Microsoft Security Bulletins For December 2013 overview
The last Microsoft patch day of 2013 is here and Microsoft has just pushed the new updates to Windows Update. If you check for new updates right now, your installation of Windows should pick them up and install them if automatic updates are configured.
Microsoft has released a total of 11 security bulletins this month, that patch a total of 24 different vulnerabilities.
Five of the bulletins have received the highest severity rating of critical, while the remaining six an important rating.
The information below provide you with all the details that you need to understand, download, and deploy the bulletins to protect affected systems and software.
In particular, you will receive information about the operating system, Office and server distribution of bulletins, a suggested deployment guide, links to each bulletin and non-security updates for additional information, as well as information on how to download and install those updates.
Operating System Distribution
The least affected client operating system are Windows 8, Windows 8.1 and Windows 7 this time with three critical and 1 important bulletin.
Windows XP is affected by three critical and two important bulletins, and Vista by four critical bulletins and one important one.
On the server side, Windows Server 2008 R2 and Windows Server 2012 are the least affected with two critical and two important bulletins each.
Windows Server 2003 is affected by two critical and three important bulletins, and Windows Server 2008 by three critical and two important bulletins.
- Windows XP: 3 critical, 2 important
- Windows Vista: 4 critical, 1 important
- Windows 7:Â 3 critical, 1 important
- Windows 8:Â 3 critical, 1 important
- Windows 8.1: 3 critical, 1 important
- Windows RT: 3 critical, 1 important
- Windows RT 8.1: 3 critical, 1 important
- Windows Server 2003: 2 critical, 3 important
- Windows Server 2008: 3 critical, 2 important
- Windows Server 2008 R2: 2 critical, 2 important
- Windows Server 2012: 2 critical, 2 important
Office Distribution
A total of three bulletins address vulnerabilities in Microsoft Office software. This time, Microsoft Office 2013 is the least affected with one bulletin that has been rated important. Then there is Office 2003 with one critical bulletin, and Office 2007 and Office 2010 which are both affected by vulnerabilities in two bulletins rated as critical and important.
- Microsoft Office 2003: 1 critical
- Microsoft Office 2007: 1 critical, 1 important
- Microsoft Office 2010: 1 critical, 1 important
- Microsoft Office 2013: 1 important
Microsoft Server Software
Two bulletins address vulnerabilities in Microsoft Server this month. The following list details which server products are affected this month, and how severely.
- Microsoft Exchange Server 2007: 1 critical
- Microsoft Exchange Server 2010: 1 critical
- Microsoft Exchange Server 2013: 1 critical
- Microsoft SharePoint Server 2013: 1 important
Deployment Guide
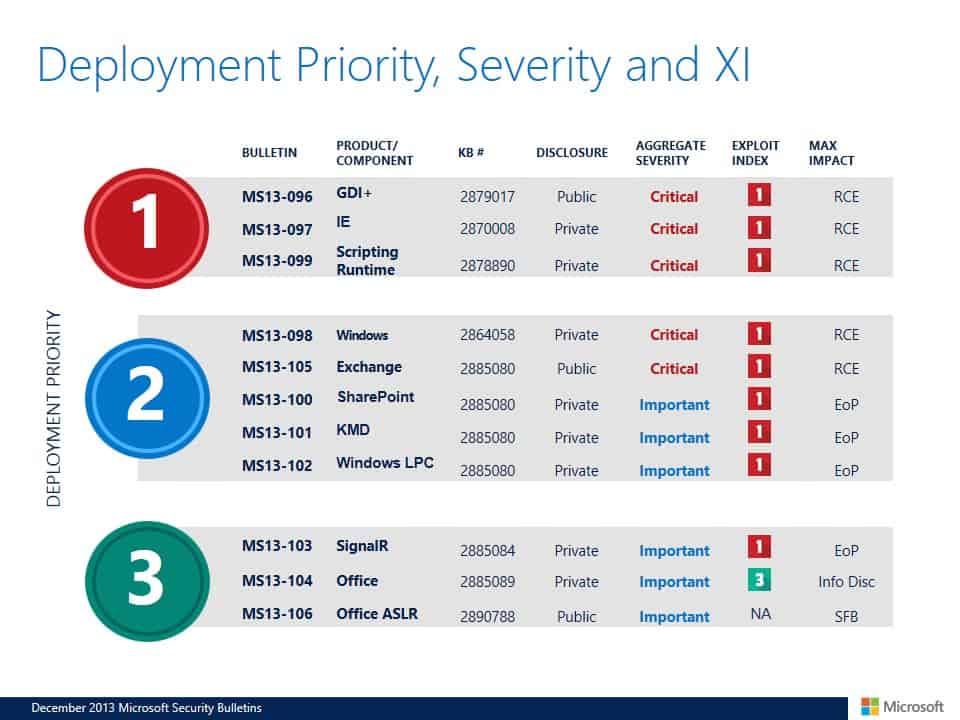
Each month, Microsoft releases a deployment guide that weights the different bulletins in terms of importance. This goes beyond the severity rating of each bulletin, as the company suggests the order of bulletin installation.
While designed for Enterprise customers, system and network administrators in particular, it can also be of use to tech savvy users and others who test bulletins first before they are deployed on live systems.
It should be clear that the deployment priority may change depending on the installed software and system used.
- Tier 1 updates: MS13-096 GDI+, MS13-097 Internet Explorer, MS13-099 Scripting Runtime
- Tier 2 updates: MS13-098 Windows, MS13-105 Exchange, MS13-100 SharePoint, MS13-101 KMD, MS13-102 Windows LPC
- Tier 3 updates: Ms13-103 SignalR, Ms13-104 Office, MS13-106 Office ASLR
Microsoft has released an updated table this month that highlights the Deployment Priority, Severity and XI. In addition to highlighting the bulletins, products and priority, it also highlights the exploit index, maximum impact and disclosure.
Security Bulletins
- MS13-096Vulnerability in Microsoft Graphics Component Could allow Remote Code Execution (2908005)
- MS13-097Cumulative Security Update for Internet Explorer (2898785)
- MS13-098Vulnerability in Windows Could Allow Remote Code Execution (2893294)
- MS13-099 Vulnerability in Microsoft Scripting Runtime Object Library Could Allow Remote Code Execution (2909158)
- MS13-105Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution (2915705)
- MS13-100Vulnerabilities in Microsoft SharePoint Server Could Allow Remote Code Execution (2904244)
- MS13-101Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430)
- MS13-102Vulnerability in LRPC Client Could Allow Elevation of Privilege (2898715)
- MS13-103 Vulnerability in ASP.NET SignalR Could Allow Elevation of Privilege (2905244)
- MS13-104Vulnerability in Microsoft Office Could Allow Information Disclosure (2909976)
- MS13-106 Vulnerability in a Microsoft Office Shared Component Could Allow Security Feature Bypass (2905238)
Other security-related information
Security Advisory 2916652 has been released. It describes an update of the Certificate Trust List (CTL) for all supported versions of Windows. A third-party digital certificate that was trusted before has been removed from the list to protect Windows systems against spoofing and man-in-the-middle attacks.
Security Advisory 2905247Â describes an issue in ASP.Net that could allow the elevation of privilege. The advisory suggests that administrators harden the security by making configuration changes.
Security Advisory 2871690 notifies customers that an update for Windows 8 and Windows Server 2012 is available that revokes digital signatures for specific UEFI modules.
Security Advisory 2915720 finally informs about a change to how Windows verifies Authenticode-signed binaries.
Non-security related updates
- Update for Windows 7 and Windows Server 2008 R2 (KB2847077)
- Update Rollup for Microsoft Windows MultiPoint Server 2012 (KB2864239)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2877213)
- Update for Windows 8, Windows RT, Windows Server 2012, Windows 7, Windows Server 2008 R2, and Windows Server 2008 (KB2891804)
- Update for Microsoft Camera Codec Pack for Windows 8.1 and Windows RT 8.1 (KB2899189)
- Update for Microsoft Camera Codec Pack for Windows 8 and Windows RT (KB2899190)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2903938)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2903939)
- Update for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, Windows Server 2012, Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Server 2003, and Windows XP (KB2904266)
- Update for Windows 8, Windows Server 2012, Windows 7, Windows Server 2008 R2, and Windows Server 2008 (KB2905454)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2907791)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2907800)
- Update for Windows 8.1 and Windows RT 8.1 (KB2909569)
- Update for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, Windows Server 2012, Windows 7, and Windows Server 2008 R2 (KB2913152)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2913253)
- Update for Windows 8.1 and Windows RT 8.1 (KB2913320)
- Windows Malicious Software Removal Tool - December 2013 (KB890830)/Windows Malicious Software Removal Tool - December 2013 (KB890830) - Internet Explorer Version
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2889784)
- Rules Update for Direct Access Best Practice Analyzer for Windows Server 2012 (KB2896496)
- Update for Windows 8.1 (KB2913236)
- Language Packs for Windows RT (KB2607607)
- Language Packs for Windows RT 8.1 (KB2839636)
- Microsoft .NET Framework 4.5.1 (KB2858725)
- Microsoft .NET Framework 4.5.1 Upgrade Language Packs (KB2858725)
- Microsoft .NET Framework 4.5.1 Language Packs for Windows Server 2012 (KB2858726)
- Microsoft .NET Framework 4.5.1 for Windows Server 2012 x64-based Systems (KB2881468)
- Rules Update for Direct Access Best Practice Analyzer for Windows Server 2012 (KB2896496)
- Update for Windows 8.1 (KB2904594)
- Internet Explorer 11 for Windows 7 and Windows Server 2008 R2 (KB2841134)
How to download and install the December 2013 security updates
All security updates are available via Windows Update. This is the recommended update tool for the majority of users. Most systems are configured to download and install the updates automatically.
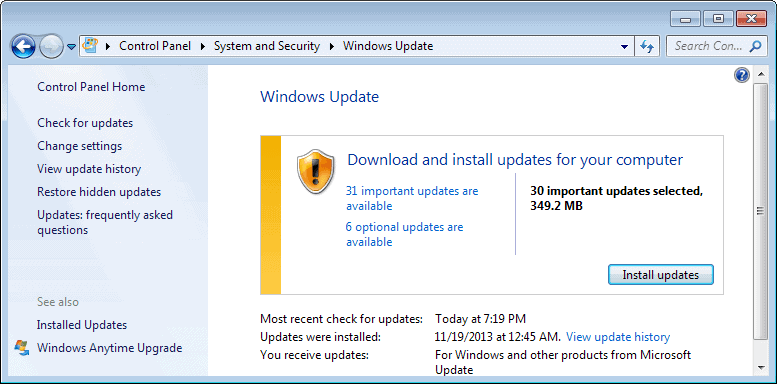
If you want to speed up things, you may want to check for updates manually instead on your system, to download and install the updates right away and not when Windows discovers them.
To do so, tap on the Windows key, enter Windows Update, and select the result from the listing. This should open the Windows Update dialog that you can use to check for new updates.
Some users may not want to use automatic updates for that. This is for instance the case if the updates need to be deployed on multiple systems. While it is possible to download them individually on each system, it does not really make sense to do so from a bandwidth perspective.
Instead of having to download the same updates multiple times, you could instead download them once and deploy them afterwards on each system, even without an active Internet connection.
Another reason for not wanting to use automatic updates is if you want to test updates before they become available.
Updates can be downloaded via third party tools, or directly from Microsoft's Download Center.
Additional information
You can access this month's Security Bulletin summary on this page on the Microsoft website. Additional information about this month's updates are available at the Microsoft Security Response Center blog.
If you prefer video, here is Microsoft's Update Tuesday overview for December 2013.
Advertisement




















The security advisory KB2916652 (http://technet.microsoft.com/en-us/security/advisory/2916652) has been updated to announce the availability of the KB2917500 update for Windows XP and Windows Server 2003 on Microsoft Update or Microsoft Download Center (http://www.microsoft.com/en-us/download/details.aspx?id=41542).
On all other supported versions of Windows, users only need to install update KB2917500 if they didn’t install the “Automatic updater of revocked certificates” (another update offered back in April 2012: http://support.microsoft.com/kb/2677070).
Omphaloskepsis and the December 2013 Security Update Release
There are times when we get too close to a topic. We familiarize ourselves with every aspect and nuance, but fail to recognize not everyone else has done the same. Whether you consider this myopia, navel-gazing, or human nature, the effect is the same. I recognized this during the recent webcast when someone asked the question – “What’s the difference between a security advisory and a security bulletin?†The answer was simple to me, as I’ve been doing this for years, but the question was valid and it reminded me that not every person on the planet knows all of the ins and outs of Update Tuesday….
http://blogs.technet.com/b/msrc/archive/2013/12/10/omphaloskepsis-and-the-december-2013-security-update-release.aspx
Thank you very much for the monthly detailed article about Microsoft updates. As always, easier and faster than having to find your way on the Microsoft security, downloads, support, and blogs sites.
Thank you :)
Microsoft Patch Tuesday: December 2013
This month’s eleven security bulletins address a total of 22 separate vulnerabilities spanning Internet Explorer, Microsoft Office, Exchange, Surface 2 and more.
MS13-088 / KB2888505 – Cumulative Security Update for Internet Explorer
More than half of the vulnerabilities this month are addressed with this one update. MS13-088 resolves ten separate vulnerabilities affecting all versions of Internet Explorer from IE6 to IE11. Two of the flaws could allow information disclosure, and the remaining eight are memory corruption issues that could be exploited to enable an attacker to execute malicious code remotely on the vulnerable system. There are no known exploits in the wild currently for these vulnerabilities, but an attacker could execute an exploit by crafting a malicious Web page and luring users to visit it.
MS13-089 / KB2876331 – Vulnerability in Windows Graphics Device Interface Could Allow Remote Code Execution
This security bulletin is rated as Critical by Microsoft because the flaw could allow an attacker to execute malicious code remotely on the target system, and the flaw impacts all supported versions of Windows from Windows XP to Windows 8.1. The severity, however, is tempered significantly by the fact that an attacker would have to create a malicious file, and somehow convince a user to open it using WordPad – an application that very few people actually use.
MS13-090 / KB2900986 – Cumulative Security Update of ActiveX Kill Bits
MS13-090 is an urgent update for two reasons. First, a successful exploit of the vulnerability enables the attacker to execute malicious code on the compromised system. Second, this is a zero-day flaw that is already being actively exploited in the wild. A specially-crafted malicious Web page can be used to trigger the flawed ActiveX control and compromise the system. All desktop versions of Windows are affected, but the potential threat can be minimized by ensuring users don’t operate with full administrator privileges.
MS13-091 / KB2885093 – Vulnerabilities in Microsoft Office Could Allow Remote Code Execution
This security bulletin addresses three vulnerabilities in Microsoft Office – impacting Office 2003, 2007, 2010, and 2013. One of the three vulnerabilities spans all versions of Office, and will probably be the one any attackers will focus their attention on. The security bulletin is only rated as Important by Microsoft, but because Microsoft Office is so pervasive, and a successful attack could lead to remote code execution, this patch should be a higher priority.
MS13-092 / KB2893986 – Vulnerability in Hyper-V Could Allow Elevation of Privilege
The threat from MS130-092 is relatively limited. The vulnerability is specific to Windows 8 and Windows Server 2012 – Windows 8.1 and Windows Server 2012 R2 are unaffected. A successful attack could lead to an elevation of privilege or to a denial of service by crashing the hypervisor, but the attacker would first need access to a guest virtual machine running within the Hyper-V host in order to pass a specially crafted hypercall to trigger the exploit.
MS13-093 / KB2875783 – Vulnerability in Windows Ancillary Function Driver Could Allow Information Disclosure
This flaw poses very little risk. A memory disclosure vulnerability in the Windows ancillary function driver can lead to an elevation of privilege, and possible information disclosure. However, the attacker has to first be logged on to the vulnerable system with valid local credentials, and then execute a specially-crafted application to trigger the flaw. A remote attacker would first need to successfully exploit of some other flaw to gain control of the target system before this flaw could be a threat.
MS13-094 / KB2894514 – Vulnerability in Microsoft Outlook Could Allow Information Disclosure
This is a publicly disclosed vulnerability that affects Outlook 2007, 2010, and 2013. If an attacker tricks a user into opening a specially-crafted malicious email message using an affected version of Outlook, it could lead to information disclosure. The attacker may be able to extract details such as IP address, open TCP ports, and other sensitive information.
MS13-095 / KB2868626 – Vulnerability in Digital Signatures Could Allow Denial of Service
MS13-095 also poses virtually no real risk in and of itself. A flaw in how Microsoft interprets digital signatures can be exploited with a specially-crafted X.509 certificate to crash the affected system and cause a denial of service condition.
MS13-096 / KB2908005 – Vulnerability in Microsoft Graphics Component Could allow Remote Code Execution
This security update resolves a publicly disclosed vulnerability in Microsoft Windows, Microsoft Office, and Microsoft Lync. The vulnerability could allow remote code execution if a user views content that contains specially crafted TIFF files.
MS13-097 / KB2898785 – Cumulative Security Update for Internet Explorer
This security update resolves seven privately reported vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the most severe of these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS13-098 / KB2893294 – Vulnerability in Windows Could Allow Remote Code Execution
This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user or application runs or installs a specially crafted, signed portable executable (PE) file on an affected system.
MS13-099 / KB2909158 – Vulnerability in Microsoft Scripting Runtime Object Library Could Allow Remote Code Execution
This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker convinces a user to visit a specially crafted website or a website that hosts specially crafted content. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS13-100 / KB2904244 – Vulnerabilities in Microsoft SharePoint Server Could Allow Remote Code Execution
This security update resolves multiple privately reported vulnerabilities in Microsoft Office server software. These vulnerabilities could allow remote code execution if an authenticated attacker sends specially crafted page content to a SharePoint server. An attacker who successfully exploited these vulnerabilities could run arbitrary code in the security context of the W3WP service account on the target SharePoint site.
MS13-101 / KB2880430 – Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege
This security update resolves five privately reported vulnerabilities in Microsoft Windows. The more severe of these vulnerabilities could allow elevation of privilege if an attacker logs on to a system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
MS13-102 / KB2898715 – Vulnerability in LRPC Client Could Allow Elevation of Privilege
This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker spoofs an LRPC server and sends a specially crafted LPC port message to any LRPC client. An attacker who successfully exploited the vulnerability could then install programs; view, change, or delete data; or create new accounts with full administrator rights. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
MS13-103 / KB2905244 – Vulnerability in ASP.NET SignalR Could Allow Elevation of Privilege
This security update resolves a privately reported vulnerability in ASP.NET SignalR. The vulnerability could allow elevation of privilege if an attacker reflects specially crafted JavaScript back to the browser of a targeted user.
MS13-104 / KB2909976 – Vulnerability in Microsoft Office Could Allow Information Disclosure
This security update resolves one privately reported vulnerability in Microsoft Office that could allow information disclosure if a user attempts to open an Office file hosted on a malicious website. An attacker who successfully exploited this vulnerability could ascertain access tokens used to authenticate the current user on a targeted SharePoint or other Microsoft Office server site.
MS13-105 / KB2915705 – Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution
This security update resolves three publicly disclosed vulnerabilities and one privately reported vulnerability in Microsoft Exchange Server. The most severe of these vulnerabilities exist in the WebReady Document Viewing and Data Loss Prevention features of Microsoft Exchange Server. These vulnerabilities could allow remote code execution in the security context of the LocalService account if an attacker sends an email message containing a specially crafted file to a user on an affected Exchange server. The LocalService account has minimum privileges on the local system and presents anonymous credentials on the network.
MS13-106 / KB2905238 – Vulnerability in a Microsoft Office Shared Component Could Allow Security Feature Bypass
This security update resolves one publicly disclosed vulnerability in a Microsoft Office shared component that is currently being exploited. The vulnerability could allow security feature bypass if a user views a specially crafted webpage in a web browser capable of instantiating COM components, such as Internet Explorer. In a web-browsing attack scenario, an attacker who successfully exploited this vulnerability could bypass the Address Space Layout Randomization (ASLR) security feature, which helps protect users from a broad class of vulnerabilities. The security feature bypass by itself does not allow arbitrary code execution. However, an attacker could use this ASLR bypass vulnerability in conjunction with another vulnerability, such as a remote code execution vulnerability that could take advantage of the ASLR bypass to run arbitrary code.
Thanks Ilev for your post every month with details of the Microsoft updates :)
MS Bulletins MS13-088 to MS13-095 are from November, and they don’t appear to have any changes to update files, do they?
Thanks for pointing this :-)
It is a mistake and MS13-088 to MS13-095 were indeed Nov. 2013 updates.
No problem :)
Sometimes I check last month security bulletins too, or updates from the last month on the Download Center, just to be sure there are no newer versions of that updates. It’s not common, but sometimes they post updated versions that may otherwise go unnoticed :)
* MS13-096 – Critical
– https://technet.microsoft.com/security/bulletin/ms13-096
– Reason for Revision: V1.1 (December 10, 2013): Clarified that
users should undo the Disable the TIFF Codec workaround and the
Disable data collaboration in Lync workaround after applying the
update. See the Update FAQ for more information. Added undo
steps to the Disable data collaboration in Lync workaround. These
are informational changes only.
– Originally posted: December 10, 2013
– Updated: December 10, 2013
– Bulletin Severity Rating: Critical
– Version: 1.1
Thanks Martin, For this mount’s update’s explanation. The layout of this mount article looks (ferry) smooth!
Much smoother than the Microsoft’s Update Tuesday overview for December 2013 video. Smirking about the clumsiness is the absolute softest qualification. That a billion dollar firm makes such terrible business video cards is unbelievable. Why not make much more use of the TV screen (in the video) and what about the place the took the movie, Is there no photogenic place in the hole of the USA, or may I say the hole wide world?
Hmm… for some reason the updates aren’t downloading. It’s like my PC keeps searching and trying to download it, but nothing pops-up.
But then again, I’m thinking it has something to do my geographical location and the fact that Windows updates usually kicks in for me on Wednesday. I’ll reschedule the automatic updates for Wednesday to see if this has any effect. It’s probably happening because of some server load scheduling on MS’s end or something.
Martin ,
According to your screen print there are no critical updates, just important one.
Important updates could be skipped with no harm done :-)
Well the critical bulletins only indicate that at least one product is affected in a critical fashion. Maybe it is because I’m running a 64-bit version, do not know but those are all the updates I have received.
If you look at installed updates the critical updates are marked as important, and the important updates are marked as recommended :-)
I think it is time for Microsoft to name the updates properly.
Link broken: Update for Windows 8.1 (KB2904594)
It sometimes takes a while before all those links to live.
It points to wrong KB, correct link: http://support.microsoft.com/kb/2904594
while current leads to: http://support.microsoft.com/kb/2896496
Ah thanks for that, I have corrected the link.