Microsoft Security Bulletins For April 2014 overview

Welcome to this month's Security Bulletins summary. The guide provides you with all information about this month's security updates for client and server Windows operating systems.
This month is special for two reasons. It is the last patch day for Windows XP, which Microsoft will stop supporting with public updates after today.
Microsoft makes available a feature update for Windows 8.1 which improves the operating system's mouse and keyboard usability. We have covered it before, check it out if you are interested in this one.
A total of four bulletins are released this month. Two have received the highest vulnerability rating of critical, while the other two a rating of important, the second highest rating.
Software affected by the updates include Microsoft Windows, Internet Explorer and Microsoft Office.
You find a summary of all important information about the security bulletins released by Microsoft this week.
Executive Summary
- Four bulletins are released by Microsoft this month that address 11 vulnerabilities across all products.
- The products affected by these vulnerabilities are Microsoft Windows, Internet Explorer and Microsoft Office.
- Two bulletins are rated critical, the other two important.
- Top deployment priority are the two critical bulletins MS14-017 and MS14-018.
Video Summary
Operating System Distribution
All client-based Windows operating systems share the same bulletin vulnerability distribution. Each system is affected by one critical and one important bulletin.
Considering that this is the last public patch day for Windows XP, we will remove the operating system from next month on.
The server-based Windows systems share the same vulnerability profile as well. Each system is affected by one important and one moderate bulletin.
- Windows XP:Â 1 critical, 1 important
- Windows Vista: 1 critical, 1 important
- Windows 7:Â Â 1 critical, 1 important
- Windows 8:Â 1 critical, 1 important
- Windows 8.1: 1 critical, 1 important
- Windows RT: 1 critical, 1 important
- Windows RT 8.1:Â 1 critical, 1 important
- Windows Server 2003: 1 important, 1 moderate
- Windows Server 2008: 1 important, 1 moderate
- Windows Server 2008 R2: 1 important, 1 moderate
- Windows Server 2012: 1 important, 1 moderate
- Windows Server 2012 R2: 1 important, 1 moderate
Other Microsoft Product Distribution
Two bulletins affect Microsoft Office software. Most products, with the exception of Office 2003 and Office 2007, are affected by one critical bulletin. The two mentioned programs are affected by one important bulletin in addition.
- Microsoft Office 2003: 1 critical, 1 important
- Microsoft Office 2007: 1 critical, 1 important
- Microsoft Office 2010: 1 critical
- Microsoft Office 2013: 1 critical
- Microsoft Office for Mac: 1 critical
- Other Office software: 1 critical
- Microsoft SharePoint Server 2010: 1 critical
- Microsoft SharePoint Server 2013: 1 critical
- Microsoft Office Web Apps 2010: 1 critical
- Microsoft Office Web Apps 2013: 1 critical
Deployment Guide
Microsoft releases a deployment priority each month to act as a guide for system and network administrators. The suggestion uses information such as a bulletins severity, exploits that already target it, and product to determine the bulletins that should be deployed with priority.
- Tier 1 updates: Ms14-017 Word Critical and MS14-018 Internet Explorer Critical.
- Tier 2 updates: MS14-020 Publisher Important.
- Tier 3 updates: Ms14-019 File Handling Important.
Security Bulletins
- MS14-017 - Vulnerabilities in Microsoft Word and Office Web Apps Could Allow Remote Code Execution (2949660) -Â Critical - Remote Code Execution
- MS14-018 - Cumulative Security Update for Internet Explorer (2950467) -Â Critical - Remote Code Execution
- MS14-019 - Vulnerability in Windows File Handling Component Could Allow Remote Code Execution (2922229) - Important - Remote Code Execution
- MS14-020 - Vulnerability in Microsoft Publisher Could Allow Remote Code Execution (2950145) - Important - Remote Code Execution
Non-security related updates
- Update for Windows 7 and Windows Server 2008 R2 (KB2800095)
- Update for Windows 7 and Windows Server 2008 R2 (KB2908783)
- Update Rollup for Microsoft Windows MultiPoint Server 2011 (KB2927581)
- Rules Update for RRAS Best Practice Analyzer for Windows Server 2012 R2 (KB2928193)
- Update for Windows 7 and Windows Server 2008 R2 (KB2928562)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2933809)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2933810)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2933811)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2934016)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2936897)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2939087)
- Dynamic Update for Windows 8.1 and Windows Server 2012 R2 (KB2953600)
- Windows Malicious Software Removal Tool - April 2014 (KB890830)/Windows Malicious Software Removal Tool - April 2014 (KB890830) - Internet Explorer Version
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2890139)
- Update for Windows 8.1 and Windows RT 8.1 (KB2895219)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2895233)
- Update for Windows 8.1 (KB2895586)
- Update for Windows 8.1 (KB2895592)
- Update for Windows 8.1 (KB2895614)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2897942)
- Update for Windows RT 8.1 (KB2903601)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2913253)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2928678)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2930294)
- Dynamic Update for Windows 8 and Windows Server 2012 (KB2939103)
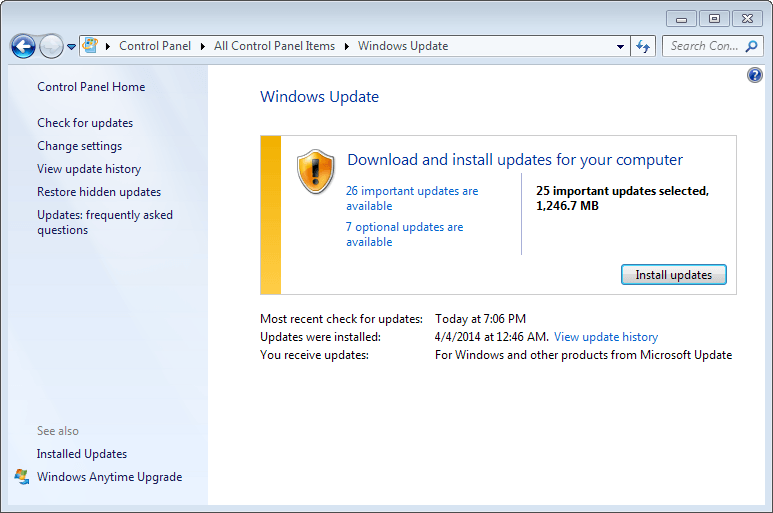
How to download and install the April 2014 security updates
The updates are as usual available via Windows Update. This is usually the way they are deployed on most home systems as Windows Update is configured to automatically download and install security updates.
The updates are available already. You may want to check for updates manually as it may take a while before Windows checks for updates again.
To do so, press the Windows-key and enter "windows updates" and select that option to run a manual update check.
You can download all updates from Microsoft's Download Center as well. The company will release a security ISO containing this month's patches as well which you can download. It takes some time before it gets released though.
If you need more information, check out our Windows Update guide which covers everything there is to know about updating Windows.
Additional information
- Microsoft Security Response Center blog on the 2014 Bulletin Release
- Microsoft Security Bulletin Summary for April 2014
- List of software updates for Microsoft products 2014




















KB2936068-MS14-018 update, after it is installed, will not let Avast! Free and Malwarebytes Anti-Malware Premium load. Even a reinstall of Avast! Free cannot be completed. I had to use a saved Restore Image to get these programs working again.
(W7 pro 32bit, IE11)
Since no later than 2014-02-19, MSE Prerelease has been available at 4.5 and as of 2014-04-09 is at
Antimalware Client Version: 4.5.216.0
Engine Version: 1.1.10401.0
Antivirus definition: 1.169.2154.0
Antispyware definition: 1.169.2154.0
Network Inspection System Engine Version: 2.1.10302.0
Network Inspection System Definition Version: 110.31.0.0
FYI Brian Krebs has a complete Patch Tuesday update, which not only includes Windows but Adobe products like Flash and AIR. I feel Adobe patches often are at least as important as Microsoft.
http://krebsonsecurity.com/2014/04/adobe-microsoft-push-critical-fixes/
As always, thank you very much for your article about Microsoft updates :)
There has been an update to Microsoft Security Essentials (v 4.5). While it’s allright for Windows Vista and newer, XP users may prefer to avoid it and keep version 4.4… ;)
This is a How To…. Disable the Security Essentials End-of-Life Warning on Windows XP
use this link and follow the instructions…
http://superuser.com/questions/738131/disable-the-security-essentials-end-of-life-warning-on-windows-xp
Tested on a VM and works fine
Also…
Funny enough, Microsoft pushes the new SE-version (4.5.216, with nagging screen) through automatic updates, but still has the previous version (4.4.304) available for manual download. I would not be surprised if they’ve pushed the 4.5-version only to XP-users.
Anyway, the solution is:
Manually download Security Essentials here. Keep it for later use.
Go to your configuration screen.
Select ‘software’ and uninstall Security Essentials.
Select ‘Automatic updates’ and opt for the second possibility (download and ask to install).
Install your downloaded version of Security Essentials.
The first time Windows Update asks you to update SE, you say no and click that you do not want to be bothered again about this update.
Also… mse 4.4.304 is available here…
http://www.filehippo.com/download_security_essentials_xp/51102
Um, why I only see the security-related updates, but nothing about the Update 1? Won’t UPD1 come through Windows Update normally? I thought this was the plan…