Microsoft Script to restore (some) deleted Windows shortcuts after Defender ASR incident
News broke on Friday the 13th that Windows users from all over the world were noticing that application shortcuts on the taskbar and Start Menu were no longer accessible.

Microsoft confirmed the issue quickly and identified a security intelligence update build as the culprit for the issue. The company stopped the update and published a new fixed build that it released shortly thereafter.
Back then, Microsoft stated that users and administrators were on their own regarding the lost shortcuts. Now, it appears, that Microsoft has created a solution to resolve the issue on impacted systems.
In an update to Friday's Tech community post about the issue, the company says that it has "confirmed steps that customers can take to recreate start menu links for a significant sub-set of the affected applications that were deleted".
Microsoft created a PowerShell script that helps Enterprise administrators in recovering shortcuts on systems that they manage.
Note: while the script has been created for Enterprise administrators and Enterprise environments, it may also run in other environments; this has not been tested, but affected users may want to give it a try if they experienced the issue.
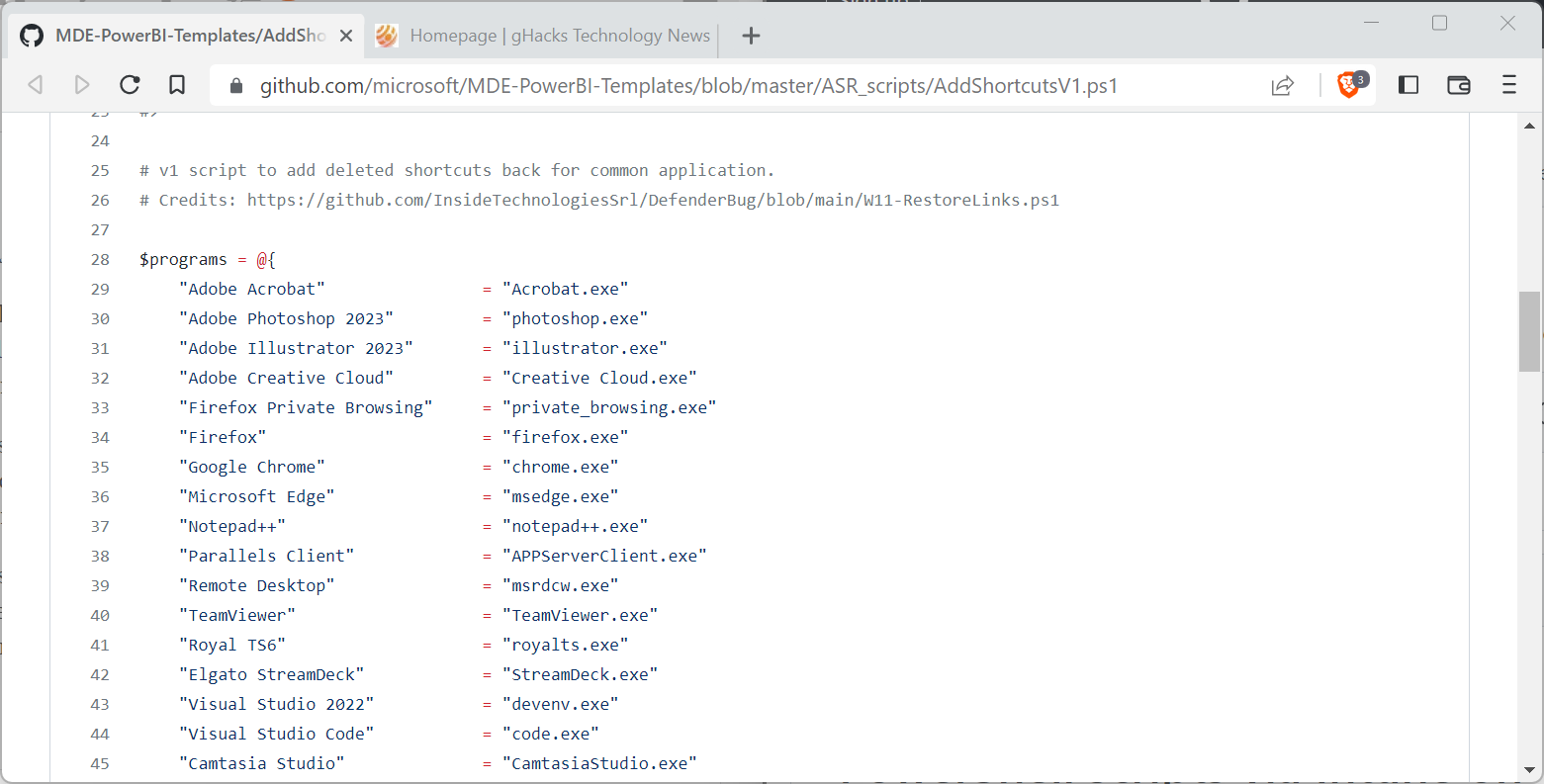
The Script is available on GitHub and includes a, rather short, list of applications and their executable files. The list is dominated by Microsoft applications, but administrators find third-party apps such as Notepad++, 7-Zip, Firefox, or Camtasia Studio as well in the listing.
The script queries a key in the Registry to determine if the listed programs are installed on the system. If they are, it checks if the shortcut exists, and if that fails, will create it.
Administrators may modify the script to add more applications to the listing. All that is required for that is to add a new line to the list of applications array using the provided syntax (which merely is "Application Name" = "filename").
The PowerShell script needs to be run with elevated privileges, either as admin or system, according to Microsoft. Instructions on running the script using Microsoft Intune are available on this GitHub page.
Administrators may also restore shortcuts manually by running application repairs on affected applications. Microsoft 365, Microsoft Edge and Microsoft Visual Studio include application repair functionality.
Administrators may run advanced hunting queries to determine the impact of the issue on their environment. Microsoft lists the available queries here. Basically, the queries retrieve events, block or otherwise, that were triggered by the broken ASR rule.
Closing Words
Microsoft's script offers limited assistance in fixing the issue. The script includes only 33 applications by default and restores shortcuts only in Start and not on the taskbar.
While administrators may add more programs to the listing, it is not an ideal solution. The script may not always restore shortcuts according to comments published by some users on the Tech community webpage.
All in all, it seems that many administrators are on their own when it comes to recovering shortcuts in their environments.





















Microsoft’s problem is they haven’t diversified their workforce enough yet. Once they do the problems will be solved.
Microsoft quality department is dump. Absolute nonsense and creepiest fiasco ever with Defender. Just get Configure Defender 3.111, set cloud protection to highest, activate PUA protection and disable as most ASR rules you can, the best solution at long term witht this buggy MS team!
My father pointed me that there is no need to disable ASR rules, just add to exclusions the *.lnk shorcuts file extension. This should prevent other big issue has the latest one with ASR rules! :]
Nothing to see here – this is professionalism, Microsoft isn’t making Windows into a joke!
I left Windows 10 for 7 when I realized that we users are the new beta testing department of the OS Microsoft will sell to corporates at high price. It was a good decision.
Imagine that there are switches and functions to compromise or completely deactivate systems be that Computers, Airplanes, Mobilephones, Cars, Firewalls with built in backdoors, any other digitally controlled equipment which could one day fall under US export restrictions.
Such a high quality product, after Bill Gates resigned the company has turned into a clown.
Haha. Microsoft is utterly awful at making software. What a disgusting company.