How do you spot a phishing site on today's Internet?
Phishing has been around for a very long time on the Internet; it refers to certain techniques that criminals use to steal passwords, credit card information, Social Security Numbers, and other valuable information.
One common technique lures unsuspecting users to a domain that looks like the destination they want to visit; Facebook's login page, a bank's website, PayPal, eBay, Amazon, or any other eCommerce site or high profile target.
The links are distributed via email campaigns, on websites, or in chat rooms.
Users were asked to look for a green padlock icon in the browser to make sure the connection to the site was secure and to verify the address of the site as well.
The padlock icon is no longer a good indicator; in fact, it never was one to begin with on its own as it merely indicated that the connection to the site was secure. Identification only worked in combination with a site's URL.
More than half of the phishing sites on today's Internet use SSL according to a new report. The rise of HTTPS, in no small part thanks to Google's pushing in Chrome and the introduction of Let's Encrypt, a service to generate free SSL certificates, forced the hand of website owners and criminals alike. Chrome flagging all HTTP sites as "not secure" played a part in that.
How do you identify phishing sites on today's Internet then?
1. The website address (URL)
The number one option to identify a phishing site is to verify its URL; this works only if you know about the address in first place.
If you don't know the URL, then you will have to research it. One option that you have is to run a search for the site name and use a trustworthy resource to make sure it is the right address for the site or service.
Some search engines, e.g. Microsoft's Bing, highlight the official site of popular companies and services when you search for them.
Tip: Firefox users should make a change to the configuration of the browser to make sure that internationalized domain names are always shown as their punycode alternative as you may not be able to distinguish domain names otherwise.
Once you have verified the address, verify that the connection is secure by checking the padlock icon and/or the protocol (it should read https://).
2. How you go there
The majority of phishing attacks start with a link most often, e.g. in an email or a chat message. One of the easiest options to avoid most phishing attacks is to never click on links in emails or chat interfaces.
While website links may point to phishing sites as well, links in emails or messages are probably more common than those.
Here is what you can do: instead of clicking on a link in an email that claims to be from PayPal, you could visit the site manually instead if you think it could be urgent.
Phishing links may also come in form of online advertisement and it is harder to detect. Content blockers help in this case.
3. Research
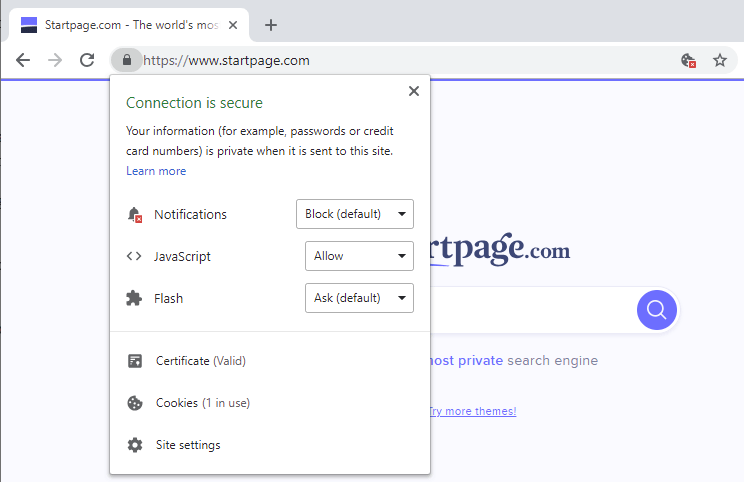
Browsers may display additional information about sites you connect to. A click on the icon in front of the address displays a screen with information usually.
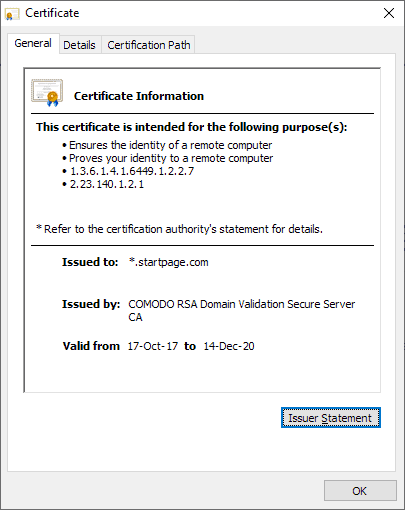
Google Chrome displays whether the connection is secure and the certificate is valid. A click on certificate opens information about the certificate including the entity it was issued to and the certification authority that issued it.
4. Indicators that are not accurate enough
Many articles and tutorials that offer advice on phishing sites suggest to check the content and visuals of a site. Their reasoning is that phishing sites often contain spelling or grammar errors, or may use a different layout or design when compared to the original.
While that may very well be the case, phishing sites often copy content from the original site. Emails that include phishing links may be easier to spot but even there it is not a 100% way to determine whether a site is a phishing site or not.
The same is true for trust signals on a site, e.g. trust icons, a "star-rating", or third-party reviews on other sites. All of these signals can be faked quite easily.
Now You: How do you make sure that a site is legitimate?




















@Martin,
I don’t see that menu shown in your screenshot of Startpage when I click the Info icon using Waterfox. This is all that appears: http://imgbox.com/6LM5sbGZ
Opening the submenu just reveals that the site has been certified by Comodo. Nothing else anywhere.
Click on the arrow next to “Secure Connection”, then click “More Information”.
From there you’ll be able to see the website certificate.
https://linx.li/selif/8orndygg.png
Yes, I’m aware of that already John, but the menu which shows in Martin’s screenshot doesn’t appear in Waterfox i.e. Javascript, Notifications, Flash etc. That’s what I was referring to.
Item 3 is wrong. For this very site, Chrome says the certificate was issued to fastly.net. The problem is the difference between DV and EV certificates. EV offers validation of the owner of the website. DV does not. This is a big deal and really needs to be part of this checklist.
Use a manager like LastPass or 1Pass – they will not fill out fraudulent sites since credentials are based on recognizing the URL – I have avoided a very convincing PayPal site that way (I don’t know virtually any of my passwords – if LastPass doesn’t fill out my credentials they are’t getting filled out)
Personally I rely to a certain point on my OS and browser “defense arsenal”. I could be caught, I try to remain aware that no digital defense is perfect.
There is a dedicated extension for Firefox I’ve used flawlessly in the past but abandoned because of its very way of processing : it has to consult its online database on every site visited by the user and even though the company is world-wide known for its professionalism and integrity, I dislike being followed should it be by a bodyguard : ‘Netcraft Anti-Phishing Extension’. With that no phishing is possible, at least closer to 100% than my arsenal.
I never, *EVER* conduct business of a confidential nature on the internet. I don’t pay my bills online, I don’t pay for or order stuff with a credit card (which in any event, I don’t use and have never had), I don’t look up my medical history, etc. etc. etc.
Phishers are out of luck, aren’t very likely to fool me.
The internet is an unsecure venue for conducting business, so sticking your hand out there for it to get chopped off is foolish.
Chrome and Firefox alert users on fishing, malware… sites.
Eventually, takes them a good day to get the warnings in place
That is right, but these need to be detected or reported before that is the case.
Please note also >
https://krebsonsecurity.com/2018/11/half-of-all-phishing-sites-now-have-the-padlock/#more-45784
@RD:
This is why I think it’s dangerous to refer to “padlock” vs “nonpadlock” sites in terms of “safe” and “dangerous”. The padlock symbol refers to the security of the communication to the site, not whether or not the site itself is “safe”.
In addition to Martin’s four points, you can use specialist block lists (either in the HOSTS file or in your browser’s adblocker) to help protect against phishing sites.
“How do you make sure that a site is legitimate?”
My main weapon is that I don’t follow links that are sent to me. If I get a link that appears to be genuinely important, then I go that website using my known-good bookmark (if I don’t have the site bookmarked, then it’s not one that I’ve engaged with before and so I can ignore the link entirely) and try to get to whatever action the link is trying to get me to do by browsing around.
This works because the only links that might be important are ones that indicate a problem with an account of mine somewhere — and if that problem is real, then there will certainly be a notification on the site’s account page itself.
The provided link is thus unimportant and I wont’ follow it regardless.
I stopped following most external links a while ago. I usually copy those addresses to clipboard and paste it myself in the address bar – this way I’m also stripping any referral information manually.
Copying a link isn’t a really good idea considering IDN attacks.
Here are a couple of places that offer some help with knowing where you are going (not a complete list):
https://safeweb.norton.com/
http://urlxray.com/getbookmarklet.php
A good hard look at trick URL misspellings always helps before you go somewhere new. That, plus a little “whois” research to see who the owners of a site might be.
My best defense over the years has been to “just say no”, and to avoid going any place I am even slightly unsure of.