Tor Browser's Connection Assist takes the frustration out of censorship circumvention
Tor Project announced the release of Tor Browser 11.5, the latest version of the open source web browser that is designed to help people circumvent censorship and stay anonymous.

It achieves this by routing network traffic through a series of Tor network nodes and limiting node information; this improves user privacy through anonymity and helps circumvent censorship. Some Internet resources may be blocked in specific regions or countries, and Tor Browser is a viable option to access these resources.
Tor Browser 11.5 is a major release that introduces the new Connection Assist feature, default HTTPS-only mode, and redesigned network settings.
Connection Assist
Tor project engineers began to improve the connection experience in Tor Browser 10.5, which was released last year. One of the main changes was the integration of the connection flow in the browser. Previously, users had to use Tor Launcher for that.
While that improved the process, it still required manual configuration, for example, to find out how to get Tor Browser working with Bridges to unblock its capabilities. Tor Network is blocked in several countries, including Russia, Belarus and China.
Connection Assist is a new automated feature that is designed to apply these configurations automatically for the user. The feature removes the manual configuration process from the equation in the best case, so that Tor Browser users can start browsing the Internet right away.
Connection Assist relies on a list that contains country-specific options. The list is downloaded and then used by Tor Browser.
Connection Assist works by looking up and downloading an up-to-date list of country-specific options to try using your location (with your consent). It manages to do so without needing to connect to the Tor Network first by utilizing moat – the same domain-fronting tool that Tor Browser uses to request a bridge from torproject.org.
HTTPS-only Mode Default
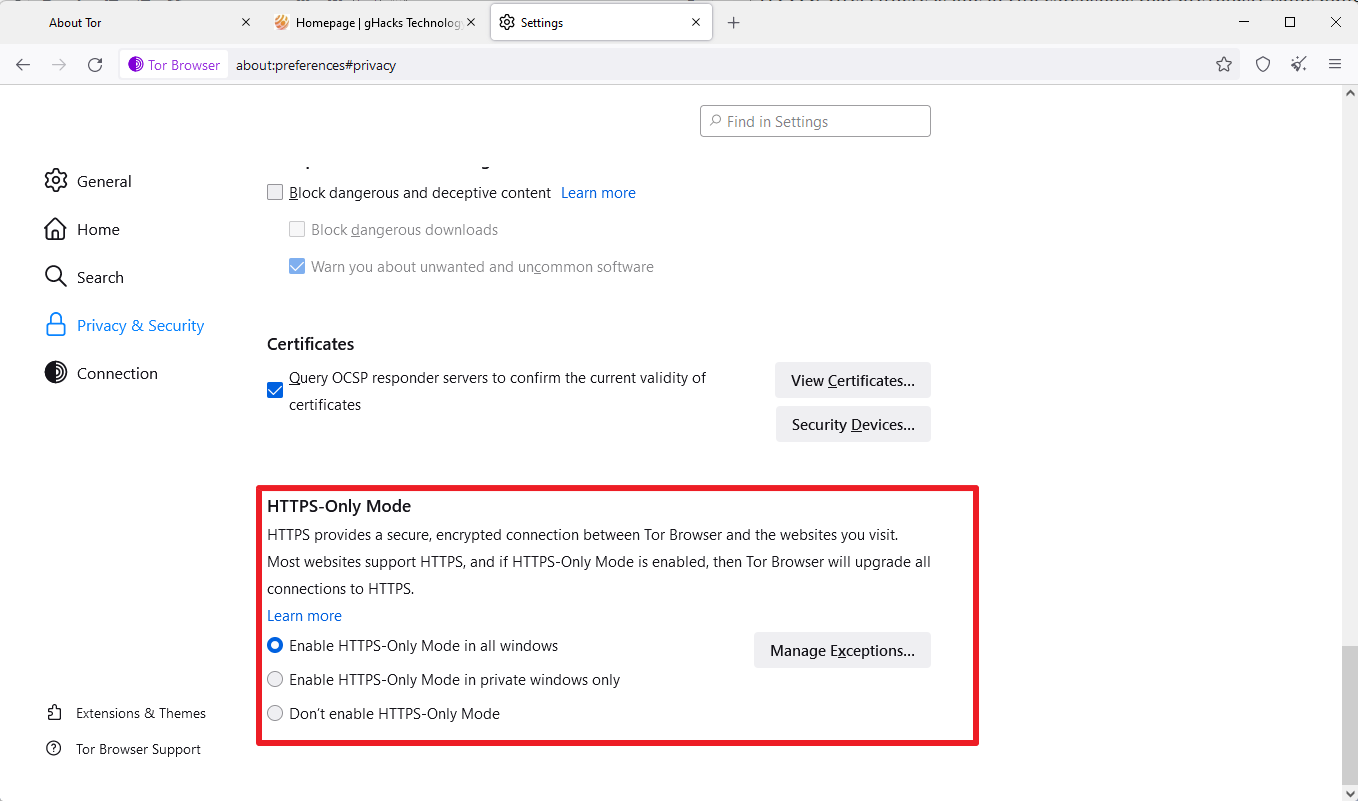
Tor Browser used HTTPS Everywhere previously to provide access to HTTPS resources whenever possible. Mozilla introduced support for HTTPS-Only in Firefox some time ago to give Firefox users an option to prioritize HTTPS over HTTP, or even block HTTP connections entirely.
Tor Browser, which is based on Firefox ESR, makes use of the HTTPS-Only mode now as well. Unlike Firefox, which has it disabled by default, it is enabled in Tor Browser. The HTTPS Everywhere extension is no longer bundled with Tor Browser as a consequence. The developer of the extension announced its retirement in 2021.
Sites that do not support HTTPS can still be accessed, as it is possible to add exceptions in the settings. Tor Browser users may disable HTTPS-Only mode in the settings by loading about:preferences#privacy as well, but this is not advised.
Improved Tor Network Settings
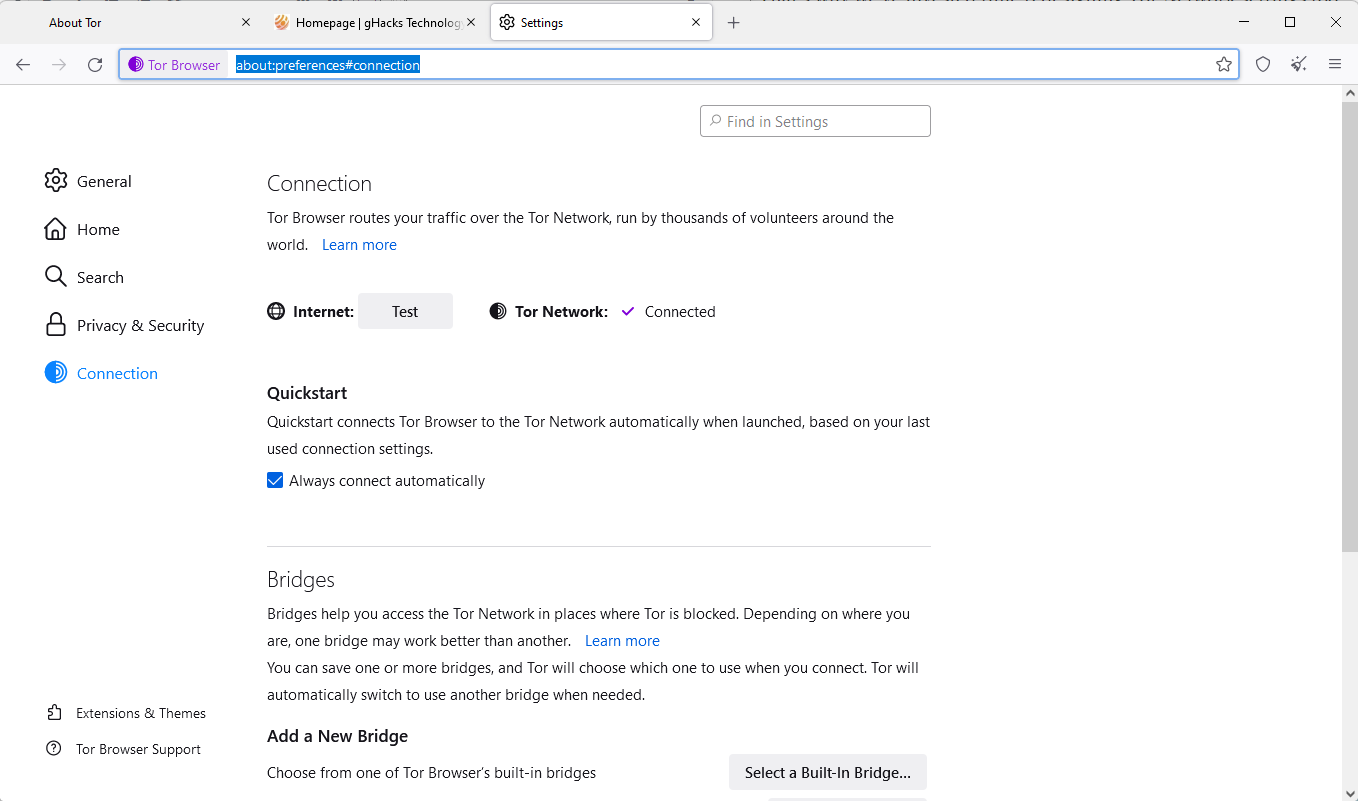
The network settings have undergone a redesign in the new Tor Browser release. Connection Assist should help many Tor Browser users automatically, but it still may be necessary to make manual adjustments. Also, some Tor users may want to make manual configuration changes.
Tor Network Settings has been renamed to Connection settings. These can be accessed by loading about:preferences#connection in the address bar.
The page displays the last connection status and an option to test the Internet connection without using Tor.
Managing bridges is now a streamlined process, and there are new bridge cards, which provide the most important details about a bridge on first glance.
Other changes in Tor Browser 11.5
Tor Browser comes with a list of bundled fonts. The new version includes more fonts to improve font display on the Internet.
Tor Browser for Android is lagging behind when it comes to features. Development focused on improving Tor for Android, for instance by fixing crashes and other issues that users experienced. The main goal is to catch up with Firefox for Android and to catch up with the desktop feature set eventually. For now, all features mentioned above are only available in the desktop version of Tor Browser.
Now You: do you use Tor Browser? What is your take on the changes?






















Browsers like Tor are no needed now. In addition many countries there is a struggle with Tor and it is impossible to connect to it. The Utopia P2P browser has anonymity at the same high level and now they have added a web proxy that is built right into the browser and you can connect proxy in 1 click.
Hi all
Just a small experiment with the very latest version of TOR (11.5) that I did which is interesting but I thought I would share with you.
I went to coveryourtracks.eff.org first and tested TOR, first on the Safest security level (as you can imagine everything came up top level) and then on the Safer security level (which, again, as expected came up that I was non-unique). No problems.
Then I went to amiunique.org and did the same two tests. Again on the Safest security level it came up that I was not unique, while on the Safer security level it came up that I was unique, despite not changing anything at all (except the security level), which I think was down to the fact that the top attributes user agent showed that I was using Windows 10, while the javascript attributes user agent below, on Safer security level, showed that I was using Linux, so I think that’s why it confused it and it put me down as unique.
Now the interesting bit.
I then installed Ublock Origin on TOR, added a few lists (like Anti-Facebook and all the Privacy lists), restarted TOR and did the two tests (on Safest and Safer security levels) again on both websites.
Incredibly the exact same results on both sites came up again, as they did above when Ublock Origin was not installed, with the exact same number of bits of information portrayed.
I just wonder if it is worth our while adding Ublock Origin to TOR after these results, as it does not, certainly on these two websites, seem to make a difference at all.
What do other readers think?
@Anonymous TOR
No. Do not modify your browser about:config or add extensions because then you are unique.
See most frequently asked questions:
“Should I install a new add-on or extension in Tor Browser, like AdBlock Plus or uBlock Origin?”
Tor Blog: Browser Fingerprinting: An Introduction and the Challenges Ahead
https://blog.torproject.org/browser-fingerprinting-introduction-and-challenges-ahead/
How do you use tor for specific websites that block access from the tor browser?
Onion Fruit Connect?
Not sure what it is or how it works.
Anyone?
I think Onion Fruit is to use TOR connection without TOR browser.
@Karen: And it’s closed-source:
“OnionFruit™ Connect is a closed-source program. One of the reasons for this is because we use proprietary assembles to create our UI (Telerik/PostSharp). We can’t share these so there is not much point in disclosing the majority of the source . . . .”
Nice improvement not only security wise.
But still I like next to using Thor even before I start up Thor, at the same time, a (Non log) VPN from a company who does not deliver my – /his data to the seven.
https://www.makeuseof.com/can-governments-see-vpn-use/
https://www.technadu.com/no-log-vpns-shared-data-with-governments/95041/
@Paul(us)
Unless you’re in a extremely repressive regime it’s totally pointless and you wouldn’t be posting here if you were.
Trying to be as secure and paranoid as you can be is more likely to arouse suspicion and that’s a very nice way to set yourself up as a target for surveillance.
Blend in.
So does Tor keep logs or not?
No, it doesn’t
https://support.torproject.org/misc/misc-6/
Hi Martin
Is it possible to completely remove the HTTPS Everywhere add-on in Tor Browser 11.5 for Android or is it just feasible to disable it?
And is there an option to turn on and off HTTPS-only mode as well?
Thx Uwe
Hi Uwe, there is only an option to disable HTTPS Everywhere; this should be sufficient. Once the new functionality lands in Tor Browser for Android, the extension is removed anyway.
HTTPS-Only Mode does not seem to be available yet in that version.
Thank you Martin for your claryfing response.
Best wishes
Uwe