Encrypt and erase to delete data reliable on SSDs
The security of data on Solid State Drives (SSDs) is not only important for government agencies and enterprises, but also for end users. Even if you do not plan on selling or giving away the hard drive or computer at all, you may encounter situations where someone else gets access to the PC. Maybe it is stolen by a thief, taken from you by a police raid, or someone in your organization or home starts to look at the data it contains more closely.
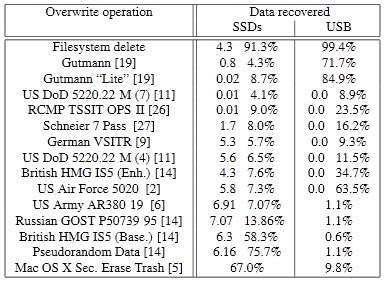
Modern SSDs come with options to securely erase the data on the drive, and that is likely what some will use to delete the data (the majority likely will not delete data at all, or only use a quick format to delete the data). Research has shown that several manufacturer issued disk sanitizing tools do not erase all of the data on the disk.
The "Reliably erasing data from Flash-based Solid State Drives" research paper from 2011 is particularly interesting in this regard as it analyzes existing techniques that include overwriting, degaussing and encryption. The researchers found [pdf] that "none of of the available software techniques for sanitizing individual ï¬les were effective.
-
All single-ï¬le overwrite sanitization protocols failed: between 4% and 75% of the ï¬les’ contents remained on the SATA SSDs. USB drives performed no better: between 0.57% and 84.9% of the data remained
- Encryption is only effective if the key store is properly sanitized.
Back then the researchers suggested a hybrid approach they called SAFE which combines encryption with secure erase.
Side note: I'm not aware of any recent studies that take into account the advancements made in drive technology in the past year. It would be interesting to see if improvements have been made in that time. Even if that is the case, the methodology is still important for older drives.
Scramble and Finally Erase (SAFE) combines the advantages of encrypting files or the full drive with secure erase to make data unrecoverable on the drive. You find the research paper here [pdf].
To summarize the algorithm:
- You encrypt the whole drive using disk encryption software like True Crypt or DiskCryptor, create a secure container on the drive, or encrypt individual files. The latter can be done with programs such as 7-Zip or WinRar (commercial). This can and should be done immediately to protect the data from third parties right away
- Before you give away the drive, throw it away, or re-purpose it in any way, you use a program to securely erase the data on the drive. Parted Magic can do that, as can Secure Erase.
The algorithm works for all drives, platter-based and Flash-based. (via Windows Secrets, thanks Ilev)
Advertisement



















My understanding from the Wikipedia article is that for most efforts, magnetic drives only need a single rewrite
https://en.wikipedia.org/wiki/Data_erasure#Number_of_overwrites_needed
Additionally, writing to a flash media drive more times than is necessary (say the full Gutmann) can dramatically reduce it’s life:
https://en.wikipedia.org/wiki/Write_amplification
Any suggestions on a good balance? Thanks for the post.
Obviously the primary benefit of the SAFE method is the encryption. If you trust the encryption can’t be broken while you HAVE the SSD, you might as well trust it to not be broken when you dump it…
The erase of encrypted data just adds an additional safety factor because now the encryption is messed up. It’s for the truly paranoid who are worried that some entity might have enough powerful decryption capability to enable them to decrypt the data given enough time once the data is in their hands.
But again, if you’re trusting the encryption in the first place, once the data is stolen, the same scenario exists: someone with enough decrypt power can still get your data because at that point you have NOT erased it!
The real problem with encryption – on SSD or hard drive – is that you have to make sure the program you use erases the work space used to encrypt the file – or do it entirely in memory (or perhaps in place so the original file is destroyed in the process.)
So either you have to encrypt the file automatically on a fully encrypted SSD drive, or you have to make sure you encrypt on a hard drive, not a non-fully-encrypted SSD, and make sure any work space on the hard drive has been securely erased. If you encrypt on a non-fully-encrypted SSD, the work space used might have fragments of the original unencrypted file which might be recoverable.
Doing encryption right is not as easy as it seems.
I’ve been using Iolo’s Drive Scrubber for years. I can not say how good it is, does anybody know? Is this a false security on my part?
bob
Well a basic test would include trying to recover files using file recovery software. But even if those programs do not show anything, there is still a chance that files may be recoverable after all (with the right tool set and skills).
Great article Martin. Thanks!
I read this nice piece of info this morning on the windows secret paid newsletter version.
Pretty awesome.