Know which site sold your data
Whenever you sign up for a service or site on the Internet, there is a chance that your data will be used by the company operating the service, or sold.
Most companies ask permissions before they add you to their newsletter. Some sneaky ones add you without option to remove yourself during signup in hope that you will forget to cancel the subscription afterwards.
It gets worse when your data is sold. Once in the system, it is there for all time and there is a chance that your email account will receive regular spam emails until it is closed.
While you cannot do much about it, you can at least try your best to understand which company or site sold your data in first place.
Option 1: Different email accounts, or aliases
There are two options for this. The first is to use different email accounts for online accounts. Besides using different accounts, you may also make use of aliases instead. Major email providers such as Outlook or Gmail support aliases.
I'm not a huge fan of the alias system that has you add +whatever to your email username. If my email is martin@example.com, I could use aliases like martin+walmart@example.com to identify the site or service that sold my data.
This works only however if the spammers are not processing the email list before sending out spam. It is easy enough to remove any +whatever characters from emails to avoid sending to aliases altogether.
You may also use so called temporary email services, but those only for unimportant accounts.
Option 2: Make use of custom middle names

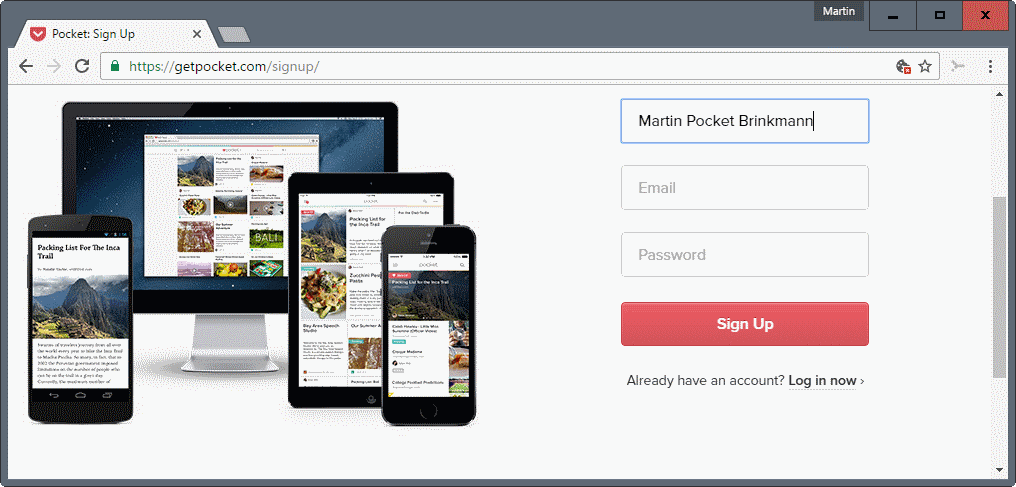
I read about this method on Reddit the other day and like it a lot (thanks Ilev). Some sites have a middle name field when you sign up. Instead of not filling it out, or filling it out with your real middle name, you could add the sites name, or another unique identifier there.
So, if I sign up for an account on a site, my name would be Martin Sitename Brinkmann. That site, or any other service the data is sold to, would usually use the full name when it addresses you in emails.
Emails would begin with Dear Martin Sitename Brinkmann. Looking at Sitename, you would know immediately where the data originated from.
Caveats: The system has some caveats. First, this may not work for services that require payments or identification. Payments may get rejected if the name does not match, and you may not be able to identify yourself if the name does not match yours.
Second, this won't work if the middle name is not listed as a field during sign up and afterwards, and won't work if the middle name is ignored when emails are sent out.
One workaround for that is to add the middle name to the name field. If you only get first and last name fields, you would add it to the first name field, and if you only get one name field, you would add it there.
There is still a chance that companies will detect this and remove your account. Most won't however as emails are usually processed automatically.
Now Read: How to fight spam, the final guide






















I’ve been using safersignup.com as an external version of option 1 for years now.
>> It is easy enough to remove any +whatever characters from emails to avoid sending to aliases altogether.
For option 2 it’s easy enough to search for middle names being “Your company” and remove them.
All together: option 2 is a very poor way of knowing who sold your information.
I 200% agree with what Tom Hawack said above: Use non time-limited DEAs.
I’m using a FREE DEA provider (that doesn’t need any browser plugins and that doesn’t require me to go to their site to create an alias!) and I have no problems AT ALL with spam. And I perfectly know what site passed my data to others too.
PS. My oldest Disposable E-mail Address is 13 years old!
Sounds good, Peter!
Would you care to share the provider name,
so we might also benefit?
Like Clairvaux, I’m not going to share it.
The lesser it is known (to spammers à nd companies blocking DEA’s) the better.
However to help you, here’s a clue:
Look for alternatives for the above mentioned trashmail @ http://alternativeto.net/software/trashmailnet/ (it has more than 9 likes and less than 18)
outlook does not permit an unlimited number of aliases unlike some paid for- providers like posteo. Besides: why offer your real name anyway? you don’t have to give away your identity either. a random letter could do the job. so far I’ve avoided DEA. I don’t trust providers from former soviet union countries. but then again: I haven’t checked the number of companies for years.
You make it sound as if the Outlook & Gmail aliases only allow the “+” type of alias. I don’t know about Gmail, but Outlook allows any type of alias you like, without any limitation s of a “+” or such like. My pseudonym here is an example.
Paranam Kid,
Do you know whether Microsoft still have their ridiculous limitation on the number of aliases allowed at Outlook.com ? Last time I looked it up, not only you had a very small number allowed at any given time (something like 8 or 10) ; they also had complex rules impossible to remember, such as “you can create only x new aliases in any given year”. Typical Microsoft boorishness.
MS limits it to 10 aliases, which is more than enough enough for me. I have not come across their complex rules. I also use some other email services that allow aliases so I don’t have all my eggs in 1 basket. By the way, I have not received any promotional emails that indicate my data was sold, so my use of aliases is not for the tracking purpose.
I have been using a paid-for remailer for a very long time now. I could not live without it, most of my mail is routed through that service. It was praised in the media long ago. It almost never changes, no updates, no fancy new features, it just works. They generally forget to collect the (small) annual fee. Two or three years later, someone wakes up and presents the bill. Then he, presumably, goes back to sleep, while the server keeps humming.
If only Windows could work this way…
@Clairvaux (see his comment above)
Sounds good!
Care to share the name?
It would help them (and you, too)
if more people subscribe to them and support them…
@Clairvaux, I ignored one’s relationship to a DEA provider could belong so intimately to one’s privacy, unless whatever secret service would be involved, which would be surprising considering they don’t sleep, dream, farnient too much down there! I mean, the first word to describe James Bond’s life isn’t dolce vita, is it?!
I consider mentioning so partially a Web service, site relates to a romantic, poetic approach of a virtual idealism :) You could have elaborated on what you consider as valuable concerning a DEA provider, but why dress the profile’s shadow of a company if not to be more precise. Well, it’s your secret. You’re quite a character!
Made me dream, at least :)
Tom,
For the same reason you might be inclined to share some stories about your life, without willing to see all of it exposed.
@Clairvaux, why mention a service if “there is a specific reason why [you} prefer not to broadcast this.”?
Poetry?!
Sorry, trek100, there is a specific reason why I prefer not to broadcast this.
Why is it that your description makes it (and me as well) feel so nonchalantly happy? Maybe the imagination of a world where you think of money only when you need it and dream elsewhere otherwise, a “dolce vita” all of farniente. Laziness is not a sin when it can be a way of life, perhaps closer to happiness than running 24/7/365.
Very nice description which splits me between a smile of laugh and one of that tenderness you feel when chocolate melts in your mouth!
That was my word of the day :)
Quoting this line of the article,
“You may also use so called temporary email services, but those only for unimportant accounts.”
Temporary email services propose indeed so called DEAs or Disposable Email Addresses and often these are known to be what most of these services offer : a volatile time-limited email address.
Nevertheless, another approach is that of services offering non time-limited DEAs. As such the user has the best of two worlds : he can remove a DEA which has been shared/sold/spammed and he can at the same time fully take advantage of an email address which can be valid over time. I know and use such a service and do consider sharing this service’s identity is not intended to promote it as an advertisement but truly as information only :
The site : https://trashmail.com/
The Firefox add-on : https://addons.mozilla.org/en-US/firefox/addon/trashmailnet/
Only a paid subscription offers unlimited in time DEAs, it’s not expensive and really worth it. The email I provide here associated with my user name is a DEA, has been the same for years, always with the same service and add-on mentioned above. Another benefit of such DEAs is that they will follow you when your true email address changes : simply notify the DEA service of your new true email address et voila …
Some very few sites refuse an email address they’ve analyzed as a DEA, perhaps because they consider as well that this address is time limited, or because they know they won’t share/sell it correctly. Personally I refuse in return such sites.
Since I’m running my own private email server (Mail In a Box) with my own domain, I have an unlimited supply of aliases like whatever@example.com, that cannot be processed to get the main address. Sadly I only figured out to actually start using them in that way about three years ago, so my actual email address has already been out there long before that.
Right. This is what I do too, bought my own domain not for hosting a website but specifically for having my own set of fully configurable email adresses. This email setup also protects against email content snooping like Google does. It costs about € 3 per month but it’s worth it.
Holy smokes… Thank you for your encouragement and information. I’m not sure I’m ready for this sort of thing, though. I’ll bookmark this thread and keep it handy. Maybe some day in the future…
Not at all, I myself am an amateur at best. Some skill sure, at least get a little bit used to working with a linux server. In a virtual machine locally or with something like Vultr or Digital Ocean where they meter by the hour so you can start a server, play around and kill it without paying significant money. Set up your user, public key authorization for ssh… stuff like that. Maybe a webserver or something else for fun. Nothing difficult and lots of tutorials online. Then get a free domain (.tk for example) and a fresh server and start testing MIAB (https://mailinabox.email/). No need to migrate your main email right away, or at all if you don’t like it.
Thanks, g. Would you say that requires the skills of an IT professional ?
Clairvaux,
No it is not, at least with Mail In a Box. Setting it up is simple as pie, all is automated. You just provide a clean server (cheapest Vultr in my case), point your DNS’s to where they need to point and run the install script. There is hardly any maintenance involved, just the periodic MIAB updates (system updates and backups can be automated). Spam is not an issue. Before, with hosted email, I was getting at least one spam a day. Now it’s maybe one a week. The filters are doing a really good job of keeping it out. I have to admit I was quite scared of the whole self-hosted email thing, having read a LOT of opinions on how much work it is to setup, maintain and whatnot, but two years in I couldn’t be happier with it.
Rick,
I was similarly surprised to see very few addresses abused through my remailer service. Over the years, it’s exceptional I have had to shut off an address because it began to give out spam. I believe 100 % of those were hacked. On top of that, I had to shut off maybe one or two addresses whose legimate owner started sending annoying marketing mail, and would not respond to unsubscribing requests.
But then, maybe spam got filtered by my ISP or my intermediate Google account, before I even saw it.
Only with your own domain can you really get an accurate feel for how often your address makes it beyond what someone promised during a sign up.
I’ve had my own for seven or eight years. I thought I would catch a lot of rogue secondary use of addresses. The exact opposite happened. I found that very few sites have broken trust over the years … maybe ten or so at the most. Of those, a few wound up getting passed on to multiple extra destinations.
And, because you know right away who passed your address on without permission (or allowed it to become part of a hacker’s loot), it’s easy to add that address to the blocked list. Problem 100 percent solved without trying to get someone or several others to strike you from their list.
RICK
Isn’t it a burden, in such a setup, to fight spam and other attacks oneself ?