NordVPN vs. ExpressVPN Comparison
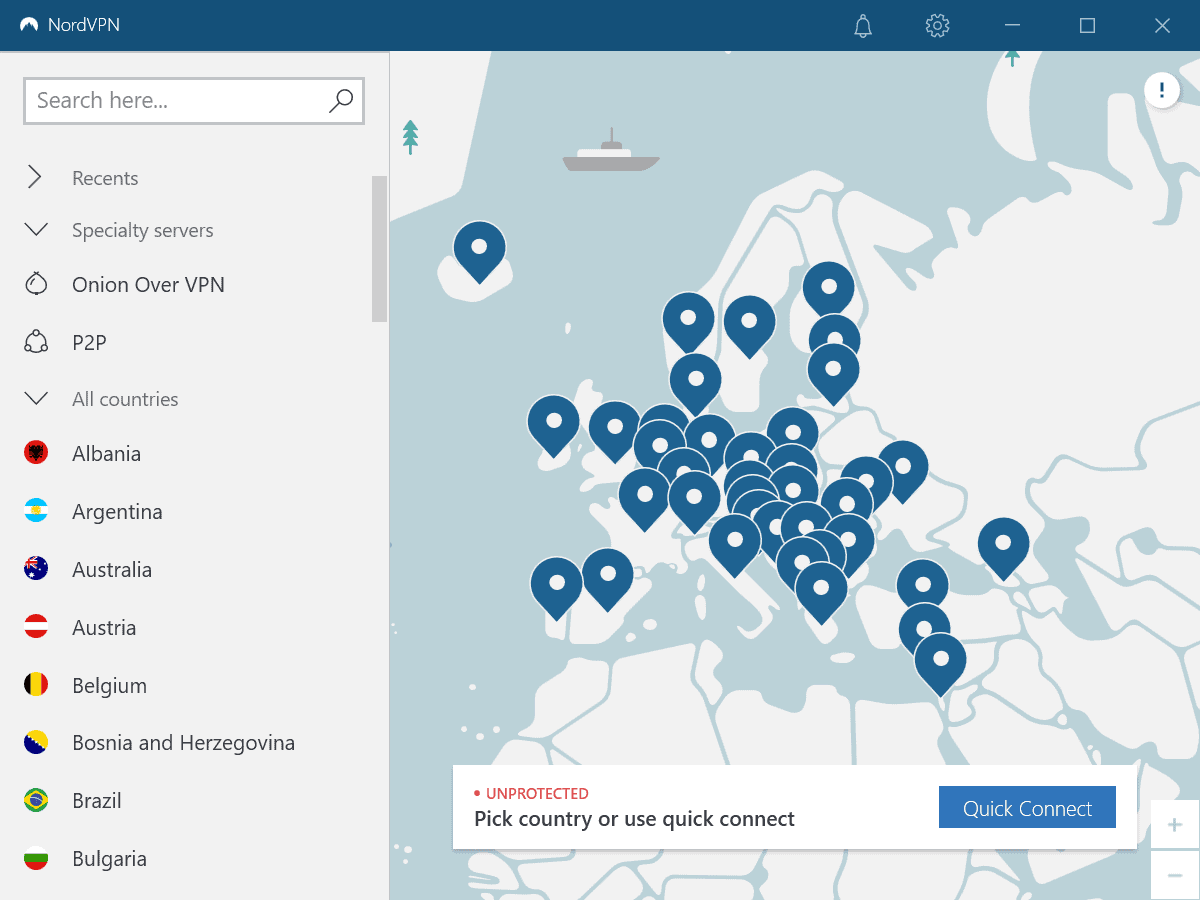
NordVPN and ExpressVPN are two popular, highly rated, VPN services. If you are looking for a new VPN service to join, you may wonder which of the two comes out at the top in general, and which may be best for you personally.
In this comparison, we will compare the two VPN services in detail to provide you with the information that you need to select the right service.
NordVPN and ExpressVPN at a glance
| NordVPN | ExpressVPN | |
|---|---|---|
| Jurisdiction | Panama | British Virgin Islands |
| Servers | More than 5300 in 59 countries | More than 3000 in 94 countries |
| VPN Apps | Windows Mac Linux Android iOS Router/other devices | Windows Mac Linux Android iOS Router/other devices |
| Protocols | NordLynx (Wireguard) OpenVPN IKEv2/Ipsec L2TP/IPsec | Lightway (custom) OpenVPN IKEv2/IPsec L2TP/IPsec |
| Logging | No | No |
| P2P/Torrents | Yes | Yes |
| Streaming (unblock) | Yes | Yes (limited) |
| Features | CyberSec P2P Servers Obfuscated Servers Tor-over-VPN Double-VPN servers Killswitch Split Tunneling | Killswitch Split Tunneling |
| Performance | Very Good | Good |
| Support | Email, chat support | Email, chat support |
| Privacy | No IP leaks No DNS leaks Killswitch works | No IP leaks No DNS leaks Killswitch works |
| Price | $11.95 per month $4.92 for 12 months ($59 per year) $3.30 per month for 24 months ($89 per year) plus 3 extra months | $12.95 per month $9.99 per month for six months ($59.95 for 6 months) $8.32 for 12 months ($99.95 per year) |
NordVPN and ExpressVPN are both highly rated and popular services, but there are lots of differences on closer inspection.
NordVPN and ExpressVPN jurisdiction
NordVPN is headquartered in Panama, which is not a member of the 14-Eyes countries.
ExpressVPN is headquartered on the British Virgin Islands, which is also not a member of the 14-Eyes countries.
Result: Tie
Server Comparison between NordVPN and ExpressVPN
NordVPN operates more than 5300 servers in 59 countries. ExpressVPN operates more than 3000 servers in 94 countries.
Here it depends on your needs; if you need access to as many countries as possible, then ExpressVPN’s offering is superior. If you just need a base set of countries, then NordVPN with its larger fleet of servers may be more appropriate, especially since it offered better performance during tests.
Result: Tie
VPN Apps supports
Both VPN services have clients for all major operating systems (Windows, Linux, Mac, iOS and Android), and support setting up the VPN on devices such as routers or Smart TVs.
NordVPN offers more features in its application, because it offers more.
Result: NordVPN
Protocols support
Both provides support the OpenVPN and Ipsec protocols. NordVPN’s main protocol is based on WireGuard while ExpressVPN has developed its own protocol Lightway.
NordVPN has the edge when it comes to server performance, and this may be partly because of WireGuard as it is adopted by other VPN services as well whereas Lightway is only used by ExpressVPN.
Result: NordVPN wins
NordVPN vs. Express VPN logging
NordVPN states on its site that it does not log user activity:
We do not store connection timestamps, session information, used bandwidth, traffic data, IP addresses, or other data. Nothing to store – nothing to share with anyone.
The claim has been verified twice through independent audits, the last one in 2020.
ExpressVPN does not log user activity either:
ExpressVPN stores no activity logs and no connection logs from our users.
No activity logs. ExpressVPN does not see or record which websites you visit. We never log the destination or contents of your traffic, and we run our own private, zero-knowledge DNS on every VPN server for added privacy and anonymity.
No connection logs. ExpressVPN never logs connection timestamps, session duration, your source IP address, or the ExpressVPN IP address that your computer assumes when connected to the VPN.
A third-party audit was performed as well and the claim was verified by the audit.
Result: Tie
Streaming and P2P: ExpressVPN vs. NordVPN
Both VPN’s support P2P traffic and the unblocking of regionally restricted content. There are differences between the two offerings though.
NordVPN supports P2P servers which are optimized for the traffic and resulted in better upload and download speeds during tests.
Both providers can be used to unblock Netflix, Amazon Prime and other streaming services, e.g. when you are abroad and want to view new series that are only available in your home region.
NordVPN may unblock more regional offers from services such as Netflix; it did better during tests and unlocked more regional Netflix offerings.
Result: NordVPN wins.
NordVPN vs. ExpressVPN features
NordVPN has the following features:
- CyberSec – protects against known malicious sites and advertising by blocking these outright when enabled.
- Killswitch – blocks Internet traffic if the VPN connection drops.
- Split Tunneling – Use some apps with a VPN connection and others without.
- P2P servers – special servers optimized for torrent traffic.
- Obfuscated servers – designed to access the VPN service in countries that make VPN use difficult, e.g. China.
- Double-VPN servers – option to chain the connection so that it is routed through two VPN servers instead of just one.
- Tor-over-VPN – option to access Tor .onion sites using the VPN.
ExpressVPN’s feature set is limited in comparison. It features a killswitch, similar to the one offered by NordVPN, and Split Tunneling support.
Result: NordVPN wins.
NordVPN vs. ExpressVPN performance
The performance of NordVPN was slightly better during tests. Granted, the Internet connection of the test system was only 50/20 Mbits, and both came close to maxing these out on most servers that we tested.
NordVPN scored slightly better in the benchmark tests.
Result: NordVPN is the winner.
NordVPN vs. ExpressVPN price comparison
Both VPN services list three plans on their sites. ExpressVPN customers may subscribe for 1 month, 6 months or 12 months, and pay $12.95, $9.99 and $8.32 respectively for the subscriptions.
NordVPN customers may subscribe for 1 month, 12 months or 24 months, and pay $11.95, $4.92 or $3.30 for the subscription. Three extra months are added to the 2-year plan free of charge.
Result: NordVPN is the clear winner.
Conclusion of NordVPN vs. ExpressVPN
NordVPN is the clear winner of the comparison, as it beats ExpressVPN in most categories. It is a lot cheaper if you subscribe at least for 12-months, offers better server performance and speeds, and has more features than ExpressVPN.
ExpressVPN is not a bad service, far from it, but it does not offer as much value for the money than NordVPN does.





















Martin does doh hide from service providers ?
It encrypts DNS lookups. If you want to make sure your ISP gets minimal information, you may want to use a VPN.
The comment section below any vpn-related article feels a lot like a battlefield between several users each one trying to prove his vpn provider is better than the others. I tried many VPNs and been using nordvpn for around 2 years now, mainly to watch US streaming services and Formula races from Austria and I’m happy with it, the downloading speed was decent and customer support were very helpful but ExpressVPN is also a good option and I in my opinion the best compassion after all is the one made by the user himself, both providers offer free trial so simply use that and you decide which one is best for your needs.
WOW,
After all that reading, I did not see BBC iplayer mentioned anywhere. So which one out of either can access the iplayer?
https://www.expressvpn.com/vpn-service/bbc-iplayer-vpn
1. VPN apps supports: NordVPN as the winner?
and the reason is “NordVPN offers more features in its application, because it offers more”
Clearly, the Header says “VPN apps Supports” not “features”
It should have been a tie.
2. Protocol Support: It should have been a tie again. Just because Wireguard is adopted by other VPN services doesn’t mean NordVPN wins. We are comparing the different protocols used. Just like NordVPN uses Wireguard, ExpressVPN uses lightway and ExpressVPN also says that they will opensource the protocol soon. It should either be a tie, or ExpressVPN should have won. Both are extremely light weight and has less lines of code.
It should have been a tie.
3. Streaming and P2P – NordVPN wins?
NO. In fact, the reason given is “NordVPN may unblock more regional offers from services such as Netflix; it did better during tests and unlocked more regional Netflix offerings.” I use NordVPN currently and it works well with most streaming services. I used ExpressVPN before and it was the same. Absolutely no issues. US, UK Netflix worked anytime any given day. Sometimes both gives some issues and all we need to do was change the server.
And as far as P2P is concerened, ExpressVPN clearly wins. It provides P2P servers for every single country. NordVPN doesn’t. ExpressVPN is clearly very easy to use. Just connect to any country and use P2P based apps – (torrent apps) if required. NordVPN has only selected servers across the map that provide P2P.
It should have either been a tie or ExpressVPN wins.
4. Features – ExpressVPN feature set is almost the same as NordVPN’s.
CyberSec – ExpressVPN provides something similar – something that has to do with browser extension that uses HTTPS only mode.(Not sure. I forgot.)
Also, it uses a speed test inside the app to give the ping, download and upload speed of each country servers. Unlike NordVPN which only gives “Connect to fastest server” which actually connects to the nearest server which is pointless. If i want to hide my location for example, why would I choose fastest server which would always be another server from my own country.
P2P servers is mentioned for NordVPN but not for ExpressVPN? Ha ha… Every single server they provide is P2P optimized.
Obfuscated server mentione for NordVPN but not for ExpressVPN? Yes! ExpressVPN doesn’t have servers in china, but the VPN itself works flawlessly in china. CHeck their FAQ’s and blogs for more details.
DoubleVPN and TOR-Over VPN are the only features that are missing in ExpressVPN but they are sometimes overkill for a casual user. Instead the speed test is an excellent option to add in a VPN.
5. Perrfomrance – Again depends on the country you reside and the country you connect to. SOme countries do not have GIgabit servers. Even for NordVPN those countries had extremely slow speeds. Obviously if you connect to USA servers, UK servers or Sydney servers. They are going to be extremely fast. but for the sake of Ping, latency, download and upload performances, we have to accept the result the editor has given. especially from where he has connected.
6. Price – Agreed. NordVPN wins.
But, this was written without any research at all. I have used both the VPN’s extensively to comment a lot more. But, these were my immediate thoughts on the lazy, unresearched writing.
Hello,
for the author of the article; you should add the number of how many devices can be connected to the 2 VPN’s simultaneously. This is of importance if you are not alone in our household and have several units.
Regards, Pascal
Thanks for the suggestion. This is a work in progress, and we are always grateful for tips that improve the quality of the review.
People in this comments section are doing way too much unneeded research. A basic “Easy Mode” uBlock Origin setup blocks googletagmanager on ExpressVPN’s website. For NordVPN, it’s googletagmanager and google-analytics. That alone would tell me all I need to know about these “privacy protecting” companies and save me the trouble.
Use Nord vpn now but not impressed and will definitely change next time. Why. 1. Nord will drop the connection if not used for a few hours leaving your IP exposed! Sure there’s a kill switch but you have to turn it off if you don’t want to use vpn. 2. Doesn’t work well with Google they know it’s a vpn and ask for Capacha checks when using search and Gmail stops working. 3 Lots of other websites know your using vpn and constantly ask verification. 4. I used another cheaper vpn
service before which was much better and faster it’s been over rated don’t believe any reviews that don’t pick up any faults they are most likely paid Nord pay big commission.
Sorry to be a negative nanny, but there are most definitely some caveats with NordVPN.
NordVPN has massive DNS Leaks! I spent weeks testing this.
If one configures any/all network interfaces to use Nord’s DNS servers your DNS queries can hit as many as 63 different servers, none of them under NordVPNs control. One particularly worrisome target is datacamp, a data analytics company in Singapore. I wish I could upload images here, I can show the leaks as detected from 3 different leak test sites. There are two ways to fix it. 1. Use the OpenVPN block-outside-dns directive. However, this breaks intranet DNS queries as well as a couple of other issues. Nord have no idea about what block-outside-dns is and how it works. The other option is don’t use Nord’s DNS servers. This issue present whether you configure the DNS servers on your router or on your PC.
Nord weren’t really all that interested, or knowledgeable in helping me resolve this so I was left with option 2.
Secondly, Several of the “features” of Nord are not available in all countries. For example, where I am Obfuscated Servers, Double VPN, and Split Tunneling are not available.
NordVPNs IP addresses cannot be used in my country for streaming services. They are all blocked. They are blocked also by PayPal, eBay and many retail and tech websites.
You should never use L2TP. It was compromised years ago (I believe Ed Snowden disclosed some issues with it too). IKE is also risky and has it’s own issues. I might be able to dig out some notes from discussions I had with Nord on this subject if anyone is interested.
The other thing you have to watch out for is that Nord only supports 2 ports. 1194 for UDP and 443 for TCP. IIRC, PIA supports 8. When ISPs start getting ordered by courts to block 1194 things are going to be tough while Nord scrambles to try and get its services operational on other ports. Sadly, where I am TCP results in a drop from 100Mbps to as low as 5Mbps.
NordVPN hacked https://techcrunch.com/2019/10/21/nordvpn-confirms-it-was-hacked/
I had Nord for half a day. Probably set a record for uninstall speed. Bought a month subscription, requested a refund the same day I installed the service and spent days answering inane questions about why I wanted to leave. Finally told them they have all the info they need, won’t get more and send a refund. They did, a good thing about Nord. The spam afterward was not a good thing.
The service was OK, I suppose. It worked but their client was really silly, not much ability to do what I wanted and it was full of upsell junk. OK for newbies, for a while. A good VPN gives you a secure tunnel, easy to use choice of servers and disappears.
All their stupid ads with deal countdown timers, native advertising “review” sites, the hype about speed, comparisons with Express (huh? what? who does that?), trillions of servers, kinda are the opposite of how a reputable VPN should act.
Both using shady marketing tactics and lie about what a VPN can do and can’t. I would stay as far as possible away from them two. There are really not much good, trustworthly providers like IVPN, Mullvad, Airvpn and some other small ones. IVPN has some great blog posts about other, shady VPNs.
Btw about the marketing and other things: https://www.ivpn.net/blog/why-we-refuse-modern-marketing/
People need to start using honest providers, not these big shady ones.
The last one in the chart comparison has 27 months for 89 per year when its $89 total based on the 3.30 per month number.
NordVpn doesn’t work in my country what so ever since we have very high online access restriction but ExpressVPN works flawlessly sure its more expensive than other VPN providers but its hands down the best and only option for me.
Please tell what country you are in, otherwise your feedback is worth nothing for other readers.
I am in KSA
Do with Mullvad, AirVPN.
Two of the best. Have both currently.
I will second that.
Same test with ProtonVPN now ;)
Sad to see that the comparision is clearly biased probably due to paid promotion as I have used both and there are some differences in tests perfomance and results.
Both have a 30-day money-back guarantee policy, I would recommend to try both and then decide yourself which one fits you most for your usage.
Even I felt that it could have been a paid promotion. But, like Martin said, every experience is different. Although I have given a pretty good comparison. I have used both VPN’s extensively. Check out my comment too. Its under the name – Mithesh
This is not a paid promotion. Your experience may differ, and I’d encourage everyone to try both services if they have the means to do so, to see which one is better for them.
You failed to address one key issue in comparing the 2 VPNs. When connecting from restricted countries (ie. China), ExpressVpn is clearly superior. NordVpN offers servers in only 1 country (Japan) and the connection is very unstable and very difficult to connect to most of the time. On the other hand, ExpressVPN offers connections to many servers in many countries without issues. If you plan on using a VPN to connect from a restricted country, then ExpressVPN is the much better product and don’t waste your time with NordVPN.
@Mitch
“…and don’t waste your time with NordVPN”
very construction feedback, would you like to expand a tiny bit on the issue?
*constructive
I can’t test this. Comments are a great way of adding content to articles. Thank you for that. Did you try NordVPN’s obfuscated servers? They are designed to allow you to connect to VPNs in countries such as China.
The real title should be: “NordVPN vs. ExpressVPN – which company pump more money into fake reviews to gain more users”.
Nord is trash, they’ve been hacked so obviously their operational security is garbage but hey go ahead and trust your security to a company that can’t even take care of its own security.
And second and more importantly, Nord is owned by a parent company that is a data aggregation company. Ie they collect and sell data on people. Sure sure I’m sure Nord takes your anonymity seriously when it’s owner makes money off of selling data. Any reviewer who picks Nord hasn’t done their research and isn’t to be trust. You can Google either of my claims there are many articles on them.
Express, neither of those problems. Sure it costs more, security usually does especially when the company doesn’t sell your data.
One owner.
I’d pick TOR over any VPN provider. There is no way to tell who truly is behing these companies, most likely government funded.
ghacks.net not responding, so my comment may appear twice. it’s been an ongoimg situation here over the past couple of weeks or so.
Don’t use Tor unless you need to, some people depend on it for very serious reasons. Leave them their bandwidth. Tor is fairly awful for everyday browsing anyway. Slooooowwwwww and a huge number of sites load poorly.
VPN’s don’t give anonymity, meaning the service knows who’s entering it. No reputable VPN would ever claim anonymity, and won’t. I sometimes use VPN’s to reduce hounding by Googleplex, et al. Keeps your IPS’s ads out of your hair, too.
Tor is what it is, nodes can be monitored same as any place else online. Truly nasty actors with some brains couldn’t be bothered with Tor for truly nasty acts. Some of the bad guys who get caught do amazingly dumb stuff such as making deals with their VPN off by mistake. Or using just Tor. Or selling (fill in the blank illegal) over a phone. Or not verifying customers. Or using Chrome. Oops.
Simple privacy measures involve getting lost in the crowd, a balancing act between letting ad companies id you and letting your protections out you. Getting it right’s a trick.
“Don’t use Tor unless you need to, some people depend on it for very serious reasons. Leave them their bandwidth.”
That’s actually true and what I do to the point I don’t use Tor much even in desktop. There’s no point in being anonymous when all you need to do is stream live sports match or watch a YouTube video.
@Yuliya:
I tend to agree. For example, from previous research I discovered that NordVPN is a uniquely Panamanian type of corporation whose ownership is not registered but by anonymous bearer shares. I once joked that half the shares are probably in the top desk drawer of the director of NSA and the other half in the top desk drawer of the director of GCHQ. And sporadic voluntary audits don’t impress me, especially if they’re done by a major corporate auditing and consulting firm. The Big Four’s true colors were revealed when the derivatives bubble popped in 2007. For actual anonymity, it seems safer to rely on technical difficulty (Tor) rather than human promises (VPNs) … and even so, I’ve even seen (unsubstantiated) allegations that Tor has been a “known honeypot for years.”
On the other hand, with a good VPN, you’ll get much faster and more consistent throughput, you can choose the country you want to appear to be operating from, you can use most pay streaming services, and (from what I hear) you won’t face as many CAPTCHA challenges. If you’re not a major intelligence or law-enforcement target but just someone who doesn’t like being tracked by every major player on the Net, VPNs seem to have valid uses. I just wouldn’t necessarily rely on them for bullet-proof anonymity.
PS: NSA reportedly flags everyone who simply *uses* Tor, or even just *reads* about it. I assume they do the same for VPNs and private messenger apps. Do you ever feel like when you’re on the Net you’re just a monkey on exhibit at the zoo, and that attempting to secure some small measure of privacy for yourself just gets you a more exclusive set of visitors?
@Peterc
If you are curious about the (likely) ownership of NordVPN… They have a strong link with Tesonet, which is a data mining company:
https://www.vpncompare.co.uk/nordvpn-security-audit-data-mining-allegations/
https://news.ycombinator.com/item?id=18609655 (this also exposes the Proton Technologies AG, developer of both ProtonMail and ProtonVPN)
There are rumors that ProtonMail was developed under CIA supervision:
https://privacy-watchdog.io/protonmails-creation-with-cia-nsa/
As for ExpressVPN: British Virgin Islands my ass, they are actually based in Hong Kong:
https://www.youtube.com/watch?v=yW_zBGXfiPg
Ownership of ExpressVPN is also a mystery, nobody knows who is behind it:
https://www.quora.com/Who-owns-Express-VPN
Not saying that all of this is accurate, it is hard to gather concrete evidence when these companies are actively trying to hide their ownership from the public. But if it smells fishy, I wouldn’t rely on it for privacy purposes. One can use those VPNs to circumvent geoblocking, but that’s pretty much it.
I wouldn’t rule out that these companies are either state-run or owned by private companies who are making a fortune with selling user data.
I think the VPN section of privacytools.io uses sound criteria, and only few VPNs live up to them (however, among them is ProtonVPN, of whom I am wary personally):
https://privacytools.io/providers/vpn/
The thing is, you ultimately don’t know if the providers really don’t log. Even if their client-side applications are open source, you still can’t look at the code that they are running on their servers. Even if they published the server-side code, you STILL wouldn’t know whether or not this is the ACTUAL code they are running on their servers. Audits can help, but might be biased or outright false if there is a monetary or professional relationship between the company conducting the audit and the client company.
As for Tor: Publicly, they state that the network is “trustless”, but this is not completely true. The speedy Tor servers are expensive and don’t pay for themselves, so I do have to wonder wonder who sponsors them. I am sure such servers aren’t maintained by private citizens. I wouldn’t be surprised if a large amount of nodes are actually state-run. It doesn’t help that the Tor network prioritizes fast connections internally, so you will always use the powerful (likely not privately owned) servers.
I also hear arguments that Tor is supposedly safe because there are multiple hops, but this is not accurate. If you control the incoming and outgoing node, you can correlate the latency via a timing attack, so you can de-anonymize people even if you are not in control of the middle node. You can save some expenses by only controlling the incloming and outgoing nodes, let the middle nodes be run by whomever (private citizen, private organization) and let them bolster an otherwise state-run network.
Insightful article re. Tor:
https://yashalevine.com/articles/tor-spooks
@Iron Heart
Aha! so now latest companies on your radar are VPNs and Email providers. In the first link you provided, well say what you want about NordVPN, just saying maybe not consider a guy’s thoughts when he himself is saying – Innocent until proven guilty. And the same for ExpressVPN, when guy who’s saying ExpressVPN is based in Hong Kong has a YouTube channel of mainly VPNs, then I know whether he should be taken seriously or not, to me it seems clickbait type.
About ProtonMail and ProtonVPN well that made me chuckle. For your kind information Proton has done enough to provide folks around the world access to Uncensored internet – yeah the thing where all opinion are analysed by a little bit of common sense, though that is not happening right now. First link you shared – even ProtonMail team responded and for second, well https://www.reddit.com/r/ProtonMail/comments/d58cq1/protonmail_questions_and_concerns/ in this thread one guy said some nice words – Who would you trust? A company started by MIT graduates who have previously worked at CERN with Ph. D’s and have started a company at Switzerland that has been audited by the EU and Mozilla, or a nobody blogger with a self-signed certificate? Of course that reminded me of madainwhatever guy. Trying to become a journalist and conspiracy theorist without providing any meaningful facts.
Also there has been birth of a new species in internet world where one guy has to completely shill one product and hate another one, like Privacy Watch Dog guy where he has to shill Tutanota and hate ProtonMail, though in reality both services are very good. He’s a joke guy trying to become popular by being a conspiracy theorist when he can’t provide a meaningful fact for real, and on purpose trying to discredit one damn good service in favour of another damn good service when he himself is probably using Gmail.
Again say what you want about Nord and ExpressVPN but since this is a public forum, use some common sense first about questioning other services like ProtonMail and ProtonVPN.
“The thing is, you ultimately don’t know if the providers really don’t log. Even if their client-side applications are open source, you still can’t look at the code that they are running on their servers. Even if they published the server-side code, you STILL wouldn’t know whether or not this is the ACTUAL code they are running on their servers. Audits can help, but might be biased or outright false if there is a monetary or professional relationship between the company conducting the audit and the client company.”
I don’t know what to make of this other than maybe laugh.
“As for Tor: Publicly, they state that the network is “trustless”, but this is not completely true. The speedy Tor servers are expensive and don’t pay for themselves, so I do have to wonder wonder who sponsors them. I am sure such servers aren’t maintained by private citizens. I wouldn’t be surprised if a large amount of nodes are actually state-run. It doesn’t help that the Tor network prioritizes fast connections internally, so you will always use the powerful (likely not privately owned) servers.
I also hear arguments that Tor is supposedly safe because there are multiple hops, but this is not accurate. If you control the incoming and outgoing node, you can correlate the latency via a timing attack, so you can de-anonymize people even if you are not in control of the middle node. You can save some expenses by only controlling the incloming and outgoing nodes, let the middle nodes be run by whomever (private citizen, private organization) and let them bolster an otherwise state-run network.
Insightful article re. Tor:
https://yashalevine.com/articles/tor-spooks”
There’s very simple way to settle all this, its called IMPROVING USER PRIVACY 101. FIRST STEP IS TO FOLLOW MADAINWHATEVER’S WORD AND USE LATEST UP TO DATE IPHONE to protect yourself from Pegasus, afterall who knows what happens when a service is open source, and then take it one step at a time ;-)
@Yash
Naive fool.
“When people start with name calling, they show they have nothing intelligent to say, so they they try to get the frustrating anger away with a personal attack. Thank you for proving the thesis.
@Iron Heart
Atleast you didn’t lied this time by mentioning other stupid baseless things, so good for you.
@Yash
You didn’t disprove any of my claims, you are just fighting back with pointless ad hominem attacks. You are a naive, petulant fool of the worst kind who believes any kind of info these companies feed you, and you are way too lazy to do any kind of research, and kind of digging yourself. This is nothing but tiresome at this point, and as far as your comments are concerned, a waste of space.
– The NordVPN hack was all over the mainstream tech news, and you can find their connection to Tesonet as well on mainstream tech news if you search for it.
– Same for the fact that ExpressVPN’s ownership is unknown. I challenge you to find out the owner (names of persons) of the company, good luck.
– You seem to be very impressed by the academic merits of the ProtonMail developers. Fine, what does that prove? This only proves a certain degree of learning, but says nothing about their trustworthiness as a business. If there is talk about them running their business in ways contrary to what was officially promised, their degrees are not enough to warrant my or anyone else’s trust, as these things are not related. Mozilla and EU (For a company registered in Switzerland!?) audits? Where? Also, these are the very entities I would trust with an audit for any privacy service, I know they have my best interests at heart. /s
– Contrary to you, I don’t dismiss the things some blogger has to say, just because it doesn’t fit into a narrow-minded, preconceived world view or choice. I don’t just dismiss it outright, because I am not a narrow-minded idiot. I take such accusations seriously and want to find out the truth.
– Were you ever in control of the servers of your VPN provider? Were you ever able to verify that they don’t actually log? Answer: You were not, so it ultimately comes down to trust, doesn’t it? You choose to trust Tesonet (who are in the data mining business, so great choice! /s), but that doesn’t mean I have to.
– The things you say about madaidan, a respected developer of the Whonix project, are absolutely retarded and are a gross misrepresentation of the information he provides. The security of the iPhone was analyzed by him, it was NOT declared a privacy solution, although it is de facto more private than most Android stock ROMs (and less private than most custom ROMs). madaidan also never said that any device was faultless (How is that even possible, looking at the complexity of today’s operating systems, you absolute moron?) or that the iPhone, or any other phone for that matter, is a defense against Pegasus, especially prior to any related software fix (Dafuq?).
I am tired of having to answer to your terribly moronic, unnecessary ad hominem replies. I am also tired of your insolence, calling me a liar without providing any kind of evidence that I lied anywhere, while you yourself provide absolutely zero useful information to others who might be looking for assistance and guidance here. I am just tired of it, and so are others. Give it a rest.
@Iron Heart
“You didn’t disprove any of my claims, you are just fighting back with pointless ad hominem attacks. You are a naive, petulant fool of the worst kind who believes any kind of info these companies feed you, and you are way too lazy to do any kind of research, and kind of digging yourself. This is nothing but tiresome at this point, and as far as your comments are concerned, a waste of space.”
Say that while looking in the mirror or better while reading your own comments, you’ll feel better.
Plus dude when you’re trying to be a conspiracy theorist you have to provide some proofs to turn someone’s head. That’s called HOW TO HAVE A CONVERSATION 101.
“– The NordVPN hack was all over the mainstream tech news, and you can find their connection to Tesonet as well on mainstream tech news if you search for it.
– Same for the fact that ExpressVPN’s ownership is unknown. I challenge you to find out the owner (names of persons) of the company, good luck.”
Like I said before, say what you want about them products, but the first thing you’ll learn when visiting IMPROVING USER PRIVACY 101 is most of the VPN owners are unknown. Few VPN owners were known but then authorities sent them a legal letter. Of course use your uncensored internet for that.
Plus you don’t get it, Nord being based in Panama has nothing to do with most employees based in US or other country, coz main point is legal troubles are avoided.
As for NordVPN hack, it is true but that happened more than two years ago. Since then they have done an audit and have switched their servers into RAM disk mode. And that is more important. Of course use your uncensored internet for that ©
I see you’ve mentioned ProtonMail and madainwhatever guy. See if it comes down to whether to trust a respected organisation with a good track record in user privacy which by the way is still going strong or a blogger who uses WordPress for his websites, I know what I’m doing and most of the internet users know as well. Privacy Watch Dog guy never proved anything other than doing pointless ranting which reminds of you.
For madainwhatever guy, he works on Whonix, good for him. But suggesting users to use iPhone over many things is plain stupidity along with other stupid things. Thankfully his bubble has already been bursted and about time too, I must say.
Plus iPhones, even the latest updated ones, were the worst offender in dealing with Pegasus and they’re even affected now, so what the hell are you trying to say when mentioning software related fix?
“– Contrary to you, I don’t dismiss the things some blogger has to say, just because it doesn’t fit into a narrow-minded, preconceived world view or choice. I don’t just dismiss it outright, because I am not a narrow-minded idiot. I take such accusations seriously and want to find out the truth.”
Dude being a conspiracy theorist is not a bad thing, but atleast use some common sense. I guess an encounter with Roy Keane would do just fine as he’ll teach some manners of not questioning some folks without any proof or meaningful FACTS. He’ll dismiss your stupid theories by saying – its all nonsense which it essentially is.
“I am tired of having to answer to your terribly moronic, unnecessary ad hominem replies. I am also tired of your insolence, calling me a liar without providing any kind of evidence that I lied anywhere, while you yourself provide absolutely zero useful information to others who might be looking for assistance and guidance here. I am just tired of it, and so are others. Give it a rest.”
Only if you had spare time for reading your recent comments again, then you would’ve seen how many times you’ve lied or contradicted yourself on topics like Adblockers, Manifest V3, Browser Fingerprinting, Linux, Windows, Brave Device name hide info and some metrics, and so on in literally every second paragraph.
Stop trying to be “I know it all dude” atleast use some real world examples to explain something than trying to be a conspiracy theorist all the time.
@Yash
You are STILL coming up with new BS replies, just wow. Way to go, waste my time and everyone else’s some more with NONSENSE.
> Plus dude when you’re trying to be a conspiracy theorist
Do you think bringing up the conspiracy theorist meme in a manner that is as painfully obvious as it is retarded, will fix anything? Read my sources, there are more than “whispers in the dark” re. NordVPN’s real owner, and the relationship of said real owner with the Proton Technologies AG. All of that can be researched by you, but you are sadly too dumb and too lazy for that. I say “sadly” because this comment section, all of us, would profit from you doing your research. Throwing around the “conspiracy theorist” moniker because you can’t admit that you have probably been fooled (pride issue, I know) is the path of least resistance, so you go for it. The problem is, you are not only deceiving yourself, you are also potentially deceiving others, and I won’t allow this to happen.
> HOW TO HAVE A CONVERSATION 101.
How is throwing ad hominems at other people a conversation? That’s just a sad substitute for an actual argument, nothing more. What you call a “conversation” is just plain nonsense on your part that is ultimately not helpful and might even be harmful.
> most of the VPN owners are unknown
There is no reason for them to hide if they have honest intentions. If they are not legally required to maintain records of user activity in their country, they can’t be coerced by the state to do so. They can reveal their name if they are true to their word regarding not keeping logs, if their applicable jurisdiction permits it. Hiding the ownership is a sign of malicious intent.
Take Mullvad for example, its owners are publicly known. They don’t have to keep records of user activity in Sweden as they are not an ISP. If the police comes knocking on their door, there is no reason for them to hide in order to keep their promise of not logging. They can just point to the applicable law.
> your uncensored internet
You seem to have a problem with a lack of censorship, am I reading that correctly? If so, you are a moron. Free exchange of ideas can only happen when conversation is not stifled.
Plus, the Internet in 2021 can hardly be considered “uncensored”. It seems you haven’t been paying attention.
> Nord being based in Panama has nothing to do with most employees based in US or other country, coz main point is legal troubles are avoided.
As I said above, they don’t have to hide their ownership provided that the legal framework they operate in doesn’t require them to keep logs. If someone comes knocking on their door, the owners can state with boldness that they don’t have to keep any record of user activity.
Their ownership being hidden likely has something to do with them being owned by a data mining company, and this fact being widely known would end their business. People who are not naive fools easily come to this conclusion once the only other reason to hide ownership (potential legal pressure on the company) is ruled it, and in this case it is ruled out.
> As for NordVPN hack, it is true but that happened more than two years ago.
People who might want to sign up for this paid service of that data mining company should be made aware of the fact that they were not even able to maintain sound operational security for an unspecified amount of time, and were lying to their users about the hack that has transpired until it was found out in other ways. If you think that potential customers shouldn’t know this, you are simply a fool and / or malicious.
> a respected organisation with a good track record in user privacy
In my book, this “good track record” just means that nothing of their potentially nefarious activities has been widely leaked so far. I distrust the Proton Technologies AG mainly due to their relationship with Tesonet (and yes, there is more than “whispers in the dark coNspIrAcy thEOriEs” about that, you just have to have an open mind).
> Privacy Watch Dog guy never proved anything other than doing pointless ranting which reminds of you.
Cool. Ultimately, you have to trust their statements, as you are not in control of the servers – you don’t really know what is going on. If there are hints at a potential relationship with a data mining company, I won’t enter into a business relationship with them. Period. Why? Because there are enough competitors who have no problem with revealing their ownership and who have not been tainted by such an accusation.
Seriously, you are entering into a business relationship that ultimately requires blind trust (you are not in control of their servers, you don’t know what is going on), and you are willing to do so despite the strong hints at a Tesonet involvement? Hahaha, I call this folly. This is extremely retarded.
And if you disqualify certain accusations just because they are ostensibly coming from a nobody with some blog vs. people with an MIT degree, you are just showing yourself for the narrow-minded idiot that you are. Why shouldn’t these people get exposed by a “nobody”? It has happened before, and will happen again. You are only looking at the outside form and not at the arguments presented, it’s called being superficial an stupid.
See, I know from prior exchanges that you are a ProtonVPN customer and that you try to justify your choices, I also know that your replies are fueled by personal animosity, but ultimately you have to understand: I don’t give a shit. All I care about is providing valuable tips and shielding people from malicious intentions, and from ignorants like you.
> But suggesting users to use iPhone over many things is plain stupidity along with other stupid things.
Why? Apple has made several sound security decisions in iOS. And this is what madaidan has analyzed, security.
> Thankfully his bubble has already been bursted and about time too, I must say.
Another fact you will never ever grasp: One security issue doesn’t invalidate an entire OS. This only means that a certain component was attackable and needed fixing. Nothing more, nothing less. Today’s operating systems are complex and can be attacked from many different angles, if one such angle has worked for the attacker, it doesn’t mean that every other component of the OS is suddenly insecure now.
> Plus iPhones, even the latest updated ones, were the worst offender in dealing with Pegasus and they’re even affected now, so what the hell are you trying to say when mentioning software related fix?
How about you inform yourself?
https://www.iphonehacks.com/2021/07/ios-14-7-1-patches-zero-day-exploit-used-nso-pegasus-spyware.html
> Dude being a conspiracy theorist is not a bad thing, but atleast use some common sense.
LOL, I am not using common sense? I have used plenty common sense above when I explained to you why there is no reason for the NordVPN or ExpressVPN owners to hide from public, you just don’t accept the only other possible explanation, as you sadly are a narrow-minded fool. Just saying it as it is.
Also, you can easily find out about these things in mainstream tech media, are these people “conspiracy theorists” as well? Yeah, I thought so. Jeez… wow.
> He’ll dismiss your stupid theories by saying – its all nonsense which it essentially is.
That’s not even a rebuttal. It’s bullshit.
> Only if you had spare time for reading your recent comments again, then you would’ve seen how many times you’ve lied or contradicted yourself on topics like Adblockers, Manifest V3, Browser Fingerprinting, Linux, Windows, Brave Device name hide info and some metrics, and so on in literally every second paragraph.
I don’t think so. Your lack of understanding, lack of willingness to learn, your laziness when it comes to doing your own research, your inability to admit when you were wrong is NOT the same as me lying / contradicting myself. Your own ignorance, and inability to understand basic concepts, is a very big problem here and in every conversation I had with you so far. Show me where I have supposedly “contradicted myself” here on gHacks, give me some real life example… I will then proceed to show you that what you maliciously call for a lie, either deliberately to taint my reputation or because of your own lack of understanding, is most likely not a contradiction in fact. I am not aware of me having contradicted myself here.
> Stop trying to be “I know it all dude” atleast use some real world examples to explain something than trying to be a conspiracy theorist all the time.
More “conspiracy theorist” blah blah, born out of laziness, lack of understanding, and an inability to admit that you were wrong. How creative of you. *Yawn*
@Iron Heart
Why on earth are you even replying when first you’re not addressing any points mentioned? Coz one line copy paste is not really the solution.
Again I’m adding, say what you want about Nord or Express, but atleast mention some credible sources to back that up. And a random guy with pointless ranting in Privacy Watch Dog or a YouTube guy with VPNs in all his videos with most of them clickbait type is not the answer.
I don’t use Nord and I really don’t care about it but if you’re throwing mud at someone, atleast do it for right reasons. Since the Nord Hack, the company has changed everything and have done an audit. Let that sink in.
As for latest Proton trashing, I don’t a give a damn about what you have to say. Thankfully Privacy Watch Dog is also now in that list too. The only reason I’m replying is coz this is a public forum and not some everything is bad trash talk show hosted by Iron Heart. If you’re saying something atleast back it up with credible sources, otherwise shut the damn mouth or keyboard in this case.
Madainwhatever guy – he is nonsense, that’s it, same as iPhone security. I like the link you provided. Next time if I want to clear something about iPhones, I’ll visit transparent iPhone Hacks for everything Apple.
Proton is a good company with good products, the same as Tutanota, same as many others. That doesn’t mean trashing of Proton in favour of Tutanota is acceptable by some random internet guy who can’t provide any evidence for real.
As for “contradicted myself show me real world examples” visit ghacks.net this time on your uncensored internet and click all in the homepage. Then visit Brave latest article, read your own comment, now breathe.
Then visit Ideas.mozilla.org article and again visit your last comment, bingo! you’ve found your contradictions.
I actually in a previous article provided some quotes of you contradicting in multiple comments in same thread. Of course I can mention that article next time or better I’ll copy paste some quotes directly than doing things in an indirect way this time. But beware coz you may not like it.
@Yash
Laughable. You are still replying. With no arguments.
So, what you are basically saying is:
You don’t care about someone’s arguments because of the outside form, the manner of presentation. I have already explained why this is just superficial and retarded. No need to further comment on this.
You say that NordVPN or ProtonVPN etc. provide a good service (I assume you mean stable connections, a good UI etc.). My reply to this is: It doesn’t matter. Other services provide this as well and have none of the shady business connections of NordVPN or ProtonVPN, they also don’t hide their owners unlike NordVPN, ExpressVPN etc. Since it ultimately comes down to blind trust, as you don’t know what is really happening on the VPN servers, why should anyone run a risk when there are other capable services? Please explain that.
Sorry, but if you trust either NordVPN or ProtonVPN, you are frankly an idiot:
https://airvpn.org/forums/topic/28876-why-you-can%E2%80%99t-trust-nordvpn/
Read the reply from “staff”, explain those weird connections between the companies to me in a way in which ProtonVPN ends up not being connected to Tesonet. Good luck.
Also, stop bashing madaidan. He is a respected developer with years of experience in the field, while you are, frankly, a clueless idiot. There is no comparison between the two of you. Show some respect and move on, especially when you don’t have any kind of counter-argument to what madaidan actually says, having to resort to embarrassing ad hominem attacks as a substitute.
Last but not least, I have no problem with you posting supposed “contradictions” and “lies” you are apparently seeing in my comments. Can’t wait to debunk your hallucinations and complete misunderstandings grounded in your own cluelessness. Go ahead!
@Iron Heart
“You say that NordVPN or ProtonVPN etc. provide a good service (I assume you mean stable connections, a good UI etc.)”
First I didn’t said this about Nord or Proton. All I’m saying is some credible independent sources with no ties to any products or no personal preference to any products can provide some good reviews. And the links you mentioned before and in the last comment are not them.
“My reply to this is: It doesn’t matter. Other services provide this as well and have none of the shady business connections of NordVPN or ProtonVPN, they also don’t hide their owners unlike NordVPN, ExpressVPN etc. Since it ultimately comes down to blind trust, as you don’t know what is really happening on the VPN servers, why should anyone run a risk when there are other capable services? Please explain that.”
I would say its a good point, why would you trust? My answer you don’t. I’ve never used Nord or Express or the latest Youtuber’s favourite Surfshark. I’m using ProtonVPN right now, no long term subscriptions like 3 years. Once the subscription ends I’ll try other VPNs, most likely which have their apps available in F-Droid, and not visiting Privacy Watch Dog or airvpn thread for some tips.
“Sorry, but if you trust either NordVPN or ProtonVPN, you are frankly an idiot:
https://airvpn.org/forums/topic/28876-why-you-can%E2%80%99t-trust-nordvpn/”
First I use Proton so thanks. Second again I guess airvpn thread is transparent for drawing conclusion about other VPNs. Plus most comments are outdated, and in Proton outright lies, mention some good sources and maybe latest ones too.
“Also, stop bashing madaidan. He is a respected developer with years of experience in the field, while you are, frankly, a clueless idiot. There is no comparison between the two of you. Show some respect and move on, especially when you don’t have any kind of counter-argument to what madaidan actually says, having to resort to embarrassing ad hominem attacks as a substitute.”
Say what you want, just look in the mirror while doing that. And a guy recommending Windows, IPhone and other laughable things – I don’t and will never take seriously :-)
“Last but not least, I have no problem with you posting supposed “contradictions” and “lies” you are apparently seeing in my comments. Can’t wait to debunk your hallucinations and complete misunderstandings grounded in your own cluelessness. Go ahead!”
Visit Ideas.mozilla.org article and see your contradictions about Firefox security when replying to me and in Brave latest article when replying to Brave Heart, and if you can’t, watch one of Roy Keane’s videos, you’ll get a sense of reality, which is use some facts and don’t question them when coming at you.
@Yash
I am trying to warn people about shady business connections here regarding services they ultimately have to put their trust in, as the veracity of their claims can’t ultimately be verified. All you are doing here is wasting my time with your naivety and plain idiocy. I think you should be ashamed, ashamed of your own pride issues blinding you to unpleasant realities, and your proven inability to admit that the services you trust may not be that trustworthy after all – you are harming people here, if people are really dumb enough to believe you (I doubt it, but who knows).
> First I didn’t said this about Nord or Proton.
You did:
“Since the Nord Hack, the company has changed everything and have done an audit. Let that sink in.”
“Proton is a good company with good products, the same as Tutanota, same as many others.”
Those are endorsements.
> All I’m saying is some credible independent sources
You mean all those reviewers acting as if they were independent while they are actually being paid via NordVPN’s and ExpressVPN’s respective affiliate programs? I know that you trust these sources. Problem is, they are lying, just like you.
> And the links you mentioned before and in the last comment are not them.
OK, once again:
– You ultimately can’t verify what happens on the servers of your VPN provider because you are not in control of the servers. They might go against their official promises and you would have no way to notice.
– There are definite hints at a connection of NordVPN and ProtonVPN to a data mining company, Tesonet.
Any sane person would think twice about booking ProtonVPN, considering those two facts combined. But you are not quite sane, are you? You are trusting in a company that has ties to a data mining company, while being unable to verify whether or not their claims about logging are actually true?
Bwahahaha, that’s plain retarded. Sorry, but that is the truth. No sane person with more than two brain cells acts this way. You are either a very stubborn fool who can’t admit the problem or you are an actively malicious shill. Choose one.
> most likely which have their apps available in F-Droid,
Their client-side apps being open source tells you nothing about their server-side code. I have already explained this, are you able to understand it (serious question)?
> and not visiting Privacy Watch Dog or airvpn thread for some tips.
You can of course – ignorantly and stupidly – choose to ignore hints at fishy business relations of companies you trust, but that doesn’t mean that others won’t appreciate my hints at red flags.
> and in Proton outright lies
They were not able to deny the allegations, they have however proceeded to hide some of their most obvious connections to Tesonet in the aftermath, as best as they could. Nothing to see here, of course, move along.
> Say what you want, just look in the mirror while doing that. And a guy recommending Windows, IPhone and other laughable things – I don’t and will never take seriously :-)
You are literally too dumb to understand madaidan’s analysis, I fear. I don’t even mean this as a slur, this is really what I perceive based on your sentences. madaidan has analyzed the security of both iOS and Windows and concluded, correctly, that both operating systems have stronger exploit mitigations in place compared to their competitors, Android and Linux. Stronger exploit mitigations mean that most hacks are harder on iOS and Windows when a component is attacked, compared to similar hacks on Android and Linux where a similar component is attacked. This is NOT an analysis of privacy, this does NOT mean that Windows and iOS are unhackable. This just means that, in most cases, they are HARDER to hack, NOT IMPOSSIBLE to hack. Counting security issues is for cretins because a) the number does not tell you how hard these hacks were and b) numbers of security issues tend to rise with popularity because more popular software is more attractive for would-be hackers and receives more scrutiny.
> Visit Ideas.mozilla.org article and see your contradictions about Firefox security when replying to me and in Brave latest article when replying to Brave Heart
Again, same as with the madaidan article, you are also too dumb to understand my comments. Same misunderstanding as with madaidan’s article, I can literally copy and paste my sentences from above:
I have commented on the security of Chromium and stated, correctly, that the browser has stronger exploit mitigations in place compared to its competitor, Firefox. Stronger exploit mitigations mean that most hacks are harder on Chromium when a component is attacked, compared to similar hacks on Firefox where a similar component is attacked. This is NOT an analysis of privacy, this does NOT mean that Chromium is unhackable. This just means that, in most cases, it is HARDER to hack, NOT IMPOSSIBLE to hack. Counting security issues is for cretins because a) the number does not tell you how hard these hacks were and b) numbers of security issues tend to rise with popularity because more popular software is more attractive for would-be hackers and receives more scrutiny.
See, I can literally copy and paste the same thing all over again, because you make the very same mistake all over again. Tiresome, pointless waste of time.
People who read these comments will understand who tries to warn them about possible issues of various so-called privacy services, and who is either a total ignorant or a shill. Guess who is who. I am out.
@Iron Heart
When I said – ‘Since the Nord Hack, the company has changed everything and have done an audit. Let that sink in.’
And ‘Proton is a good company with good products, the same as Tutanota, same as many others.’
That doesn’t mean an endorsement, * [Editor: removed]. If it is one, then you endorse Brave all the time. All I said was since Nord Hack, the company has done an audit and ProtonMail is a good service like Tutanota. Funny you didn’t said I endorse Tutanota too by that pathetic logic.
“You say that NordVPN or ProtonVPN etc. provide a good service (I assume you mean stable connections, a good UI etc.)”
Folks who can’t read should not open their mouth. So when I denied your quote, you’re saying this is an endorsement. I never said Nord is a good service. Luckily this thread is a proof of that.
“I am trying to warn people about shady business connections here regarding services they ultimately have to put their trust in, as the veracity of their claims can’t ultimately be verified. All you are doing here is wasting my time with your naivety and plain idiocy. I think you should be ashamed, ashamed of your own pride issues blinding you to unpleasant realities, and your proven inability to admit that the services you trust may not be that trustworthy after all – you are harming people here, if people are really dumb enough to believe you (I doubt it, but who knows).”
Man STFU. And this “ultimately can’t be verified” – King of contradiction Iron Heart can’t be verified.
“You mean all those reviewers acting as if they were independent while they are actually being paid via NordVPN’s and ExpressVPN’s respective affiliate programs? I know that you trust these sources. Problem is, they are lying, just like you.”
I never even mentioned any reviewers so what are you trying to say? Lying as if your life depends on it, eh?
And certainly I never praised Nord or Express. Looking back at this thread, I’m questioning a guy who didn’t provided any proof in Privacy Watch Dog and in a reddit link I mentioned earlier he couldn’t even make his damn point against ProtonMail.
And I’m also saying that a random youtuber who makes only VPN videos can’t be trusted when most of the videos are clickbaits. So stop lying when saying other reviewers? I never mentioned one, not yet and this thread is proof of that.
“– You ultimately can’t verify what happens on the servers of your VPN provider because you are not in control of the servers. They might go against their official promises and you would have no way to notice.
– There are definite hints at a connection of NordVPN and ProtonVPN to a data mining company, Tesonet.”
And
“Any sane person would think twice about booking ProtonVPN, considering those two facts combined. But you are not quite sane, are you? You are trusting in a company that has ties to a data mining company, while being unable to verify whether or not their claims about logging are actually true?
Bwahahaha, that’s plain retarded. Sorry, but that is the truth. No sane person with more than two brain cells acts this way. You are either a very stubborn fool who can’t admit the problem or you are an actively malicious shill. Choose one.”
And
“Their client-side apps being open source tells you nothing about their server-side code. I have already explained this, are you able to understand it (serious question)?”
You’re more than welcome to highlight flaws in their server side infrastructure, if you can. You only provided just one link for ProtonVPN and that is of AirVPN blog, and the link posted by Staff as you said – vpnscam or something like that doesn’t even load. I’m using Firefox so maybe you can open that in Brave and paste some quotes here if you can. Safe to say way to go making a fool of yourself by mentioning a thread in which the link provided doesn’t even load.
“They were not able to deny the allegations, they have however proceeded to hide some of their most obvious connections to Tesonet in the aftermath, as best as they could. Nothing to see here, of course, move along.”
Some quotes, links to prove it? Of course apart from the link from Staff you mentioned in AirVPN blog whose provided link doesn’t load?
“You are literally too dumb to understand madaidan’s analysis, I fear. I don’t even mean this as a slur, this is really what I perceive based on your sentences. madaidan has analyzed the security of both iOS and Windows and concluded, correctly, that both operating systems have stronger exploit mitigations in place compared to their competitors, Android and Linux. Stronger exploit mitigations mean that most hacks are harder on iOS and Windows when a component is attacked, compared to similar hacks on Android and Linux where a similar component is attacked. This is NOT an analysis of privacy, this does NOT mean that Windows and iOS are unhackable. This just means that, in most cases, they are HARDER to hack, NOT IMPOSSIBLE to hack. Counting security issues is for cretins because a) the number does not tell you how hard these hacks were and b) numbers of security issues tend to rise with popularity because more popular software is more attractive for would-be hackers and receives more scrutiny.”
Same old sh*t, trying to defend a joke guy whose bubble has been bursted and was already a joke before Pegasus. See some tweets by Daniel Micay on software security first before writing more nonsense.
“I have commented on the security of Chromium and stated, correctly, that the browser has stronger exploit mitigations in place compared to its competitor, Firefox. Stronger exploit mitigations mean that most hacks are harder on Chromium when a component is attacked, compared to similar hacks on Firefox where a similar component is attacked. This is NOT an analysis of privacy, this does NOT mean that Chromium is unhackable. This just means that, in most cases, it is HARDER to hack, NOT IMPOSSIBLE to hack. Counting security issues is for cretins because a) the number does not tell you how hard these hacks were and b) numbers of security issues tend to rise with popularity because more popular software is more attractive for would-be hackers and receives more scrutiny.”
This is not what you wrote, so let me correct you –
When replying to Brave Heart in latest Brave article on gHacks, Iron Heart July 25, 8:01 p.m. wrote – “Believe it or not, eight zero-days in this year so far is NOT bad for a software with that kind of complexity and attention attached to it. Let’s take a look at Firefox / Gecko, shall we?
https://www.mozilla.org/en-US/security/advisories/”
See Iron Heart here you’re replying to someone who mentioned some security issues in Chromium which were fixed recently by mentioning issues Firefox fixed. Fair enough, that how things roll in software world.
Now your contradiction, Ideas.mozilla.org gHacks article, Iron heart July 26 12:49 a.m. – “> Of course some real world examples for Firefox security issues are always welcome :-)
Feel free to choose any of them:
https://www.mozilla.org/en-US/security/advisories/”
Funny thing is you’re providing a link which list security issues fixed, and look these are Firefox security issues, although that can be said about Chromium or any other software which list security issues fixed.
Again way to go making a fool of yourself by using two different quotes for same thing and twisting facts to suit your pathetic definitions.
There are countless contradictions, even in last few comments you only listed one link – of AirVPN blog to question ProtonVPN and even that doesn’t load, not to mention it is 2 years old now. So before writing again, atleast provide some evidence for your imaginary theories and if you can’t, don’t reply writing same old s*it again.
@Yash
> That doesn’t mean an endorsement, you idiot.
In which realm of imagination is “Proton Technologies offers good products.” NOT an endorsement? Hahaha…
> If it is one, then you endorse Brave all the time.
I’ll point out the obvious difference to you: Brave has no server-side component that I need to trust with my data, it is 100% locally run open source software. VPNs have a server-side component to them of which the code is not public.
> All I said was since Nord Hack, the company has done an audit
“As for NordVPN hack, it is true but that happened more than two years ago. Since then they have done an audit and have switched their servers into RAM disk mode. And that is more important. Of course use your uncensored internet for that ©”
Another endorsement written by a naive fool, so great, they are using RAM disk now… LOL. I can’t even…
> Funny you didn’t said I endorse Tutanota too by that pathetic logic.
Even if that’s the case, how does it matter for my argument? A broken clock is right twice a day, so if you happen to endorse some OK product amid your defense of untrustworthy products, this doesn’t necessarily raise the general standard of your posts. Even you have to be right every now and then, even though it is hard to believe.
> I never said Nord is a good service.
OK, so you don’t believe NordVPN is a good (= trustworthy?) service. Cool. Then perhaps you should stop rushing to their defense when this shady company is being criticized.
> And this “ultimately can’t be verified”
Well yeah, it’s still true. You have never seen the server-side code of your VPN service, correct?
> I never even mentioned any reviewers so what are you trying to say? Lying as if your life depends on it, eh?
You seem to like mainstream tech websites and their reviews, because apparently, the word of some nobody blogger isn’t enough for you even if it’s only meant as a hint at possible issues. Instead, you seem to be relying to on (paid) mainstream tech endorsements of ProtonVPN, ExpressVPN and similar services. Your comments ooze this mentality since you are superficially dismissing sources that don’t have a highly professional appearance to them, whatever such an outside appearance might be worth.
Paid reviews are a shit source for information in reality, you know.
> You’re more than welcome to highlight flaws in their server side infrastructure, if you can.
In case of ProtonVPN, I wasn’t talking about flaws of their operational security. They could have top notch operational security and still log, the two aren’t even related. I can’t verify their no logging claim and neither can you. I am just saying that them having ties to a data mining firm doesn’t build up trust in their unverifiable claims.
> You only provided just one link for ProtonVPN and that is of AirVPN blog, and the link posted by Staff as you said – vpnscam or something like that doesn’t even load. (…) Safe to say way to go making a fool of yourself by mentioning a thread in which the link provided doesn’t even load.
The thread is two years old, so links don’t necessarily exist anymore. It happens all the time, private blogs sometimes just don’t stay online. So what? You can also draw this information from elsewhere without having to rely on dead links.
> Some quotes, links to prove it? Of course apart from the link from Staff you mentioned in AirVPN blog whose provided link doesn’t load?
They are trying to cover their tracks, my dude:
https://old.reddit.com/r/technology/comments/8x9aik/protonvpn_is_being_operated_by_a_data_mining_firm/e24vxbh/
Also the reply from “krn” does some before – after comparisons and again shows that they are trying to cover their tracks:
https://news.ycombinator.com/item?id=18609655
Have we established now that you put your trust in Tesonet, but fail to admit it? But yeah, we certainly had to waste space massively here to come to that conclusion…
> Same old sh*t, trying to defend a joke guy whose bubble has been bursted and was already a joke before Pegasus.
Same old sh*t coming from you, rather. I have said it multiple times and will say it again, just for you: One security issue doesn’t invalidate the security of the ENTIRE operating system. It just means that some component was at some point attackable. Wow. Happens all the time, says nothing about the general state of security of an OS, of all its other components.
> This is not what you wrote, so let me correct you –
This is not a contradiction, you utter moron. No operating system, browser, or any other type of complex software is unhackable. I never made that claim and neither did madaidan, if you care to read what was clearly said for once. Keeping that ind mind, software can have strong exploit mitigations that make hacks harder. Compared to Chromium, Firefox just lacks certain exploit mitigations. Trivial sandbox escapes and memory safety issues are possible in Firefox that are either no longer possible in Chromium or are much harder to realize. That does not mean that Chromium doesn’t have any zero days, you fool. It just means that Chromium exploits, while possible, would take greater effort because more barriers have to be taken to achieve a predefined goal.
I am in awe (not in a good way) of your inability to understand what was clearly laid out to you, in front of your very eyes.
> Funny thing is you’re providing a link which list security issues fixed, and look these are Firefox security issues, although that can be said about Chromium or any other software which list security issues fixed.
Does some number of fixed / former security issues say anything about the exploit mitigations that are in place? Answer: It doesn’t.
If you care to look into the security issues fixed by Firefox, you will find that some of the exploits wouldn’t have been possible in Chromium in the same way, with such effortlessness. Did Firefox fix the issues? Yes, but very similar trivially exploited security issues will creep up if they don’t put stronger exploit mitigations in place. Why do you think they are trying to frankenstein Project Fission onto the old codebase? To make such hacks less trivial, you see…
> There are countless contradictions
No, there is only your blatant retardation and lies. Shall I sum the things I said about security to you? Here we go:
– Exploit mitigations like sandboxing or real site isolation don’t mean that software is suddenly unhackable now, the hacks just become comparatively harder.
– If such exploit mitigations are not in place, easier – and even trivial – hacks may lead to success. This needs to be improved if that’s the case.
– Every software of the complexity of a browser or operating system inevitably has exploitable security issues. Claiming that any browser or OS is unhackable is retarded and such a claim was never made by me or anyone else here.
– Security comparisons are relative and never absolute, and security improvements are an ongoing effort.
– Comparing the mere number of security issues says nothing without exploring and comparing the easiness of the respective hacks and without taking into account the popularity & general scrutiny applied to each software.
This is the kindergarten version, I really hope this exposes your maliciousness or foolishness for what it is. A WASTE OF TIME.
Can you PLEASE stop annoying me now? I had to show yet again that you are putting your trust in the wrong people, and although this is nothing particularly new, the huge threads that emerge from your pride issues and lack of understanding are a massive time sink.
@Iron Heart
Dude its all getting boring.
“In which realm of imagination is “Proton Technologies offers good products.” NOT an endorsement? Hahaha…”
“Proton Technologies offers good products” – I would love to see in which comment I said this, I only remember saying it for ProtonMail but also for Tutanota too.
“As for NordVPN hack, it is true but that happened more than two years ago. Since then they have done an audit and have switched their servers into RAM disk mode. And that is more important. Of course use your uncensored internet for that ©”
There are generally two sides of an argument, and so when you mentioned Nord Hack, that’s what I said – two years ago and audit done, even MartinB has mentioned audit. And as for audit you’re more than welcome to analyse their findings. See what I did there – No trashing and no praising of Nord – that’s it. But then in a mind of conspiracy theorist if it is an endorsement, then good for you. RAM disk – I’m not an expert but when a certain government obtained Express servers, they couldn’t find anything and it happened four years ago, and after that most companies started doing it including Nord. Again no praising, no trashing, just saying FACTS. If this is an endorsement, well good for you.
“OK, so you don’t believe NordVPN is a good (= trustworthy?) service. Cool. Then perhaps you should stop rushing to their defense when this shady company is being criticized.”
There is a thing in the world and that’s called being neutral. So when I’m saying ‘I never said Nord is a good service’ it doesn’t mean it is a bad service. Funny how the modern society works, if I said something, then some stupid guy would start doing his tantrum – look he said it is a bad service or look that is a bad service.
“Well yeah, it’s still true. You have never seen the server-side code of your VPN service, correct?”
Well I asked you to provide some links for that in case of Proton, but you didn’t. So if you can’t provide the links, better shut your mouth.
“You seem to like mainstream tech websites and their reviews, because apparently, the word of some nobody blogger isn’t enough for you even if it’s only meant as a hint at possible issues. Instead, you seem to be relying to on (paid) mainstream tech endorsements of ProtonVPN, ExpressVPN and similar services. Your comments ooze this mentality since you are superficially dismissing sources that don’t have a highly professional appearance to them, whatever such an outside appearance might be worth.
Paid reviews are a shit source for information in reality, you know.”
I would love to know which mainstream site I mentioned here in this thread which made you write all this, go ahead and list some.
“In case of ProtonVPN, I wasn’t talking about flaws of their operational security. They could have top notch operational security and still log, the two aren’t even related. I can’t verify their no logging claim and neither can you. I am just saying that them having ties to a data mining firm doesn’t build up trust in their unverifiable claims.”
When you can’t prove something, its better to STFU, that’s what I said in earlier comments. So instead of writing “I wasn’t talking about …..” better provide some evidence or don’t mention it.
“They are trying to cover their tracks, my dude:
https://old.reddit.com/r/technology/comments/8x9aik/protonvpn_is_being_operated_by_a_data_mining_firm/e24vxbh/
Also the reply from “krn” does some before – after comparisons and again shows that they are trying to cover their tracks:
https://news.ycombinator.com/item?id=18609655
Have we established now that you put your trust in Tesonet, but fail to admit it? But yeah, we certainly had to waste space massively here to come to that conclusion…”
Funny the first link you mentioned, someone said it already that PIA is behind all this, that VPN has new ownership since writing that blog which is already three years old, so good from you mentioning transparent and honest blog. Way to go making a fool of yourself, I’ll admit, questioning Proton without any proof and providing a link to a blog of a VPN service which has some serious questions about its current ownership. A guy trying to be too smart trashing Nord and Express and then mentioning PIA, that was really good from you Iron Heart.
And second link, again no evidence, just some dude trying hard to be too smart and not providing any facts at all about Proton. Seriously laughable.
I only listed Firefox to highlight your contradictions when mentioning same links, but since you ignored it and started saying it again – Firefox is not secure, then here’s the answer – yeah all Firefox users are living in alternate reality where it is secure ;-)
As for mentioning Kindergarten version and all that nonsense, there is a simple way to settle all this. Its called checking Daniel Micay(guy you said I should worship) and GrapheneOS twitter account and see some actual OS level security, before writing again.
Its funny when a guy is trying too hard to act smart and saying stuff about security when he is infact defending a joke guy in madainwhatever.
Go ahead and do some research on OS level security before saying anything.
@Yash
> Dude its all getting boring.
The only thing I can 100% agree on. Perhaps you should stop spreading your disinformation.
> “Proton Technologies offers good products” – I would love to see in which comment I said this, I only remember saying it for ProtonMail but also for Tutanota too.
“Proton is a good company with good products, the same as Tutanota, same as many others.”
“Products” is plural and thus has to include both ProtonMail and ProtonVPN. Anyway, by endorsing ProtonMail, you are implicitly saying that you trust the company. Wouldn’t make sense for you to suddenly distrust ProtonVPN coming from the same company, would it? Plus, from prior conversations with you, I know that you are a ProtonVPN customer, so if that is not a statement of trust, then I don’t know what is. You call their products “good” and thus endorse them, there is really no way around it.
> There are generally two sides of an argument, and so when you mentioned Nord Hack, that’s what I said – two years ago and audit done, even MartinB has mentioned audit. And as for audit you’re more than welcome to analyse their findings.
I’ll repeat it again for you: Their operational security is not my main concern with them. It used to be shit obviously, they have been hacked – but that is not the issue I describe here. The issue is that I don’t trust their privacy protection claims and this hasn’t anything to do with operational security. You are mixing up unrelated topics as always, way to go.
> But then in a mind of conspiracy theorist (…)
Is you calling me a “conspiracy theorist” (really tired meme as of 2021, I must say…) supposed to be the antidote to me suggesting that you have been fooled? If so, it’s not really working so far, is it? But hey, whatever helps you sleep…
> M disk – I’m not an expert but when a certain government obtained Express servers, they couldn’t find anything and it happened four years ago,
So you think that a server that at least transmitted data related to a high profile assassination (Russian ambassador in Turkey was killed) being empty proves anything? OK, fine, let’s see:
1) Only one server in Turkey was (officially) found to be devoid of user data. This server being empty doesn’t prove a no logging policy across their entire VPN server network.
2) The server being empty does not prove that they were not logging. Logged data could have been wiped after the fact, after it was noticed that data related to a high profile criminal case was stored there. Logging could very well have happened beforehand.
3) As for who would do that, either the (employer of the) assassin would have an interest to do that, or ExpressVPN themselves because a) they didn’t want to be dragged into a high profile assassination court case and b) because their official no logging claims were acutely in danger if a third party (law enforcement) seized their server and found any logs (in court).
4) Such a wipe is a matter of seconds, especially as far as RAM disks are concerned. Wiping HDDs / SSDs would take far longer, RAM can be instant.
I also find it curious that the assassin supposedly used a VPN server in Turkey for an assassination carried out in Turkey, knowing that Turkish authorities would have physical access to the server… Anyways.
You can deny what I am saying about a possible vested interest in wiping such data, either by the attacker or ExpressVPN themselves, but you can hardly deny 1) and 2) above. Your “proof” doesn’t prove what you think it proves.
Also, if they were really not logging, if their claims were truthful and if their jurisdiction officially permits a no logging policy, I wonder why we still haven’t gotten the names of the owners of ExpressVPN? Why wouldn’t they want to stamp their name on true and lawful statements?
> So when I’m saying ‘I never said Nord is a good service’ it doesn’t mean it is a bad service.
Putting one’s trust in them or not, and consequently using their service or not, is ultimately a binary Yes / No decision. Verbal decorations aside, you either join the club or you don’t. There is no “neutral” here.
> Well I asked you to provide some links for that in case of Proton, but you didn’t. So if you can’t provide the links, better shut your mouth.
> When you can’t prove something, its better to STFU, that’s what I said in earlier comments. So instead of writing “I wasn’t talking about …..” better provide some evidence or don’t mention it.
Do you possess any kind of reading comprehension? I said that their no logging claims are NOT VERIFIABLE, because the server-side code is NOT PUBLIC. How am I supposed to point to code that is not public? Are you retarded?
The honest answer to the question “Does ProtonVPN log user activity?” is “I can’t verify it.”, all I have is their word that they don’t log. Here, we arrive again at the binary decision, “Do I trust their word or not?”. Considering their connections to Tesonet that they clumsily tried to hide when the topic was first brought up, I don’t trust them, because Tesonet’s business model implies an analysis of user data, which requires logs. You choose to dismiss the hints at possible conflicts of interest because they are coming from a nobody blogger, which, in my opinion, is superficial, arrogant, blind, and absolutely retarded, but is ultimately really just you arriving at the other side of the binary Yes / No trust decision.
> I would love to know which mainstream site I mentioned here in this thread which made you write all this, go ahead and list some.
I don’t need to. You putting your trust in them either means that you have read their website and chose to trust their official claims outright, or that you read and trusted some third party review where those claims were repeated, if you didn’t just outright trust the website.
Neither of these sources of information would touch on any possible issue with the company, the company itself would of course not admit any of it, and paid reviewers wouldn’t because of the money coming from affiliate programs.
> Funny the first link you mentioned, someone said it already that PIA is behind all this, that VPN has new ownership since writing that blog which is already three years old, so good from you mentioning transparent and honest blog.
It doesn’t really matter “who” is behind the allegations about the Proton Technologies AG, it is the information given that matters. The Proton Technologies AG desperately yet clumsily trying to hide their connection to Tesonet post-allegations is enough for me to believe that there is some “meat on the bone”, so to speak. Why are they hiding information about something that is outright false according to them, in each case information that would confirm the actual veracity of the alleged “false claims”? Hm…
This is a consistent theme with you, by the way: Some nobody blogger says something, it has to be false already based on outside appearance. Some competitor of ProtonVPN reveals something about them, so it has to be false because blah blah… You are looking way too much at the “who said” and far less on the “information given”. Information can’t just be disqualified based on superfluous “who said” discussions. Curiously, what you never look at is how the Proton Technologies AG has responded to the allegations, namely by frantically trying to hide anything that could serve as proof against them (and yet you expect me to provide strong proof, which they have likely destroyed – LOL, talk about making the impossible happen despite all obstacles thrown in by people who want to hide from the public).
> Way to go making a fool of yourself, I’ll admit, questioning Proton without any proof and providing a link to a blog of a VPN service which has some serious questions about its current ownership. A guy trying to be too smart trashing Nord and Express and then mentioning PIA, that was really good from you Iron Heart.
I haven’t endorsed Private Internet Access, in fact, I haven’t even brought them or their product up. You did. I merely pointed to a discussion on their forums that wasn’t about them even.
They might well suffer from similar issues as the ones I criticize in case of NordVPN or ExpressVPN, namely obscure ownership. I don’t make an excuse for Private Internet Access here at all.
However, if these untrustworthy companies decide to rat each other out, I am all for it. I don’t see a smear campaign here, I see a golden opportunity for gathering intelligence about these companies from their back and forth allegations. Competition is good for something at last, haha.
> And second link, again no evidence, just some dude trying hard to be too smart and not providing any facts at all about Proton. Seriously laughable.
Your willful blindness is the only thing laughable here.
> I only listed Firefox to highlight your contradictions when mentioning same links, but since you ignored it and started saying it again – Firefox is not secure
There is no contradiction, because I have never made the claims you allege I’ve made. I never said that any software is unhackable, neither did madaidan. This would be stupid, easily debunked, and an absolute non-starter. It seems you have to put words in my mouth, this is very pathetic.
However, the impossibility of making an unhackable piece of software at the level of complexity of a web browser doesn’t mean that it is OK for basic exploit mitigations (which are making hacks LESS TRIVIAL, NOT IMPOSSIBLE) to be missing.
> yeah all Firefox users are living in alternate reality where it is secure ;-)
You are living in the same reality as I do, one in which Firefox lacks basic exploit mitigations and has fairly trivial hacks associated with its name so far. There is a reason why they didn’t compete in the Pwn2Own hacking contest for some time while Chrome and Safari did. I’ll let you figure out what the reason was, I am sure it had absolutely nothing to do with a pronounced lack of very basic exploit mitigations and resulting trivial hacks. /s
> As for mentioning Kindergarten version and all that nonsense, there is a simple way to settle all this. Its called checking Daniel Micay(guy you said I should worship) and GrapheneOS twitter account and see some actual OS level security, before writing again.
You mean the same Daniel Micay who is still spreading the truth about the actual state of Firefox’s security?
https://old.reddit.com/r/firefox/comments/gokcis/firefox_is_insecure_refuted/frh286y/
That Daniel Micay? Haha, I don’t think bringing him up will do you a favor, this known expert disagrees heavily with your nonsensical claims about Firefox’s security. Oh and yes, of course, going by the bullshit you consistently write here, you should respect, even worship him. You can only learn from him, as you don’t know what you are talking about – sadly across the board.
> joke guy in madainwhatever.
Seasoned developer = a joke, you = someone important? LOL, are you kidding me? You are some random dude with strong opinions but very little knowledge to back it all up, that’s the truth. At least show some respect to people who know what they are talking about.
> Go ahead and do some research on OS level security before saying anything.
Read my last comment. I have said some useful things about security (what it means, and what it isn’t) that you still don’t understand.
@Iron Heart
“Putting one’s trust in them or not, and consequently using their service or not, is ultimately a binary Yes / No decision. Verbal decorations aside, you either join the club or you don’t. There is no “neutral” here.”
This line fortunately revealed your true colours. In your mind everything is good or bad. Well I guess you’re right in your mind atleast.
This thread is kinda getting boring, all of a sudden I’m talking about things I didn’t even started. So lets do a reshuffle –
I don’t give a damn about Nord or Express or PIA, all I’m saying is if you’re throwing mud at someone, better do it for right reasons, and for once in your life, use some common sense. I’m being neutral here, no trashing and no praising, if you can’t understand it, don’t talk about it. And your latest comment is a proof – you can’t understand things properly. You didn’t mention any new links about VPN security and privacy, luckily to prove this I only need to scroll your last comment. So before trying to be too smart again, first atleast mention some good sources to prove your claims or better stay on the fence. For example I don’t use Vivaldi, but that doesn’t mean in every Vivaldi article, I have to say its getting slow. Stay on the fence, no trashing and no praising.
And then you wrote stuff about Express servers without some proof, all I can say is I’m not that interested in reading someone’s else ranting when no evidence was shared in his usual totalitarian mindset.
About Proton which was the main issue I even said in my first comment in this thread, again you didn’t mention any links in your latest comment. As for which products I use – For Email its Tutanota, and for VPN its Proton. But that doesn’t mean I now have to trash ProtonMail like Privacy Watch Dog trash guy. And that’s the point. But then again you started trashing Proton for reasons only known to you, and when asked to provide some proof, you went back in your shell and started saying – Oh look Proton is bad, server code is not public, you can’t verify their claims, look at these links, which I will be honest they really made me laugh. Again share some good posts, links than ranting, and maybe alternatives too which are better if you can, once my VPN subscription ends, I’ll check them.
Facebook for promotion against Net Neutrality years ago, mentioned Delloit report(or something like that) to the crowd which was in truth created by Facebook itself. And its the same thing I’ve seen in your shared links against Proton. Allegations made by a rival company, whose claims were proved false in the very same reddit thread, and has some serious questions about its ownership. I now truly believe you don’t read comments in a thread before sharing them. Also you don’t use common sense oherwise you would’ve seen this rival company taking a dig miles out, and would have also seen the hoax created against Proton, again if want to say something, you’re more than welcome but only if you can make a good point than what you do you do all the time – ranting.
About bloggers, I don’t have problem with them, would say one thing though – don’t question a service when you can’t prove your point for real. Privacy Watch Dog is an example.
Now about the reddit link you shared, I liked it. First what Daniel Micay said about Firefox security – IDGAF, if Firefox would have been insecure, someone other than him would have noticed it. Daniel Micay isn’t the only security expert in the world and no real world incidents have been shared, which I have also said in the past. Second it also has comments from Gorhill which I liked, him asking for evidence which then weren’t provided as expected, afterall when one guy is trashing Firefox on purpose then he loses the sense of reality.
I never took Daniel Micay seriously when it comes to Firefox security. He in multiple reddit comments also praised Google Play Services, iPhone and what not for reasons other than privacy, he even praised Google requiring key from app developers, I’m not going to list them, find them yourself by using your uncensored internet(meant as sarcasm which went above your head judging by your earlier comments). When Pegasus news broke, he retweeted a tweet which clearly said Sandboxes are not enough, and new secure language has to be used, which I already mentioned in another article, go check that. So yeah I’m connected to reality to make a decision, while you’re not.
“I’ve said some useful things about security” – no you haven’t. You never proved anything, shared some concrete evidence for reasons behind them and more importantly trying too hard to prove you’re smart when you aren’t. And this line – “show some respect to some people who know what they are talking about” If you mean I have to trust madaidan and start using Windows over Linux, stop using LineageOS, Firefox, VPNs and more importantly give preference to Smartphones over Desktop, then yeah I know how much respect that guy deserves, spoiler alert – nothing.
In your last few comments, you didn’t add much apart from ranting of course, so share some more links, I want to know how disconnected you’re from ground reality about many products and services ;-)
@Yash
> I don’t give a damn about Nord or Express or PIA, all I’m saying is if you’re throwing mud at someone, better do it for right reasons, and for once in your life, use some common sense.
Dude, I am using plenty of common sense, you just choose to dismiss it because of your own preconceived opinions. The latter can’t be helped and is not my fault, you see.
Also, “throwing mud”, really? The mud is already there, I am just uncovering it. Those are in-house problems, not something I would first have to throw at them.
> You didn’t mention any new links about VPN security and privacy, luckily to prove this I only need to scroll your last comment. So before trying to be too smart again, first atleast mention some good sources to prove your claims or better stay on the fence.
Use your brain, only for once: If they (NordVPN and ProtonVPN) are owned by a data mining company, public knowledge of this would wreak havoc to their business. So once those allegations surfaced, they did everything in their power to DESTROY EVIDENCE. I can’t point to evidence that they pulled from the public eye! Same like I can’t point to code that is not public!
However, luckily, third parties are revealing Tesonet’s web of lies:
https://www.docdroid.net/kOP3JAh/tesonet-web-of-lies-pdf
Plenty of links and shady connections in there. I bet that, while still arguing with me here based on wounded pride, you are probably already trying to get your money back from ProtonVPN, hahaha.
> And then you wrote stuff about Express servers without some proof, all I can say is I’m not that interested in reading someone’s else ranting when no evidence was shared in his usual totalitarian mindset.
Hahaha, you really copied the “totalitarian mindset” response I posted in one of our prior pointless conversations and you now try to throw it right back at me after the “conspiracy theory” meme hasn’t worked. Ridiculous… Bad news for you, though: That no data was found on ONE(!) server that has transmitted data related to a high profile assassination before, proves absolutely nothing.
If any of ExpressVPN’s claims were true, why are they hiding? Still waiting for an answer from you.
> But that doesn’t mean I now have to trash ProtonMail like Privacy Watch Dog trash guy.
No need to. Other people have already found out about Tesonet, you wouldn’t add anything new here.
> and maybe alternatives too which are better if you can, once my VPN subscription ends, I’ll check them.
The Privacytools.io list is otherwise solid, I just think that their ProtonVPN endorsement is questionable.
> Allegations made by a rival company, whose claims were proved false in the very same reddit thread, and has some serious questions about its ownership.
The claims weren’t proven false. Proton Technologies AG proceeded to destroy evidence that could have compromised them. Surely that was a trust building measure, right?
And again: PIA suffers from similar issues as ExpressVPN or NordVPN or ProtonVPN, namely unclear ownership. I am NOT defending PIA here. All I am saying is that it is great that these companies rat each other out. It is to our benefit.
> and would have also seen the hoax created against Proton
It’s sadly not a hoax, you naive fool. And yet again: Let them rat each other out, this is absolutely fantastic, if anything.
> First what Daniel Micay said about Firefox security – IDGAF
You can choose to not care, but this won’t make the glaring security issues go away. You are acting like a child: “If I close my eyes, the problem is no longer there.”
> if Firefox would have been insecure, someone other than him would have noticed it.
Mozilla themselves have noticed it, hence their attempt to implement real site isolation and memory-safe language.
> Daniel Micay isn’t the only security expert in the world and no real world incidents have been shared,
You do realize though that many of the security issues Mozilla fixes monthly were actively exploited before, right? Sometimes to the point where they had to provide hotfixes, you know, the x.y.1 emergency updates following major releases.
> Second it also has comments from Gorhill which I liked, him asking for evidence which then weren’t provided as expected, afterall when one guy is trashing Firefox on purpose then he loses the sense of reality.
What Micay says about extensions not being fail-safe is self-explanatory. No third party component using the browser’s APIs is fail-safe. Gorhill has no clue about security, otherwise he would have been more considerate in his rants about the removal of the webRequest API which gives fairly dangerous privileges to extensions.
> I never took Daniel Micay seriously when it comes to Firefox security.
…but at the same time, you were never able to prove him wrong. :D You just choose not to look at the evidence, like a child. This is not a proper response.
> He in multiple reddit comments also praised Google Play Services, iPhone and what not for reasons other than privacy, he even praised Google requiring key from app developers, I’m not going to list them, find them yourself by using your uncensored internet(meant as sarcasm which went above your head judging by your earlier comments).
All of this is OK from a security perspective, if you ask me. Privacy is a different matter, but this is not what was analyzed there.
> When Pegasus news broke, he retweeted a tweet which clearly said Sandboxes are not enough, and new secure language has to be used, which I already mentioned in another article, go check that.
Yes, and? That is 100% correct. Sandboxes are a bandaid fix until memory-safe languages can be used to rewrite the application. Firefox has neither of the two. It has seen some memory-safe language use in its code, but not where it really matters. None of the most attacked components of Firefox are written in memory-safe languages as of yet. Its sandbox always was and still is a joke, so there is also no real mitigation until then.
> If you mean I have to trust madaidan and start using Windows over Linux,
You still aren’t getting it, are you? They analyzed the exploit mitigations that are in place, and here Windows beats desktop Linux. Windows hacks are much harder to realize when comparable components are attacked. Yes, Windows has numerically more malware, but this is because it is the more attractive target and receives much more scrutiny, furthermore the number of security issues tells you nothing about how hard the hacks actually were.
Linux’s security is basically security by obscurity, it is hardly used, and thus an unattractive target. That’s all there is to it. Its exploit mitigations are fairly weak and if it suddenly had a relevant market share, hackers would have a field day.
> stop using LineageOS,
From a security aspect? Of course! You had to unlock the bootloader (without an option to re-lock it, which e.g. GrapheneOS allows) and you possibly rooted the phone etc. These actions weaken the overall security of the phone.
> Firefox,
Firefox has obvious security issues. madaidan and Micay have already cited them, no need to rinse and repeat.
> VPNs
If the owner of the VPN is malicious, you are screwed. Also, you still don’t understand that they strictly analyze the security aspects of it on the website.
> and more importantly give preference to Smartphones over Desktop
Huh? Source? Where was that said?
> then yeah I know how much respect that guy deserves, spoiler alert – nothing.
How much respect do you deserve for failing to get what they want to convey and for constantly misrepresenting them?
> disconnected you’re from ground reality about many products and services ;-)
I don’t think I am disconnected, haha. I am taking allegations against a type of industry seriously that has often been shown to be infested with malicious parties stealing user data despite public promises to the contrary. I am also monitoring reactions to said allegations, and if the reaction is simply the accused VPN company hiding the evidence, then I can draw the correct conclusion from that – you can’t, but that’s not my problem.
@Iron Heart
You can’t read properly, good for you.
I have already said enough about Nord and Express and since you didn’t mention anything new, no need to address them again. About ExpressVPN, first you said their servers were secure back in 2017, good you got that right, and second you asked who are their owners? I don’t know I never used that VPN, but I know whether to trust a random youtuber with VPN clickbaits. Who’s Express owner? Find yourself, I don’t use that service, never have and quite frankly don’t care.
I was wondering where do you get all this shitload to write about Proton, so I did a quick research(research part meant as a sarcasm so you can understand it was meant as sarcasm). I searched ProtonVPN Tesonet on Google! here’s the link – https://www.google.com/search?q=protonvpn%20tesonet. And not to my surprise, I found all the links you have posted in this thread at first page of search results. Anyway point is even your latest link was there on the main page, but then I found one useful link – https://github.com/privacytools/privacytools.io/issues/928. In this link all your theories about Proton are dismissed, ironically all your Proton trashing links were there too which were then dismissed in a good way – lacking evidence. In the end for all your trash talk I know everything, you were nothing but an idiot and luckily that GitHub thread has everything to answer. That thread is infact two years old. I should have figured this out earlier that, not that your pathetic theories links are all trash which they are, but that some good folks have already dismissed them, back in 2019.
God! only if I had done this bit earlier, searched ProtonVPN Tesonet on Google(I don’t use Google but maybe from now, to answer your stupid theories I might as well use Google to save my precious time arguing with a troll), then I wouldn’t have to write multiple comments here. In the end as proved two years ago, those theories were a joke, same as you.
I hope this topic is closed for now, and I will only respond if you have something meaningful to share, if you still want to trash Proton without any evidence go ahead, but only after reading the comments in GitHub thread.
Have to say you proved yourself an amateur, so much for your wounded pride.
“> and maybe alternatives too which are better if you can, once my VPN subscription ends, I’ll check them.
The Privacytools.io list is otherwise solid, I just think that their ProtonVPN endorsement is questionable.”
Good from you responding in a nice way. But my question was which VPN companies have verified their claims and other stuff you wrote against Proton, good luck mentioning any names.
“All I am saying is that it is great that these companies rat each other out. It is to our benefit.”
To some extent I can agree, but Big Tech also doing this would be nice.
“Mozilla themselves have noticed it, hence their attempt to implement real site isolation and memory-safe language.”
I was expecting this, just few words when Rust will be fully developed, certain security experts would be using it including Daniel Micay. Of course afterall they would want to say hey look I made Rust.
Good of you to mention Fission, just one thing it will enhance the working of Firefox, not fixing a broken Firefox. Those two things are different, of course to prove Broken part, in other words, Firefox is insecure now, you’re welcome to name some real world incidents.
“You do realize though that many of the security issues Mozilla fixes monthly were actively exploited before, right? Sometimes to the point where they had to provide hotfixes, you know, the x.y.1 emergency updates following major releases.”
And what does this has to do with Firefox is insecure? Is Firefox the only software to deal with these sort of things? Seriously some lines you write are dumb. As if Chromium doesn’t list issues fixed.
Plus when you mention Firefox is insecure, you mention sandbox and memory exploit thing, of course name some real world incidents of them things exploited if you can, and that’s what I meant when I said Daniel Micay isn’t the only security expert in the world. Seriously you copy pasted that line and in the reply wrote stuff which has no connection to it.
Also every software publishes issues fixed monthly, so what does that mean? Since you think its exclusive to Firefox, I had to tell you that – every software does that. Chuckle!
Though about Daniel Micay I would add one thing – He is the only security expert I heard of, who clearly said F-Droid is insecure, which is laughable, to find that, check his twitter.
“What Micay says about extensions not being fail-safe is self-explanatory. No third party component using the browser’s APIs is fail-safe. Gorhill has no clue about security, otherwise he would have been more considerate in his rants about the removal of the webRequest API which gives fairly dangerous privileges to extensions.”
You didn’t read the content of link of yours, even Daniel Micay didn’t directly questioned Gorhill and more importantly he didn’t dismissed his words, but since you are an idiot, you have to write Gorhill has no clue about security. I can only imagine how much clue Brave team has about security, who in their blog praised uBO and Gorhill. Seriously man stop saying things which even you know are false.
“…but at the same time, you were never able to prove him wrong. :D You just choose not to look at the evidence, like a child. This is not a proper response.”
Yeah I have to prove Daniel Micay wrong HAHAHAHA, even though he passionately says Firefox is insecure and never shared any proof. You are just humiliating yourself by writing this – you were never able to prove him wrong. One thing I would say I’m still laughing.
“All of this is OK from a security perspective, if you ask me. Privacy is a different matter, but this is not what was analyzed there.”
Yeah you’re right, in your mind it is ok, good to say that. Atleast now I know you can’t be taken seriously :-)
“Yes, and? That is 100% correct. Sandboxes are a bandaid fix until memory-safe languages can be used to rewrite the application. Firefox has neither of the two. It has seen some memory-safe language use in its code, but not where it really matters. None of the most attacked components of Firefox are written in memory-safe languages as of yet. Its sandbox always was and still is a joke, so there is also no real mitigation until then.”
Any real world examples of exploiting Firefox insecurity to prove your claims, other than another Daniel Micay reddit comment obviously?
I see you’re justifying what madainwhatever guy said, good luck. About where did he said that? “The desktop security model is very broken. It was not designed with security in mind — security was only a poorly implemented afterthought. However, there are some operating systems that are less bad in this regard. If you can, stay away from desktop and stick to mobile devices.” Link – https://madaidans-insecurities.github.io/security-privacy-advice.html. Good luck explaining that along with other laughable things.
“Hackers would find a field day” when mentioning Linux security, here’s a fact – I’m the chief of Hackers’s association. When Linux will replace Windows, I’ll order my crew to attack it, until then I’m waiting. Sorry I had to blow my cover.
“There are rumors that ProtonMail was developed under CIA supervision:”
Fun actual fact, not a rumor: The code that TOR is based on was created by US military, the Navy to be exact. And if NSA is somewhat competent they probably have lots of nodes. Just saying…
I have had Nord for a few months – mainly to use UK streaming sites from Spain and is working well for me.
BBC Sport website says 404 when on UK server but iplayer runs great!