Windows 10 Threat Mitigation advancements
The new Windows as a Service model of Microsoft has helped Microsoft implement new threat mitigations and protection against threats faster than in the previous model that saw new releases happen every three years.
Windows as a Service evolves the operating system constantly, or more precisely, twice a year with feature updates around March and September of each year.
A new blog post on Technet compares the old release model to the new in regards to threat mitigation, and highlights improvements and advancements that Microsoft made since the release of Windows 10.
Windows 10 Threat Mitigation advancements

The author compares exploitation a decade ago to exploitation techniques that are used today. Microsoft's take away from that was that the faster release of Windows 10 feature updates would reduce the impact that new exploitation techniques had on the Windows population.
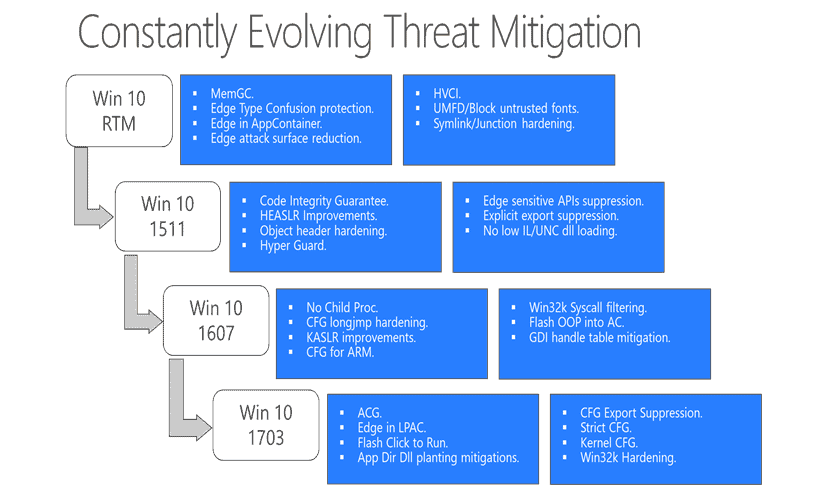
The graphic that you see above shows new threat mitigation techniques that Microsoft added to the first four versions of Windows 10.
The blog article highlights important mitigations afterwards:
- User Mode Font Driver (UMFD) -- A feature implemented in the original release version of Windows 10. It moved font processing into an App Container in user mode. Additionally, administrators may disable the processing of untrusted fonts for a process using the Process Font Disable policy. (see Block programs from loading untrusted fonts in Windows 10)
- Win32k Syscall Filtering -- The Win32k subystem is the number one target to escape the sandbox because of its large attack surface and its 1200 APIs. The feature limits the list if APIs that can be targeted.
- Less Privileged App Container (LPAC) -- LPAC is a restricted version of App Container that denies access by default.
- Structured Exception Handling Overwrite Protection (SEHOP) -- Designed to block exploit techniques that use the Structured Exception Handler (SEH) overwrite technique.
- Address Space Layout Randomization (ASLR) -- This technique loads dynamic link libraries into random memory address space to mitigate attacks that target specific memory locations.
- Heap protections -- Windows 10 protects the heap in various ways, for instance by using heap metadata hardening, and through heap guard pages.
- Kernel pool protections -- Protects the memory that is used by the kernel.
- Control Flow Guard -- Needs to be compiled into software programs. Microsoft added this to Edge, Internet Explorer 11 and other Windows 10 features. Control Flow Guard detects if an attack changes the "intended flow of code".
- Protected Processes -- Protected processes are important or system critical processes. Windows 10 prevents untrusted processes from tampering with protected processes. In Windows 10, security applications may be put into the protected process space.
- Universal Windows apps protections -- Windows Store apps -- UWP and converted Win32 programs -- are vetted before they are made available.
- No Child Proc -- Designed to block code execution by launching child processes.
Microsoft mentions the main objectives when implementing threat mitigations into Windows 10 afterwards:
Reducing the attack surface of Windows Platform
Takes soft target out of the picture
Eliminates existing exploitation techniques so that new techniques need to be found.
Reducing impact of vulnerability by isolation.
Make overall exploitation harder and expensive
Closing Words
Windows as a Service guarantees faster deployment of exploit mitigation techniques according to Microsoft. While that is probably true for some techniques, others may have also been added to previous versions of Windows as updates.
Now Read: Windows Defender Exploit Guard - Native EMET in Windows 10Â (via Born)


















Write news about telemetry, everyone is freaking out and you get ~100+ comments, write something which actually improve the security of the entire OS/applications, only two comments … Blows my mind. I really like that WD finally becomes an good all-in-one solution, the EMET integration is a big step forward imho.
When MS now cut some deprecated things off, like Kerberos it really would be the ‘most secure OS ever’ as they promised, cause mostly when I look at the CVE’s it affects already known holes which exist since years or is drive-by. However my point is that the work here is really well done and I’m really looking forward to see more focus on the security related aspect. That said, MS should generally focus more on removing obsolete things or made more toggles for opt-ins, so that there is a less risk for malware, because the more you pre-install the higher the risk/chance is that you get vulnerable because you might use outdated software because you not maintain it regularly or that it comes by design already with a risk.
What I really would like to see (together with some other people) is a better firewall interface, which allows a better integration, similar like WFC I guess that would help a lot. Especially against ransomeware which wants to load the external payload from unknown/untrusted resources, which easily could be prevented by restricting the internet. But maybe we see something for RS 4?! Who knows.
Thank you very much for including the link to the entire article. Mr Brinkman, your site is a great source for info technology.