EMET, Microsoft's Enhanced Mitigation Experience Toolkit
A few days ago I took a look at SEHOP (Structured Exception Handler Overwrite Protection), a Windows security feature that is disabled by default in Windows Vista and Windows 7, and enabled in Server products. SEHOP adds a mitigation technique to the operating system to prevent attackers from exploiting software vulnerabilities on the system. It is in this regard a pro-active defense mechanism that protects against certain unpatched vulnerabilities.
Chris Earner mentioned EMET in the comments, a Microsoft tool that let you configure SEHOP and other security features in a graphical user interface.
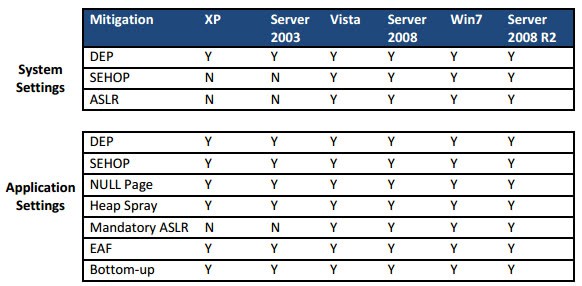
Microsoft's Enhanced Mitigation Experience Toolkit can be downloaded at the official Download Center. The product is compatible with all recent versions of Windows, including Windows XP, Vista and 7, as well as the server operating systems. Some features may however not be available in XP.
The program installs a notifier on the system and a gui application that you can start from the start menu.
It allows you to configure the following security features in a variety of ways on the system:
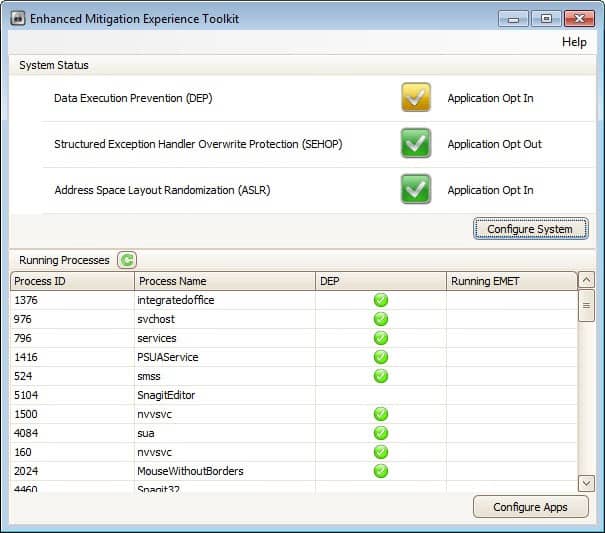
- Data Execution Prevention (DEP)
- Structured Exception Handler Overwrite Protection (SEHOP)
- Address Space Layout Randomization (ASLR)
The program displays the system status of all three features and the status of running processes on startup. Features can either be opt in or opt out for applications, with individual per-process settings available as well.
A click on configure system offers to switch between custom, recommended and maximum security settings. Depending on the selection, features are either changed to opt in our opt out, with the custom setting allowing you to make the selection for each feature individually.
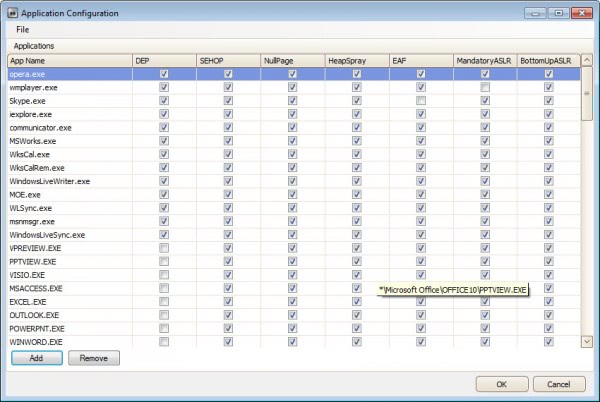
Instead of configuring security features on a global level, you can instead configure them on a per-process level instead. A click on configure apps in the main application window gives you options to configure program executables individually. Additional options are available here: Null Page, Heap Spray, EAF, Bottom-up
Windows 64-bit users need to note that some features are only available for 32-bit processes and not 64-bit processes running on their system. The EMET user guide offers information about the available mitigation techniques, you find it in the program directory on the system.
Please note that adding processes to the application listing may have negative stability effects. While most should work just fine, some may crash or not start at all after you have enabled certain security features in EMET. The EMET Support forum may be of help here.
When it comes to processes to add, it is probably best to look at processes that are attacked more often than others. You may then come up with a list of plugins like Java or Flash, web browsers, Adobe products, Microsoft Office and other high profile programs that you want to add to EMET.
EMET furthermore ships with three protection profiles which you find in the program directory under Deployment. They can be imported into EMET under File > Import in the Application Configuration window. Here it is also possible to export the current security configuration which may be helpful if you want to deploy the same protection on other computer systems. System administrators can use the Group Policy or System Center Configuration Manager to deploy, configure and monitor EMET installations in Enterprise environments.
Tests have shown that EMET can protect the system against vulnerabilities that could otherwise be exploited by attacks and malware.
Closing Words
EMET is an excellent security tool that you can deploy easily on a single PC or across a network of computers. You will spend some time configuring and testing processes, but once that is out of the way, you have added protection to your system that automatically mitigates several popular attack forms.
Advertisement




















Thank you Martin, am now going to look at your Link (have been having horrendous computer crashes, have been repeatedly doing reinstallalations with Windows 7 and want Linux Mint MATE Nadia Please!!!
EEEEEEEKKK HOWL!!!
TOO GEEKY!!!!!
Do not know where on Ghacks to write this question but am doing it here because it probably could go into “Security” category.
Have got Windows 7 Home Premium and like to have on Desktop a lot of stuff from “Control Panel” and “All Programs > Accessories”.
Problem is that a lot of the time (but not always) when the PC is booted-up some or even all of the Icons from “Control Panel” and “Accessories” are gone from Desktop!!!
The computer is brand new and have used diagnostic programs on the Hard-drive but they all say there is nothing wrong with it.
Check out this, it may help you: https://www.ghacks.net/2010/03/30/fix-windows-7-desktop-shortcuts-disappearing/
It is also surprising that it is not easy to find a complete in-depth step by step checklist of securing a Windows machine: registry changes, services that may be disabled without problems, advanced policy configuration etc.
They do exist, but almost all of them are geared towards a Active Directory environment, not a stand-alone computer.
Microsoft has a couple standards of differing security. See http://technet.microsoft.com/en-us/library/cc677002.aspx for the tool.
It is surprising that EMET is still not promoted widely even though it is an excellent method of protecting the PC from malware.
I have been using it since long and can vouch for it. An advanced user can even skip anti-virus softwares if EMET is configured well. For a normal user, EMET and a light antivirus software is an almost bulletproof method to secure the PC.
A good start to set-up EMET can be found here: http://www.rationallyparanoid.com/articles/microsoft-emet-2.html