CloudFogger, Secure File Storage In The Cloud
Services like Dropbox, Microsoft OneDrive or Spideroak make life more comfortable for users who work on different devices regularly. They are file sync and online storage solutions that act as backup storage, online storage for sharing and access, and for distributing files across devices.
With the move to the cloud, come security considerations. What if the service that you store your data on gets hacked, or a third party manages to get access to the files? If you do not protect your data, it could get stolen by hackers or accessed by third parties.
Update: Cloudfogger is no longer available. We suggest you check out some of the alternatives listed on this page.
If you do not want to risk that, you have two options: Do not make data available in the cloud, or use additional protection - read encryption - to protect it from third party access.
You can use traditional programs like True Crypt for that, or a new breed of programs that have been optimized for protecting files in the cloud.
Cloudfogger is a new secure file storage software for the Windows operating system that works well with cloud storage services like Dropbox, Box.net or OneDrive, and local storage.
Here is how it works.
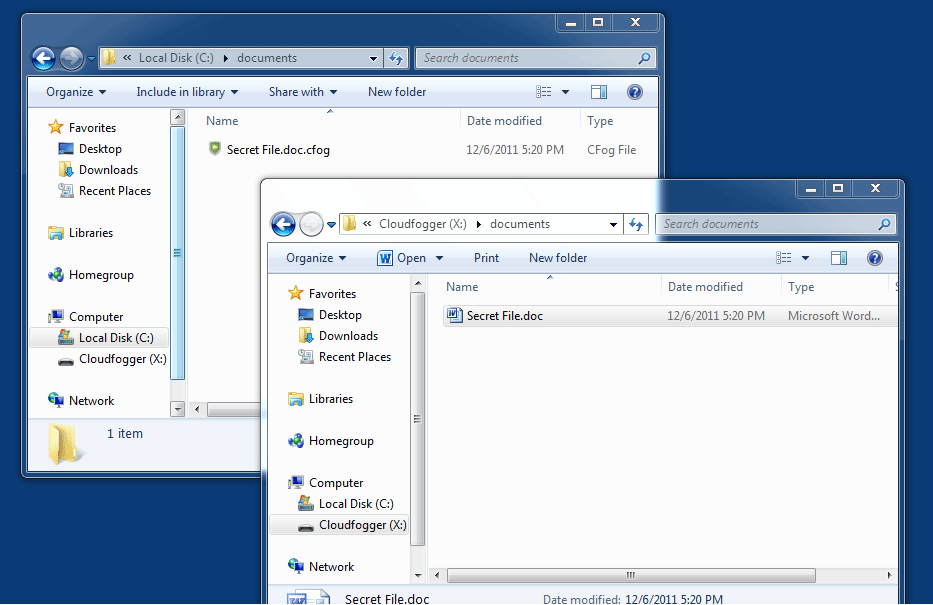
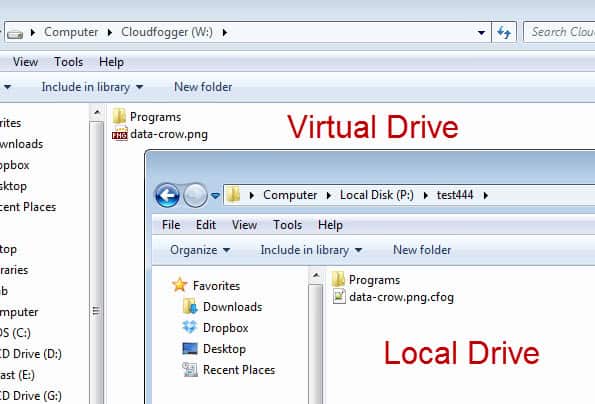
The service creates a virtual drive on the system that you can use to process files automatically. This virtual drive is linked to a physical location on the hard drive. Files stored in the physical location are encrypted, while files in the virtual drive are decrypted. The program uses AES 256bit encryption with RSA key protection for that.
You can use the program locally right away if you want to encrypt and decrypt important files on the fly. The same method works for cloud storage as well. You can for instance select a Dropbox subfolder as the physical location on the drive. This would mean that all files that you move into the folder using the virtual drive would automatically be stored in encrypted form in the cloud, and on all computer systems where the data is synchronized with.
You keep your local access to the files, keep files synchronized, and make sure that only you or users with the correct passphrase and program can do that.
CloudFogger can furthermore protect individual files stored in other locations on the computer. The program adds options to decrypt and encrypt files to the Windows Explorer context menu. These files can be loaded if the virtual drive has been unlocked on the system.
You can create a CloudFogger account during setup that enables you to share files more easily with other members of the service. Account creation is fully optional.
The program is currently available free of charge. It appears as if the developers plan to go commercial at one point in time. They do however note that users who have downloaded the free version will be able to use that version even if that happens.
Update: Make sure you read the license thoroughly, especially item 10 (thanks 40hz for pointing that out)
I’d suggest carefully reading the enclosed license that comes with t his product. Especially item 10 where you give the developer ( plus it’s subsidiaries and affiliates) your permission to gather personally identifiable information off your computer. The article goes on to state such information is not restricted to purely technical data about your system despite assurances it is solely for improving their product. Why they would require any information (other than technical data) about your system to accomplish that is anybody’s guess.

























> We will be replacing the EULA with an updated version in the next release where the old part 10 (will now be part 5) explains better what we are collecting and doing with the collected data.
> We always only used the data for statistical purposes to improve the product and its usability.
> All data was always and will be stored in anonymized, aggregated form.
Please keep in mind, that in some countries storing personal data that isn’t needet is illegal, and most parts (or often all parts) of the EULA could be ignored, like here in Germany.
So would recomment: user servers from germany. No one here is allowed to to anything with personal data.
Regarding the concern about gathering personal information that is on the computer that isn’t limited to technical information: I have nothing to prove this of course, but I noticed that the path to the folder share for my cloudfogger default path includes my profile name, which could perhaps be considered personal; and if that happens to be stored on their servers somewhere just as a shortcut or to improve user features, they might have used that language to cover themselves.
Related: How am I supposed to be sharing files with other people now? I right clicked the file and clicked “Manage Shares” and added my friends email address he used for cloudfogger as “partner”, but not sure what to do next.
Oh hey, figured it out. To share an encrypted file, make a folder in your dropbox and share it with your friend dropbox email address, then right click the file and choose “Cloudfogger > Fogg and Share” and put in your friends cloudfogger email address; then place the newly encryped .cfog file into the shared directory
more details, here:
http://imkilo.blogspot.com/2012/04/how-to-share-encrypted-files-with.html
Hello 40hz, hello Martin,
The included EULA in the latest release (v1.1.1152) is based on a standard EULA and point 10 assures us more rights than we need or use.
We will be replacing the EULA with an updated version in the next release where the old part 10 (will now be part 5) explains better what we are collecting and doing with the collected data.
We always only used the data for statistical purposes to improve the product and its usability.
All data was always and will be stored in anonymized, aggregated form.
If you got any questions, we look forward to your inquiry.
@lucky:
I’m sorry, I did not understand your question completely.
Could you please contact us via our Help desk on our website http://www.cloudfogger.com regarding your question?
Greetings,
Claudius from Cloudfogger
Does this mean that there are 2 sets of information, one encrypted and another decrypted – If so then this simply wont do to encrypt entire folders as I’d use HD spacec quick
I’d suggest carefully reading the enclosed license that comes with t his product. Especially item 10 where you give the developer ( plus it’s subsidiaries and affiliates) your permission to gather personally identifiable information off your computer. The article goes on to state such information is not restricted to purely technical data about your system despite assurances it is solely for improving their product. Why they would require any information (other than technical data) about your system to accomplish that is anybody’s guess.
Dunno. It’s sort of handing somebody a blank check in return for something “free.” Not to say this company isn’t reputable. I’m sure they are. But with a wildcard term like “affiliates” (who are left unnamed and subject to change) also being allowed access to any gathered information, I’m disinclined to install this product. (I aborted the installation BTW.) Then too, there’s always the chance this company may be acquired by someone who isn’t quite as reputable at a later date.
All I can say is caveat emptor with this one.
Good find, I add the info to the post.
Just thinking it might not be a bad idea to do an article about why it’s so important to actually read the EULA rather than just click through it. Most are pretty standard. But every so often you see something buried in one that you might not find acceptable. ;-)
I read somehwere that you would spend many days reading Eulas if you would, and that is only by assuming that users would actually understand what the eulas say. Here is the article: http://www.theatlantic.com/technology/archive/2012/03/reading-the-privacy-policies-you-encounter-in-a-year-would-take-76-work-days/253851/
It says you would be spending 76 work days a year reading Eulas.
We wrote about this three years ago: ‘Cloudy Cloud, Google Chrome and privacy in The Cloud’:
http://irdial.com/blogdial/?p=2362 Apple users are going to be in for the biggest refit and replacement operation ever seen when Apple builds encryption into iCloud. Of course, they should have started with privacy as their first priority from the beginning… Better late than never.
The auto encryption of local folders seems useful. But as a SpiderOak user the cloud aspects are superfluous as it automatically encrypts files as they are uploaded to the cloud, or local storage.
Martin,
I use
7-ZIP’s own AES 256bit encryption,
before I upload any important file “to the Cloud”.
Is that as effective,
and has the same result as your solution?
I take it you do that manually, correct? The only difference is that the encryption happens automatic with this program as long as you drag the files into the virtual drive.