Bitdefender USB Immunizer, Protect Removable Drives To Autorun-Based Attacks
Back in the days of the floppy drive, disks where the most common way of spreading viruses and malware. The Internet has taken over, and floppy drives are long gone.
They have been replaced by removable drives and optical discs, which are also capable of spreading malware, and while they are not the number one attack vector anymore, they still pose a threat.
Autorun attacks, like that by the Stuxnet worm, have become a common attack form. That common, that Microsoft has started to patch the autorun functionality in Windows.
Panda Security released USB Vaccine a while ago which offered to vaccinate a computer or USB drive to protect the computer from autorun based attacks.
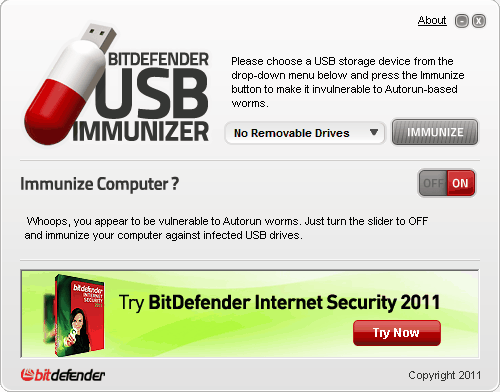
Bitdefender, another popular security developer, has now released a similar program called Bitdefender Immunizer.

The program offers the same functionality as Panda USB Vaccine. Users can either immunize the computer as a whole, or immunize a connected removable drive.
The product page describes what happens if you immunize an USB drive:
The Immunize option allows you to immunize your USB storage device or SD card against infections with autorun-based malware. Even if your storage device has been plugged into an infected computer, the piece of malware will be unable to create its autorun.inf file, thus annihilating any chance of auto-launching itself.
This basically blocks the creation of autorun.inf files on immunized USB devices.
The computer immunization has the following effect:
The Immunize Computer slider allows you to toggle the autorun feature On or Off for any removable media (except for CD/DVD-ROM devices). If you accidentally plug in an infected USB drive that has not been immunized, the computer will not auto-execute the piece of malware located on the USB storage device.
The security patch linked above seems to have the same effect as the Immunize Computer option.
It has to be noted that immunizing removable devices or computers does not protect the system if the user executes malicious software on the device or computer manually. It only protects against autorun-based attack forms that require no user interaction.
Interested users can download USB Immunizer from the Bitdefender Labs website.
Update: Bastik has posted his findings in the comments, they are important and need to be mentioned in the article. Thanks Bastik for the helpful insight.
The tool does not offer to remove the protection from drives that it has immunized. To unprotect a drive you need to display hidden files in Windows and hidden system files. This can be done via Tools > Folder Options > View in Windows Explorer. You then need to delete the folder autorun.ini on the drive.
The tool displays an email prompt on exit with no apparent option to close it. Just click the ok button without entering an email address to close the program for good.



























I think Windows XP, Vista and 7 with the latest updates installed (KB971029 – March 2011) should no longer autorun programs from USB sticks, external drives or removable drives (only CDs or DVDs).
Anyway this may be a good idea to protect USB drives from being infected if conected to an infected machine. But is this trick of the autorun.inf folder still safe (malware just have to delete the folder or previous autorun.inf and write its own)? I have always formated my USB sticks with NTFS and used permissions to keep anyone from writing or creating files on the USB stick root folder (only read permissions allowed for Administrators, System, Everyone and Owner), and only allowing writing inside subfolders. This always worked well for me.
Thanks for the article :)
This is indeed an old trick, and marketing this as a security solution doesn’t give me too much confidence in a product or developer. The only reason that a malware can’t simply remove the folder and write it’s own infected autorun.inf is that it doesn’t bother to do so – and that’s because most USB drive don’t have this kind of protection. If someday this will change, the malware behavior will change too.
Creating a read-only autorun.inf folder is an old trick. I’ve been using it for a few years now.
Their dark blue links on dark gray background on responses makes my eyes hurt.
There’s no help at all the page is not helpful and the tool comes zipped, but is just an .exe (no install) with no help included. Their is nothing explained in the exe and the webpage is just partly helpful.
However here is what it does for immunizing the removable drive :
(Requires to have admin rights, which the application asks for)
– remove autorun.inf (if present on the selected drive)
– create a folder called “autorun.inf”
– which contains a folder called “bdsanitize1.dir” and two files called “bdsanitize1.file” and “bdsanitize2.file
– “bdsanitize1.dir” contains a folder named “bdsanitize2.dir” and the same files as above
– “bdsanitize2.dir” is empty
– All files and folders are hidden and marked as system files (which hides them even if you let windows display hidden files), all files are zero bytes.
The creation of an autorun.txt works fine, but creating or copying a autorun.inf on the drive results in a message that an autorun.inf is already present and that I have to choose another name. It’s not possible to overwrite the file.
The tool can not remove the protection it added to a drive, which looks like a downside, but might be not the case. If that tool can’t remove the protection it added, then specialized malware shouldn’t be able too.
How to remove the protection:
(there is no instruction on how to do that)
(works without admin rights)
– Make Windows display hidden files
– Make it display (critical) system files
– Delete the folder “autorun.ini” (You’ll get some warnings that system files should not be deleted)
Formating the drive should work too. I guess you can remove this protection with an OS that does ignore all that.
Tested with an FAT formated removable drive.
Further I want to add that the tool includes a banner which displays advertisements for BD, which is legit, but the images are changing to quicly for me. Also it asks for your email when you close the tool, which you do not have to enter.
Bastik, thanks for your input, it has likely cleared some questions that users might have. I agree on the banner issue. Have updated the article to reflect this, and the email form (with no optout other than clickin ok)
Well, that’s true about floppies and that was a common vector for viruses way back when. But anyone with a half an ounce of sense or working within an informed business structure had on hand a little sheet of sticky tabs and used one to cover the write-slot on the 5.25″ disks. Later it became merely force of habit to move the little slider in the write-window of the three and a half inchers.
I have two ancient USB sticks, a 1.1 64 MB and a 2.0 128 MB (yes, megabytes) that have slide switches to enable write protection. I have on several occasions mounted each on severely infected systems running autorun.inf exploits among others. The USB sticks remained unaffected.
To this day I keep the 2.0 stick loaded with some premium portable/stand-alone diagnostic and cleanup utilities and have used it with great success; yes, 128 MB is plenty roomy for that.
Icing on the cake is both sticks use blazingly fast “old school” SLC flash memory and even the 1.1 is about as fast as all of the current single channel MLC types. It comes in handy for quick sneaker net file transfers when I get fed up with some ones dysfunction file sharing or accounts permissions.
To my knowledge one can no longer acquire a switch protected USB stick. At any price. So sad.
Any reason why companies do not produce sticks with write protection sliders anymore?