Is your web app vulnerable? Here's how to solve the top 10 security issues

Developing or using web-based software requires critical consideration of web application security due to the increasing number of online threats. Therefore, it is more crucial than ever to ensure that web applications are secure and safeguarded against potential vulnerabilities. Unfortunately, many developers tend to neglect web application security, making it an afterthought, and failing to take the necessary measures to secure their applications. This can result in users' personal data and sensitive information becoming susceptible to various types of attacks such as cross-site scripting (XSS), SQL injection, and others.
In this article, we will discuss some of the most common web application security vulnerabilities and offer advice on how to address them. It is crucial to comprehend these vulnerabilities and how to protect against them, whether you are a developer or a user, to ensure a safe and secure online environment.

10 Web application security vulnerabilities and how to fix them
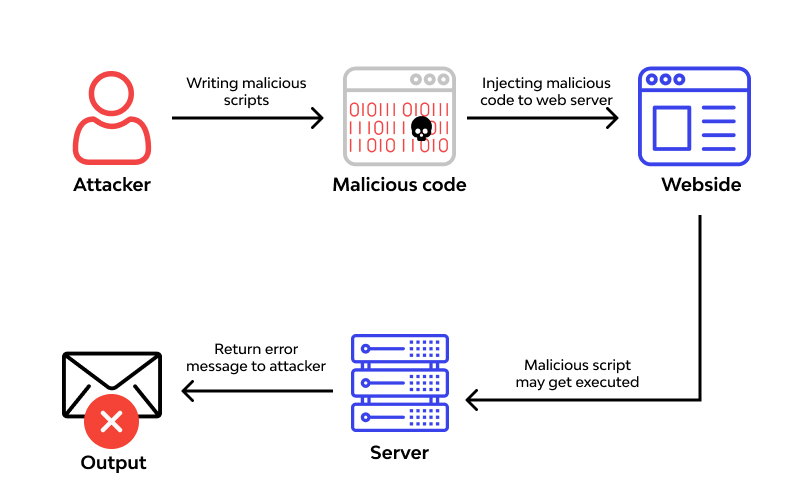
Cross-site scripting (XSS)
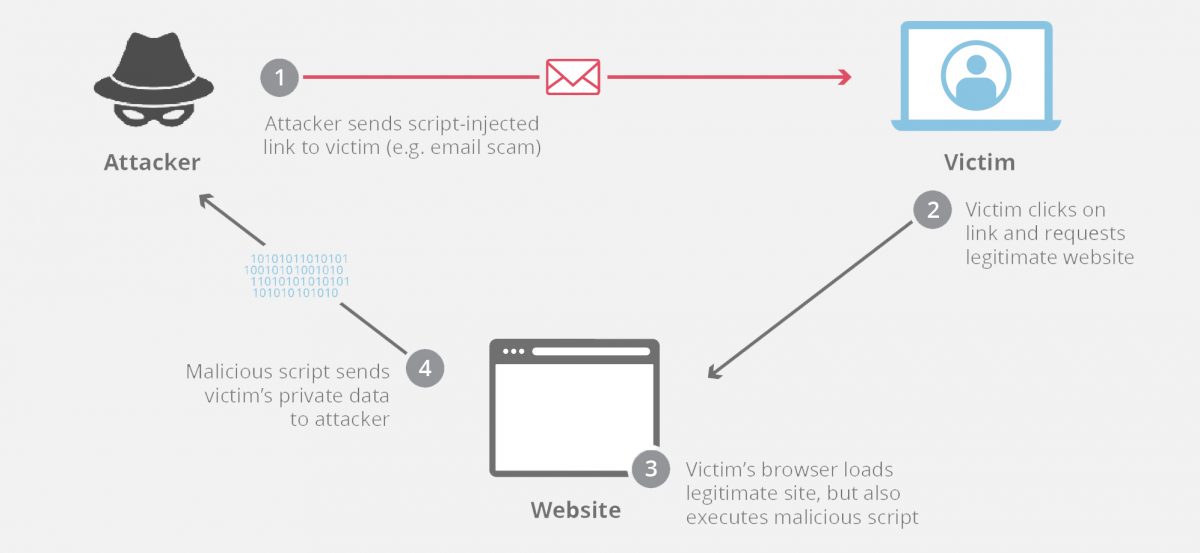
When attackers inject malicious code into a web page viewed by other users, it is known as cross-site scripting (XSS). This type of web application vulnerability can result in the theft of sensitive user data, unauthorized access to user accounts, and other severe security issues.
How to fix it
In order to prevent XSS, developers can take several measures such as sanitizing user input, validating data, and adopting secure coding practices. If an XSS vulnerability is detected, developers can rectify it by identifying and removing the malicious code, and implementing measures such as Content Security Policy (CSP) to prevent future attacks. On the other hand, users can protect themselves by using web browsers with built-in XSS protection features and avoiding clicking on suspicious links.
SQL injection (SQLi)
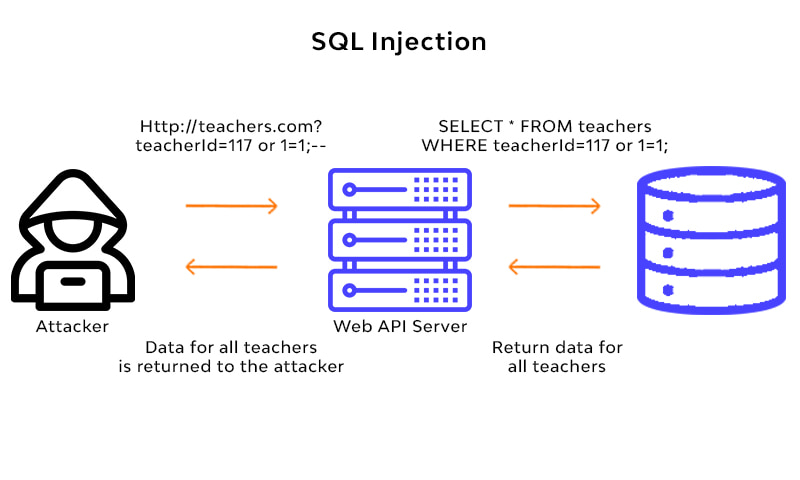
SQL injection (SQLi) is a type of web application vulnerability that allows attackers to manipulate the SQL queries used by a web application to gain unauthorized access to data. As a result, sensitive user data may be stolen, modified, or deleted, among other issues.
How to fix it
To prevent SQLi, developers can use parameterized queries and prepared statements, validate user input, and adopt secure coding practices. If an SQLi vulnerability is detected, developers can rectify it by identifying and removing the malicious code, as well as implementing measures such as web application firewalls (WAFs) to prevent future attacks.
Cross-site request forgery (CSRF)
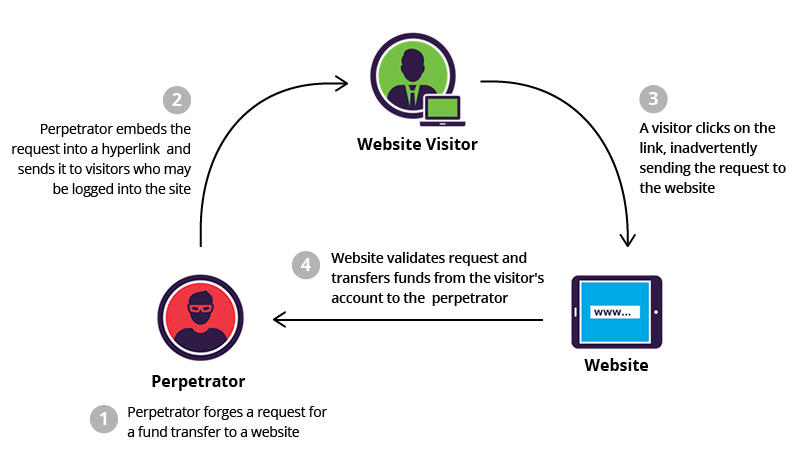
Cross-site request forgery (CSRF) is a web application vulnerability that allows attackers to deceive authenticated users into executing undesired actions on a web application without their awareness or consent. Such actions may include modifying account settings, making purchases, or even deleting data.
How to fix it
To prevent CSRF, developers can use mechanisms such as CSRF tokens, which are unique, secret values included in each request, and validated by the server to ensure that the request was indeed initiated by the user. If a CSRF vulnerability is detected, developers can rectify it by identifying and blocking malicious requests, as well as implementing secure coding practices to prevent future attacks. Web application firewalls (WAFs) can also aid in detecting and blocking CSRF attacks.
Broken authentication and session management
Broken authentication and session management is a type of web application vulnerability that arises when authentication and session management mechanisms are inadequately implemented, allowing attackers to obtain unauthorized access to user accounts. This can lead to the compromise of sensitive data, theft of user identities, and other security issues.
How to fix it
To insulate against Broken authentication and session management, developers can use secure authentication mechanisms such as multi-factor authentication (MFA) and strong password policies, as well as implementing secure session management mechanisms. If a vulnerability is detected, developers can rectify it by identifying and fixing any flaws in the authentication and session management mechanisms, and providing users with guidance on securing their accounts.
Security misconfigurations
Security misconfigurations refer to vulnerabilities that arise from incorrectly configured web application components, servers, and network devices. This can include anything from default passwords and insecure configurations to outdated software, unnecessary services, and open ports that are not required.
How to fix it
To prevent Security misconfigurations, developers can implement secure configurations, regularly review security settings, and maintain up-to-date software versions. If a misconfiguration vulnerability is detected, developers can rectify it by identifying and fixing any misconfigurations, ensuring that default passwords are changed, and limiting the number of unnecessary services and ports exposed to the internet. Penetration testing can also help to identify security misconfigurations.
Insecure direct object references
Insecure direct object references occur when a web application permits users to access specific objects, such as files, records, or database entries, without adequately authenticating or authorizing them. This can enable attackers to manipulate or delete sensitive data, such as personal information, financial data, or proprietary data.
How to fix it
To prevent Insecure direct object references, developers can implement proper authentication and authorization mechanisms, such as role-based access control, as well as sanitize user input and implement secure coding practices. If this vulnerability is detected, developers can rectify it by identifying any insecure direct object references, and implementing access controls to restrict user access to only authorized objects. This can involve modifying the application's code to implement access controls, using session management, or implementing security features like Content Security Policy (CSP).
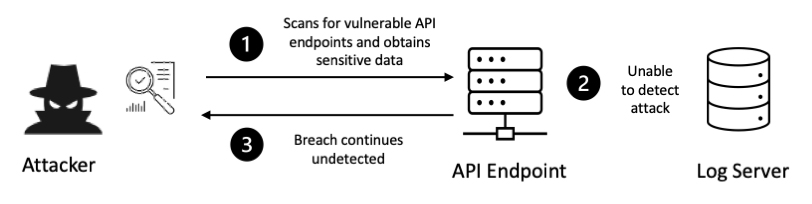
Insufficient logging and monitoring
When a system doesn't adequately log and monitor crucial events and activities, like uncommon system behavior or unauthorized access attempts, it's known as insufficient logging and monitoring. This can lead to challenges in detecting and addressing security incidents promptly, which can result in significant repercussions for an organization.
How to fix it
Organizations can prevent and rectify insufficient logging and monitoring by implementing strong logging and monitoring systems that can capture and analyze security events in real-time. This involves setting up alerts and notifications to detect suspicious activity, conducting regular reviews of system logs to identify any anomalies or security breaches, and performing routine security audits to identify and address any system weaknesses.
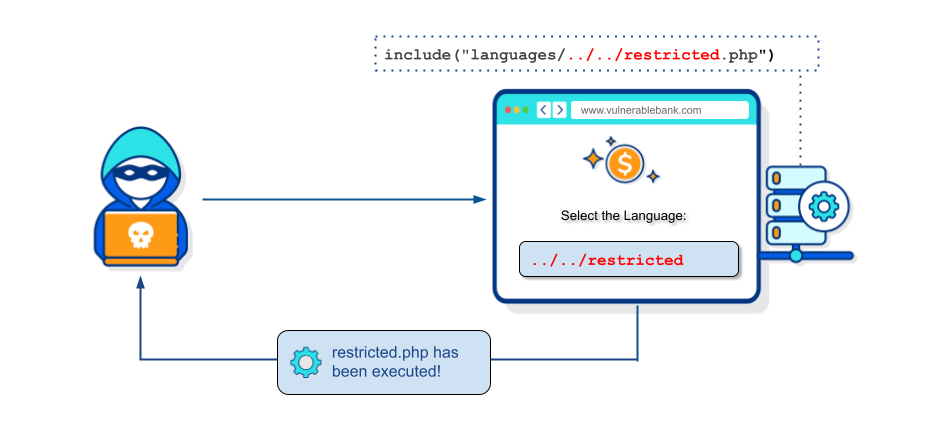
File inclusion vulnerabilities
A file inclusion vulnerability happens when a web application permits user-controlled input to include local or remote files. This can lead to an attacker gaining access to sensitive information or executing unauthorized code on the server.
How to fix it
To avoid and fix file inclusion vulnerabilities, developers of web applications should validate and sanitize all user-controlled input to ensure its safety before using it. They should also avoid using dynamic file inclusion functions and instead use static includes whenever feasible. Furthermore, implementing a content security policy (CSP) can assist in preventing attacks by limiting the types of content that can be included in a web page.
Remote code execution (RCE)
RCE, which is a security vulnerability, enables an attacker to run arbitrary code on a targeted system by exploiting a weakness in a web application or network service. As a consequence of this, the attacker can gain complete control over the system, which includes the ability to steal data, modify or delete files, and execute commands.
How to fix it
In order to prevent and correct remote code execution vulnerabilities, it is recommended that organizations adhere to secure coding practices, such as input validation, output encoding, and effective error handling. Keeping software and applications up-to-date with the latest security patches and updates is also crucial. Limiting the impact of an attack can be achieved by using network segmentation, firewalls, and access control lists.
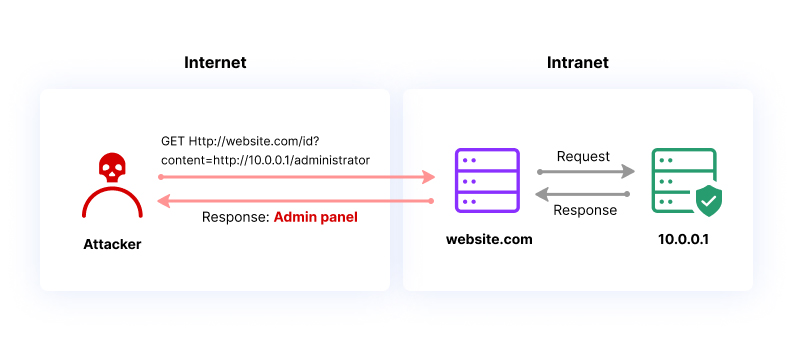
Server-side request forgery (SSRF)
An instance of vulnerability known as Server-side request forgery (SSRF) enables attackers to tamper with server-side operations by sending manipulated requests to a web application. By exploiting this weakness, an attacker can execute unauthorized actions, including accessing confidential information and manipulating server-side resources.
How to fix it
To prevent and address vulnerabilities related to SSRF, developers of web applications should take certain measures. This includes validating and sanitizing all input from users, such as URLs, IP addresses, and domain names. Additionally, implementing access control measures can help to restrict the attacker's ability to send requests to sensitive resources. Furthermore, developers should avoid constructing network requests using input from users, and instead use predefined lists or whitelists of allowed resources.

















Very valuable article.
Thank you.
GPTZero indicates nearly all of this article was likely written by AI. Hmm…
@Martin
For those with RSS readers that have good filters, a new category (e.g. ‘developers’) would work well.