How to prevent your ISP from snooping on you
Internet Service Providers may be able to sell your web history in the United States without you giving your consent. The new ruling passed the US Senate and the House of Representatives already, and the last thing standing in its way is the President of the United States.
Assuming that the change in privacy rules will pass, ISPs may sell your browsing data to third-parties. Since you interact with the ISP directly when you are using the Internet, data that may be included in the package may include your browsing history, general usage information, location information, interests (based on sites), searches, and more.
Since you may not want the data to be sold in first place, one of the best courses of action is to prevent the ISP from knowing much about what you do online in first place.
How that is done? Glad you asked.
Encryption is the way to go
The best option that you have, without doubt, is to use encryption. A VPN service is ideal, as it encrypts traffic between your computer and the Internet destinations. While your ISP sees that connection, it won't know anything about what happens afterwards.
This means that the ISP does not know which sites you visit on the Internet, what you do on those sites, which searches you run, or what your interests are other than that you are using a VPN to protect your Internet data stream.
Note: Depending on the VPN, you may need to change DNS servers as well to avoid that the look ups use the ISPs DNS server. Good VPN services use their own DNS servers, and/or offer DNS leak protection. It is suggested not to use DNS servers from a company that either admitted openly to selling usage data, or is a known advertising company.
You may want to check out FreeDNS, they state no registration and logging on their website, Verisign Public DNS, also with the promise that they don't sell your public DNS data to third-parties or redirect queries to ads. (If you know of others, let us know in the comment section below please). Note End
While you can use free VPN services, most do sell your data, anonymously or not. It is advised therefore to get a paid VPN service instead.
You can check out Ghacks Deals for VPN service offers, or use the Internet for that. A service that I can recommend is Private Internet Access. You can get a 2-year subscription for $59.95 currently on Ghacks Deals.
If you are on a tight budget, you may want to consider using Opera's built-in browser VPN instead. The main advantage here is that it is free and easy to setup as you only need to flip a switch. Opera VPN is available for desktop browsers, but also for Opera on iOS and Android.
The downside is that you need to take Opera's current situation into account. The browser was sold to a Chinese consortium, and the VPN is managed by SurfEasy, a Canadian company. Canada is part of Five Eyes, an intelligence alliance that Australia, Canada, New Zealand, UK and the US are members of.
Another downside is that Opera's VPN protects only the web browser but not other traffic. If you use Netflix's app or other applications, P2P, FTP, email desktop clients, chat programs, or any other program that runs outside of the browser, you need to be aware of that those are not protected.
Additional tips
Another thing that you may want to do is connect to HTTPS versions of sites whenever possible. The HTTPS connection is encrypted. This means that your ISP does not know what you do on the site, only that you connected to it.




















How about Kasdpersky Secure connection from Kaspersky Internet Security 2018. any insight on this ? any info/warnings ?
I wanna be able to use my computer without the blog owner(s) knowing my ISP address. Where do I go to be able to have it look like my computer is not my computer? I wasn’t sure if the information in the article applied to the particulars of what I am looking for. Please explain.
Your computer’s IP, which is hidden with a VPN, is not its only signature. So called fingerprinting is increasingly elaborated which means that if you hide your computer’s true IP (with a dynamic IP provided by a VPN) without taking care of your fingerprints, a site will not only ne able to recognize you (that is: your computer) bit moreover will know that your computer is hiding itself.
Have a try with this test page :
‘Cross-browser fingerprinting test 2.0’ over at [https://fingerprint.pet-portal.eu/]. A, evercookie script is used. Of course if you block javascript then whatever tracking is seriously limited (as well as 99% of sites readability), or if, with a blocker application you refuse, say :
/evercookie.$important
/evercookie/*$important
/evercookie_$important
then sites naive enough to use the evercookie script without changing its name will defeat when using that tracking method …
What I mean is that, either dive into the ultra elaborated universe of a context such as ‘Tails’ either gently slap the trackers with best known “soft” methods and remain convinced that doing so hardly hides the feet only of she who wished to be entirely dressed… and is never a Knock-Out. That’s how it is : Web tracking, be it by your computer’s manufacturer, be it by your Web applications (first of, your browser); be it by advertisement companies, social sites, ISPs, governments … it’s like good and bad guys united to track you (sometimes united even otherwise!).
That’s for tracking the computer. Now, thinks the smart guy, maybe they know it’s the same computer but what they can’t know is who’s using it, right? May be wrong with latest fingerprinting processes which analyze what is specific to each of us, such as the way, the speed of typing … but that’s another extra level, the ultimate so to say.
Good luck :)
sites using
@ Carol Joy
Different solutions, in order of difficulty :
– Use the so-called VPN mode of the Opera browser (which is not really a VPN, but more of a proxy).
– Use a full-fledged VPN (free VPNs are usually discouraged because it is feared that they tend to sell your data, but they will still hide your ISP from the site you visit).
– Use Tor.
– Use Tails (overkill if you just want to hide your IP from a blog).
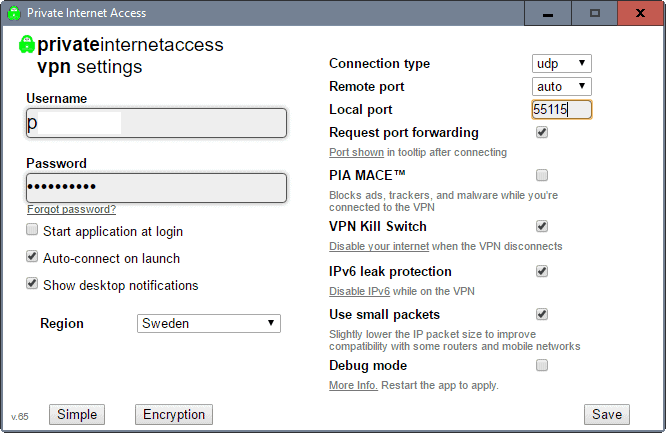
Hey Martin I use Private Internet Access. I was wondering about the “Local Port” number you have in the picture above: 55115. Could you explain that setting to me please? How I can utilize that feature?
-Thank You
Sam
It is just the port that PIA runs on locally. I randomize the port regularly, but there is nothing else to it.
Question, how good would the TOR Browser be for use against this ISP BS ?
Also is TOR good for using at public WiFi hot spots ? – This one i read somewhere.
VPN providers may not log or sell your data but can the same can be said about the ISP’s of VPN providers?
Isn’t the encryption happening only between you and VPN Provider? Wouldn’t the ISP’s of VPN providers able to see unsure http traffic? I could be wrong ofc.
Why isn’t my comment showing up or being approved ?
Landed in spam, not it is live.
Alright, i thought that could be it. I figured someone might find those links a good read, plus someone might answer those questions.
@Lausanne if you think it’s funny you have a real problem!
@areader. I read the stuff you are having difficulties with and I have to agree with Lausanne. Sorry mate, it hate to be so blunt, but I think the problem is yours and only yours. If you don’t get it don’t blame it on others.
I use Symantec/Norton DNS (all platforms)
i’ll try and post this again. Here are some helpful Links.
https://torrentfreak.com/vpn-services-anonymous-review-2017-170304/ – Newest article posted on March 4, 2017
https://torrentfreak.com/vpn-anonymous-review-160220/ – Last years posted on December 20, 2016
https://torrentfreak.com/which-vpn-services-take-your-anonymity-seriously-2014-edition-140315/ – 2014’s
Here’s another article one might want to read – https://torrentfreak.com/vpn-providers-no-logging-claims-tested-in-fbi-case-160312/
Question, how good would the TOR Browser be for use against this ISP BS ?
Also is TOR good for using at public WiFi hot spots ? – This one i read somewhere.
1 – Is this a solution to Trump signing away your digital privacy? We give Invizbox Go a go.
Let’s go over the pros and cons: https://www.theregister.co.uk/2017/03/30/invizbox_solution_for_digital_privacy/
2 – Using a VPN Sucks: https://motherboard.vice.com/en_us/article/using-a-vpn-sucks
Some excerpts:
“Whenever I actually had to get something done, I turned off the VPN.”
“I don’t blame either Private Internet Access or Freedome for the issues I faced. Both VPNs were leaps and bounds better than ones I’ve tried in the past. But VPNs are primarily used by people who want to protect themselves in very specific and temporary circumstances. They’re great for encrypting traffic on public WiFi networks, such as at the airport or at Starbucks. They’re great for journalists and security researchers who want to hide their identity while reporting. They’re terrible for always-on, regular-ass internet usage.”
“The takeaway here is that no VPN is going to get widespread adoption from the average internet user, nor should it. We’ve repeatedly seen that given the choice between privacy and convenience, most people will choose convenience.”
“Quite simply, it’s bullshit that the average internet user has to even think about using a VPN.”
I just installed Opera with the built in VPN feature on my desktop and surface pro. I tried installing it on my Android phone but it’s not the same experience (Opera Mini?). I only use Opera for casual web browsing. Any financial transactions are still done through a locked down Firefox. I do like Opera for browsing and surfing the internet. It’s not a perfect solution but it’s better than nothing to keep marketers from profiting. I really enjoy this site and will visit it often!
@ areader
I don’t get it. What’s your prob with a funny & sally reply to an unproven rant ? Actually, your whining makes me sick.
“Another thing that you may want to do is connect to HTTPS versions of sites whenever possible. The HTTPS connection is encrypted. This means that your ISP does not know what you do on the site, only that you connected to it.”
Great tip….but a bit ironic seeing as Ghacks.net doesn’t support HTTPS connections itself.
We support both http and https, give it a try.
@Otkon,
1- If ‘HTTPS Everywhere’ (HE) opens gHacks called via https with http it may be that it has previously logged gHacks as http only. If so, open HE and remove gHacks from the ‘Whitelisted domains’ (http only)
2- Once above checked/done, I agree that I’ve noticed that HE will not open http gHacks as https when it should, when it always opens a site via https first and returns to http only if https fails. This is odd. HE meets a situation with gHacks which seems to say “no https here’ even though https is available. Really odd.
3- To have HE always open gHacks via https two conditions:
– gHacks must not be in HE’ http only whitelist ;
– gHacks must be in HE’s https only blacklist.
Otherwise, HE or not, gHacks via https works fine now.
You may think you support it but “giving it a try” by entering https://www.ghacks.net into the URL will redirect to the insecure http *UNLESS* HTTP Everywhere is set to “block all unencrypted requests”. Why is the site not HTTPS by default?
You sure do!
COMODO CA Limited
Validity : 20/03/2017 – 20/04/2018
…
Access is slightly slower than with http (which is very fast) but runs nicely.
Now I can tell all my secrets without fearing they be heard :)
Are we to believe that the VPN providers were not among the ones lobbying for this law change or not-change, whatever?
ISPs will likely lose some customers where that is even possible but yeah they can make a few more bucks now, but aren’t VPN providers some of the ones who profit the most by this change? It seems a bit fishy to me. Hopefully the rest of the world will not follow the US’s bad example, but I’m not too hopeful because the US can be quite “convincing” if you know what I mean :(
For years (if not decades), there was a very popular meme (before memes even existed), that since viruses were a boon to anti-virus software publishers, obviously the whole virus phenomenon was the result of a conspiracy by anti-virus software publishers.
Now at last, there’s nobody left pretending (it seems to me) that it’s Avast, Kaspersky and Norton which actually write malware and release it into the wild. The criminals who built this industry are so obvious and powerful that they can’t be ignored anymore.
Are we really willing to go again down the route of dumb assumptions with VPN providers now ?
I you really want to invoke the political and economic influence of some involved parties, that would be American communication providers, which are far more powerful than VPN providers. The latter are, often, not American to begin with, and they represent altogether a tiny, tiny business niche with no weight to speak of.
Almost nobody uses a VPN provider. Everybody uses a telco / Internet provider. Not everybody in the world is a geek. As a matter of fact, almost nobody is.
That would be a win-win scenario for ISPs and VPNs!
Oops, looks like I forgot the users :)
try joining the crowdfunding campaign to buy the law makers and trumps internet data the bigger it gets the more chances of success
Was this article just a commercial ? If so sad.
While you can use free VPN services, most do sell your data, anonymously or not. It is advised therefore to get a paid VPN service instead.
You can check out Ghacks Deals for VPN service offers, or use the Internet for that. A service that I can recommend is Private Internet Access. You can get a 2-year subscription for $59.95 currently on Ghacks Deals.
Whatever browser I use, I make sure to use all the best privacy addons, ublock origin, ssl validation, disable wrtc, etc. There are others who know more or have more detailed info on that.
Then I take two other steps.
1. Use Simple DNSCrypt a windows build version of DNSCrypt at https://simplednscrypt.org/ it provides dns encryption from my end.
2. Use a DNS Service that does not log queries, of course there is no 100% way to verify any of this, but enough layers, and I’ll have reasonable protection. I use Open-Nic. Of course there are others.
I do not use VPN’s because they also tag that your using a vpn, and that can make you more visible, even if the exact actions your taking online are not.
There’s was an interesting academic study performed back in 2015 regarding VPNs which is worth a read.
I was proposing to signup myself to VyprVPN after reading it and coming to the conclusion that they were the best of the bunch. But then I discovered they don’t accept Mastercard for some unknown reason and I don’t have VISA.
My second choice was Astril mentioned at the top of page 88 as the only VPN which uses the same IP address for both the DNS server and the VPN tunnel gateway which makes it impossible for a hacker to produce a split tunnel and fool the victim into believing that their connection is encrypted according to the study. However, according to a number of VPN review sites they keep the last 20 connection logs which isn’t very encouraging.
Here’s the link to the study: https://www.eecs.qmul.ac.uk/~hamed/papers/PETS2015VPN.pdf
Don’t worry, be happy. What makes you think all of the information going through the lines is going to somehow reflect on your one or two hours of surfing? Total paranoia.
Tools like Lantern, Book VPN, purchase a cheap VPS w/ SSH, Nord, whatever. AWS–another free option. Use History Scrambler; works like a charm. Tor works fine. What would really help is if users allowed their own computers to be nodes for Tor, then use Tor rather than their own IP. That way Tor would become extremely fast with all of the additional nodes and peace and happiness will reign again. Maybe let’s all just move someplace where Internet and mobile this or that is a pointless tool and learn how to fish.
The old Psiphon can help; Epic Privacy browser much better than Opera; SSTP. Cocoon browser. MAC spoofing. Magellan. Alkasir.
What about Tor, instead of a VPN ?
Anybody using the latest build of Linux Mint or Ubuntu and a VPN may want to check for DNS leaks. The latest Network Manager build is buggy and leaks the DNS like Niagra Falls. The fix is to downgrade Network Manager to 1.22 anf lock it from upgrading until the build is fixed.
That’s interesting – thanks for sharing. I haven’t noticed any leaks with Mint 18 (I periodically use dnsleaktest.com as a test). But you got me wondering what version of Network Manager I’ve got installed. Here’s what I see:
network-manager 1.2.6
network-manager-openvpn 1.1.93
network-manager-gnome 1.2.6
network-manager-openvpn-gnome 1.1.93
This is on an off-the-shelf Mint 18 Xfce installation. Are you specifically talking about the network-manager package itself?
@Robert @Jason
thanks. resently my network manager stopped working as smoothly as it used to. troubleshooting in vain so far. maybe this could fix it
I’m using Linux Mint 18.1 Cinnamon 64 bit build. In synaptics, I had to downgrade to 1.2.2. I got the info from this link while doing a search for a fix. https://www.reddit.com/r/linuxmint/comments/5yqt0b/dont_upgrade_network_manager_for_a_while_if_you/
Yandex.Browser uses DNSCrypt technology.
https://yandex.com/support/browser/security/protection.xml
This article is about your ISP snooping on you. So Opera with its built-in VPN does shield you from snooping by your ISP, but snooping by the Canadian government, if I understand well.
Opera is not a VPN, although it says that in the URL, it is a simple PROXY
Opera is NOT A VPN, it is a PROXY, don’t be fooled
At least they won’t sell it. And the NSA/GCHQ/Five Eyes already know what you’re doing anyway. ;-)
Well, you can select a different exit point (Netherlands, Germany, Singapore) in which case I’m not sure Canada can do much about it.
@Heimen Stoffels, at this point do you, should we differentiate the fact ISPs are (bound to be) allowed to sell users’ data from the fact that intelligence agencies are allowed to snoop on users’ data? On the perception level security remains more legitimate than business when it comes to getting undressed for their sake. But at the end is there truly an ethical difference between the two?
The Netherlands is only going to be safe for a little while longer. Here in the Netherlands they’ve been recently making it much easier for the national security service to snoop on you as well. It’s called the “sleepnetwet” (sleepnet law). It basically gives them almost all of the power the NSA has in the States. The law is almost fully accepted, it’s only some months away from full acceptance. So enjoy our exit point while you can, but it won’t be safe for long anymore.
well I would start comparing DNScrypt to VPN – it’s easier to setup on router (say you have DD-WRT or LEDE) and it’s a good first step
free and definitely better than selling soul to VPN providers without proper research
https://thatoneprivacysite.net/
I am in tight budget and I need a free desktop VPN.. I know free VPNs are bad as well..
Please suggest me the best(!) available VPN service fro free!
Thanks,
Great free VPN is WINDSCRIBE (10gb month) LIMITED !
https://windscribe.com/upgrade
(pro version is also great for $)
Alternatives:
Steganos Online Shield VPN – 1 Year
https://www.steganos.com/specials/?m=pcpro0317&p=sos
OkayFreedom VPN Premium – 1 Year
https://www.okayfreedom.com/specials/chip0617/of
Check out DNS-CRYPT. It’s not a VPN but it will help.
This one works really good on Windows 10. It even has regular updates. https://simplednscrypt.org/
“Internet Service Providers may be able to sell your web history in the United States without you giving your consent.”
All depends of the President now. Gosh, will he ratify?!
Outside the grand country and more specifically in Europe we haven’t this neo-cyber-liberalism planned yet, which doesn’t mean ISPs here in Europe would be de facto blind to what their customers discover of and live on the Web. I have no idea of what my ISP does with my data, I only know what the law doesn’t entitle it to do.
DNS queries here are performed with the DNSCrypt-proxy and I limit resolvers to those who comply to DNSSEC validation. OpenDNS is not of that lot so I avoid it most of the time, but it is truly the fastest and error-free so I happen to be tempted when other DNSCrypt resolvers fail, which happens though really seldom.
VPN. That’s the big question for me at this time. Should I be abroad, in a country bound to allow ISPs to sell their customers’ data (when you think about it this is beyond liberalism, it’s plain uncivilized in a country which considers itself as a guide) that I’d already have a VPN or at least on my way to.
VPN and VPN. The article clearly states that a paid VPN is basically more worthy of a user’s confidence. Basically.
At this stage if I compare the likelihood of my data being managed by my ISP with a VPN service never sure of at 100% and with moreover UL and DL reduced speeds, I’m not inclined to make the move. I’d rather conceive Tor should I become excessively suspicious of ghosts wandering around my traveling on the Web.
only an old PDF file would need this much privacy…
have something you want to share, Martin?
I setup a VPN on my home router using Tomato Shibby’s OpenVPN setup within the OS. I know that what I send from my device to the routers OpenVPN is encrypted but not sure about what is sent from the router to the ISP carries the same encryption, anybody know?
DNS WATCH
https://dns.watch/index
UncensoredDNS
https://blog.uncensoreddns.org/dns-servers/
I’ve been using F-Secure Freedome VPN and it works perfectly for me. No problems with watching stuff (TV) from other countries. But I cannot say anything about how it may work with Netflix and other video streaming sites since I have not subscribed to any of them. But for just watching a soccer game or a TV show in Europe this VPN is doing very well. They are located in Finland.
fsecure is shit and p2p is NOT allowed + they log and share user data. dont believe anything that comes out of finland as all companies are either owned by finnish government or allowed by finnish government > fi gov also works with cia, fbi etc. due their shit scared attitude about russia.
@HadschiHalef I felt sick after reading your contaminated comment
Thank you, Anon2, for your very informative and well founded contribution. It’s always a pleasure reading posts from apparently highly knowledgeable people talking “shit”.
You stated, that F-Secure is shit. I looked into it, but unfortunately you are wrong. It is a company with different products, one of it is “VPN Freedome”. So your “shit” does not apply here.
They logging is very limited, please read their privacy policy and you will find your “shit” statement about logging being pure “shit”.
You wrote, all companies are either a) owned or b) allowed by finnish government. Again, sorry to correct your “shit” about the all owned. And of course all companies have to be allowed by designated parts of the government. This, my highly educated friend, you should have known but you preferred your own “shit” interpretation.
About the rest of your highly appreciated “shit” please read about 5eyes, etc. and even you may be able to figure out what information is being exchanged or not.
This may give you a different view on the “shit” you have produced with your opinion.
My closing words are to wish you a wonderful massive daily defecation so that your “shit” never ends and please continue to provide us with your “shit” as long as your are full of it. Again, thank you for your …, well, you already know, right ?
https://www.theatlantic.com/technology/archive/2017/03/encryption-wont-stop-your-internet-provider-from-spying-on-you/521208/
While certainly an interesting read i feel it maybe a bit misleading to associate that with using a VPN, yes encryption isn’t a fool proof way of masking your online activity but what Martin’s saying is to use a VPN and encryption.
Encryption =\= VPN.
Encryption (HTTPS) merely encrypts between two endpoints, both of which are visible to your ISP.
With a properly configured VPN, your ISP sees only encrypted traffic, and that encrypted traffic(from their viewpoint) only travels to and from one endpoint. Your traffic is tunneling through that endpoint so your ISP can’t see the final destination.
http://www.express.co.uk/life-style/science-technology/632080/Windows-10-Microsoft-Data-Collection-Statistics
Corporate Vice President for Windows and Devices Group Yusuf Mehdi listed the figure in his blog post: “Over 82 billion photos viewed within the Windows 10 Photo app.
“Over 44.5 billion minutes spent in Microsoft Edge across Windows 10 devices in just the last month.”
“Over 2.5 billion questions asked of Cortana since launch. Around 30 per cent more Bing search queries per Windows 10 device vs. prior versions of Windows.”
It is not clear whether Microsoft is also monitoring the fine details of the 2.5 billion questions asked of Cortana, or what users are doing during their 44.5 billion minutes spent in Microsoft Edge.
@ Beecher
https://www.wired.com/2017/03/vpns-wont-save-congress-internet-privacy-giveaway/
As per the link, tech companies are trying to pre-install/pre-load/build-in/back-door tracking software locally on routers, computers, smartphones, smart TVs, IoT devices, etc, eg US telcos pre-installed Carrier IQ on their smartphones.
……. It’s likely that OEM Win 10 computers also have such tracking software.
Hi Martin,
I’ve been using https://www.dnscrypt.org/ and their worldwide network of recommended servers to prevent nosy folks from having it easy. When I travel, or am using public wifi, I also use Private Internet Access. I am thinking of logging my router into it at home in order to protect all my traffic, but I will begin with a test to see how it impacts speed and responsiveness. PIA has been excellent in my experience on all my devices and computers and I’ve been a subscriber for years. I was pleased to see you used it as your example. They claim to keep no logs and I am inclined to believe them, especially since they’ve been kicked out of places for refusing to hand over logs they indicated to authorities they do not have.
I hope you are well. Keep up your wonderful work.
>While you can use free VPN services, most do sell your data, anonymously or not. It is advised therefore to get a paid VPN service instead
Because paid VPN providers surely won’t sell my data.
Great “logic” there, chief.
Leave the house unlocked because the locksmith might keep a copy of the key.
Well, paid providers do have a different business model, as they earn money through subscriptions. You are right that you never know for 100% though. Check the privacy policy, FAQ sections, online reviews, and you will realize the quite a few paid providers state explicitly that they don’t sell user data.
And how would you make sure they don’t log? You take their word for it?
So, your solution is don’t use them because you cannot verify it?
Always look for the ones that don’t log information. If they don’t log, they won’t have anything to sell.
#1 – all corporations try to maximize their profit
#2 – people do lie
#3 – corporations only don’t lie when they must assume they will be caught and being caught reduces their profit