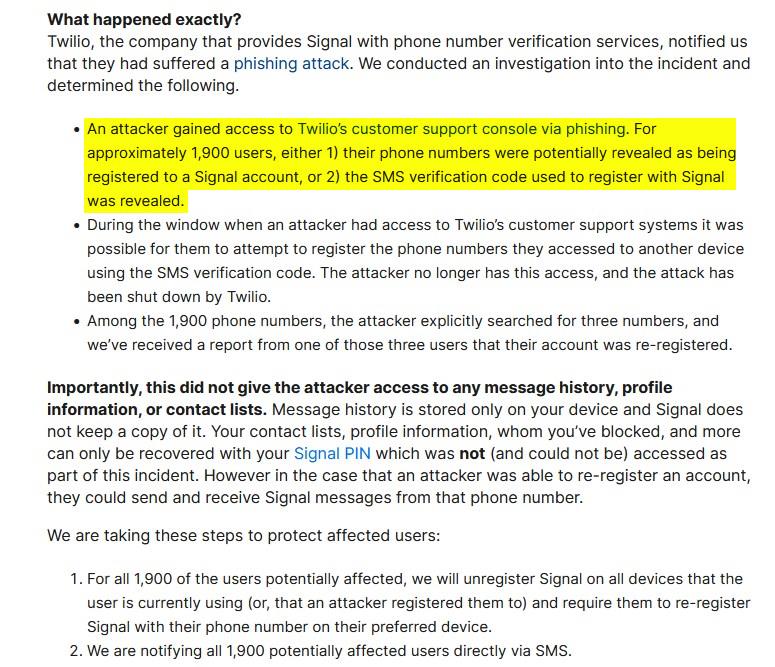
Signal says that the Twilio phishing attack exposed the phone numbers of around 1900 of the messaging service's users. While that may seem like a lot, the company says that it represents a very low percentage of its total users. Signal has reassured users that the data breach did not expose their personal data such as their message history, contact lists, profile information, blocked users, etc. So, how exactly are users affected?
Hackers could have gained access to the SMS verification code that was used to register Signal accounts. The attackers may have attempted to re-register a user's number on another device, or discovered that a number was tied to a Signal account. Twilio worked with service providers to shut down the attack vectors as soon as it discovered the attack and notified Signal about it, so while the threat has ended, there is a possibility that the exposed numbers were at risk before the issue had been resolved.
Signal says that the attacker searched for three numbers, and one of those users had reported that their account had been re-registered by someone else. That's why the company is reaching out to the other affected users, in order to prompt them to re-register Signal on their devices. You can refer to this support article for more details regarding the incident.
Meanwhile, Twilio has confirmed that approximately 125 of its users' data had been accessed by malicious actors for a limited time, and that it alerted them about it. The company states that there is no evidence that customer passwords, authentication tokens, or API keys were accessed by the attackers.
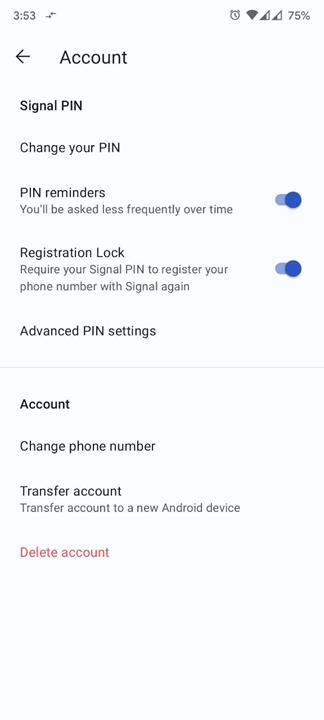
Signal is also encouraging users to enable registration lock on their Signal accounts to secure their accounts. You can do so from the Signal Settings (profile) > Account > Registration Lock. This will add an extra layer of security, i.e., the app will ask you to enter your Signal PIN to register the account again.





















May it’s time for ghacks to do another round up of similar apps and not sugarcoat it like many people do by gathering up a lazy list with no original thought outside of marketing fluff. Ghacks articles are usually pretty good.
I guess here is a chart that may give people an idea of a few of these apps. It appears to be a bit dated now as there are many more similar apps that have popped up over the years particularly of late but its still a decent enough chart for what they look at.
https://www.securemessagingapps.com/
Signal is a CIA tool, so imagine all the “signal protocol” apps that agencies have access to and people still use them, especially when you have to give your phone number away which pretty much is linked to you by ID or a personal document and you don’t even know if it is true they remove it from their server when you delete your account.
This was probably done in purpose then you blame Twilio and done, people will keep using their CIA made tool and keep blaming on the 3rd party. Like the people who think the are safe for using Tor, another US gov financed and made tool, the only good thing about Tor for them is that they can easily transfer their kiddies photos, while idiots host nodes for free giving the pervs more power.
Why do people even worry, I mean, Signal says they are the most private blablala messenger, I remember recently reading Moxie clown post about how Telegram wasn’t encrypted babla, well, seems like Telegram hasn’t had a problem like this ever, even if Telegram works like synching all conversations with photos and everything perfectly fine, unlike messengers like Signal that you only get after linking your device, so you would think the risk is higher in Telegram servers, but nah, some lame phishing attacks maybe but nothing directly related to Telegram.
Why on earth do these so called privacy apps need your phone number anyway. I feel as though tying your phone number that absolutely identifies you to an app built around being completely anonymous is a huge flaw.
The weakest link strikes again.
While arguably Signal should be more circumspect about choosing subcontractors, Twilio employees that clicked on the phishing text message should be downright ashamed. It’s their job isn’t it to be tech-savvy for an internet security firm like Twilio??
No matter what the non-implications for Authy are, I’ve deleted my Authy account and moved to Aegis. I can’t trust a firm that doesn’t even have the honesty to get in front of the issue, never mind how poor its training must be with it’s own staff on security.