Is your device at risk? North Korean group launches new attack with Remote Access Trojan
Infamous North-Korean threat group APT37 has upgraded its arsenal of attacks with a new Remote Access Trojan, that is attacking targets on Windows and mobile devices.

The group, known for malicious attacks such as RedEyes or ScarCruft, is based in North-Korean and believed to be supported by the North-Korean state.
AhnLab Security Emergency response Center published a new report today that provides information on APT37's latest activities. According to the report, which is available in Korean only, AhnLab researchers provide information on the latest malware that APT37 uses it its attacks.
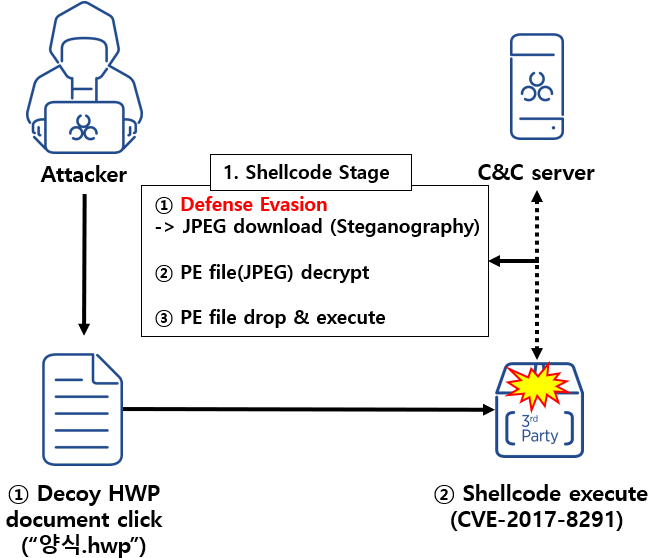
The attack begins with phishing emails being sent out to targets of the attacks. The current attack exploits an old vulnerability in EPS in the Hangul word processor, which is used in South Korea predominantly.
EPS, which stands for Encapsulated PostScript) files, is a vector file format for professional and high-quality printing. Created by Adobe in the late 1980s, EPS was designed to "make it easier to incorporate images and illustrations into predominantly text-based creations".
Victims who launch the attachment trigger the exploit code, which will download and then execute additional malware stored within a JPEG image. The specially crafted JPEG image uses steganographic techniques to hide the malware. It executes the M2RAT named malware, with the filename lskdjfei.exe, on the system. The malware injects itself into the explorer.exe process and creates a new startup Registry key to ensure that the system remains infected after restarts.
The startup entry is created using a PowerShell script that is run via the Command Prompt. The threat group used the technique before in an attack in 2021.
Remote Access Trojan
M2RAT is a remote access trojan that runs a wide range of malicious activities on infected user systems. These range from logging keystrokes to capturing screenshots, executing commands on the system and the copying of data and sending of the data to remote locations.
Some of the operations, the screen capturing component for instance, act automatically, while other activities require remote commands.
The malware includes functionality to scan mobile devices connected to the Windows device. When it detects a mobile device connection, e.g., that of a smartphone or tablet, it will scan the device for specific types of data. Data that it is interested in includes voice recordings and documents. Any data that is found during the scan is then copied to the PC and transferred to a remote location.
The malware compresses data by creating password-protected RAR archives. Local copies are deleted to make it more difficult to trace the operation. M2RAT operates in memory on host devices, which does make detection and analysis of the malware more difficulty according to the analysis.
The attack seems to target users in South Korea specifically, but there is a possibility that the attack may be adjusted to exploit vulnerabilities in other programs that support EPS, or that attacks use different file types in attacks. (via Bleepingcomputer)


















