Protect Files From Unauthorized Access With Encoding Decoding
Full disc encryption or encrypted container files are useful to prevent unauthorized access to a larger number of files. This may feel like overkill though if you only want to make sure that a single file is protected from access. That's where a program like Encoding Decoding comes into play. The program, available as a portable version and setup, can be used to encrypt and decrypt individual files in record time.
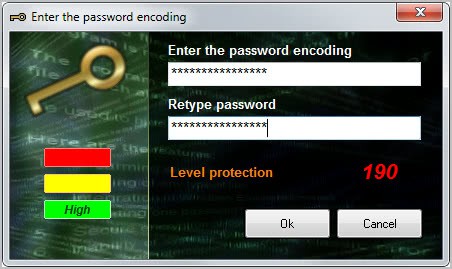
All that needs to be done is to drag and drop a file into the application window to encrypt or decrypt files. A password prompt is displayed if you drag and drop an unencrypted file into the program interface. This password along with an internal algorithm is used to encrypt the file, so that only users with the password can decrypt it to access its contents. Encoding Decoding displays the password strength of the selected password directly in the program interface which can act as a guideline for users who want to make sure they select a secure password.
Please note that the original file will remain on the system. If you do not want that, you need to delete it manually as there is no option to delete the original file automatically after a successful encryption. Check out securely delete files if you want to delete the file so that it cannot be recovered anymore.
The decryption works in exactly the same way. Drag and drop an encrypted file into the program interface and enter the correct password to decrypt the file. The file is then saved to the same directory the encrypted file is stored in.
Users who do not want to drag and drop files into the interface can alternatively click in the program window to open the file browser. The program supports three different encoding algorithms which are unfortunately not explained in the program window, help file or the developer page.
Windows users interested in the program can download it from the developer website. It is compatible with all recent 32-bit and 64-bit editions of the operating system.
Advertisement





















I second Crodol. We can’t rely on such a product when it doesn’t give adequate security. Even if you just need to “hide” files from your spouse/relatives, you can get better security using an encrypted 7z or rar archive, which you probably have a program installed to create one.
It would help if the program has good documentation explaining how it works, what algorithm it uses, what mode of operation is implemented, and how the encryption keys are generated (PBKDF2? If so, how many rounds using which hash function?). Instead, it has a one page “guide” that explains nothing. Also, what makes “ultra encoding” more secure? Shouldn’t that be implemented/checked by default?
Lastly, I tried the portable version but it requires UAC elevation. That’s not very portable or trustworthy.
My suggestion for an open source alternative is AxCrypt (http://sourceforge.net/projects/axcrypt/)
If you are looking to hide files from a friend or relative a simple right click ‘hidden’ should do the trick, if you are looking into actually password locking files, i would want to know what types of algorithms are in use, at least blowfish i hope.
The big question is what algorithm is used and if it is a atrustworthy (open source?) implementation. If not than you are much better off using some zip-program like the free PeaZip or Totalcommander…
You are right. But it also depends on the use. If you just want to hide a file from a relative or friend, then you may not really need to know which algorithm the program uses. Unless your friend or relative is a computer geek, that is.