Microsoft Security Bulletins May 2016
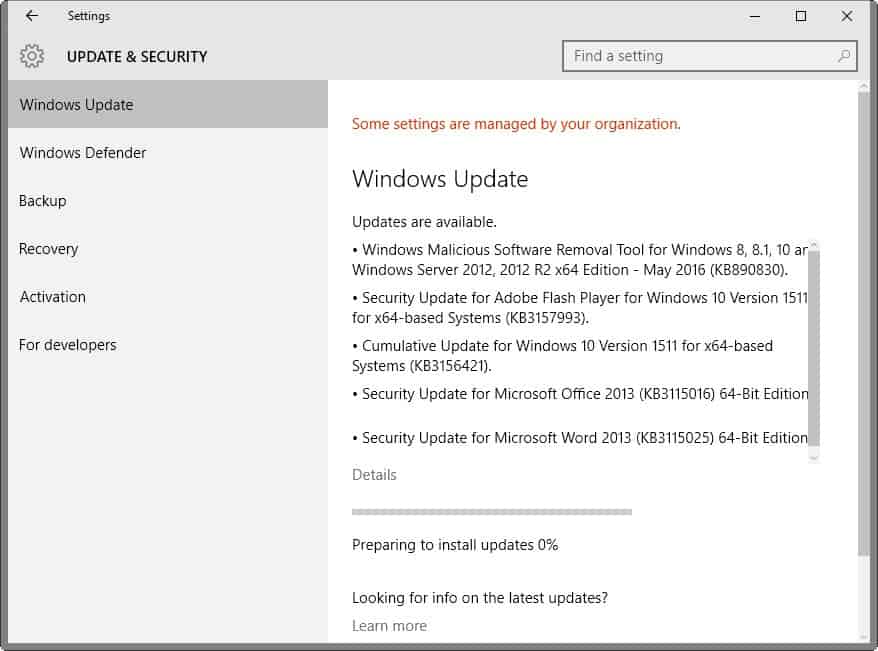
The Microsoft Security Bulletins May 2016 overview provides you with information about the May 2016 Patch Day for Windows and other Microsoft products.
The overview lists all security and non-security patches that Microsoft released for client and server versions of the Windows operating system.
All link to Microsoft Knowledge Base pages or other resources that allow you to find out more about individual patches.
The patch overview begins with a summary of the most important information. It is followed by the operating system and other Microsoft products distribution that highlights all products for which patches have been released.
This is followed by the list of security bulletins and patches, and information on how to download the patches to local systems.
Microsoft Security Bulletins May 2016

Executive Summary
- Microsoft released a total of 16 security bulletins in May 2016 that patch security issues in Microsoft Windows, Microsoft Office, and other company products.
- Eight security bulletins have received a maximum severity rating of critical, the other eight one of important.
Operating System Distribution
The extra critical bulletin that Windows Vista is affected by (MS16-053) patches a vulnerability in JScript and VBScript.
The extra critical bulletin that Windows 8.1, 8.1 RT and Windows 10 are affected by is MS16-064. It patches the built-in Adobe Flash Player in Internet Explorer and Microsoft Edge.
Windows 10 finally is also affected by the critically rated bulletin MS16-052 which fixes a critical vulnerability in Microsoft Edge.
- Windows Vista: 3 critical, 3 important
- Windows 7: 2 critical, 3 important
- Windows 8.1: 2 critical, 3 important
- Windows RT 8.1: 3 critical, 3 important
- Windows 10: 4 critical, 3 important
- Windows Server 2008: 1 critical, 3 important, 2 moderate
- Windows Server 2008 R2: 1 critical, 3 important, 1 moderate
- Windows Server 2012 and 2012 R2: 1 critical, 3 important, 2 moderate
- Server core: 1 critical, 3 important, 1 moderate
Other Microsoft Products
Patches for the following non-Windows Microsoft products were released this month:
- Microsoft Office 2007, 2010 and 2013: 1 critical
- Microsoft Office 2013 RT: 1 critical
- Microsoft Office 2016: 1 critical
- Microsoft Office for Mac 2011, 2016: 1 critical
- Microsoft Office Compatibility Pack SP3,Word Viewer: 1 critical
- Microsoft SharePoint Server 2010: 1 critical
- Microsoft Office Web Apps 2010: 1 critical
Security Bulletins
MS16-051 - Cumulative Security Update for Internet Explorer (3155533) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user.
MS16-052 - Cumulative Security Update for Microsoft Edge (3155538) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge.
MS16-053 - Cumulative Security Update for JScript and VBScript (3156764) - Critical - Remote Code Execution
This security update resolves vulnerabilities in the JScript and VBScript scripting engines in Microsoft Windows. The vulnerabilities could allow remote code execution if a user visits a specially crafted website.
MS16-054 - Security Update for Microsoft Office (3155544) - Critical - Remote Code Execution
The vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file.
MS16-055 - Security Update for Microsoft Graphics Component (3156754) - Critical - Remote Code Execution
The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a specially crafted website.
MS16-056 -Â Security Update for Windows Journal (3156761) - Critical - Remote Code Execution
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted Journal file.
MS16-057 - Security Update for Windows Shell (3156987) - Critical - Remote Code Execution
The vulnerability could allow remote code execution if an attacker successfully convinces a user to browse to a specially crafted website that accepts user-provided online content, or convinces a user to open specially crafted content.
MS16-058 - Security Update for Windows IIS (3141083) - Important - Remote Code Execution
The vulnerability could allow remote code execution if an attacker with access to the local system executes a malicious application.
MS16-059 - Security Update for Windows Media Center (3150220) - Important - Remote Code Execution
The vulnerability could allow remote code execution if Windows Media Center opens a specially crafted Media Center link (.mcl) file that references malicious code.
MS16-060 - Security Update for Windows Kernel (3154846) - Important - Elevation of Privilege
The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-061 - Security Update for Microsoft RPC (3155520) - Important - Elevation of Privilege
The vulnerability could allow elevation of privilege if an unauthenticated attacker makes malformed Remote Procedure Call (RPC) requests to an affected host.
MS16-062 - Security Update for Windows Kernel-Mode Drivers (3158222) - Important - Elevation of Privilege
The more severe of the vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-064 - Security Update for Adobe Flash Player (3157993) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, and Windows 10.
MS16-065 - Security Update for .NET Framework (3156757) - Important - Information Disclosure
This security update resolves a vulnerability in Microsoft .NET Framework.
The vulnerability could cause information disclosure if an attacker injects unencrypted data into the target secure channel and then performs a man-in-the-middle (MiTM) attack between the targeted client and a legitimate server.
MS16-066 - Security Update for Virtual Secure Mode (3155451) - Important - Security Feature Bypass
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow security feature bypass if an attacker runs a specially crafted application to bypass code integrity protections in Windows.
MS16-067 - Security Update for Volume Manager Driver (3155784) - Important - Information Disclosure
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure if a USB disk mounted over Remote Desktop Protocol (RDP) via Microsoft RemoteFX is not correctly tied to the session of the mounting user.
Security advisories and updates
Microsoft Security Advisory 3155527 - Update to Cipher Suites for FalseStart
FalseStart allows the TLS client to send application data before receiving and verifying the server Finished message.
This allows an attacker to launch a man-in-the-middle (MiTM) attack to force the TLS client to encrypt the first flight of application_data records using the attacker’s chosen cipher suite from the client’s list.
To avoid downgrade attacks, TLS clients only allow FalseStart when their strongest cipher suites are negotiated.
Non-security related updates
- Update for Windows Server 2012 R2 and Windows Server 2012 (KB3159706) - Update enables ESD decryption provision in WSUS in Windows Server 2012 and Windows Server 2012 R2.
- Update for Windows 8.1, Windows 8, and Windows 7 (KB3150513) - May 2016 Compatibility Update for Windows. This update provides updated configuration and definitions for compatibility diagnostics performed on the system. The updated definitions will improve accuracy and help enable Microsoft and its partners ensure compatibility for customers who want to install the latest Windows operating system.
- Update for Windows 8.1 and Windows 7 (KB3035583) - Update installs Get Windows 10 app in Windows 8.1 and Windows 7 SP1.
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3103616) - WMI query doesn't work in Windows Server 2012 R2 or Windows Server 2012.
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3103709) - Windows Server 2012 R2-based domain controller update, April 2016.
- Update for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows Embedded 8 Standard, and Windows Server 2012 (KB3125424) - LSASS deadlocks cause Windows Server 2012 R2 or Windows Server 2012 not to respond.
- Update for Windows Server 2012 R2 (KB3134179) - Update adds performance counters for Remote Desktop Connection Broker in Windows Server 2012 R2.
- Update for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows Embedded 8 Standard, Windows Server 2012, Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB3138378) - Update for Journal.dll binary in Windows.
- Update for Windows Server 2008 and Windows Vista (KB3139921) - "No computer account for trust" error when you change domain account password in Windows
- Update for Windows Embedded 8 Standard, Windows Server 2012, Windows 7, and Windows Server 2008 R2 (KB3140245) - A new registry key enables TLS 1.1 and TLS 1.2 to default secure protocols in WinHTTP in Windows.
More information for KB3140245
32-bit Windows key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp
64-bit Windows key (add 32-bit also): HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp
Values:
| DefaultSecureProtocols Value | Protocol enabled |
|---|---|
| 0x00000008 | Enable SSL 2.0 by default |
| 0x00000020 | Enable SSL 3.0 by default |
| 0x00000080 | Enable TLS 1.0 by default |
| 0x00000200 | Enable TLS 1.1 by default |
| 0x00000800 | Enable TLS 1.2 by default |
- Update for Windows Server 2012 R2 (KB3143777) - Cluster service fails when shutting down or data deduplication fails with "Drive is locked" in Windows Server 2012 R2.
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3144474) - TFS application pool and Certreq.exe crash after security update 3081320 is installed in Windows Server 2012 R2.
- Update for Windows 8.1 and Windows Server 2012 R2 (KB3144850) - Update enables downgrade rights between Windows 10 IoT and Windows Embedded 8.1 Industry.
- Update for Windows Server 2008 R2 x64 Edition (KB3145126) - Loading DNS zones takes a long time on a Windows Server 2008 R2-based DNS server.
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3145384) - MinDiffAreaFileSize registry value limit is increased from 3 GB to 50 GB in Windows 8.1 or Windows Server 2012 R2.
- Update for Windows Server 2012 R2 (KB3145432) - Cluster nodes or VMs go offline when they are using VMQ capable NICs on a Windows Server 2012 R2 host.
- Update for Windows Embedded 8 Standard and Windows Server 2012 (KB3146600) - Wbengine.exe crashes when you run a backup on a GPT formatted drive in Windows Server 2012.
- Update for Windows 8.1 and Windows Server 2012 R2 (KB3146601) - GPO import fails and rollback results in the target policy being deleted on a Windows Server 2012 R2-based DC.
- Update for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, and Windows Server 2012 (KB3146604) - WMI service crashes randomly in Windows Server 2012 R2 or Windows Server 2012.
- Update for Windows Server 2012 R2 (KB3146621) - iSCSI target service crashes randomly in Windows Server 2012 R2.
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3146627) - Network drives aren't mapped correctly from DFS namespace in Windows Server 2012 R2-based RDS server.
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3146751) - "Logon is not possible" error or a temporary file is created when you log on App-V in Windows Server 2012 R2.
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3146978) - RDS redirected resources showing degraded performance in Windows 8.1 or Windows Server 2012 R2.
- Update for Windows Server 2012 R2 (KB3148146) - Some printer settings are not restored correctly when you use Printbrm.exe in Windows Server 2012 R2.
- Update for Windows Server 2012 R2 (KB3148217) - High network usage after you implement file screening on a Windows Server 2012 R2-based Work Folders sync server.
- Update for Windows 8.1, Windows Server 2012 R2, and Windows Server 2012 (KB3148812) -
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB3149157) - Reliability and scalability improvements in TCP/IP for Windows 8.1 and Windows Server 2012 R2.
May 10th Cumulative Update for Windows 10 (KB3156421)
Note: Some users report slow PCs after installing this update.
- Improved reliability in a number of areas including Cortana, Bluetooth, Shell, Internet Explorer 11, Microsoft Edge, Miracast, and USB.
- Fixed memory leak that occurs when opening a portable document format (PDF) form multiple times.
- Fixed issues with text alignment for right to left languages in Internet Explorer 11 and Microsoft Edge.
- Fixed issue that affected Bluetooth function when a PC resumes from sleep.
- Fixed issue where user accounts weren't locked out after a number of failed sign in attempts.
Fixed issue with revised daylight saving time. - Fixed issue that sometimes corrupts CompactFlash cards inserted into a card reader.
- Fixed issue that caused recorded video to be lost when answering an incoming call on some phones.
- Fixed issue that could result in unexpected battery drain while the phone screen is off.
- Fixed additional security issues with kernel mode drivers, remote procedure calls, the Microsoft Graphics Component, Internet Explorer 11, Microsoft Edge, Windows Shell, Windows Journal, Virtual Secure Mode, Schannel, and Jscript.
How to download and install the May 2016 security updates
All updates are made available on Windows Update for download. Depending on how the update service is configured on a Windows machine, updates may be downloaded and installed automatically, or manually.
It is suggested to research updates before they are installed to make sure they are needed and don't cause issues.
Updates are also available on Microsoft's Download Center website. The company announced this month however that it made the decision to limit direct update downloads.
Security updates are also made available as a monthly ISO image that users and administrators can download from Microsoft's website.
Additional resources
- Microsoft Security Bulletin Summary for May 2016
- List of software updates for Microsoft products
- List of security advisories of 2016
- Our in-depth update guide for Windows
- Windows 10 Update History





















Quoting an extract of the TOS,
“If you choose to get important software updates for your PC, the Windows Malicious Software Removal Tool (MSRC) may be included with these updates.”
I haven’t chosen anything pertinent to “important software updates” yet the MSRC is always included in Windows Updates unless I install its updated version before. Perhaps is the MSRC included because I had installed it first of all. If I remember correctly the MSRC is not a native Windows component, but I may be mistaking. Anyway, Windows Update could install its update without performing a scan, moreover because if it detects the updated MSRC already installed it will not use it to scan malware.
Thanks for this complete resume, Andrew.
….maybe a dumb question– but what exactly does “Windows Update” scan for during the long pre-scan of a PC ?
Does it ONLY look at primary Windows/Microsoft components… or anything it wants to look at on a given PC ?
Is the scan data encrypted when sent to Microsoft servers ?
Is Windows Update any kind of significant privacy risk to personal data on my PC ?
In short, yes and no, depending on your view of privacy.
Update Services Privacy Statement
Last updated March, 2012
Microsoft is committed to protecting your privacy. This privacy statement explains the data collection and use practices of the Windows Update and Microsoft Update services (the “Update Services”). This statement does not apply to other online or offline Microsoft sites, products, or services.
What this feature does
Update Services for Windows include Windows Update and Microsoft Update:
Windows Update is a service that provides you with software updates for Windows software and other supporting software such as drivers and firmware supplied by device manufacturers.
Microsoft Update is a service that offers you new software from Microsoft and provides you with software updates for Windows software, as well as other Microsoft software such as Microsoft Office.
In versions of Windows prior to Windows 8, Update Services might periodically show you detailed notifications about new Microsoft software and specific updates that you can install manually. Some updates available through the Update Services can only be obtained by users that have validated they are running genuine Microsoft software. Genuine Microsoft software validation is covered by a separate privacy statement that you can read online here.
Information collected, processed, or transmitted
The Update Services collect information from your computer that allows us to operate and improve the services, such as:
The Microsoft software and other supporting software (e.g., drivers and firmware supplied by device manufacturers) installed on your computer for which the Update Services have updates available. This helps us determine which updates are appropriate for you.
Your Windows Update and/or Microsoft Update configuration settings such as whether you want updates automatically downloaded or installed.
The successes, failures, and errors you experience when accessing and using the Update Services.
Plug and Play ID numbers of hardware devices – a code assigned by the device manufacturer that identifies the device (e.g., a particular type of keyboard).
Globally Unique Identifier (GUID) – a randomly generated number that does not contain any personal information. GUIDs are used to identify individual machines without identifying the user.
BIOS name, revision number, vendor, and revision date – information about the set of essential software routines that test your hardware, start the operating system on your computer, and transfer data among hardware devices connected to your computer.
Manufacturer, Model, Platform Role, and SKU Number—information about the PC used to enable diagnostic investigations into driver installations.
You can use these Update Services by going to Windows Update in Control Panel and checking for updates or changing your settings to allow Windows to automatically install updates as they become available (recommended). Within the Windows Update feature you can choose whether to opt in to Microsoft Update.
If you choose to get important software updates for your PC, the Windows Malicious Software Removal Tool (MSRC) may be included with these updates. MSRT checks computers for infections by specific, prevalent malicious software (“Malwareâ€) and helps remove any infections found. If the software runs, it will remove the Malware listed here. During a Malware check, a report will be sent to Microsoft with specific information about Malware detected, errors, and other information about your computer. For more information, read the Windows Malicious Software Removal Tool privacy statement here.
Use of information
The data sent to Microsoft is used to operate and maintain the Update Services. It is also used to generate aggregate statistics that help us analyze trends and improve our products and services, including the Update Services.
To generate aggregate statistics, the Update Services use the GUID collected by the Update Services to track and record the number of individual computers that use the Update Services and whether the download and installation of specific updates succeeds or fails. The Update Services record the GUID of the computer that attempted the download and installation, the ID of the item that was requested, whether updates were available, and standard computer information.
The MSRT information described above is used to help improve our anti-malware and other security products and services. No information in the MSRT reports will be used to identify or contact you.
Required Updates
If you turn on the Update Services, in order for them to properly function some software components on your system that make up or are directly related to the Update Services will need to be updated from time to time. These updates must be performed before the service can check for, download, or install other updates. These required updates fix errors, provide ongoing improvements, and maintain compatibility with the Microsoft servers that support the service. If the Update Services are turned off, you will not receive these updates.
Cookies/Tokens
A token is similar to a cookie. It stores information in a small file that is placed on your hard disk by the Update Services server, and is used when your computer connects to the Update Services server to maintain a valid connection. It is stored on your computer only, not on the server. This cookie/token contains information (such as last scan time) in order to find the most recently available updates. It contains information to manage what content should be downloaded to your computer, when that should happen, as well as a GUID to identify your computer to the server.
Information contained in the contents of the cookie/token is encrypted by the server (with the exception of the cookie/token expiration time). This cookie/token is not a browser cookie so it cannot be controlled with your browser settings. The cookie/token cannot be removed; however, if you do not use the Update Services, the cookie/token will not be used.
About surveys
Occasionally you might be invited to participate in a survey about the way you use the Windows Update or Microsoft Update Services. Each survey includes a privacy statement that details the way Microsoft will use the information submitted with that survey.
Choice and control
Update Services are turned on if you choose one of the following settings: (a) install updates automatically; (b) download updates but let me choose whether to install them; or (c) check for updates but let me choose whether to download and install them. The Windows Update service is turned on and set to “Install updates automatically” when you choose the express settings during Windows setup.
If you turn on the Update Services, regardless of which setting you have chosen, required updates to some components of the service will be downloaded and installed automatically without further notice to you. If you would prefer not to receive required updates, turn off the Update Services.
You can also choose whether to check for or automatically install Important and Recommended updates for your computer or Important updates only. Optional updates are never installed automatically. To change your Update Services settings after Windows setup:
If you’re using Windows 8:
Swipe in from the right edge of the screen, and then tap Search. If you’re using a mouse, point to the lower-right corner of the screen, then click Search.
Enter Windows Update in the search box, tap or click Settings, and then click Install optional updates.
Click Change settings. To turn off the Update Services (including required updates), select Never check for updates.
If you’re using Windows Vista or Windows 7:
Click the Start button, click All Programs, and then click Windows Update.
Click Change settings. To turn off the Update Services (including required updates), select Never check for updates.
If you’re using Windows XP:
Click the Start button and select Control Panel, then select Automatic Updates.
To turn off the Update Services (including required updates), select Turn off Automatic Updates.
If you have chosen to check for and install important updates, and recieve MSRT as part of these updates for your computer, you may disable the software’s reporting functionality by following the instructions found here
http://update.microsoft.com/windowsupdate/v6/vistaprivacy.aspx?ln=en-us
Not at all a dumb question since I’ve been asking myself the exact same thing :)
No answer at this time. I have no idea if the scan resumes to updates pertinence or if the company grabs the opportunity to make a search on the deep life of the user’s device(s). What I can say is that I always try to remember to install separately the updated ‘Malicious Software Removal Tool’, first because when it is installed by Windows Update it performs a fast scan but still lengthy in time, secondly because having this ‘Malicious Software Removal Tool’ scan the computer may bring that extra layer of information about the user’s installed applications… this is hypothetical, I frankly don’t know and, between paranoia/conspiracy and credulity objectivity is a tough aim.
@Tom Hawack: Manually install the update KB3153199 and then tell me how it went.
@Giova, I did and it resolved the delay problem, at least it seems so since after installing KB3153199 WinUpdate scan took less than 3 minutes.
I’ve posted this good news here but having added a link to AskWoody’s article my post is awaiting moderation …
Thanks!
Thanks again Martin, four this mount Microsoft update news.
I have a question for you this mount.
This mount particular i noticed a much longer system research time for updates
for main windows 7 pro o.s. and office 10. About three times as long in fact.
Martin did you noticed the same or did you hear – or read any whispering s about
prolonged system update research?
Apparently, the long update scan is a bug that affects only Win7 machines. This patch https://support.microsoft.com/en-us/kb/3153199 resolves the issue apparently. Make sure you download it manually from Microsoft though.
via http://www.infoworld.com/article/3069693/microsoft-windows/windows-7-update-scans-taking-forever-kb-3153199-may-solve-the-problem.html
It’s a known Windows Update problem.
Following Woody’s advice at http://www.askwoody.com/2016/win7-windows-update-once-again-taking-forever/ I’ve manually downloaded/installed KB3153199 and WinUpdate scan delay fell to less than 3 minutes, performing as such what KB3145739 (April 2015) had seem to magically allow last month but no longer with this 05-2015 WinUpdate…
Windows Update has become a capharnaüm (not sure the word is valid in English, call it a “mess” then).
I only read that some users are experiencing this but did not experience it myself.
Thanks for letting me know!
Hopefully next mount the Windows necessary update research will go again as swift like it use to be!
Many people got this update. Is it recommended to install this update?
KB3153731 – May 2016 DST update for Azerbaijan, Chile, Haiti, and Morocco in Windows.
Or this update disappears/vanish after some days?
Same as Paranam Kid. Microsoft’s comment on this update mentions that it is only required for computers located in a GMT-3 list of countries (forgot which ones besides Morocco…).
From Windows Update’s GUI itself there is a link for more information concerning every update. Otherwise Web searching for KB3153731 will provide extensive information.
I did not install KB3153731 because those time zones are not relevant for me. I actually do not install any updates that are irrelevant to me the way KB3153731 is. I DO install all security updates.
Tom H: Leave it a few days and try again late at night or very early in the morning. In all fairness, I think their servers get hit pretty hard at update time. I find this often helps.
Yet we see people doing Win 10 updates on the same day and getting them quickly and easily.
Hi Owl, thanks for the idea/recommendation. I did think about this possibility, MS servers climbing to saturation because of the tremendous hits at the time of updates, but then I put it on the account of my imagination considering the company’s strength, I mean in terms of servers as well. Now that you say so this could explain why last April I suddenly noticed the Win Update scan of my computer fall under 3 minutes, considering this was done a few days after Patch Tuesday… I hope it turns out to be the reason because as I said I just won’t (or will I nevertheless?) wait hours for a scan with a cpu at 55% …. :) Thanks.
The best security for windows right now is to BLOCK the entire of Microsoft. All it’s Networks, All it’s CIDR that way you don’t get a GREEDY FASCIST INTENDED un-bootable box. Make sure that you NEVER GET A PACKET FROM THEM EVER AGAIN. If your box is getting a packet you still have crap running or HOLES. Debug it until you drop, cause that’s where windows is headed off the cliff. The best days have already been written. All of this new stuff is fascist spying tracking based ecosystems.
This advice is for those with WORKSTATIONS, Game Desktop, Production Boxes that produce TV, Videos, Sound, 3D parts etc..
Otherwise SWITCH TO LINUX.
THOSE WHO hate this CORPORATE FASCIST NEW WORLD ORDER TAKEOVER. IT IS TIME TO TAKE ACTION, YOU GOT BACK STABBED BY THE POWERS THAT BE, but the last words on the matter ain’t in YET… Make these bastards pay for their treason and insolence
heh… you’re funny :)
My May 10, 2016 Patch Tuesday updates all completed quickly and successfully. Very happy with Windows 10. I’m using a Dell XPS 8300 that was defragged using Defraggler by Piriform (freeware) before the Windows updates were loaded. Boy, this is a better defragger than the built in Windows 10 defragger. System works very fast again. Don’t let any one tell you that defragging isn’t necessary in Windows 10 ….. and that it occurs on its own….Windows 10 defrag is anemic compared to Piriform’s Defraggler.
I experienced no slow down to my operating system after May 10 updates but I am not a beta tester with Windows Insider. In general though, it is wise to clean out your tower periodically. You would be shocked how dusty it can become inside. This can cause malfunctions. Running SFC /scannow in administrative command prompt is periodically wise. Also perform DISM /online /cleanup-image /startcomponentcleanup . Let it finish! CHKDSK C: /f /r run in administrative command prompt can take six hours for a 2 TB HD but it fixes and repairs errors on your hard drive. Let it run while you are asleep. All these tasks enable Windows Update to complete more successfully and in a timely manner. Good luck to you in your endeavors and if you don’t understand how to do something GOOGLE it.
April’s Windows Updates was a nightmare, for many updates wouldn’t install and update scan took a very long time, several hours for some to even an overnight adventure for others; here I was on a 35-40 minutes’ delay. Then I managed to install manually KB3145739 after which the slow Windows Update fell to less than 3 minutes. Were both related? No idea.
Now, May 2016 and Windows 7, Updates, 5… 10… 15 minutes … still scanning. I won’t wait any longer, it could mean 5 minutes as it could mean hours. No more Windows Update until it is generally acknowledged that the Windows Update scan delay has been fixed. Not to mention the cpu climbing and fixed at height of 55%…. what, wait hours with a half-cpu power until the insane company finally finishes scanning my computer? No way. fed up.
Until this Windows Update scan delay is fixed, NO more updates. Que sera sera.. What a pain, Microsoft is drowning, crappy company, let it go to hell. Can’t bear any more, any longer.
I reinstalled 7 on my laptop a couple of weeks ago and had the same issue. After a morning of doing nothing, with CPU usage fluctuating between 30-50%, at someone’s sugestion I installed these updates:
support microsoft com/en-us/kb/3102810
support microsoft com/en-us/kb/949104
Restart, install first one, restart again, install second, another restart.. and now it found all (100+) the updates in less than 5 minutes and begin the download as soon as I clicked install (it did not stay at 0% at all). And all the subsequent updates (Office 2010, etc) were fast as well.
Yet another bad decision by micro$oft for not releasing 7 SP2.
I hear you, Tom. For me, it took 2 or 3 hours for the update scan to complete. There’s no way this is not intentional. I know in the years when WIn 7 was MS’ latest OS the scan would take 30 minutes tops. Usually less. now that I’m refusing Win 10, it always takes hours.
I work on PC’s and see alot of Win 7 machines, On a fresh rebuild of the OS, it can literally take half a day to do scan and install updates on these Win 7 PC’s. I can’t help but think that MS is attempting to make using Win 7 more unpleasant.
I’m also growing to hate this company.
@Tom Hawack: Sorry, my reply was *specifically* directed at Jeff-FL’s problem (which everyone has I guess) when doing clean installs and first scan for updates.
As for the inner workings of MS’s update mechanisms, I have no desire to waste my time with it. I have way too much goat porn to view, and so little time :)
My comment Tom Hawack May 11, 2016 at 9:28 pm # awaiting moderation … for what this time?
WP is nuts.
@Pants, the article you mention is a great information when performing a fresh rebuild of the OS but doesn’t explain,
– why Windows Update can take between 3 minutes and several hours on an installed system,
– why April 2015 Patch Tuesday took hours to scan and suddenly only minutes after manually downloading/installing KB3145739,
– why this May 2015 Patch Tuesday again took hours and then minutes after manually downloading/installing this time KB3153199,
– what relationship between a patch (KB3145739 in April, KB3153199 this May) and Windows Update’s scanning feature,
– why did KB3145739 seem to repair the scanning speed issue in April and no longer in May?
Why did we not encounter such long Windows in the past? I’ve installed Windows 7 in August 2013 and never encountered the Windows Update delays affecting the system since a few months now. Amazing.
If you or anyone has an answer I’d be most interested to know why and how this Windows Update has become a mess, by the time required to scan, to download updates as well for some users (not here), and by encountering more and more update install failures.
You think that’s bad, XP clean installs near the end of its life would take upwards of 5 hours and resources would hit like 100% CPU the whole time.
Ahhh fun times.
@Jeff-FL: I have an (as yet untested) solution for you.
I have a Win7 SP1 I use for clean installs. Doing the updates takes ages, kinda. It will take anywhere from 1 to 2 hours to actually progress to the stage where it has detected all the updates – after that, it goes at it’s normal speed (downloading, installing, reboot if required, recheck, download, install etc).
I read this recently: http://www.zdnet.com/article/sticking-with-windows-7-the-forecast-calls-for-pain/
Quote: “Download two updates before starting the installation process, KB3083710 and KB3102810, and copy them to a USB flash drive. Install Windows 7 with SP1 and leave the network cable disconnected. Install those two updates from the flash drive before connecting to the network and running Windows Update for the first time, and you can cut that horrendous delay down to a matter of a few minutes.”
So the next Win7 machine I set up for family, friends or clients, I’m going to try this. I doubt you need to do the disabled network thing – just install Win7, install those two KBs (from local copies), run updates.
@Jeff-FL, there’s good advice as how to proceed to make WinUpdate scan normally (manually downloading/installing KB3153199) available here : http://www.askwoody.com/2016/win7-windows-update-once-again-taking-forever/
It worked for me, scan took afterwards less than 3 minutes.
In my case, with Windows 7, it took 2.5 hours to download and install and the core temperatures were well over 50℃ for much of that time. There’s got to be a better way.
Just leave this NSA Client behind.
Redmond is just another factory of NSA. Period.
So, referencing the winbeta article…
“Microsoft just dropped a cumulative update for Windows 10, and it includes quality improvements and security fixes. While not widespread, since the release, though, some Windows 10 users on Reddit have complained that the update makes their computer slow. Microsoft has responded to such complaints, and a Microsoft employee has posted a workaround for the issue to the Windows 10 subreddit.”
I am really hating these subpar updates they are releasing… I feel like ever since they switched to Windows 10 / Insider program their updates are not as stable as they used to be.