- July 2020 Security Updates release notes
- List of software updates for Microsoft products
- List of the latest Windows Updates and Services Packs
- Security Updates Guide
- Microsoft Update Catalog site
- Our in-depth Windows update guide
- How to install optional updates on Windows 10
- Windows 10 Update History
- Windows 8.1 Update History
- Windows 7 Update History
Microsoft Windows Security Updates July 2020 overview
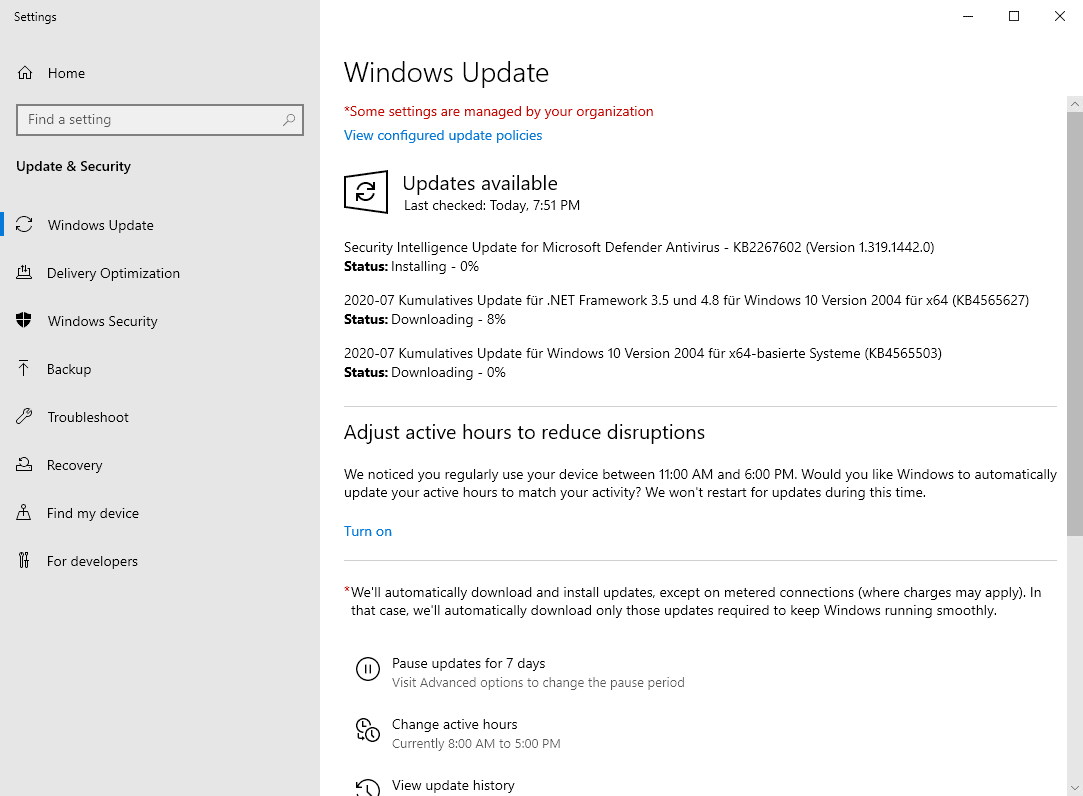
It is the second Tuesday of the month and that means that it is Patch Day for Windows and other Microsoft products. The Microsoft Windows July 2020 Patch Day brings security updates for all supported client and server versions of Microsoft's Windows operating system as well as other company products such as Microsoft Edge.
Our monthly overview provides you with detailed information about the updates that Microsoft released today.
You can download an Excel spreadsheet that contains a list of released security updates, and check out the updates released for any version of Windows. The overview includes download links, links to resources on Microsoft's support website, and known issues.
If you have missed out last month's Patch Day overview, check it out here.
Microsoft Windows Security Updates July 2020
Click on the following link to download the July 2020 spreadsheet to your system. It lists released security updates of the July 2020 Patch Day. Click on the following link to start the download: microsoft-windows-updates-july-2020
Executive Summary
- Microsoft released updates for all client and server versions of the Windows operating system that it supports.
- Updates are also available for products such as Windows Defender, Internet Explorer, Microsoft OneDrive, Microsoft Edge, Microsoft Office, Visual Studio and Skype for Business.
Operating System Distribution
- Windows 7Â Â (extended support only): 35 vulnerabilities: 6 critical and 29 important
- CVE-2020-1374 | Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2020-1409 | DirectWrite Remote Code Execution Vulnerability
- CVE-2020-1410 | Windows Address Book Remote Code Execution Vulnerability
- CVE-2020-1421 | LNK Remote Code Execution Vulnerability
- CVE-2020-1435 | GDI+ Remote Code Execution Vulnerability
- CVE-2020-1436 | Windows Font Library Remote Code Execution Vulnerability
- Windows 8.1: 40 vulnerabilities: 6 rated critical and 34 rated important
- same as Windows 7
- Windows 10 version 1803: 78 vulnerabilities: 6 critical and 72 important
- CVE-2020-1374 | Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2020-1409 | DirectWrite Remote Code Execution Vulnerability
- CVE-2020-1410 | Windows Address Book Remote Code Execution Vulnerability
- CVE-2020-1421 | LNK Remote Code Execution Vulnerability
- CVE-2020-1435 | GDI+ Remote Code Execution Vulnerability
- CVE-2020-1436 | Windows Font Library Remote Code Execution Vulnerability
- Windows 10 version 1809: 81 vulnerabilities: 4 critical and 78 important
- same as Windows 10 version 1803
- Windows 10 version 1903: 85 vulnerabilities: 5 critical and 73 important
- same as Windows 10 version 1803
- Windows 10 version 1909:Â
- same as Windows 10 version 1803
- Windows 10 version 2004:
Windows Server products
- Windows Server 2008 R2 (extended support only):Â 42 vulnerabilities: 13 critical and 29 important
- same as Windows Server 2016
- Windows Server 2012 R2: 48 vulnerabilities: 13 critical and 35 important.
- same as Windows Server 2016
- Windows Server 2016: 70 vulnerabilities: 13 critical and 57 important.
- CVE-2020-1032 | Hyper-V RemoteFX vGPU Remote Code Execution Vulnerability
- CVE-2020-1036 | Hyper-V RemoteFX vGPU Remote Code Execution Vulnerability
- CVE-2020-1040 | Hyper-V RemoteFX vGPU Remote Code Execution Vulnerability
- CVE-2020-1041 | Hyper-V RemoteFX vGPU Remote Code Execution Vulnerability
- CVE-2020-1042 | Hyper-V RemoteFX vGPU Remote Code Execution Vulnerability
- CVE-2020-1043 | Hyper-V RemoteFX vGPU Remote Code Execution Vulnerability
- CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability
- CVE-2020-1374 | Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2020-1409 | DirectWrite Remote Code Execution Vulnerability
- CVE-2020-1410 | Windows Address Book Remote Code Execution Vulnerability
- CVE-2020-1421 | LNK Remote Code Execution Vulnerability
- CVE-2020-1435 | GDI+ Remote Code Execution Vulnerability
- CVE-2020-1436 | Windows Font Library Remote Code Execution Vulnerability
- Windows Server 2019: 83 vulnerabilities: 7 critical and 77 are important
- CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability
- CVE-2020-1374 | Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2020-1409 | DirectWrite Remote Code Execution Vulnerability
- CVE-2020-1410 | Windows Address Book Remote Code Execution Vulnerability
- CVE-2020-1421 | LNK Remote Code Execution Vulnerability
- CVE-2020-1435 | GDI+ Remote Code Execution Vulnerability
- CVE-2020-1436 | Windows Font Library Remote Code Execution Vulnerability
Other Microsoft Products
- Internet Explorer 11: 2 vulnerability: 1 critical, 1 important
- CVE-2020-1403 | VBScript Remote Code Execution Vulnerability
- Microsoft Edge:Â 2 vulnerabilities: 0 critical, 2 important
- Microsoft Edge on Chromium:
- see here (latest security patches from the Chromium project)
Windows Security Updates
Windows 7 SP1 and Windows Server 2008 R2
Fixes and improvements
- Security Updates
Windows 8.1 and Server 2012 R2
Fixes and improvements
- Security Updates
Windows 10 version 1803
- Support page: KB4565489Â
Fixes and improvements
- Fixed an issue that might cause lsass.exe to fail with the error "A critical system process, C:\WINDOWS\system32\lsass.exe, failed with status code c0000008. The machine must now be restarted."
- Fixed an issue that prevented some applications from printing large file documents or documents with graphics.
- Security updates.
Windows 10 version 1809
- Support page: KB4558998
Fixes and improvements
- Fixed an issue when loading Browser Helper Objects in IE Mode in Microsoft Edge.
- Fixed an issue that might cause lsass.exe to fail with the error "A critical system process, C:\WINDOWS\system32\lsass.exe, failed with status code c0000008. The machine must now be restarted."
- Fixed an issue that prevented some applications from printing large file documents or documents with graphics.
- Security updates.
Windows 10 version 1903 and 1909
- Support page: KB4565483
Fixes and improvements
- Same as Windows 10 version 1809
Windows 10 version 2004
- Support page: KB4565503Â
Fixes and improvements
- Fixed issues in certain apps that use the ImeMode property to control the Input Method Editor mode.
- Fixed an issue that prevented changing the system local on Server Core platforms using PowerShell.
- Fixed a game and app distortion issue when switching from full screen mode to window mode, or resizing windowed mode windows.
- Fixed a OneDrive app connecting issue.
- Fixed an issue that might cause lsass.exe to fail with the error "A critical system process, C:\WINDOWS\system32\lsass.exe, failed with status code c0000008. The machine must now be restarted."
- Fixed an issue that prevented some applications from printing large file documents or documents with graphics.
- Security updates.
Other security updates
KB4565479 -- 2020-07 Cumulative Security Update for Internet Explorer
KB4565529 -- 2020-07 Security Only Quality Update for Windows Server 2008
KB4565535 -- 2020-07 Security Only Quality Update for Windows Embedded 8 Standard and Windows Server 2012
KB4565536 -- 2020-07 Security Monthly Quality Rollup for Windows Server 2008
KB4565537 -- 2020-07 Security Monthly Quality Rollup for Windows Embedded 8 Standard and Windows Server 2012
KB4565513 -- 2020-07 Cumulative Update for Windows 10 Version 1507
KB4565499 -- 2020-07 Cumulative Update for Windows 10 Version 1703
KB4565508 -- 2020-07 Cumulative Update for Windows 10 Version 1709
.NET Framework
KB4565577 -- 2020-07 Security Only Update for .NET Framework 3.5 for Windows Embedded 8 Standard and Windows Server 2012
KB4565578 -- 2020-07 Security Only Update for .NET Framework 2.0, 3.0 for Windows Server 2008
KB4565579 -- 2020-07 Security Only Update for .NET Framework 3.5.1 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4565580 -- 2020-07 Security Only Update for .NET Framework 3.5 for Windows 8.1 and Windows Server 2012 R2
KB4565581 -- 2020-07 Security Only Update for .NET Framework 4.5.2 for Windows 8.1 and Windows Server 2012 R2
KB4565582 -- 2020-07 Security Only Update for .NET Framework 4.5.2 for Windows Embedded 8 Standard and Windows Server 2012
KB4565583 -- 2020-07 Security Only Update for .NET Framework 4.5.2 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4565584 -- 2020-07 Security Only Update for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded 8 Standard and Windows Server 2012
KB4565585 -- 2020-07 Security Only Update for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 8.1 and Windows Server 2012 R2
KB4565586 -- 2020-07 Security Only Update for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4565587 -- 2020-07 Security Only Update for .NET Framework 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4565588 -- 2020-07 Security Only Update for .NET Framework 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4565589 -- 2020-07 Security Only Update for .NET Framework 4.8 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4565610 -- 2020-07 Security and Quality Rollup for .NET Framework 3.5 for Windows Embedded 8 Standard and Windows Server 2012
KB4565611 -- 2020-07 Security and Quality Rollup for .NET Framework 2.0, 3.0 for Windows Server 2008
KB4565612 -- 2020-07 Security and Quality Rollup for .NET Framework 3.5.1 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4565613 -- 2020-07 Security and Quality Rollup for .NET Framework 3.5 for Windows 8.1 and Windows Server 2012 R
KB4565614 -- 2020-07 Security and Quality Rollup for .NET Framework 4.5.2 for Windows 8.1 and Windows Server 2012 R2
KB4565615 -- 2020-07 Security and Quality Rollup for .NET Framework 4.5.2 for Windows Embedded 8 Standard and Windows Server 2012
KB4565616 -- 2020-07 Security and Quality Rollup for .NET Framework 4.5.2 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4565621 -- 2020-07 Security and Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded 8 Standard and Windows Server 2012
KB4565622 -- 2020-07 Security and Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 8.1 and Windows Server 2012 R2
KB4565623 -- 2020-07 Security and Quality Rollup for .NET Framework 4.6 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4565634 -- 2020-07 Security and Quality Rollup for .NET Framework 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4565635 -- 2020-07 Security and Quality Rollup for .NET Framework 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4565636 -- 2020-07 Security and Quality Rollup for .NET Framework 4.8 for Windows Embedded Standard 7 and Windows Server 2008 R2
KB4566466 -- 2020-07 Security Only Update for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4566467 -- 2020-07 Security Only Update for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4566468 -- 2020-07 Security Only Update for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4566469 -- 2020-07 Security Only Update for .NET Framework 2.0, 3.0, 4.5.2, 4.6 for Windows Server 2008
KB4566517 -- 2020-07 Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4566518 -- 2020-07 Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4566519 -- 2020-07 Security and Quality Rollup for .NET Framework 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4566520 -- 2020-07 Security and Quality Rollup for .NET Framework 2.0, 3.0, 4.5.2, 4.6 for Windows Server 2008
KB4565625 -- 2020-07 Cumulative Update for .NET Framework 3.5 and 4.7.2 for Windows Server 2019 and Windows 10 Version 1809
KB4565627 -- 2020-07 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server, version 2004 and Windows 10 Version 2004
KB4565628 -- 2020-07 Cumulative Update for .NET Framework 4.8 for Windows Server 2016 and Windows 10 Version 1607
KB4565629 -- 2020-07 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1703
KB4565630 -- 2020-07 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1709
KB4565631 -- 2020-07 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1803 and Windows Server 2016 (1803)
KB4565632 -- 2020-07 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server 2019 and Windows 10 Version 1809
KB4565633 -- 2020-07 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server, version 1909, Windows 10 Version 1909, Windows Server 2019 (1903), and Windows 10 Version 1903
KB4566516 -- 2020-07 Cumulative Update for .NET Framework 3.5, 4.7.2 and 4.8 for Windows Server 2019 and Windows 10 Version 1809
Servicing Stack Updates
KB4558997 -- 2020-07 Servicing Stack Update for Windows Server 2019 and Windows 10 Version 1809
KB4565353 -- 2020-07 Servicing Stack Update for Windows Server 2008
KB4565354 -- 2020-07 Servicing Stack Update for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4565551 -- 2020-07 Servicing Stack Update for Windows 10 Version 1703
KB4565552 -- 2020-07 Servicing Stack Update for Windows 10 Version 1803
KB4565553 -- 2020-07 Servicing Stack Update for Windows 10 Version 1709
KB4565554 -- 2020-07 Servicing Stack Update for Windows Server, version 2004, Windows Server, version 1909, Windows 10 Version 1909, Windows Server 2019 (1903), and Windows 10 Version 1903
KB4565912 -- 2020-07 Servicing Stack Update for Windows Server 2016 and Windows 10 Version 1607
KB4566425 -- 2020-07 Servicing Stack Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2
KB4566426 -- 2020-07 Servicing Stack Update for Windows Embedded 8 Standard and Windows Server 2012
KB4565911 -- 2020-07 Servicing Stack Update for Windows 10 Version 1507
KB4566785 -- 2020-07 Servicing Stack Update for Windows Server, version 2004 and Windows 10 Version 2004
Known Issues
Windows 7 SP1 and Windows Server 2008 R2
Windows 8.1 and Windows Server 2012 R2
- Certain operations such as rename may fail on Cluster Shared Volumes. The error received is "STATUS_BAD_IMPERSONATION_LEVEL (0xC00000A5)" in that case.
- Solution 1: Run the operation from a process with elevated rights.
- Solution 2: Perform the operation from a node that does not have CSV ownership.
Windows 10 version 1809
- Devices with some Asian language packs may receive error "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND".
- Solution 1: Uninstall and reinstall any language packs that were installed recently. Check for updates afterwards.
- Solution 2: Reset this PC.
Windows 10 version 1903 and 1909
- Internet access may not be available after installing this update on a device with a WWAN LTE modem.
- Microsoft is working on a solution.
Windows 10 version 2004
- Some apps, such as Microsoft Excel, may throw errors for for users of the Microsoft Input Method Editor for Chinese and Japanese.
Security advisories and updates
ADV200008 | Microsoft Guidance for Enabling Request Smuggling Filter on IIS Servers
Non-security related updates
Microsoft Office Updates
You find Office update information here.
How to download and install the July 2020 security updates

Security updates are released via Windows Update and other update management systems such as WSUS. Administrators may download updates manually as well to install them directly.
Note: We recommend that systems are backed up fully before updates are installed.
The following instructions guide you through the process of checking for updates via Windows Update:
- Open the Start Menu of the Windows operating system, type Windows Update and select the result.
- Select check for updates in the application that opens. Updates may be installed automatically when they are found or offered by Windows; this depends on the operating system and version that is used, and update settings.
Direct update downloads
Windows 7 and Server 2008 R2
- KB4565524 -- 2020-07 Security Monthly Quality Rollup for Windows 7
- KB4565539 -- 2020-07 Security Only Quality Update for Windows 7
Windows 8.1 and Windows Server 2012 R2
- KB4565541 -- 2020-07 Security Monthly Quality Rollup for Windows 8.1
- KB4565540 -- 2020-07 Security Only Quality Update for Windows 8.1
Windows 10 (version 1803)
- KB4565489 -- 2020-07 Cumulative Update for Windows 10 Version 1803
Windows 10 (version 1809)
- KB4558998 -- 2020-07 Cumulative Update for Windows 10 Version 1809
Windows 10 (version 1903)
- KB4565483 -- 2020-07 Cumulative Update for Windows 10 Version 1903
Windows 10 (version 1909)
- KB4565483 -- 2020-07 Cumulative Update for Windows 10 Version 1909
Windows 10 (version 2004)
- KB4565503 -- 2020-07 Cumulative Update for Windows 10 Version 2004
Additional resources






















from https://support.microsoft.com/en-my/help/4566517/kb4566517 via https://www.askwoody.com/forums/topic/recent-win7-kb4566517-update-failed-to-install/#post-2281342
“[…] On systems with .NET Framework 4.5.2 and above, you may observe a patch install failure with Error: 0x643, or error code 1603, when attempting to install this update on a system with a proper Extended Security Update (ESU) license installed.
We are working on a resolution and will provide an update in an upcoming release. […]â€
Hi,
For Windows 2012 R2 server, please advise on whether we need to install KB4565540 and KB4565541? or just KB4565541 monthly rollup is sufficient?
For those people for whom the update was not successful or caused issues, I would urge you to consider getting an external hard drive and imaging your hard drive before any Patch Tuesday update. I had a client who refused to take this advice when upgrading from Windows 7 to Windows 10, and it was not fun to deal with the aftermath. I use Macrium Reflect, but there are many good imaging programs out there. Many of which are free to use for personal use. The key thing is to make an image, not a clone and then create a bootable usb drive if the company offers such a tool. Hope this helps.
I noticed on the two machines I updated yesterday & today there’s no MSRT (Malicious Software Removal Tool) this time around, anyone know why?
Windows 8.1 x86/x64 comes with .NET 4.5.1 by default, I’ve never needed to update .NET as our installed programs don’t require it.
Martin, I have a couple of questions:
Why isn’t there a security update for .NET 4.5.1 as per ALL the other .NET versions?
Has it been overlooked by MS or is it simply not affected by the remote code execution vulnerability?
And before anyone mentions ‘update to .NET 4.5.2 or above’, I won’t as our systems are not asking for it and is obviously not required.
to answer my own question; it was depreciated:
https://devblogs.microsoft.com/dotnet/support-ending-for-the-net-framework-4-4-5-and-4-5-1/
Looks like .NET 4.5.2 upgrade :(
news from abbodi from askwoody.com (https://www.askwoody.com/forums/topic/standalone-installer-script-for-windows-7-esu-regardless-the-license/#post-2280539)
“The ESU_LOCK workaround is removed and no longer working”
Windows 8.1 with Classic Shell is workable, and causes less of a headache. It’s certain that MS will continue to break ESU hacks.
‘Keep it simple’ obviously isn’t Microsoft’s catch-phrase where Windows 10 is concerned.
Computers were once heralded as probably the greatest technical tool for mankind’s progress. Seems to me much of mankind is now so preoccupied with the ongoing task and convolutions of keeping said computers updated, that mankind’s technical progress has slowed greatly since the introduction of W10.
;-)
Microsoft announced a sever level 10, Server DNS security bug CVE-2020-1350 – Windows DNS Server Remote Code Execution Vulnerability
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350
just an hour ago an ex-collegue called me and said to NOT install on DC with DNS role until patch of the patch is released.
just saying 0-o
This is a must have patch
https://www.askwoody.com/2020/faq-the-windows-dns-server-security-hole-cve-2020-1350-from-a-normal-users-perspective/
This update ….. up mi PC. My proccesor i7 6700hq is stuck at 0.80 ghz. What the hell, what do I do now!!!!????!!!!
BypassESU v7 still works with Windows 7 Professional x86 and x64, updated without a hitch. If you use Avast, disable it before updating. 2004, zero issues so far..
I used your method, was able to install KB4566517, so thanks I guess…
Why would you install a virus such as Avast anyways?
Thanks Martin for all the great info. Win 8.1 Monthly Rollup, Servicing Stack and .Net Rollup (KB4566519) all installed without issue (Macrium image created first). All telemetry tasks/services are still disabled and everything appears to be working normally.
KB4565636 should say “Security and Quality Rollup for .NET Framework 4.8 for Windows 7 SP1 and Windows Server 2008 R2 SP1”
Uneventfully I went from *.900 to Microsoft Windows [Version 10.0.18363.959]. I correctly am still not offered 2004.
Updated two LTSC machines and one Server 2019. All well :)
SSU: https://www.catalog.update.microsoft.com/Search.aspx?q=KB4558997
Update pack (cumulative): https://www.catalog.update.microsoft.com/Search.aspx?q=KB4558998