Microsoft Security Bulletins October 2010
Every second Tuesday in a month is patch day over at Microsoft. What does it mean? Microsoft pushes out all security patches of a month on that day to all users of their Windows operating systems and other applications like Microsoft Office. Only highly critical vulnerabilities receive out of band security patches.
This month's patch day is huge. While it is not the largest in history, it addresses the impressive amount of 49 vulnerabilities affecting Windows, Internet Explorer, Microsoft Office and the .net framework.
Looking at the number and type of updates this month, we have a fairly standard number of bulletins affecting products like Windows and Office. This month we also have a few bulletins originating from product groups that we don't see on a regular basis. For example, SharePoint, the Microsoft Foundation Class (MFC) Library (which is an application framework for programming in Windows), and the .NET Framework. It's worth noting that only six of the 49 total vulnerabilities being addressed have a critical rating. Further, three of the bulletins account for 34 of the total vulnerabilities. (via)
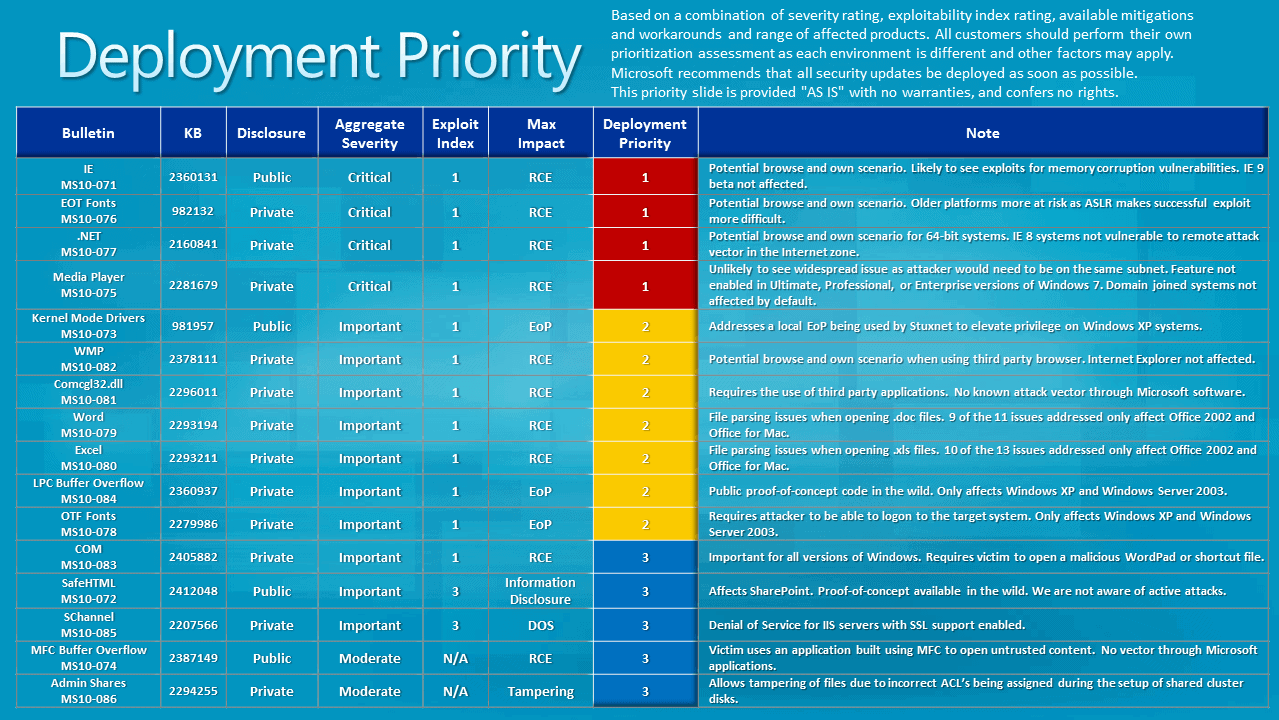
Deployment Priority
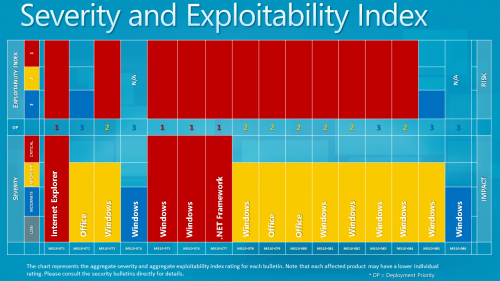
Severity and Exploitability
Four of the vulnerabilities have a maximum severity rating of critical, 10 of important and the remaining 2 of moderate.
- MS10-071 - Cumulative Security Update for Internet Explorer (2360131) - This security update resolves seven privately reported vulnerabilities and three publicly disclosed vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-075 - Vulnerability in Media Player Network Sharing Service Could Allow Remote Code Execution (2281679) - This security update resolves a privately reported vulnerability in the Microsoft Windows Media Player network sharing service. The vulnerability could allow remote code execution if an attacker sent a specially crafted RTSP packet to an affected system. However, Internet access to home media is disabled by default. In this default configuration, the vulnerability can be exploited only by an attacker within the same subnet.
- MS10-076 - Vulnerability in the Embedded OpenType Font Engine Could Allow Remote Code Execution (982132) - This security update resolves a privately reported vulnerability in a Microsoft Windows component, the Embedded OpenType (EOT) Font Engine. The vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could take complete control of an affected system remotely. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-077 - Vulnerability in .NET Framework Could Allow Remote Code Execution (2160841) - This security update resolves a privately reported vulnerability in Microsoft .NET Framework. The vulnerability could allow remote code execution on a client system if a user views a specially crafted Web page using a Web browser that can run XAML Browser Applications (XBAPs). Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. The vulnerability could also allow remote code execution on a server system running IIS, if that server allows processing ASP.NET pages and an attacker succeeds in uploading a specially crafted ASP.NET page to that server and then executes the page, as could be the case in a Web hosting scenario.
- MS10-072 - Vulnerabilities in SafeHTML Could Allow Information Disclosure (2412048) - This security update resolves one publicly disclosed vulnerability and one privately reported vulnerability in Microsoft SharePoint and Windows SharePoint Services. The vulnerabilities could allow information disclosure if an attacker submits specially crafted script to a target site using SafeHTML.
- MS10-073 - Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - This security update resolves several publicly disclosed vulnerabilities in the Windows kernel-mode drivers. The most severe of these vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS10-078 - Vulnerabilities in the OpenType Font (OTF) Format Driver Could Allow Elevation of Privilege (2279986) - This security update resolves two privately reported vulnerabilities in the Windows OpenType Font (OTF) format driver. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. All supported editions of Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.
The vulnerabilities could allow elevation of privilege if a user views content rendered in a specially crafted OpenType font. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS10-079 - Vulnerabilities in Microsoft Word Could Allow Remote Code Execution (2293194) - This security update resolves eleven privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted Word file. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-080 - Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution (2293211) - This security update resolves thirteen privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted Excel file or a specially crafted Lotus 1-2-3 file. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-081 - Vulnerability in Windows Common Control Library Could Allow Remote Code Execution (2296011) - This security update resolves a privately reported vulnerability in the Windows common control library. The vulnerability could allow remote code execution if a user visited a specially crafted Web page. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-082 - Vulnerability in Windows Media Player Could Allow Remote Code Execution (2378111) - This security update resolves a privately reported vulnerability in Windows Media Player. The vulnerability could allow remote code execution if Windows Media Player opened specially crafted media content hosted on a malicious Web site. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-083 - Vulnerability in COM Validation in Windows Shell and WordPad Could Allow Remote Code Execution (2405882) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted file using WordPad or selects or opens a shortcut file that is on a network or WebDAV share. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-084 - Vulnerability in Windows Local Procedure Call Could Cause Elevation of Privilege (2360937) - This security update resolves a publicly disclosed vulnerability in Microsoft Windows. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. All supported editions of Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.
The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs specially crafted code that sends an LPC message to the local LRPC Server. The message could then allow an authenticated user to access resources that are running in the context of the NetworkService account. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
- MS10-085 - Vulnerability in SChannel Could Allow Denial of Service (2207566) - This security update resolves a privately reported vulnerability in the Secure Channel (SChannel) security package in Windows. The vulnerability could allow denial of service if an affected Internet Information Services (IIS) server hosting a Secure Sockets Layer (SSL)-enabled Web site received a specially crafted packet message. By default, IIS is not configured to host SSL Web sites.
- MS10-074 - Vulnerability in Microsoft Foundation Classes Could Allow Remote Code Execution (2387149) - This security update resolves a publicly disclosed vulnerability in the Microsoft Foundation Class (MFC) Library. The vulnerability could allow remote code execution if a user is logged on with administrative user rights and opens an application built with the MFC Library. An attacker who successfully exploited this vulnerability could obtain the same permissions as the currently logged-on user. If a user is logged on with administrative user rights, an attacker could take complete control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-086 - Vulnerability in Windows Shared Cluster Disks Could Allow Tampering (2294255) - This security update resolves a privately reported vulnerability in Windows Server 2008 R2 when used as a shared failover cluster. The vulnerability could allow data tampering on the administrative shares of failover cluster disks. By default, Windows Server 2008 R2 servers are not affected by this vulnerability. This vulnerability only applies to the cluster disks used in a failover cluster.
The patches are as usual available via Windows Update and Microsoft Download. Microsoft has furthermore released the October 2010 Security Release ISO Image containing all references security patches and Knowledgebase articles.
Advertisement




















Hoi Martin, Thanks a million of do i have to say nowadays a billion for the extensive works you did on this month gigantic list, of patches from Microsoft. Especially with the two picture who can pop-up its a ferry handy read (this because a pictures says more than thousand worths.)