Microsoft Security Bulletins For February 2014 overview
Yes, it is this time of the months again. Microsoft has just released this month's security bulletins for its Windows and Office products.
The company has released a total of seven bulletins targeting different client and server versions of Microsoft Windows, Internet Explorer, Microsoft Security Software, and the Microsoft .Net Framework.
Four bulletins have received the highest severity rating of critical, while the other three one of important, the second highest rating.
This means that at least one product is affected by the severity rating, while others may have received the same rating, a lower rating, or may not be affected at all.
The information that you find below provides you with all the information you need to deploy those patches on your system. They help you understand what each bulletin addresses, how it is deployed, and provide you with links to Microsoft pages for additional information.
Video Summary
Operating System Distribution
Six of the seven bulletins address vulnerabilities in Microsoft Windows client or server software. Least affected on the client side are Windows XP and Windows Vista, followed by Windows 7 and then Windows 8, 8.1, RT and RT 8.1 which are all affected by the most vulnerabilities.
The situation is similar on the server side. Server 2003 and 2008 are the least affected products, followed by Server 2008 R2 which is affected by one additional bulletin, and then Server 2012 and Server 2012 R2 which are affected by one additional bulletin.
- Windows XP:Â 2 critical, 2 important
- Windows Vista: 2 critical, 2 important
- Windows 7:Â Â 3 critical, 2 important
- Windows 8:Â 3 critical, 3 important
- Windows 8.1: 3 critical, 3 important
- Windows RT: 3 critical, 3 important
- Windows RT 8.1:Â 3 critical, 3 important
- Windows Server 2003: 2 important, 1 moderate, 1 low
- Windows Server 2008: 2 important, 1 moderate, 1 low
- Windows Server 2008 R2: 1 critical, 2 important, 1 moderate, 1 low
- Windows Server 2012: 1 critical, 3 important, 1 moderate, 1 low
- Windows Server 2012 R2: 1 critical, 3 important, 1 moderate, 1 low
Office Distribution
There have been no bulletins this month that address security issues in Microsoft Office products.
- Microsoft Office 2003
- Microsoft Office 2007
- Microsoft Office 2010
- Microsoft Office 2013
- Microsoft SharePoint Server 2010
- Microsoft SharePoint Server 2013
- Microsoft Office Web Apps 2010
- Microsoft Office Web Apps 2013
Microsoft Security Software
- Microsoft Forefront Protection 2010 for Exchange Server: 1 critical
Deployment Guide
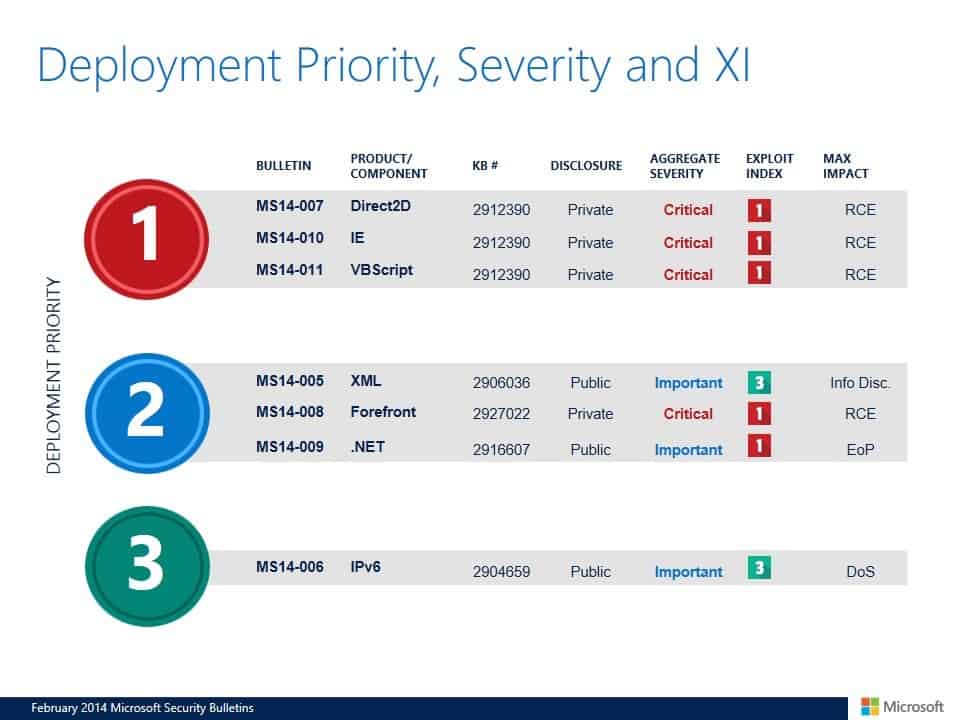
Microsoft suggests the following deployment priority for this month's bulletins.
- Tier 1 updates: MS14-007 Direct2D, Ms14-010 Internet Explorer, MS14-011 VBScript
- Tier 2 updates: MS14-005 XML, MS14-008 Forefront, MS14-009 .NET
- Tier 3 updates: MS14-006 IPv6
Security Bulletins
- Â MS14-010 Cumulative Security Update for Internet Explorer (2909921) - Critical - Remote Code Execution
- MS14-011 Vulnerability in VBScript Scripting Engine Could Allow Remote Code Execution (2928390) - Critical - Remote Code Execution
- MS14-007 Vulnerability in Direct2D Could Allow Remote Code Execution (2912390) - Critical - Remote Code Execution
- MS14-008 Vulnerability in Microsoft Forefront Protection for Exchange Could Allow Remote Code - Critical - Remote Code Execution Execution (2927022)
- MS14-009 Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (2916607) - Important - Elevation of Privilege
- MS14-005 Vulnerability in Microsoft XML Core Services Could Allow Information Disclosure (2916036) - Important - Information Disclosure
- MS14-006 Vulnerability in IPv6 Could Allow Denial of Service (2904659) - Important - Denial of Service
Other security-related contents
- Security Update for Internet Explorer Flash Player for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, and Windows Server 2012 (KB2929825)
- Security Advisory 2862973 has been revised - Update for Deprecation of MD5 Hashing Algorithm for Microsoft Root Certificate Program
Non-security related updates
- Update for Windows 7 and Windows Server 2008 R2 (KB2830477) - Update for RemoteApp and Desktop Connections feature is available for Windows
- Update for Windows 8.1, Windows Server 2012 R2, Windows 8, Windows Server 2012, Windows 7, and Windows Server 2008 R2 (KB2843630) - Update helps unmanaged Office 2010 users to work with Microsoft RMS in Windows
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2908816) - Update for the CopyFile() function in nonbuffered scenarios in an SMB environment in Windows RT 8.1, Windows 8.1 and Windows Server 2012 R2
- Update for Windows 7 and Windows Server 2008 R2 (KB2913751) - Smart card redirection in remote sessions fails in a Windows 7 SP1-based RDP 8.1 client
- Update for Windows RT 8.1 (KB2913760) - Drivers and firmware cannot be updated on Windows 8.1-based devices
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2917929) - Compatibility update is available for Windows RT 8.1, Windows 8.1 and Windows Server 2012 R2: February 2014
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2917931) - Compatibility update is available for Windows RT 8.1, Windows 8.1 and Windows Server 2012 R2: February 2014
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2917932) - Compatibility update for the web, store, and media upgrade experience is available for Windows 8.1 and Windows Server 2012 R2: February 2014
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2919393) - Windows RT, Windows 8, and Windows Server 2012 update rollup: February 2014
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2919394) - Windows RT 8.1, Windows 8.1, and Windows Server 2012 R2 update rollup: February 2014
- Update for Windows 7 and Windows Server 2008 R2 (KB2919469) - Canada country code is incorrect in Windows 7 SP1 or Windows Server 2008 R2 SP1
- Update for Windows 8.1 (KB2919907) - GUI elements freeze after disconnecting the Bluetooth adapter in Windows 8.1
- Update for Windows 8.1 and Windows RT 8.1 (KB2922474) -Unexpected DPI appears when a Windows 8.1-based device that has iSCT enabled resumes from sleep
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2923300)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2923528)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2923768)
- Windows Malicious Software Removal Tool - February 2014 (KB890830)/Windows Malicious Software Removal Tool - February 2014 (KB890830) - Internet Explorer Version
- Update for the Microsoft .NET Framework 4 on Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2836939)
- Update for the Microsoft .NET Framework 3.5 SP1 on Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2836940)
- Update for the Microsoft .NET Framework 2.0 SP2 on Windows Server 2003 and Windows XP (KB2836941)
- Update for the Microsoft .NET Framework 3.5.1 on Windows 7 and Windows Server 2008 R2 (KB2836942)
- Update for the Microsoft .NET Framework 3.5.1 on Windows 7 and Windows Server 2008 R2 (KB2836943)
- Update for the Microsoft .NET Framework 2.0 SP2 on Windows Server 2008 (KB2836945)
- Update for the Microsoft .NET Framework 3.5 on Windows 8 and Windows Server 2012 (KB2836946)
- Update for the Microsoft .NET Framework 3.5 on Windows 8 and Windows Server 2012 (KB2836947) - Windows RT, Windows 8, and Windows Server 2012 update rollup: January 2014
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2911101) - Windows RT 8.1, Windows 8.1, and Windows Server 2012 R2 update rollup: January 2014
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2911106) - Windows RT 8.1, Windows 8.1, and Windows Server 2012 R2 update rollup: January 2014
- Update for Windows Server 2012 R2 (KB2904440) - A servicing stack update is available for Windows RT 8.1, Windows 8.1, and Windows Server 2012 R2
How to download and install the February 2014 security updates
All security updates are provided via Microsoft's Windows Update service. If the automatic update feature is enabled, updates are distributed automatically to PCs.
You can speed up the discovery of updates though by opening Windows Updates on your system to run a manual check for updates.
If you have blocked automatic updates for more control over the updating process, you may download updates from Microsoft's Download Center website instead were all are made available as well. There you will also find the monthly security ISO image that Microsoft creates, containing all security patches released for that month.
Downloading updates manually makes sense in certain situations. If you need to deploy updates to several local PCs, you will save bandwidth doing so as you only need to download the updates once to deploy them on all PCs.
You can also use third-party software that downloads all Windows patches to your system.
Additional information
- Microsoft Security Response Center blog on the 2014 Bulletin Release
- Microsoft Security Bulletin Summary for February 2014
- List of software updates for Microsoft products 2014





















It took me a while to find the URL of the page with “the monthly security ISO image that Microsoft creates”, so here it is:
Title is: Security updates on ISO-9660 DVD5 image files…
URL: http://support.microsoft.com/kb/913086
Anyone realized the @Skydrive (soon to be @OneDrive) icon is back in the taskbar/ notification area of @Windows 8.1? Not sure about other systems/ versions of Windows.
I followed your link to Microsoft’s Download Center (towards the end of your article), and then clicked on the Microsoft Update box in the upper left of that page. And started to laugh. Firefox popped an alert that says, “www.update.microsoft.com uses an invalid security certificate”.
As always, thank you very much Martin for your article on the Microsoft monthly updates :)
It appears that a few non-security related updates for Office 2010 were released by the end of January. They can be found in the MS Download Center.
Yes there was 7 updates for Office 2010 on Win 7 – 8.1. The one note update screwed up all the printer functions (HP) was a pain to reload them all. Lost most of the printer Programs in Win XP, give up on a sony Vaio office 03 on it after reloading the HP progams for the printers as it could not find them or would only half load
I use the WSUS Offline Update
from http://download.wsusoffline.net/
Thanks Martin, For guiding me threw main 21 Microsoft 7 pro system updates from this mouth!
30 security bugs. None has been found by Microsoft’s security team, all by outsiders.
24 security bugs in IE copied over and over from the 13 years old IE6 up to Windows 8.1’s IE11.