Chrome 63 notifies you of Man-in-the-Middle issues
Google plans to launch a new security feature in the upcoming Chrome 63 browser that notifies users about Man-in-the-Middle (MITM) issues.
MITM is best known as a method to attack user systems by intercepting and manipulating traffic. Many security programs with firewall and browsing components do use similar functionality to inspect encrypted traffic.
The security feature that will launch in Chrome 63 displays a notification to users if (legitimate) security software causes issues on the system because of its interference with encrypted SSL traffic.

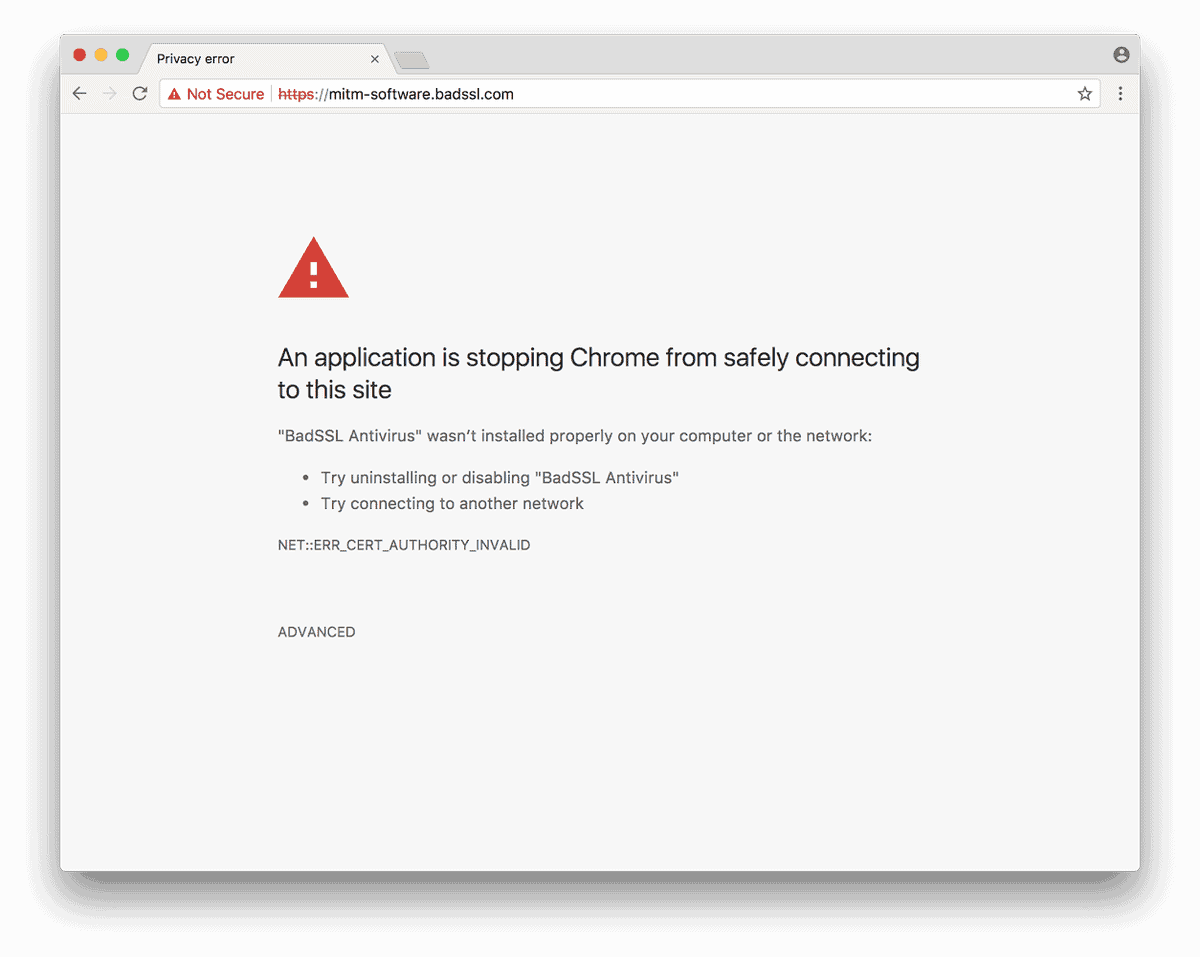
Google Chrome displays a notification if it detects Man-in-the-Middle interference with connections to secure sites.
The notification reads:
- An application is stopping Chrome from safely connecting to this site.
- "Name of Software" wasn't installed properly on your computer or your network.
- Try uninstalling or disabling "Name of Software"
- Try connecting to another network
Chrome displays the name of the program that is responsible for the behavior, and suggests to uninstall or disable it. An update may help as well if one is available that resolves issues with the behavior, or to disable the functionality in the security program that taps into connections if such an option exists.
It is important to note that Chrome will distinguish between MITM issues caused by "legitimate" software installed on the system, and MITM attacks. Chrome displays the new notification for the former only, while it will show a SSL error page just like before for the latter.
Sasha Perigo, the project lead of the feature provides the following information on the workings of the feature:
For this error page we say a user has "misconfigured" software if they don't have the root required for the MITM program.
We check the error code the certificate validator threw, and check fields on the missing cert to see if it's MITM software.
This error page will only be shown to users who were already seeing SSL errors. If you're not seeing SSL errors right now, you're all good!
She confirms that there is a chance of false positives, and that a team monitors the functionality and will adjust it if the need arises.
Chrome 63's planned release date is December 5th, 2017. The feature is part of any version of Chrome that is already on version 63. Only Chrome Canary is on version 63 right now, which means that the following works only in that particular version of Chrome and not in Dev or Beta channel builds right now.
Tip: load about:chrome to check the version of the web browser. If you see version 63, the feature is available.
The new feature needs to be enabled manually in Chrome Canary right now. You don't need to do this once it lands in stable, as it is then part of all versions of Chrome automatically.
You need to launch Chrome with the parameter --enable-features=MITMSoftwareInterstitial.
On Windows, you'd simply right-click on the Chrome icon on the taskbar, then again on Google Chrome Canary when the menu opens, and there on properties. A single right-click is sufficient if you right-click on the Chrome shortcut on the Desktop or in the Start Menu.
Append --enable-features=MITMSoftwareInterstitial to the end of the target field, and make sure there is a space between the previous value and the new parameter, e.g. "C:\Users\Martin\AppData\Local\Google\Chrome SxS\Application\chrome.exe" --enable-features=MITMSoftwareInterstitial.




















All Chromium-based (including Chrome) browsers are useless – no option to disable JavaScript globally not just individually sites.
I wonder how this will act with corporate firewalls that are basically doing MitM attacks on their user’s connections to enforce content filter and protect against pesky viruses that come down SSL connections to end users?
So basically if you were already seeing SSL issues, you’ll be affected. How often does that happen?
This implementation isn’t really designed for MITM in the first place, the real reason is that some AV software in the past implemented their AV Firewall/SSL not the right way, then you often saw the error and most of the time the server owner/webmaster got blamed for this. In fact if it’s bad implemented such tunnels are weak and vulnerable against attacks and side-channel interception.
So since Chrome 63 you can now add “–enable-features=MITMSoftwareInterstitial” param to see the name of what is intercepting the connection.
https://chromium-review.googlesource.com/c/chromium/src/+/656507/4
However, this isn’t a new error code it’s just an warning/hint as Sasha Perigo tells us (https://twitter.com/sashaperigo/status/906263091624591360), the developer of this new ‘feature’.
I wonder how long it takes for Mozilla to steal … oh I mean ‘adapt’ this feature. :-D
I seem to recall a couple of Firefox extensions that check for MitM attacks. They’ve been around for a while, I think.
The reason this is useful is that many antivirus actually mess with the secure connection and make it less secure when it finally leaves the computer. If I remember correctly an written by some security expert a few…months ago, maybe a year.
Don’t take this at face value, double check what I’m saying if you’re interested or dismiss it otherwise, because it’s too vague.
Won’t the new feature in Chrome 63 regard Proxy or VPN connections as Man-in-the-Middle interference ?
I don’t think so generally speaking.