RouterCheck for Android tests your router's security
How secure is the router your computer and devices are connected to whenever you are using the Internet? The free Android app RouterCheck tries to find that out by running a series of tests to reveal security issues or even vulnerabilities affecting the router.
Most home computer users connect to the Internet using a router or modem making these devices the gateway to the Internet.
What many don't know is that these devices may be as vulnerable to attacks as computer systems.
Kevin published a guide recently about securing a wireless router properly recommending the use of a new strong admin password for it, the right type of encryption for wireless connections and other best practices.
But security goes even beyond that. For instance, unless routers are configured to update automatically when new firmware is released, they may operate using old firmware that may make the device vulnerable to attacks.
RouterCheck is a free app for Android that scans the router for known vulnerabilities but also for common issues like open ports or an insecure admin password that can be fixed immediately by the user.
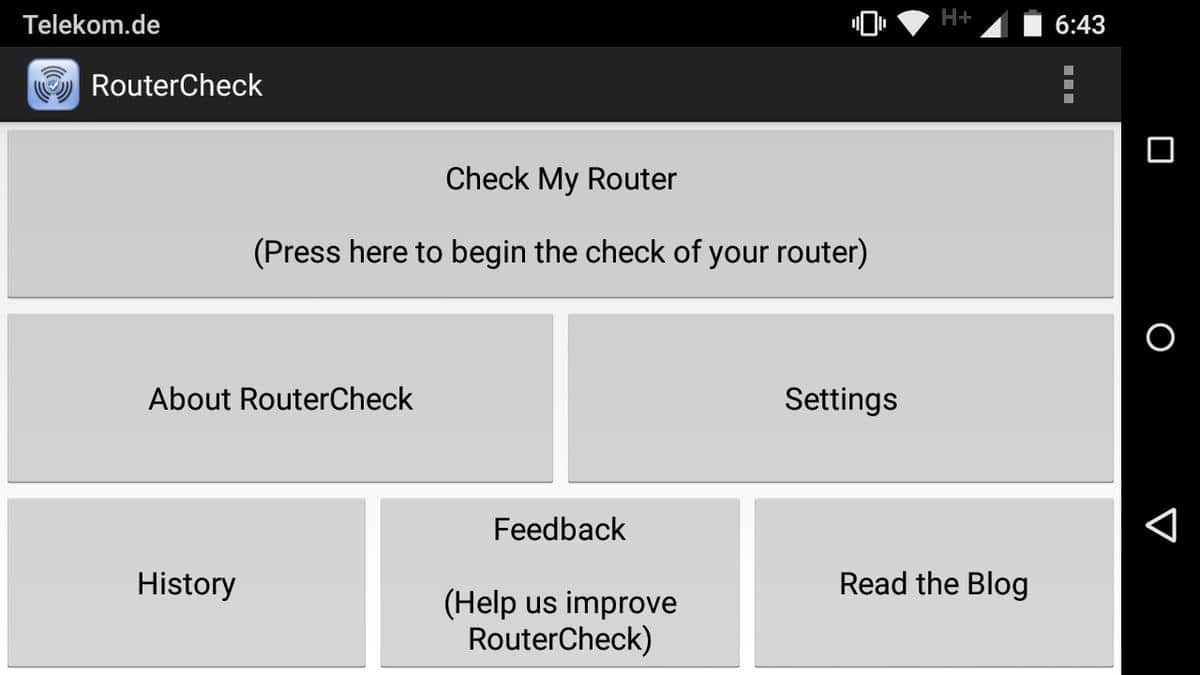
Tap on the "check my router" button when the main interface has loaded to start the test. You need to confirm that you are the owner of the router or home network before you can run tests.
The test itself won't take longer than a minute to complete and a detailed report is presented to you in the end.
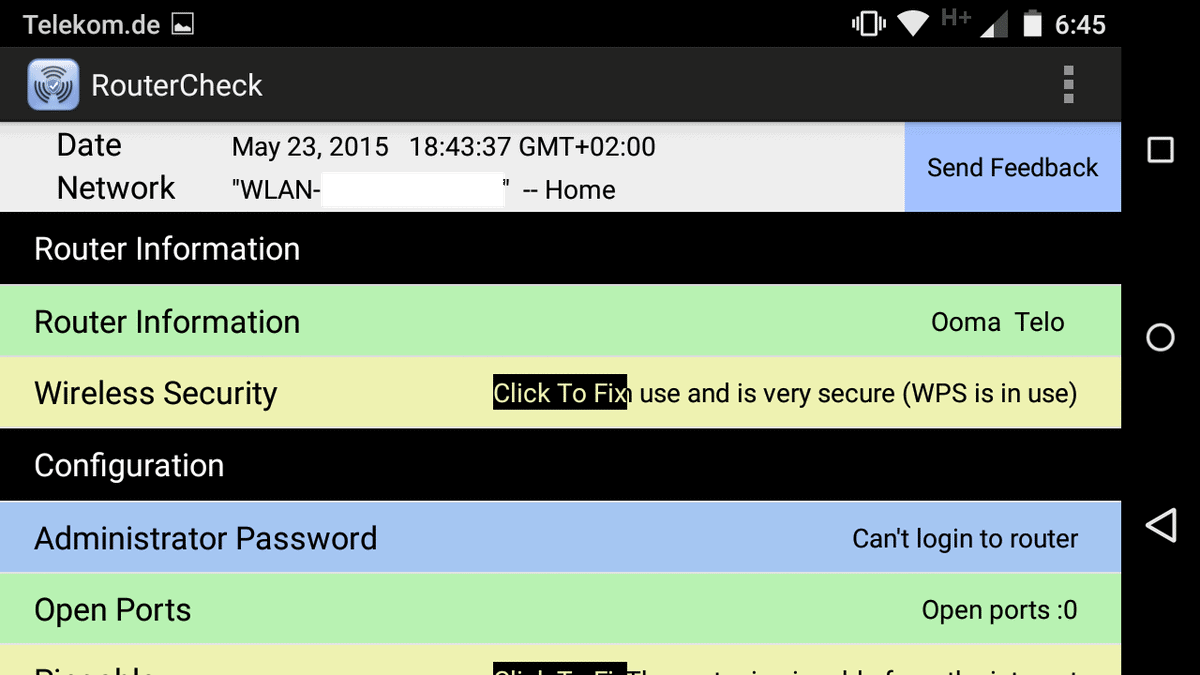
The report lists the finding of the tests and you may want to go through all of them one by one to fix issues found by the app.
Results are color coded: green means ok, blue that the test could not be performed, yellow issues that you may want to address and there may also be red for severe issues but I could not confirm that.
An option to fix the issue is displayed for each yellow issue in the interface. For instance, you may receive a warning that your router is pingable. If you click on the fix button you are taken to a page that describes why that is a problem and how to fix it.
It needs to be noted that the instructions are general in nature as routers may use different menu names and navigational structures. The information provided are extensive on the other hand and should help even inexperienced users correct it.
The app checks several important values and preferences including the admin password, the type of wireless security used (if any), and whether the router is vulnerable to a set of known vulnerabilities (currently three in total).
The explanations and instructions provided help understand why something is an issue, why it is better fixed and how that is done.
Verdict
RouterCheck is a useful application for Android that checks whether your router is configured properly security-wise.
While you may not have an issue with all issues the app recommends to fix, the vulnerability check alone makes it worth running at least once.

























Is this thing just harvesting router admin passwords?
Sericon Technology has no contact info…
Jennifer Paton Smith is listed as CEO and Founder but on her Linkedin page she calls herself the Technical Writer…
Also noticed she reviewed her own app…on the Google Play page…5 stars natch…
No way, RouterCheck is totally legit. And to prove it, I’m just going to need your router admin password…
Comment of the month ;)
I’m Sander Smith the founder and president of Sericon Technology
Jennifer is a VP and also a founder
Contact info is on the website http://www.routercheck.com/contact-us/
or just write to us at beta@RouterCheck.com
We’re in Toronto, Canada
Are we stealing your info?? So many people ask us this, we even have a webpage to deal with it:
http://www.routercheck.com/are-we-really-the-hackers/
No we are not stealing your info. People who steal your info do not tell you what your vulnerabilities are and then tell you how yo fix them.
If there’s anything else you’d like to know, I’d be glad to discuss it.
Why is she reviewing her own app on the Google Play store?
All reviews have since disappeared except two…imagine that…LOL…
Regarding routers security :
KCodes NetUSB: How a Small Taiwanese Software Company Can Impact the Security of Millions of Devices Worldwide
Today the SEC Consult Vulnerability Lab released an advisory regarding a vulnerability in a software component called NetUSB. This post intends to give some background information about this vulnerability.
NetUSB is a proprietary technology developed by the Taiwanese company KCodes, intended to provide “USB over IP†functionality. USB devices (e.g. printers, external hard drives, flash drives) plugged into a Linux-based embedded system (e.g. a router, an access point or a dedicated “USB over IP†box) are made available via the network using a Linux kernel driver that launches a server (TCP port 20005). The client side is implemented in software that is available for Windows and OS X. It connects to the server and simulates the devices that are plugged into the embedded system locally. The user experience is like that of a USB device physically plugged into a client system. It’s worth noting, that the NetUSB feature was enabled on all devices that we checked and the server was still running even when no USB devices were plugged in!
We initially found the NetUSB kernel driver on a TP-LINK device and decided to spend some time on it. To establish a server-connection, a simple mutual authentication check needs to be passed. The authentication is entirely useless as the AES keys are static and can be found in the kernel driver as well as in the client software for Windows and OS X. As part of the connection initiation, the client sends his computer name. This is where it gets interesting: The client can specify the length of the computer name. By specifying a name longer than 64 characters, the stack buffer overflows when the computer name is received from the socket. Easy as a pie, the ‘90s are calling and want their vulns back, stack buffer overflow. All the server code runs in kernel mode, so this is a “rare†remote kernel stack buffer overflow.
It turns out, that not only TP-LINK uses NetUSB in their products. We found references to 26 vendors in the file “NetUSB.infâ€, which is part of the client driver setup for Windows. It is likely, that these vendors have licensed the NetUSB technology and are using it in some of their products. Our advisory contains a list of affected devices, where SEC Consult has verified the vulnerability within the firmware. Unless otherwise stated, the list is incomplete regarding other affected vendors…
http://blog.sec-consult.com/2015/05/kcodes-netusb-how-small-taiwanese.html
The only yellow I got was for DNS, where it apparently didn’t like 192.168.1.1 as local DNS server. However, I did not understand what it wanted me to do. I don’t have 192.168.1.1 anywhere in my Linksys settings that I can find and it isn’t clear what they are suggesting I do.
Everything else was green except for the blue warning that it could not login to my router (which is good since I changed the password from the default long ago).
The real problem with this router (a Linksys EA2700) is that the firmware hasn’t been updated in two years or so and likely won’t ever be updated given that Linksys was sold to Belkin a while back.
Try DD-WRT. That’s what I use and I like it. There hasn’t been a stable release in years, but it gets regular beta updates. It’s more secure than a stock firmware, and you can also get additional features (e.g. mine didn’t have repeater function with stock firmware, now it does).
I couldn’t find it using their search function. Does it being beta mean that I would have to deal with many problems?
I think it does. http://download1.dd-wrt.com/dd-wrtv2/downloads/betas/2015/05-19-2015-r26947/linksys-ea2700/
Unfortunately, DD-WRT doesn’t have a version for the Linksys EA2700.
CyanogenMod’s Privacy Guard says this: RouterCheck would like to access your location.
Also, this app failed to detect my Wi-Fi security (it says it’s disabled, even though it clearly is not), and it says my DNS is set to Local DNS 192.168.0.1, even though my DNS is set to OpenDNS actually.