Microsoft Security Bulletins For January 2015
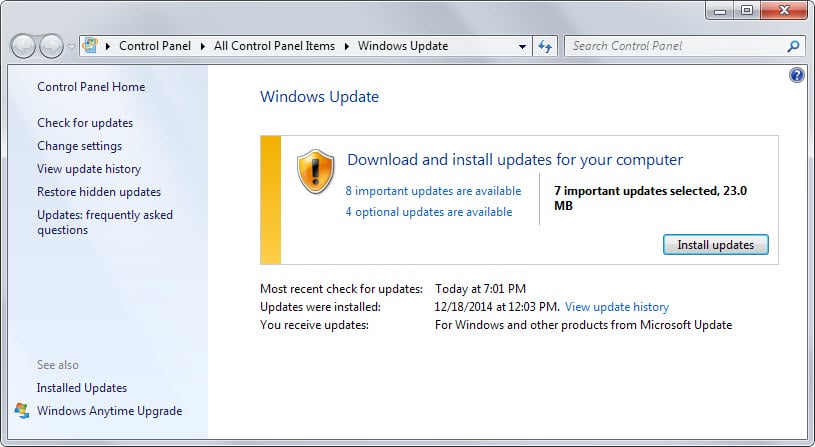
Microsoft has just released security updates for January 2015 for all supported operating systems (Windows Vista to Windows 8.1) and other company products.
The updates are already available on Windows Update and you may want to run a manual check for updates to install them right away.
Below you find information about the January 2015 security bulletins that Microsoft released. It starts with the executive summary which highlights the most important update information.
You also find listed how individual operating system editions are affected by the update, how other Microsoft products are affected, and how to install the updates.
Last but not least, all security and non-security updates are listed as well with links and additional information such as severity or impact.
Executive Summary
- Microsoft released eight security bulletin this month fixing eight unique vulnerabilities in total.
- One of the bulletins received the highest severity rating of critical, the others a rating of important.
- Vulnerabilities affect only client and server operating systems.
Operating System Distribution
All desktop operating systems but Windows RT and RT 8.1 are affected by one bulletin in a critical way.
All server operating systems are also affected by one bulletin in a critical way.
- Windows Vista: 1 critical, 3 important
- Windows 7:Â 1 critical, 4 important
- Windows 8: 1 critical, 5 important
- Windows 8.1: 1 critical, 5 important
- Windows RT: 4 important
- Windows RT 8.1:Â 4 important
- Windows Server 2003: 1 critical, 2 important
- Windows Server 2008: 1 critical, 2 important
- Windows Server 2008 R2: 1 critical, 4 important
- Windows Server 2012: 1 critical, 5 important
- Windows Server 2012 R2: 1 critical, 5 important
- Server Core installation: 1 critical, 5 important
Security Bulletins
- MS15-001 - Vulnerability in Windows Application Compatibility Cache Could Allow Elevation of Privilege (3023266) - Important - Elevation of Privilege
- MS15-002 - Vulnerability in Windows Telnet Service Could Allow Remote Code Execution (3020393) - Critical - Remote Code Execution
- MS15-003 - Vulnerability in Windows User Profile Service Could Allow Elevation of Privilege (3021674) - Important - Elevation of Privilege
- MS15-004 - Vulnerability in Windows Components Could Allow Elevation of Privilege (3025421) - Important - Elevation of Privilege
- MS15-005 - Vulnerability in Network Location Awareness Service Could Allow Security Feature Bypass (3022777) - Important - Security Feature Bypass
- MS15-006 - Vulnerability in Windows Error Reporting Could Allow Security Feature Bypass (3004365) - Important - Security Feature Bypass
- MS15-007 - Vulnerability in Network Policy Server RADIUS Implementation Could Cause Denial of Service (3014029) - Important - Denial of Service
- MS15-008 - Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (3019215) - Important - Elevation of Privileges
Other security related updates
- Security Update for Internet Explorer Flash Player for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, and Windows Server 2012 (KB3008925)
Non-security related updates
- Microsoft .NET Framework 4.5.2 for Windows 8, Windows RT, and Windows Server 2012 (KB2901982)
- Microsoft .NET Framework 4.5.2 for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB2901983)
- Microsoft .NET Framework 4.5.2 for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2934520)
- Microsoft .NET Framework 4.5.2 Language Packs for Windows 8, Windows RT, and Windows Server 2012 (KB2938103)
- Microsoft .NET Framework 4.5.2 Language Packs for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2938104)
- Windows Malicious Software Removal Tool - January 2015 (KB890830)/Windows Malicious Software Removal Tool - January 2015 (KB890830) - Internet Explorer Version
- Update for Windows 8.1 (KB2997841) - System crashes after you restart or wake up the computer in Windows 8.1 or Windows RT 8.1
- Update for Windows 8 (KB3008273) - An update to enable an automatic update from Windows 8 to Windows 8.1
- Update for Windows 7 and Windows Server 2008 R2 (KB3024777) - Install KB3024777 to fix an issue with KB3004394 on Windows 7 and Windows Server 2008 R2
How to download and install the January 2015 security updates
All security updates are made available automatically via Microsoft's Windows Update service as well as business and enterprise related update services the company operates.
Most home users should get the patches automatically though. If you have disabled automatic updates you can check for updates manually at any time using Windows Update:
- Tap on the Windows-key and type Windows Update.
- Select the result from the results.
- Click on the check for updates button to run a check.
You can install some or all of the security patches displayed to you by the program.
Other options include visiting Microsoft's Download Center to download individual patches or to download this month's security ISO image containing them all.
Additional information
- Microsoft Security Response Center blog on the 2015 Bulletin Release
- Microsoft Security Bulletin Summary for January 2015
- List of software updates for Microsoft products
- Our in-depth update guide for Windows




















It seemed this has worked for me too. I used the download to repair the installation. After the reboot KB2901983 was back as before. So I installed it again. After the reboot it did not came back this time.
My conclusion – it’s awful – flags up no less than 85 (yes eighty-five) things for the 8 bulletins actually issued today – and that’s when only patches for Windows and Windows Server have come out. I wonder how many more there would be if other products we use like Office or Visual Studio also had patches.
It seemed this has worked for me too. I used the download to repair the installation. After the reboot KB2901983 was back as before. So I installed it again. After the reboot it did not came back this time.
It seemed this has worked for me too. I used the download to repair the installation. After the reboot KB2901983 was back as before. So I installed it again. After the reboot it did not came back this time.
I thought I would give myBulletins a try – just to see how helpful it really is.
My conclusion – it’s awful – flags up no less than 85 (yes eighty-five) things for the 8 bulletins actually issued today – and that’s when only patches for Windows and Windows Server have come out. I wonder how many more there would be if other products we use like Office or Visual Studio also had patches.
I can see what I need to know a whole lot quicker with the security bulletin summary.
I just had a notification of 3 Windows updates on my Windows 7 64bit OS. One of them included KB2901983, marked as important, but not checked. I checked it and started the install along with the other 2 updates. It hesitated for quite a while on KB2901983 and I just walked away for maybe 20 minutes. When I got back, it said all 3 updates were successfully installed. After the required reboot, I am up and running with no obvious issues.
I had the same problem with KB2901983 not installing in Windows Updates.
I downloaded this: “Microsoft .NET Framework 4.5.2 (Offline Installer) for Windows Vista SP2, Windows 7 SP1, Windows 8, Windows 8.1, Windows Server 2008 SP2, Windows Server 2008 R2 SP1, Windows Server 2012 and Windows Server 2012 R2” from here: http://www.microsoft.com/en-us/download/confirmation.aspx?id=42642 and all my problems went away. The KB2901983 no longer appears in Windows Update.
Thank you for sharing this solution Wayne.
It seemed this has worked for me too. I used the download to repair the installation. After the reboot KB2901983 was back as before. So I installed it again. After the reboot it did not came back this time.
Also I now got the windows stating updates were succeeded a you normally get. So it looks your solution worked.
Thank you!
Hello.
I have the same problem with KB2901983 as Kinmokuchi on a Windows 7 Professional 64-bit with 16GB RAM.
The update installes and after rebooting, it asks again for the same update to be installed.
So the update keeps coming back.
KB2901983 won’t install on my Windows 7 home basic service pack 1 , 8 GB RAM , Pentium P6100 (2 ghz) ,Sony vaio PC
Tried again and again but it takes a lot of time (about half hour) and then fails , it is a recommended update , is it necessary , what can I do to successfully install it?
Please advice , Thanks in Advance :)
********************************************************************
Title: Microsoft Security Bulletin Releases
Issued: January 13, 2015
********************************************************************
Summary
=======
The following bulletins have undergone a major revision increment.
* MS14-080 – Critical
Bulletin Information:
=====================
MS14-080 – Critical
– Title: Cumulative Security Update for Internet Explorer
– https://technet.microsoft.com/library/security/ms14-080
– Reason for Revision: V2.0 (January 13, 2015): To address issues
with Security Update 3008923, Microsoft re-released MS14-080 to
comprehensively address CVE-2014-6363. In addition to installing
update 3008923, customers running Internet Explorer 10 on Windows 8,
Windows Server 2012, or Window RT should also install update
3029449, which has been added with this rerelease. Customers who
have already successfully installed the 3008923 update, which has
not changed since its original release, do not need to reinstall
it. See Microsoft Knowledge Base Article 3008923 for more
information.
Martine,
On my Windows 7 64bit sp1 the Microsoft .NET Framework 4.5.2 is not-selected. Seems so too on your PC as well (only 7 important updates selected).
Okay got word back from Microsoft. The update will be checked in the near future.
“This is an expected behavior with large update releases. Once the rollout is complete, all users will see the box checked.†–a Microsoft spokesperson
“This is an expected behavior with large update releases. Once the rollout is complete, all users will see the box checked.â€
Exactly 2 weeks after Jan 2015’s Patch Tuesday, KB2901983 (Microsoft .NET Framework 4.5.2, 52.4 MB) is still left unchecked at my Windows Update.
At the left pane, KB2901983 is categorized as “Important”, but in the detailed right pane, it states: “Update type: Recommended”. Meanwhile, Microsoft’s KB2901983 page states: “The .NET Framework 4.5.2 product is offered as a recommended update.”
So what does it mean when an update is Important-Recommended-Unchecked all at the same time ? To bypass or to install ?
You are right, it is not installed by default.
The following seems a bit ambiguous, but I think it’s saying that 4.5.2 supersedes everything after 3.5. If that’s the case, it’s a pretty good way to simplify things:
This version of the .NET Framework runs side-by-side with the .NET Framework 3.5 SP1 and earlier versions, but performs an in-place update for the .NET Framework 4, .NET Framework 4.5 and .NET Framework 4.5.1.
First time I can recall an “important” update not preselected. Why did it not go under Optional updates?
Waiting for a statement from Microsoft, will let you know should they answer.
Maybe telnet is an issue for ATMs and other stuff still using XP embeds, otherwise no clue how many OS could need it. Thank you for reporting on Patch Tuesday this month; I now cringe and prepare to install what ones I’ll get since I see no problems yet reported here (unlike last month).
Notice that the:
“MS15-002 – Vulnerability in Windows Telnet Service Could Allow Remote Code Execution (3020393)”
is only available IF you have “telnet” installed. According to MS:
“Telnet is not installed by default on Windows Vista and later operating systems.”
in my line of work which involves quite a lot of telnet related work, none.
Where Telnet is needed I hardly see ever the MS telnet server beeing used. Mostly it is a 3rd part Telnet service.
The MS telnet is only used for brief test cases.
I think out of 100 telnet customers only 1 really uses the MS telnet.
Interesting, wonder how many systems are affected by the vulnerability.
Only those which have telnet installed. So, not so many if MS stopped installing it by default starting with Vista.
I just mentioned this in case people start to wonder why their windows update doesn’t have the 3020393 offered. I noticed that I wasn’t offered this and read this info from the KB article.
Pete, I was wondering about the number of systems that have Telnet enabled. It cannot really be that many, can it?
I agree that it can be puzzling if you don’t get an update even though it is listed as available for your operating system. Thanks again.
Martin, Like every mouth I am thanking you for this mouth work you did on this monthly patch Tuesday article.
But from this mouth on I am going to give you a even more hardly meant thank for your trouble, this because
I read earlier this mount in one of your articles that Microsoft is not releasing any advanced security notifications,
anymore before patches are made available, on Patch Tuesday.
These monthly security reviews complete with links are a great service, Martin.
I like to examine the details of each new update before installing on my systems.
Microsoft made my job harder than it should be unfortunately with all the changes that it introduced.
Trying my best, glad that you find it useful.