Workaround for Windows 10 and 11 HiveNightmare Windows Elevation of Privilege Vulnerability
Earlier this week, security researchers discovered a vulnerability in recent versions of Microsoft's Windows operating system that allows attackers to run code with system privileges if exploited successfully.
Overly permissive Access Control Lists (ACLs) on some system files, including the Security Accounts Manager (SAM) database, are causing the issue.
An article on CERT provides additional information. According to it, the BUILTIN/Users group is given RX permission (Read Execute) to files in %windir%\system32\config.
If Volume Shadow Copies (VSS) are available on the system drive, unprivileged users may exploit the vulnerability for attacks that may include running programs, deleting data, creating new accounts, extracting account password hashes, obtain DPAPI computer keys, and more.
According to CERT, VSS shadow copies are created automatically on system drives with 128 Gigabytes or more storage space when Windows updates or MSI files are installed.
Administrators may run vssadmin list shadows from an elevated command prompt to check if shadow copies are available.
Microsoft acknowledged the issue in CVE-2021-36934, rated the severity of the vulnerability as important, the second highest severity rating, and confirmed that Windows 10 version 1809, 1909, 2004, 20H2 and 21H1, Windows 11, and Windows Server installations are affected by the vulnerability.
Test if your system may be affected by HiveNightmare
- Use the keyboard shortcut Windows-X to display the "secret" menu on the machine.
- Select Windows PowerShell (admin).
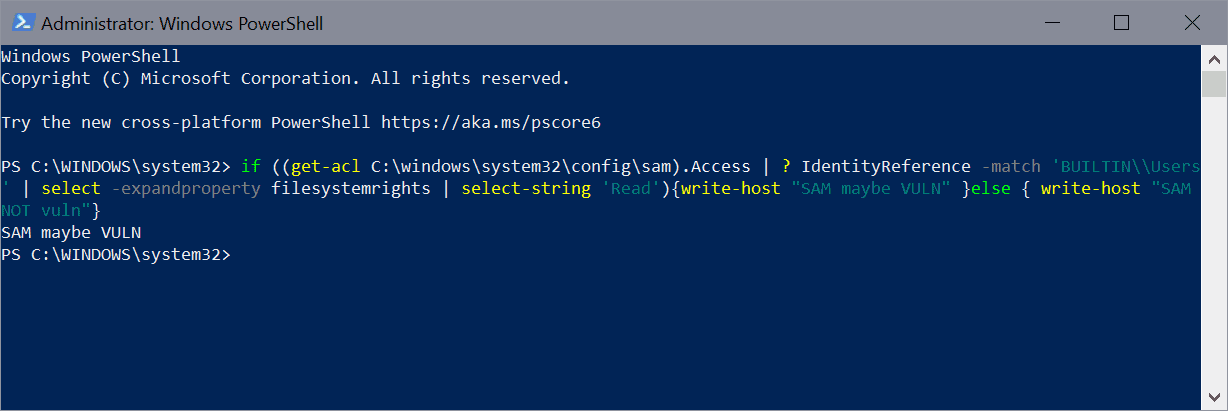
- Run the following command: if ((get-acl C:\windows\system32\config\sam).Access | ? IdentityReference -match 'BUILTIN\\Users' | select -expandproperty filesystemrights | select-string 'Read'){write-host "SAM maybe VULN" }else { write-host "SAM NOT vuln"}
If "Sam maybe VULN" is returned, the system is affected by the vulnerability (via Twitter user Dray Agha)

Here is a second option to check if the system is vulnerable to potential attacks:
- Select Start.
- Type cmd
- Select Command Prompt.
- Run icacls %windir%\system32\config\sam
A vulnerable system includes the line BUILTIN\Users:(I)(RX) in the output. Non-vulnerable system will display an "access is denied" message.
Workaround for the HiveNightmare security issue
Microsoft published a workaround on its website to protect devices against potential exploits.
Note: deleting shadow copies may have unforeseen effects on applications that use Shadow Copies for their operations.
Administrators may enable ACL inheritance for files in %windir%\system32\config according to Microsoft.
- Select Start
- Type cmd.
- Pick Run as administrator.
- Confirm the UAC prompt.
- Run icacls %windir%\system32\config\*.* /inheritance:e
- vssadmin delete shadows /for=c: /Quiet
- vssadmin list shadows
Command 5 enables ACL interheritance. Command 6 deletes shadow copies that exist and Command 7 verifies that all shadow copies have been deleted.
Now You: is your system affected?



















Hi, I guess that (F) stands for Full Control but what does the (I) mean in the output?
From the link rgearding the vulnerability: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934
“Attack vector = Local”
ie.
”
The vulnerable component is not bound to the network stack and the attacker’s path is via read/write/execute capabilities. Either: the attacker exploits the vulnerability by accessing the target system locally (e.g., keyboard, console), or remotely (e.g., SSH); or the attacker relies on User Interaction by another person to perform actions required to exploit the vulnerability (e.g., tricking a legitimate user into opening a malicious document)
”
so it seems this is a non-issue for most, isn’t it?
If Volume Shadow Copies (VSS) are available on the system drive, and you have an SSD drive, is going to have HALF life, thanks to the VSS write back and forth. Disabled Long Time ago thanks to info from O&O Defragment/Trim program…
Not vulnerable.
As an admin, I don’t have read permission to C:\Windows\System32\config. Can’t even open it.
I can take ownership, change the permissions then restore the defaults but don’t care to or need to.
Seems an easy problem to fix in Pro; whether Home, the ad server, allows it, IDK. The CERT doc cites “multiple versions of windows,” not at all helpful, which ones???
First command result: “SAM NOT vuln”
Second command result includes: “BUILTIN\Administrators:(I)(F)”, but not an “access is denied” message, and no lines with “(I)(RX)” in the result, just “(I)(F)”.
Will wait for Microsoft patch.
I’m with ilev on this one.
It’s irresponsible of you to reccomend deleting shadow copies with out first stating in BIG BOLD TEXT what the consequences of doing so will be.
“If Volume Shadow Copies (VSS) are available on the system drive, unprivileged users may exploit the vulnerability for attacks…”
So if I trust the local “users” (me and wife) which of course I do, then there is no issue.
If bad actors have got an unprivileged user access to your computer, the bad actor can escalate its privilege to SYSTEM and run bad code.
I ran the workaround and still get “Sam maybe VULN.”
Did you restart your PC after making the changes?
I ran the Power Shell script, and it showed that my system was in fact affected by the vulnerability. I then ran the workaround which showed that my system had no shadow copies. So now I guess I am supposed to keep running the workaround regularly until Microsoft gets around to fixing this.
I’m sooooo glad I run Windows 8.1. :)
So glad I use Windows 7 ESU. No botched patches, no forced crap. Windows 7 is last good version of Windows.
“Now You: is your system affected?”
Was vulnerable. Not now. Thanks.
Don’t run Microsoft’s stupid workaround deleting VSS files. You won’t be able to restore to previous versions nor restore backups.
Don’t do anything. Wait for a proper fix.
Your assumption is not correct. I removed VSS and all restore points. Then I successfully made a drive image using Macrium Reflect 8. The image was 2-GB smaller than the one I made the day before. So, one can make drive images without VSS.
BetaNews has a much better article detailing the problems with deleting “existing” VSS:
“Impact of workaround Deleting shadow copies could impact restore operations, including the ability to restore data with third-party backup applications.”
That means the workaround may possible affect a 3rd party program backup.
“Note that any capabilities relying on existing shadow copies, such as System Restore, will not function as expected. Newly-created shadow copies, which will contain the proper ACLs, will function as expected”
https://betanews.com/2021/07/21/hivenightmare-security-vulnerability-windows-10-windows-11-registry/
It’s unfortunate gHacks doesn’t provide the entire picture.
The powershell command does not work. It always outputs “Sam maybe VULN”.
Although I have run both recommended commands:
Run icacls %windir%\system32\config\*.* /inheritance:e
vssadmin delete shadows /for=c: /Quiet
Did you restart the system after you made the changes?
For Step 6:
vssadmin delete shadows /for=c: /Quiet
It failed. I simply removed the “/Quiet” and it gave me a Y/N prompt and worked successfully from there.
Thank you for posting this Martin.