Microsoft Releases First 2012 Security Update
Microsoft today has released seven security related bulletins that fix issues in the Windows operating system and in Microsoft's Developer Tools. One bulletin has received the maximum severity rating of critical, the highest available rating, while the remaining six bulletins have all received a rating of important, the third highest rating.
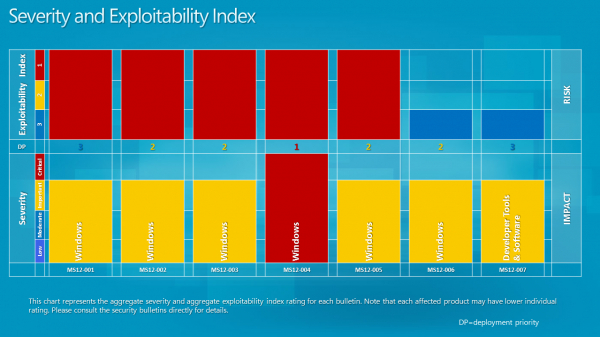
It is interesting to note that the severity rating of the first bulletin is critical on Windows XP and Vista, while only important on Windows 7 and Windows Server 2008 R2. When you look at all bulletins you will notice that Windows XP is affected by all, Vista by five and Windows 7 by four of the vulnerabilities addressed in the bulletins.
The Security Bulletins have just been posted on Microsoft's Technet website. Here is this month's summary with links to each security bulletin.
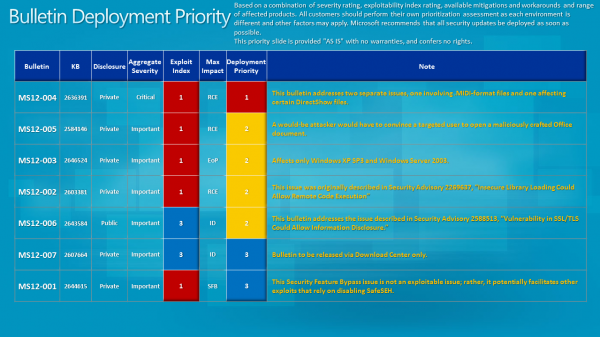
- MS12-004 - Vulnerabilities in Windows Media Could Allow Remote Code Execution (2636391) - This security update resolves two privately reported vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if a user opens a specially crafted media file. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-001 - Vulnerability in Windows Kernel Could Allow Security Feature Bypass (2644615) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow an attacker to bypass the SafeSEH security feature in a software application. An attacker could then use other vulnerabilities to leverage the structured exception handler to run arbitrary code. Only software applications that were compiled using Microsoft Visual C++ .NET 2003 can be used to exploit this vulnerability.
- MS12-002 - Vulnerability in Windows Object Packager Could Allow Remote Code Execution (2603381) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a legitimate file with an embedded packaged object that is located in the same network directory as a specially crafted executable file. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-003 - Vulnerability in Windows Client/Server Run-time Subsystem Could Allow Elevation of Privilege (2646524) - This security update resolves one privately reported vulnerability in Microsoft Windows. This security update is rated Important for all supported editions of Windows XP, Windows Server 2003, Windows Vista, and Windows Server 2008. All supported editions of Windows 7 and Windows Server 2008 R2 are not affected by this vulnerability.
The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application. The attacker could then take complete control of the affected system and install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability can only be exploited on systems configured with a Chinese, Japanese, or Korean system locale.
- MS12-005 - Vulnerability in Microsoft Windows Could Allow Remote Code Execution (2584146) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Office file containing a malicious embedded ClickOnce application. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-006 - Vulnerability in SSL/TLS Could Allow Information Disclosure (2643584) - This security update resolves a publicly disclosed vulnerability in SSL 3.0 and TLS 1.0. This vulnerability affects the protocol itself and is not specific to the Windows operating system. The vulnerability could allow information disclosure if an attacker intercepts encrypted web traffic served from an affected system. TLS 1.1, TLS 1.2, and all cipher suites that do not use CBC mode are not affected.
- MS12-007 - Vulnerability in AntiXSS Library Could Allow Information Disclosure (2607664) - This security update resolves one privately reported vulnerability in the Microsoft Anti-Cross Site Scripting (AntiXSS) Library. The vulnerability could allow information disclosure if a an attacker passes a malicious script to a website using the sanitization function of the AntiXSS Library. The consequences of the disclosure of that information depend on the nature of the information itself. Note that this vulnerability would not allow an attacker to execute code or to elevate the attacker's user rights directly, but it could be used to produce information that could be used to try to further compromise the affected system. Only sites that use the sanitization module of the AntiXSS Library are affected by this vulnerability.
The updates are already available on Windows Update. The easiest way to open the updating tool is to click on the start menu orb and select Windows Update from the program listing there.
Windows users who do not want to or can't use Windows Updates can download the updates from Microsoft's Download Center beginning later today. Microsoft as usual will release an ISO image with all security updates of the month for easier distribution.
Update: The severity and exploitability index and bulletin deployment information have been posted.
The next security updates will be released on February 14, 2012.
Advertisement




















Haven’t noticed any issues and I got all the recent updates.
Of course, the sites that no longer work could be dependant on which Browser you use!
MS12-006 – Vulnerability in SSL/TLS
There are a number of known issues with the patch, and you may find that some sites no longer work once you have installed it.
I got 5 updates for Window 7 64 bit. MS12-006 – Vulnerability in SSL/TLS hasn’t been auto selected (my default browser is Chrome). I installed MS12-006 too.
By me the security update KB 2584146 (89kb) was not automatically selected, but i checked the box anyway and installed it. How come this update was not automatically selected and can it do it any harm now I installed it? Should I uninstall it?
Here are more information about the update: http://support.microsoft.com/kb/2584146
Just got them now., the first of many for 2012!!
Only got 5 this time, which is fine by me! :)