Find out if your email and phone number were in Facebook's latest data breach
In April 2021, a large set of Facebook user data was published on the Internet. The data included information on 533 million Facebook users and included dates of births, email addresses, phone numbers, geographic locations, names, or genders.
Not all of the data was complete, but about 2.5 million accounts had their email addresses leaked along with other data. Malicious actors can use the entire data set to link phone numbers to names, and the subset that contained email addresses for attacks against these accounts, e.g. through phishing emails or brute force hacking.
Have I Been Pwned is a free site on the Internet that feeds an ever growing database with public data leaks so that users from all around the world may search it.
All it takes is to type an email address to find out if it was included in any of the data breaches that the site has in its database.

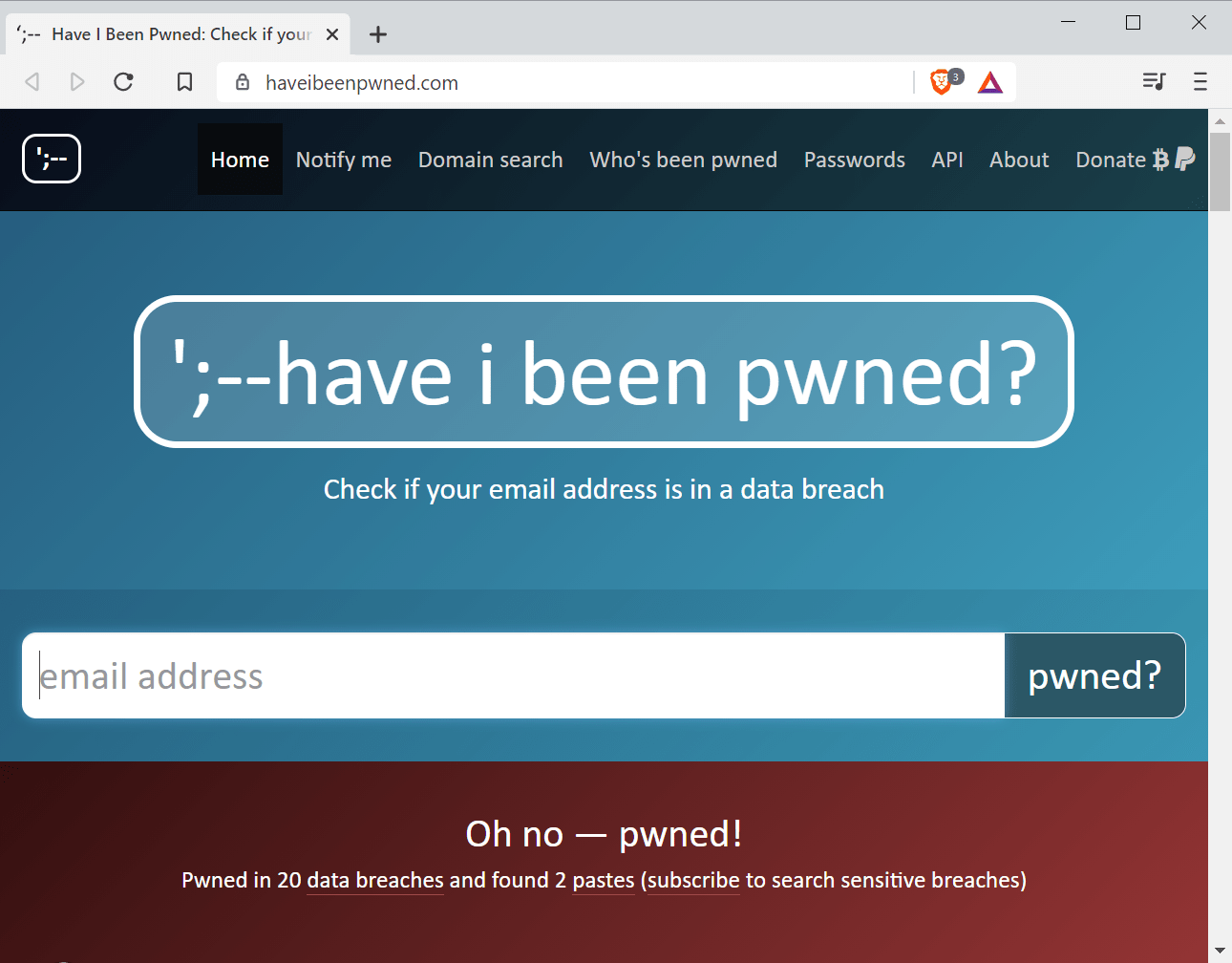
All you need to do is visit the homepage of the Have I Been Pwned service, type an email address, and click on the pwned? button to run a search for itt in the database.
All hits are listed on the results page. To find out if the email address was included in the Facebook leak, check if Facebook is among the listed services the email address was found in.
Only accounts that included the email address can be searched. The developer of the service, Troy Hunt, mentioned on Twitter that he won't add phone search capabilities to the site because it would be a lot of work and would not provide much value.
What you need to do if your account email has been leaked
The leaked data sets did not include password hashes it appears, but certain forms of attacks are very likely ranging from phishing emails and spam to trying to find the email address or phone number in other breaches, and hacking into accounts.
If the email address has been leaked, it is a good idea to change the password on all sites the email address was used on.
Now You: do you use services like Have I Been Pwned or Firefox Monitor to find out if your data was leaked on the Internet?






















Martin the new frontpage layout sucks. Please do a user poll to see how much your old layout was better
I know you’ll just ignore me because you’re a busy boi.
The joke’s on them, I don’t use Facebook.
Webservices like this are great, but lets face it, inputting your actual email address and or phone number yourself, is like flagging your data as actually valid.
Now queue the troll comments.
@pwned,
> Webservices like this are great, but lets face it, inputting your actual email address and or phone number yourself, is like flagging your data as actually valid.
Now queue the troll comments.
In response to your request (Now queue the troll comments),
In general, your opinion is reasonable.
However,
“Have I Been Pwned” is the user’s free will whether to use it or not.
If you don’t trust it, just ignore it (don’t use it).
There’s a fine line between being wary of risks and being paranoid, and It’s wisdom (skills: knowledge and experience).
It is more important to overlook the actual risk (leakage of one’s account information, etc.) because of the fear of risk. If it has been leaked, you need to take immediate action. If left unchecked, the severity will be immeasurable.
Instagram named the most invasive social media in the world, now Facebook, the most UNPROFESSIONAL PRETENDING PROFESSIONAL technology company in the world (PROVE ME WRONG), why can’t those malakas Future-Proof your stuff, and other poor voluntarily people sacrifice their data for the God Of Social Media Facebook, such a failure, don’t work at Facebook, bad company, with a lot of stupid history, Facebook is constantly under siege, protection is like just for fun and for beauty, time to [[[[[QUIT FACEBOOK]]]]]. This is not all about hate, but also about love for those poorly affected people, and the lists will go on and on, you just have to wait, counting down.
Sorry but thouse people are fully to blame for this.
They put their TRUST in Mark the SUCKERman wich is a corporate evil psycho and he does what all psychos do wich is treat people like objects and not human beings.
They are far to NAIVE and they have to learn to NEVER TRUST anybody with BILLONS of $$$.
A clickable link would be preferable instead of reading the URL at the top of the first image.
Right, added it!
I still dislike the new ghacks facelift.
Looks like the search button has been moved from the main page to the bottom. Now I gotta scroll down to click on it. Why keep ruining the main page?
this isn’t ghacks anymore, whatever they say.
it’s essence has been diluted.
You can bookmark this URL and have gHacks back
https://www.ghacks.net/?s
Thank you!
The facelift is a facelift, dont like it, dont look at it.
You can always change the CSS and redesign the site to your liking.
@pwned I am simply voicing the fact that I still couldn’t get used to it with time; concerning functionality and looks. The new dark color is an improvement in the first regard.
You make it sound like modifying CSS/JS is a trivial task even for ghacks readers!
@Yuliya Thanks
Not a single facebook user would be interested in this.
Anyone who enters their personal information on facebook clearly doesn’t value it enough to be concerned about its privacy.
Pretty much this. Every agency knows about them anyway, what difference a couple of skiddies makes at this point?
> Now You: do you use services like Have I Been Pwned or Firefox Monitor to find out if your data was leaked on the Internet?
I use the password manager “KeePass Password Safe” regularly, and I’ve added the Have I Been Pwned database locally to audit my passwords.
Check all your KeePass passwords locally against the Have I Been Pwned database|gHacks Tech News
https://www.ghacks.net/2019/01/18/check-all-keepass-passwords-against-the-have-i-been-pwned-database-locally/
I learned about the “new Facebook incident: account email has been leaked” in a newsletter from the Have I Been Pwned’s provider, troyhunt.com, and two days ago, checked “all my account IDs” just in case (I don’t use Facebook).
As a result, I was able to reconfirm that it does not exist in the “leaked” database of Have I Been Pwned.
About “Have I Been Pwned”,
Have I Been Pwned: Who, what & why
https://haveibeenpwned.com/About
Who, what & why
The background on the who, the what and the why of Have I Been Pwned
Troy Hunt Profile Picture
Who is behind Have I Been Pwned (HIBP)
I’m Troy Hunt, a Microsoft Regional Director and Most Valuable Professional awardee for Developer Security, blogger at troyhunt.com, international speaker on web security and the author of many top-rating security courses for web developers on Pluralsight.
I created HIBP as a free resource for anyone to quickly assess if they may have been put at risk due to an online account of theirs having been compromised or “pwned” in a data breach. I wanted to keep it dead simple to use and entirely free so that it could be of maximum benefit to the community.
Short of the odd donation, all costs for building, running and keeping the service currently come directly out of my own pocket. Fortunately, today’s modern cloud services like Microsoft Azure make it possible to do this without breaking the bank!
What is the site all about?
This site came about after what was, at the time, the largest ever single breach of customer accounts — Adobe. I often did post-breach analysis of user credentials and kept finding the same accounts exposed over and over again, often with the same passwords which then put the victims at further risk of their other accounts being compromised.
The FAQs page goes into a lot more detail, but all the data on this site comes from “breaches” where data is exposed to persons that should not have been able to view it.
Why build the site?
This site serves two primary purposes for me: firstly, it obviously provides a service to the public. Data breaches are rampant and many people don’t appreciate the scale or frequency with which they occur. By aggregating the data here I hope that it not only helps victims learn of compromises of their accounts, but also highlights the severity of the risks of online attacks on today’s internet.
Secondly, the site provided me with an excellent use case for putting a number of technologies through their paces and keeping my hands-on skills somewhat current. Projects like this are an excellent way of staying relevant as my day job increasingly focuses more on software management and less on actually building things (which I happen to love doing!) It’s been an enormously fulfilling journey that I’ve invited others to join me on by way of often blogging in depth about the process, something I intend to keep up as the site inevitably evolves over time.
Have I Been Pwned: FAQs
https://haveibeenpwned.com/FAQs
Troy Hunt: About | troyhunt.com
https://www.troyhunt.com/about/
LOL… This article is missing a clickable link to the “have i been pwned” site, likely resulting in some people typing in Troy’s URL wrong, and getting pwned in the process.
Here is the correct link:
https://haveibeenpwned.com/
I’ve used Troy Hunt’s site before and it’s handy.
Martin, perhaps you should add a link to the site?
Did that, thanks.
Have I Been Pwned: Check if your email has been compromised in a data breach
https://haveibeenpwned.com/
imagine using faecesbook in this day and age…
Oh enlighten us, what people should use from social media if they really have to? Perhaps… VKontakte?
Telegram.
…And complaining about private data leaks. Although the leaked gender list will provide an interesting read.
@Yuliya,
> imagine using faecesbook in this day and age…
Have I Been Pwned’s “leaked” database is not limited to the one from the Facebook.
https://haveibeenpwned.com/PwnedWebsites#Facebook
There is also includes “known” leaked data that has been leaked to the black market, as well as data that has been found to be misused by financial institutions.
Have I Been Pwned: Pwned websites
https://haveibeenpwned.com/PwnedWebsites
The severity of this problem ranges from hacking into sites (such as online shopping, financial institutions, government agencies, social networks, etc.) to theft and leakage from breaches of my and other’s PC and other systems.
In today’s society, we have no choice but to use some kind of online service, which leads to the “sharing of personal information” with others (relatives, friends, communities, employers, government agencies, etc.).
In other words, there is a concern that the information may be leaked from these other parties even if the individual has taken all possible measures to prevent it.
In addition to doing our best to manage personal information, it is important to limit the data we share and the people we share it with.
It was reported that the personal information of more than 500 million users was leaked from Facebook, and it was newly discovered that the personal information of 500 million people was also leaked from LinkedIn, a business-focused social networking service, and is being traded on hacking forums.
Scraped data of 500 million LinkedIn users being sold online, 2 million records leaked as proof | CyberNews
https://cybernews.com/news/stolen-data-of-500-million-linkedin-users-being-sold-online-2-million-leaked-as-proof-2/
The leak of personal information from LinkedIn was discovered when CyberNews found a “post on a hacking forum offering to trade personal information of 500 million LinkedIn users. The post also offered to sell the personal information of 2 million people for about $2 (about $220) as proof that the personal information was genuine.
CyberNews purchased a sample and found that the data being traded included “LinkedIn ID”, “full name”, “email address”, “phone number”, “gender”, “links to LinkedIn profiles”, “links to other social networking sites where you are registered”, and “professional titles and work-related information”.
CyberNews noted that attacks such as “targeted phishing attacks”, “sending spam to 500 million users”, and “revealing passwords through brute force attacks” have been successful.
“For a capable cybercriminal, an email address alone could be enough to cause damage”, CyberNews said, emphasizing the seriousness of the leak.
CyberNews recommends the following measures to protect yourself from those attackers.
â— Be aware of suspicious messages and contact from strangers.
â— Change your email address and password for LinkedIn.
â— Use a password manager to create and manage strong passwords.
â— Enable multi-factor authentication for all of your online accounts.
About LinkedIn
https://about.linkedin.com/
Welcome to LinkedIn, the world’s largest professional network with nearly
740 million members in more than 200 countries and territories worldwide.
LinkedIn leads a diversified business with revenues from membership subscriptions, advertising sales and recruitment solutions under the leadership of Ryan Roslansky. In December 2016, Microsoft completed its acquisition of LinkedIn, bringing together the world’s leading professional cloud and the world’s leading professional network.
LinkedIn | Wikipedia
https://en.wikipedia.org/wiki/LinkedIn
LinkedIn (/lɪŋktˈɪn/) is an American business and employment-oriented online service that operates via websites and mobile apps. Launched on May 5, 2003,[4] the platform is mainly used for professional networking, and allows job seekers to post their CVs and employers to post jobs. As of 2015, most of the company’s revenue came from selling access to information about its members to recruiters and sales professionals.[5] Since December 2016, it has been a wholly owned subsidiary of Microsoft. As of February 2021, LinkedIn had 740 million registered members from 150 countries.[3]
LinkedIn: Security and technology
Main article:
In June 2012, cryptographic hashes of approximately 6.4 million LinkedIn user passwords were stolen by Yevgeniy Nikulin and other hackers who then published the stolen hashes online.[164] This action is known as the 2012 LinkedIn hack. Security experts criticized LinkedIn for not salting their password file and for using a single iteration of SHA-1.[165]
On May 31, 2013 LinkedIn added two-factor authentication, an important security enhancement for preventing hackers from gaining access to accounts.[166]
In May 2016, 117 million LinkedIn usernames and passwords were offered for sale online for the equivalent of $2,200.[167] These account details are believed to be sourced from the original 2012 LinkedIn hack, in which the number of user IDs stolen had been underestimated. To handle the large volume of emails sent to its users every day with notifications for messages, profile views, important happenings in their network, and other things, LinkedIn uses the Momentum email platform from Message Systems.[168]
In 2014, Dell SecureWorks Counter Threat Unit (CTU) discovered that Threat Group-2889, an Iran-based group, created 25 fake LinkedIn accounts.
According to reporting by Le Figaro, France’s General Directorate for Internal Security and Directorate-General for External Security believe that Chinese spies have used LinkedIn to target thousands of business and government officials as potential sources of information.[170]
In 2017, Germany’s Federal Office for the Protection of the Constitution (BfV) published information alleging that Chinese intelligence services had created fake social media profiles on sites such as LinkedIn, using them to gather information on German politicians and government officials.[171][172]
Moving emails to LinkedIn servers[edit]
At the end of 2013, it was announced that the LinkedIn app intercepted users’ emails and silently moved them to LinkedIn servers for full access.[173] LinkedIn used man-in-the-middle attacks.[174]
LinkedIn: Privacy policy
The German Stiftung Warentest has criticized that the balance of rights between users and LinkedIn is disproportionate, restricting users’ rights excessively while granting the company far-reaching rights.[175] It has also been claimed that LinkedIn does not respond to consumer protection center requests.[176]
In November 2016, Russia announced its intention to block the network in its own country, as it “illegally stores data of Russian users on servers abroad.” The relevant law had been in force there since 2014.[177][178]
Potential 2018 breach, or extended impacts from earlier incidents[edit]
In July 2018, Credit Wise reported “dark web” email and password exposures from LinkedIn. Shortly thereafter, users began receiving extortion emails, using that information as “evidence” that users’ contacts had been hacked, and threatening to expose pornographic videos featuring the users.