Microsoft Security Bulletins For October 2013 overview

Microsoft has released a new set of updates and patches for its software product a couple of seconds ago. The company releases security updates in one go on every second Tuesday of the month, and only breaks that habit for critical security vulnerabilities that are exploited in the wild.
Today eight bulletins have been published by the company that fix security vulnerabilities in Microsoft Windows and Office, Internet Explorer, Microsoft Server Software, the Microsoft .Net Framework, and Microsoft Silverlight.
Four of the vulnerabilities have received the highest severity rating of critical, and they all affect the Microsoft Windows operating system.
The remaining four bulletins have received a maximum severity rating of important, the second highest rating. Three of them affect Microsoft Office, one Microsoft Server Software, and one Microsoft Silverlight.
Note: Highest or maximum severity rating means that at least one product has received that rating. Other products may have received the same rating, a lower rating, or may not be affected by a particular vulnerability at all.
The update for Internet Explorer will fix the critical vulnerability that came to light earlier this month.
The eight bulletins released this month fix a total of 26 different vulnerabilities in Microsoft products.
Operating System Distribution
All Windows client operating system,s with the exception of Windows RT and the not yet released Windows 8.1 and Windows RT 8.1 are affected by four bulletins that have received a vulnerability rating of critical.
The same is true for server versions of Windows, as all supported Windows Server editions are affected by the critically rated and one moderately rated security bulletin.
- Windows XP: 4 critical
- Windows Vista: 4 critical
- Windows 7:Â 4 critical
- Windows 8:Â 4 critical
- Windows 8.1: 1 critical
- Windows RT: 2 critical, 1 important
- Windows RT 8.1: 1 critical
- Windows Server 2003: 3 critical, 1 moderate
- Windows Server 2008: 3 critical, 1 moderate
- Windows Server 2008 R2: 3 critical, 1 moderate
- Windows Server 2012: 3 critical, 1 moderate
Office Distribution
As far as Microsoft Office is concerned, two bulletins have been released this Patch Tuesday that affect the application. Only Microsoft Office 2007 and Microsoft Office for Mac are affected by both bulletins, while all other supported Office versions are only affected by one.
- Microsoft Office 2003: 1 important
- Microsoft Office 2007: 2 important
- Microsoft Office 2010: 1 important
- Microsoft Office 2013: 1 important
- Microsoft Office for Mac: 2 important
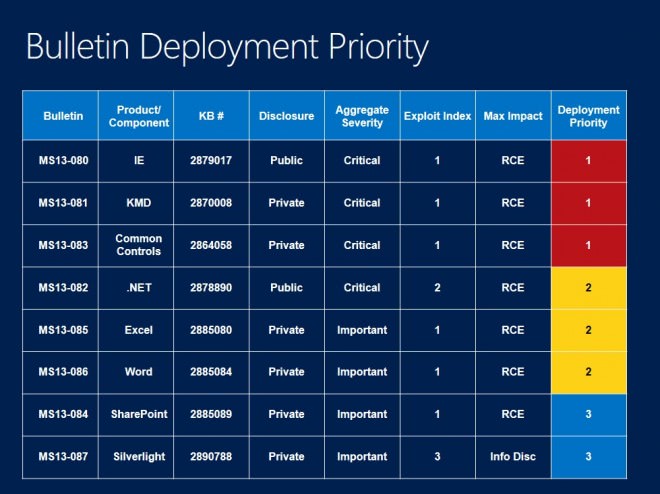
Deployment Guide
Each month, Microsoft releases a bulletin deployment guide that aims to help system and network administrators, and individual interested users alike, determine the update priority of each bulletin released.
While there is no obligation to do so, it is usually best to follow the guide. It usually suggests to install patches that protect against critical vulnerabilities first, but those too may receive different priorities in regards to deployment.
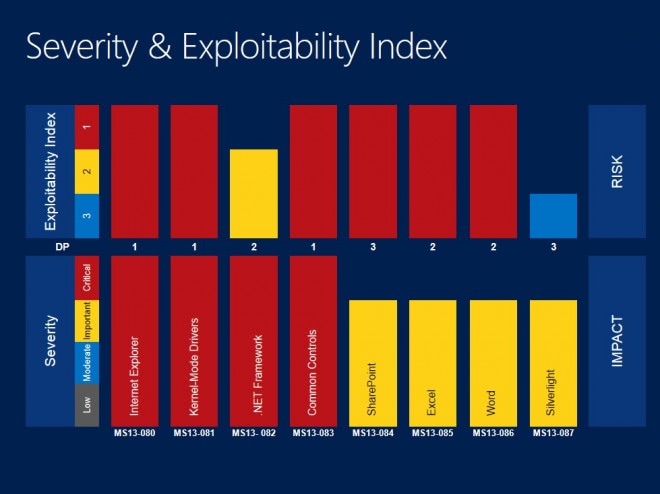
- Tier 1 updates: MS13-080 Internet Explorer, MS13-081 KMD, Ms13-083 Common Controls
- Tier 2 updates: MS13-082Â .NET Framework, MS13-085 Excel, MS13-086 Word
- Tier 3 updates: MS13-084 SharePoint, MS13-087 Silverlight
Security Bulletins
- MS13-080Cumulative Security Update for Internet Explorer (2879017)
- MS13-081Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2870008)
- MS13-082Vulnerabilities in .NET Framework Could Allow Remote Code Execution (2878890)
- MS13-083Vulnerability in Windows Common Control Library Could Allow Remote Code Execution (2864058)
- MS13-084Vulnerabilities in Microsoft SharePoint Server Could Allow Remote Code Execution (2885089)
- MS13-085Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution (2885080)
- MS13-086Vulnerabilities in Microsoft Word Could Allow Remote Code Execution (2885084)
- MS13-087Vulnerability in Silverlight Could Allow Information Disclosure (2890788)
Other Security related updates
- MS13-079: Security Update for Windows 8 for x64-based Systems (KB2853587)
- MS13-076: Security Update for Windows 8 for x64-based Systems (KB2876315)
Non-security related updates
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2802618)
- Update for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2 (KB2834140)
- Update for Microsoft .NET Framework 4 on XP, Server 2003, Vista, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2836939)
- Update for Windows 7 and Windows Server 2008 R2 (KB2846960)
- Update for Windows 7 (KB2852386)
- Update Rollup for Windows Server 2012 Essentials (KB2862551)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2869628)
- Update for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2 (KB2882822)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2883201)
- Update for Windows 7 and Windows Server 2008 R2 (KB2888049)
- Dynamic Update for Windows 8.1 and Windows RT 8.1 (KB2891300)
- Windows Malicious Software Removal Tool - October 2013 (KB890830)/Windows Malicious Software Removal Tool - October 2013 (KB890830) - Internet Explorer Version
- Internet Explorer 10 for Windows 7 and Windows Server 2008 R2 (KB2718695)
- Update for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2808679)
- Microsoft Browser Choice Screen Update for EEA Users of Windows 8.1 (KB976002)
- Language Packs for Windows RT (KB2607607)
- Language Packs for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2839636)
- Update for Windows 7 and Windows Server 2008 R2 (KB2846960)
- Update for Microsoft Camera Codec Pack for Windows 8.1 and Windows RT 8.1 (KB2859675)
- Update for Internet Explorer Flash Player for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, and Windows Server 2012 (KB2889543)
How to download and install the October 2013 security updates

The updates will be deployed automatically on most user systems by the operating system's automatic update feature. While that is the recommended installation method on most systems, some users may want full control over the update process, which automatic updates does not offer.
This is also the case for businesses and organizations who need to test updates before they are deployed on a computer network.
Last but not least, this is also the way to go if updates need to be deployed on systems without direct Internet connection.
All security patches can be downloaded from Microsoft's Download Center either as standalone update downloads, or in form of a monthly ISO image that contains all security patches for that month.
Another alternative to that are third party tools that download updates and patches automatically to the system.
Advertisement




















As always, thank you Martin for your report on Microsoft monthly updates, and thanks Ilev for your comment with additional details :)
i think this has been added twice in this article=>
Update for Windows 7 and Windows Server 2008 R2 (KB2846960)
This month is the 10th anniversary of Patch Tuesday.
Microsoft’s Patch Tuesday Turns 10: A Decade of Botched Updates and Broken PCs
Back in 2003, the Redmond-based tech giant officially introduced a completely new concept for its customers that made many people in the IT industry applaud the company’s efforts to keep its products fully-patched.
Simply called Patch Tuesday, the new patch management process was basically supposed to deliver security updates for all products in Microsoft’s lineup that could be vulnerable to attacks and thus expose users’ data to hackers.
The idea was pretty simple. Microsoft wanted to use the second Tuesday of each month to deliver these updates, with the company promising to keep all users secure by launching all patches at the right moment….
Ten years ago, it all sounded great and Microsoft was clearly very optimistic with its new patch management process. But things changed significantly as the time passed by and Patch Tuesday has now become a nightmare for the millions of Windows users out there….
http://news.softpedia.com/news/Microsoft-s-Patch-Tuesday-Turns-10-A-Decade-of-Botched-Updates-and-Broken-PCs-388580.shtml
Microsoft Patch Tuesday: October 2013
MS13-080 / KB2879017 – Cumulative Security Update for Internet Explorer
MS13-080 is a critical, must-patch-as-soon-as-possible update. It applies to all supported versions of Internet Explorer, and resolves ten separate security flaws in the browser. The real reason that this update is so urgent, though, is that two of the vulnerabilities are being actively exploited in the wild by attacks. The most severe vulnerabilities could allow an attacker to execute code remotely on the vulnerable system just by luring the user to view a specially-crafted malicious website. Microsoft released a Fix-It tool to guard against one of the zero-day exploits, and there was speculation that Microsoft may even release an out-of-band patch before the Patch Tuesday cycle to address the issue, but the volume of attacks never reached a point concerning enough to warrant the rushed update.
MS13-081 / KB2870008 – Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution
MS13-081 is also rated as Critical. It addresses seven different vulnerabilities in Microsoft Windows. A couple of the flaws are related to how the Windows kernel handles font files. This update applies to all versions of the Windows operating system except for the most current: Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2. An attacker can compromise a system and gain complete control of the affected system by getting a user to view content with embedded OpenType or TrueType font files. Sadly, it’s not difficult to con users into opening a malicious file attachment, so it’s important to apply this patch as soon as possible.
MS13-082 / KB2878890 – Vulnerabilities in .NET Framework Could Allow Remote Code Execution
This security bulletin takes care of three flaws in the .NET framework. Two are denial of service flaws, but the third – and most dangerous of the three – is an extension of the OpenType font-parsing vulnerability from MS13-081. Again, an attacker could potentially gain complete control of an affected system by luring users to visit a malicious XAML browser application that exploits the font-parsing flaw.
MS13-083 / KB2864058 – Vulnerabilities in Windows Common Control Library Could Allow Remote Code Execution
MS13-083 deals with a vulnerability in a shared DLL file, Comctl32.dll. All versions of Microsoft Windows are impacted by this flaw except Windows XP SP3, Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2. The issue itself is a memory corruption flaw that can be triggered by an integer overflow in the shared library. There are no Microsoft products that directly expose this flaw to attack, but a wide variety of third-party applications use and rely on this DLL, so it may be more urgent for some organizations to apply this patch. It is rated as Critical by Microsoft because a successful exploit enables the attacker to remotely execute malicious code on the compromised system.
MS13-084 / KB2885089 – Vulnerabilities in Microsoft SharePoint Server Could Allow Remote Code Execution
This patch fixes two vulnerabilities in SharePoint. The impact of the flaws themselves, though, extends beyond just SharePoint. The vulnerabilities affect SharePoint Services 3.0, SharePoint Foundation, SharePoint Server, Excel Services, Word Automation Services, Web Applications 2010, and Excel Web App 2010. One of the two vulnerabilities can lead to code execution in the context of the SharePoint service, and the other enables cross-site scripting attacks. If successfully exploited, an attacker could gain access to the SharePoint server itself, or spoof user actions on the site.
MS13-085 / KB2885080 – Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution
The MS13-085 update is rated as Important by Microsoft. It resolves two vulnerabilities in Microsoft Office that impact Excel 2007, 2010, and 2013, as well as Office for Mac 2011, the Excel Viewer, and the Office Compatibility Pack. The vulnerabilities could enable an attacker to remotely execute malicious code on the compromised system using the same rights and privileges as the currently logged in user. Microsoft stresses that the impact of this threat can be minimized by ensuring that users operate with limited privileges and do not log into Windows as Administrator.
MS13-086 / KB2885084 – Vulnerabilities in Microsoft Word Could Allow Remote Code Execution
MS13-086 is very similar to MS13-085, but it only affects Microsoft Word 2003 and 2007, along with the Office Compatibility Pack. The vulnerabilities can be exploited to allow the attacker to execute arbitrary code in the context of the logged in user. Again, best practices suggest users not log into Windows as Administrator, which will reduce the potential impact of a successful exploit.
MS13-087 / KB2890788 – Vulnerability in Silverlight Could Allow Information Disclosure
Microsoft rated MS13-087 as Important. There is a flaw in Silverlight 5, and the Silverlight 5 developer runtime, which can be exploited using a specially-crafted malicious website. There is no risk of remote code execution, which is part of why Microsoft gave this security bulletin a lower level of urgency, but an attacker can exploit this flaw to view local data on the target system.
wow now we can delete OUTDATED UPDATE BACKUP using disk cleanup in windows 7.
but how to do it with command line?
any idea.
@ank91
For command line : http://support.microsoft.com/kb/315246
@ank91
Thanks for the tip.
http://support.microsoft.com/kb/2852386
No, we can’t.
It was possible in XP but it is not possible since Vista as updates
are backed up incrementally by the Shadow copy function.
kb2852386 for win 7 adds new feature in win 7 by which we can delete superseeded hotfix backup from winsxs.
thats cool.
martin, can you investigate?
That’s a lot of updates! Considering MS has been on a roll lately with patch Tuesday’s I’m going to go on a limb here and say there will be at least one regression/bad update this month. : )
Thanks again Martin,
This mouth 25 Microsoft updates and this month I had a strange thing (what never happened before) happening after I updated and rebooted main system. The system asked when it completed booted up for another restarted/reboot from the system?
It can happen that the computer needs to be restarted several times for all updates to be installed on the system. On my W7 64-bit system, it took only one reboot though.