Microsoft Security Bulletins For August 2014
Welcome to the Microsoft Security Bulletin overview for August 2014. It offers information about all security and non-security patches released by Microsoft since the last release.
A total of nine bulletins have been released this month which patch security issues in Microsoft Windows, Internet Explorer, Microsoft Server Software, the .NET Framework and Microsoft Office.
Two bulletins have received the highest severity rating of critical while the remaining seven bulletins a rating of important.
In addition to regular updates, Windows 8.1's August Update has been released as well. It is a smaller update for the operating system that adds three new features or improvements to it. It is likely that it won't impact the majority of users in any way though.
Microsoft's new out-of-date ActiveX Controls blocking rolls out with this update as well but won't be active for the next 30 days to give customers more time to test it before it goes live.
Executive Summary
- A total of nine security bulletins addressing 37 vulnerabilities have been released.
- Microsoft Windows client and server operating systems, Windows Server and Internet Explorer are affected.
- Two bulletins have received the highest severity rating of critical.
- Top deployments are MS14-051 for Internet Explorer, MS14-043 for Media Center and MS14-048 for One Note, with MS14-051 seeing active attacks in the wild.
Video Summary
Operating System Distribution
Vulnerabilities may impact operating systems in a different way or not at all. This month's distribution shows this clearly as Vista and RT are affected by one critical and three important bulletins while all remaining systems are affected by two critical bulletins and four important ones.
The least affected operating system on the server side is Windows Server 2003 followed by Server 2008. All other server products share the same vulnerability distribution of four important and one moderate bulletin.
- Windows Vista: 1 critical, 3 important
- Windows 7:Â Â 2 critical, 4 important
- Windows 8:Â 2 critical, 4 important
- Windows 8.1: 2 critical, 4 important
- Windows RT: 1 critical, 3 important
- Windows RT 8.1:Â 1 critical, 3 important
- Windows Server 2003: 2 important, 1 moderate
- Windows Server 2008: 3 important, 1 moderate
- Windows Server 2008 R2: 4 important, 1 moderate
- Windows Server 2012: 4 important, 1 moderate
- Windows Server 2012 R2: 4 important, 1 moderate
- Server Core installation: 4 important
Other Microsoft Product Distribution
- Microsoft Office Software: 1 important
- SQL Server 2008: 1 important
- SQL Server 2008 R2: 1 important
- SQL Server 2012: 1 important
- SQL Server 2014: 1 important
- Microsoft SharePoint Server: 1 important
- Windows Media Center TV Pack for Windows Vista: 1 critical
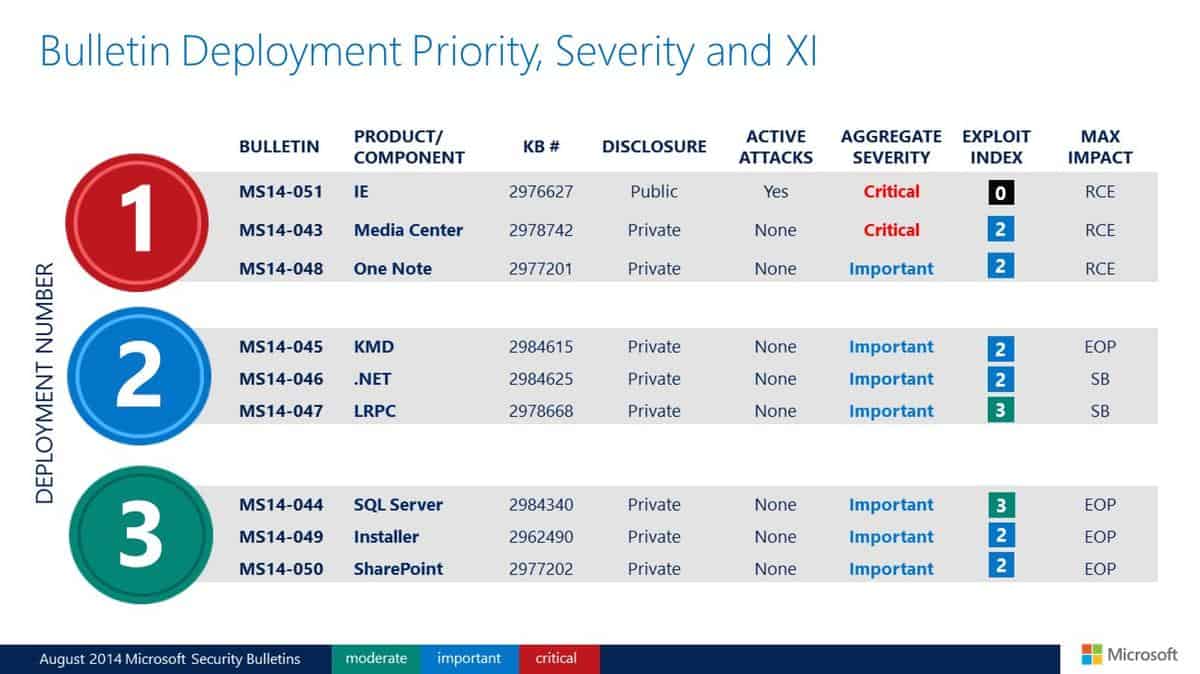
Deployment Guide
Microsoft releases a deployment guide each month suggesting the order in which updates should be installed on affected systems.
- Tier 1: MS14-051 Internet Explorer (critical), MS14-043 Media Center (critical), Ms14-048 One Note (important)
- Tier 2: MS14-045 KMD, MS14-046 .NET, MS14-047 LRPC (all important)
- Tier 3: MS14-044 SQL Server, MS14-049 Installer, MS14-050 SharePoint (all important)
Security Bulletins
- MS14-051 - Cumulative Security Update for Internet Explorer (2976627) - critical - Remote Code Execution
- MS14-043 - Vulnerability in Windows Media Center Could Allow Remote Code Execution (2978742)Â - critical - Remote Code Execution
- MS14-048 - Vulnerability in OneNote Could Allow Remote Code Execution (2977201) - Important - Remote Code Exeuction
- MS14-044 - Vulnerabilities in SQL Server Could Allow Elevation of Privilege (2984340) - Important - Elevation of Privileges
- MS14-045 - Vulnerabilities in Kernel-Mode Drivers Could Allow Elevation Of Privilege (2984615) - Important - Elevation of Privileges
- MS14-049 - Vulnerability in Windows Installer Service Could Allow Elevation of Privilege (2962490) - Important - Elevation of Privileges
- MS14-050 - Vulnerability in Microsoft SharePoint Server Could Allow Elevation of Privilege (2977202)Â - Important - Elevation of Privileges
- MS14-046 - Vulnerability in .NET Framework Could Allow Security Feature Bypass (2984625) - Important - Security Feature Bypass
- MS14-047 - Vulnerability in LRPC Could Allow Security Feature Bypass (2978668)Â - Important - Security Feature Bypass
Security related updates
- Security Update for Windows Server 2003 (KB2982792) - Microsoft security advisory: Improperly issued digital certificates could allow spoofing
Security Advisories
- Security Advisory 2755801: Update for Vulnerabilities in Adobe Flash Player in Internet Explorer.
Non-security related updates
- Update for Windows 7 and Windows Server 2008 R2 (KB2970228)
- Update for Windows 8.1 and Windows RT 8.1 (KB2971239)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2975331)
- Update for Windows 8.1 and Windows RT 8.1 (KB2978002)
- Update for Windows 8.1 and Windows RT 8.1 (KB2979500)
- Update for Windows 7 and Windows Server 2008 R2 (KB2980245)
- Update for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, Windows Server 2012, Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB2981580)
- Update for Windows 8.1 and Windows RT 8.1 (KB2981655)
- Windows Malicious Software Removal Tool - August 2014 (KB890830)/Windows Malicious Software Removal Tool - August 2014 (KB890830) - Internet Explorer Version
- Update for Windows 8 and Windows RT (KB2973544) - An update to enable an automatic update from Windows 8 to Windows 8.1
- Windows 7 Service Pack 1 (KB976932) -
Information about Service Pack 1 for Windows 7 and for Windows Server 2008 R2 - Update for Windows 8.1 and Windows RT 8.1 (KB2980654) - July 2014 OneDrive reliability update for Windows 8.1 and Windows RT 8.1
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2962407) - Windows RT, Windows 8, and Windows Server 2012 update rollup: June 2014
- Update for POSReady7 (KB2959943) - "Another application has exclusive access to the device" error when you claim multiple devices through POS for .NET 1.14
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2962407 - Windows RT, Windows 8, and Windows Server 2012 update rollup: June 2014)
- Update for Windows 8 (KB2973544) - An update to enable an automatic update from Windows 8 to Windows 8.1
- Windows 7 Service Pack 1Â (KB976932) - Information about Service Pack 1 for Windows 7 and for Windows Server 2008 R2
How to download and install the August 2014 security updates
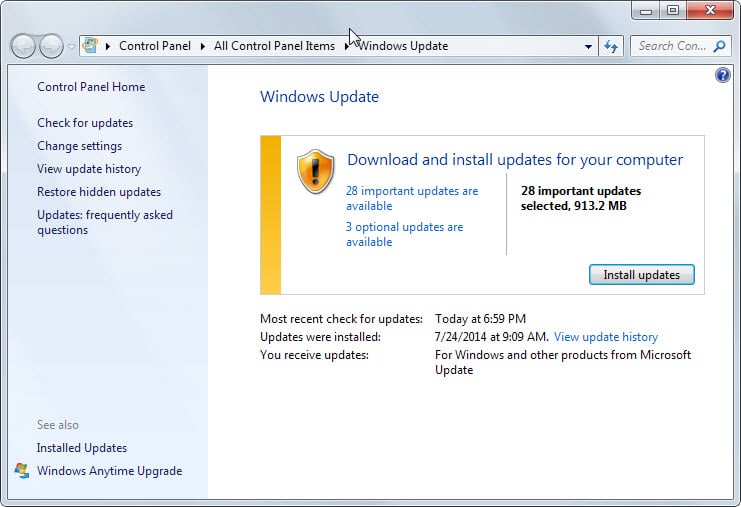
Most Windows users will receive the updates via the operating system's automatic update feature. It is recommended to check for updates manually as this is not done in real-time by the system.
To do so, tap on the Windows-key, type Windows Update, and select the right result. Here you need to select check for updates to run a manual check for new updates.
Patches are also made available on Microsoft's Download Center. While not as comfortable it provides users and system administrators with improved deployment options.
Microsoft releases a security ISO each month containing all updates and patches of that month. You find a link list of all security ISO images here.
Additional information
- Microsoft Security Response Center blog on the 2014 Bulletin Release
- Microsoft Security Bulletin Summary for August 2014
- List of software updates for Microsoft products 2014
- Our in-depth update guide for Windows






















https://answers.microsoft.com/en-us/windows/forum/windows_7-windows_update/blue-screen-stop-0x50-after-applying-update/6da4d264-02d8-458e-89e2-a78fe68766fd
I’m watching the above thread for official updates
Same as Rick ! Lost access to Windows Store and several programs had vanished or did not work anymore.
Read this about it:http://www.infoworld.com/t/microsoft-windows/users-find-fix-botched-kb-2982791-and-kb-2970228-windows-update-248476
Don’t install the August updates!
Microsoft has pulled (or is pulling) 6 of them reportedly. I would imagine that new ones will be made available once they correct the issues.
I stupidly installed and had to do a system recovery as program after program crashed.
Big thanks for this, keep up the good work :)
BTW, wrong link for “Security Advisory 2755801: Update for Vulnerabilities in Adobe Flash Player in Internet Explorer”, it should be https://technet.microsoft.com/library/security/2755801
Thanks Dexter, sorted it out!
I have to add my voice and thank Martin taking the time to write this wonderful and detailed summary of this month’s updates. Very much appreciated.
I have one question though:
Last night on BetaNews, I noticed a “pre-release” version of Microsoft Security Essentials.
I’m running Windows 7 and am am curious to know what the latest full version of MSE is – and will new versions be pushed via the monthly updates ?
Thanks again Martin. Your site gets better and better.
Security as we know it will soon become irrelevant.Martin have you seen this? https://srlabs.de/badusb/ or this https://github.com/hkm/routerpwn.com
update is good except that I’ve encountered a frozen taskbar when switching apps and desktop. I have to autohide the desktop taskbar inorder to close the app
Turn “Animate Windows When Minimizing and Maximizing” on and you will see the intended behavior of the taskbar for this update. People with the animations off are seeing the persistent taskbar for some reason.
thanks, works for me. kudos… and here’s an article why many are complaining about the updates:
http://www.pcworld.com/article/2465631/microsoft-pulls-august-windows-update-after-crashes.html
I have to agree totally with Scott Elsdon his comment concerning the quality of your summery of this mount Microsoft updates Martin.
I like to ad that your summery s every mount are getting a little bit better than the mount before. :-)
Excellent summary as always Martin, thank you for your work.
You are welcome Scott ;)