Permadelete: remove files securely on Windows PCs
Permadelete is a new open source program for Microsoft Windows devices that you may use to remove files securely from the PC.
The delete operation on Windows does not really do what the majority of users expects it to do. Instead of removing the contents of a file and its reference from the system, delete simply removes the reference but leaves the contents on the disk.
The parts of the disk are set to write again, so that data may overwrite the deleted file eventually. Until that is the case though, file recovery tools may recover the deleted files completely or partially.
We have reviewed several secure file deletion programs in the past: there are FileWing Shredder and Hardwipe, Free File Wiper, RightDelete, and the excellent Eraser to name just a few.
Not all of these programs work in the same way. Eraser for instance overwrites the free disk space so that deleted data cannot be restored anymore.
Update: The lead developer of Permadelete added information to the GitHub project repository as a result of our review. It explains core issues that we had with the program. First, the Internet connection on start is an update check. Second, for SSDs, files are merely deleted but not overwritten.
Permadelete
Permadelete is a new entry in the niche. It is an early version of an open source program for Windows. It does require Microsoft .Net Framework 4.5, needs to be installed, and tries to establish a connection on start which you may want to block as it is not clear why it does so (maybe update check).
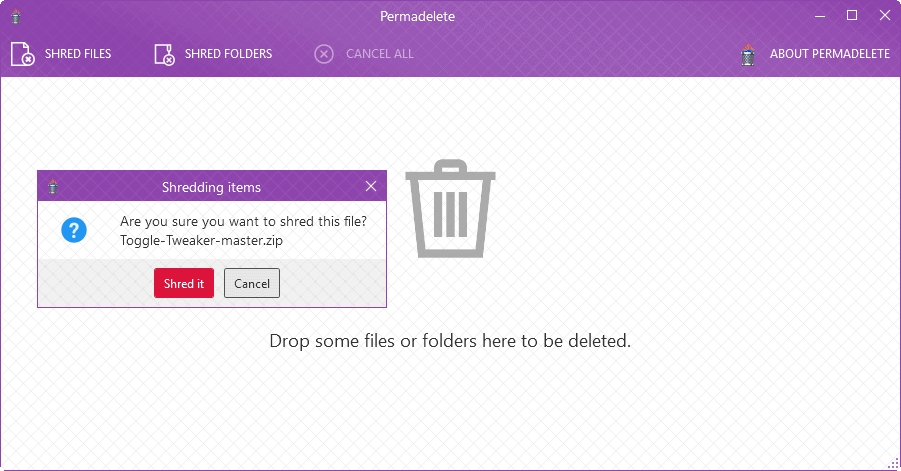
The interface of Permadelete is compact. You may drag and drop files or folders to the interface to have them deleted securely, or use the shred files or shred folders icons instead to use a file browser for selecting files or folders.
The application displays an option during installation to add it to the "send to" menu of Explorer. You may use it to send files or folders directly from Explorer to Permadelete.
The program displays a security prompt whenever you drag something to the interface. You need to accept it by selecting "shred it" to start the secure deletion process.
There is nothing more to the program other than that right now. Permadelete overwrites the locations the dropped files or folders are stored on with random characters.
The program lacks any options, and what weights more heavily, returns no status information after the shredding. While it displays the "are you sure" prompt when you drop files to the interface, it does not return anything after the process completes.
Another issue that is not addressed right now is that it makes no distinction between platter-based hard drives and Solid State Drives. Secure delete tools don't work reliably with Solid State Drives, and programs like Permadelete should at least inform users about that when files or folders are dragged from SSDs.
Closing Words
Permadelete is a work in progress. It works considerably well for files stored on non-Solid State Drives, but could use feedback after the deletion process, and an option to turn off update checks.
Now You: How do you handle deleted data on your devices?



























Using Permadelete for several months with no apparent problems, conflicts, etc. Not a tech so unable to determine if the file “shredded” is overwritten in a manner to ensure the data is gone for eternity.
Assuming the program works due to lack of negative comments at various Web sites. Appears it automatically updates since my program declares it is the newest 0.6 build.
Since Permadelete is not butting heads with other programs and causing mayhem I am a happy fellow and will continue using the program when needed. Kudos to the creator and may he become the next Bill Gates or whoever is deemed worth emulating.
Hi all! a new version of Permadelete is out that add more customization and control!
https://github.com/DevelopersTree/permadelete/releases
Thanks for the review Martin! I see that it has started quite a discussion :) if anybody needs more information about how Permadelete works, please take a look at this wiki page: https://github.com/encrypt0r/permadelete/wiki/How-Permadelete-works
Hi encrypt0r,
Is portable (non-install) version available? how do you turn off auto update?
Hi Claire! I have just added a portable version to download, you can find it here: https://github.com/encrypt0r/permadelete/releases/tag/v0.5-beta (scroll down a bit to the “Downloads” section)
As for turning off auto update, I am afraid currently there is no way. But would you mind telling my why is it required? If there is a good reason, I will try to add a way in the next release.
Should be portable. No need to bloat Windows PCs with installations.
Hi ilev! I have just added a portable version to download, you can find it here: https://github.com/encrypt0r/permadelete/releases/tag/v0.5-beta (scroll down a bit to the “Downloads” section)
Is Eraser still any good ? I still use Eraser 5.8 something because I figured a long time ago that Eraser 6 sucked, though I don’t know why. Now they’re at 6.2. Is it any good ?
I don’t remember if the quality of the erasure was worsened, but bad things included a perma-running service, much slower erasure time, a program generally both slower and more intrusively installed in windows instead of an on-demand thing.
Any changes on that front ?
Same thing with Sandboxie. Worsened at version 4 long ago. I don’t know what it’s worth nowadays (v5.16).
I cannot say, have not looked at the programs for a while. Today, I stumbled upon an interesting offer for Sandboxie though which got you a five computer lifetime license for less than 15 per computer.
TRIM has nothing to do with ‘secure deleting’ files. SSD also need (a lot of more) secure deleting mechanism/tools since it’s harder to delete stuff on a ssd.
“With modern solid-state drives, the drive’s firmware scatters a file’s data across the drive. Deleting a file will result in a “TRIM†command being sent, and the SSD may eventually remove the data during garbage collection. A secure delete tool can tell an SSD to overwrite a file with junk data, but the SSD controls where that junk data is written to. The file will appear to be deleted, but its data may still be lurking around somewhere on the drive. Secure delete tools just don’t work reliably with solid-state drives.”
Trim is just the trigger to maybe (MAYBE) delete files or not and even with in 90% of all cases the files can still be recovered.
The problem is that because the nature of NAND flash memory, SSD’s can’t be directrly overwrite data which means repeatedly overwriting a file before deleting it will not securely erase it. What helps are ATA secure erase commands. They trigger a process which also delete all over-provisioned NAND regions. The problem here is that not all drives supporting this command.
If you use encryption ensure it deletes the key and then you be ‘more secure’ because no matter what, the data can’t be recovered.
Nonsense to say it politely, try recovering a file on e.g. a Samsung SSD. If you are fast enough you can even see it deteriorate. Black stripes over a jpeg for example. After 10 seconds it’s completely gone. Overwritten with 0’s as that is the state of an emtpy cell. You may be right for some old low-tech models. But new firmwares of current gen drives, even old ones like the EVO 840 give short shrift to deleted data.
This will reduce SSD lifetime.
SSDs by design don’t need secure file erasing:
http://articles.forensicfocus.com/2014/09/23/recovering-evidence-from-ssd-drives-in-2014-understanding-trim-garbage-collection-and-exclusions/
(If Martin is okay with me posting this link.)
HK-Rapper, that is a really interesting link, but I draw very different conclusions from you based on what I read there. Far from saying SSDs don’t need secure file erasing, the article itemizes a number of scenarios that can make SSD data easily recoverable. It turns out that these scenarios are pretty common occurrences, meaning a large proportion of computer users can expect to be affected.
Additionally, all this discussion of SSD deletion assumes you’re not using a journaling file system. If you are (and most people are at this point), then this is a whole other discussion.
I think at this point the only truly “secure” way of deleting data on SSD is to keep the data encrypted and then delete the encryption key when you are ready to destroy the data. This is something you could do if you were planning to sell or dispose of your disk, for example.
Always ok if the linked resource offers useful information. This one does, so thanks for that ;)
You should not run this on a SSD anyway as it won’t delete the data securely. Lifetime is only really reduced if you run a first or second generation SSD.