Lock-down your Windows system with Simple Software-restriction Policy
Simple Software-restriction Policy allows you to harden Windows machines by adding Linux-like execute permissions to them.
Windows by default does not prevent software from being run from any location on the computer which malware and unwanted software exploit.
For instance, programs may be run directly from USB Flash Drives, download folders or system temp directories.
Simple Software-restriction Policy changes that by locking down that functionality on the system. It ships with a default rules file which is a good start but may need tweaking.
After installation, you will notice that you cannot execute files anymore from download folders or most folders on the system for that matter.
It is still possible to run software from select locations, the program files folder for instance but executions from most locations are blocked.
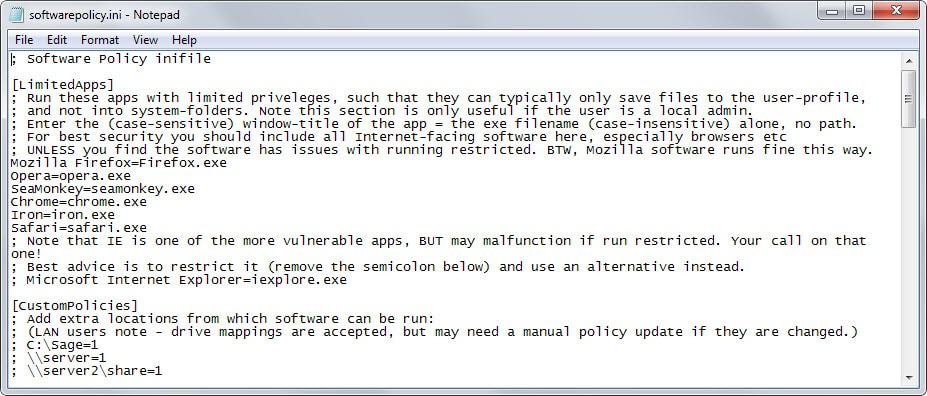
The program's functionality is defined in the softwarepolicy.ini file. Open it in any plain text editor to fine-tune its behavior. This is not as intimidating as it sounds as the syntax is simple and instructions are provided for each entry.
Here is a short list of important sections in the ini file that you may find useful:
- LimitedApps - This is only useful if the user is a local admin. If that is the case, it ensures that the programs listed in this section are run with limited privileges. Web browsers such as Firefox, Opera or Chrome are listed in this section by default. In addition, you may define when these restrictions apply (when the app is locked down, always, never).
- CustomPolicies - Use this section to define locations on the computer or network where software exeuctions are not blocked in.
- AdminMenuPasswordLevel - Enable this to password protect the unlocking functionality of the application and the software#s configuration.
- SoftwarePolicy - Defines extensions that are limited by the program. Includes many executable file types and important file types such as exe, bat or reg by default.
- AddRootDirs - Block or allow programs to run from root directories, e.g. c: or d:
- AddTempDir - Block or allow programs from running from temporary directories
- IncludeDlls - Whether to prevent the launching of dynamic link libraries as well.
- AlwaysAllowSystemFolders - Determines whether system programs can be launched at all times.
- Disallowed - Add paths or executable files that should never be run on the system.
The two main features of the program are to lock-down the execution of programs on the system to safe areas and to run specified programs automatically with limited privileges.
The program ships with an unlock option with disables its protection which may be useful when certain applications or updates won't run properly when the application is enabled. A folder full of portable applications for instance may be a good target for an exemption as you won't be allowed to run the programs on the Windows machine otherwise.
Depending on how you are using your system currently, you may need to change certain behaviors after enabling Simple Software-restriction Policy's protection. It is for instance no longer possible to run downloaded executable files directly from the download directory unless you make modifications to the default configuration.
Verdict
Simple Software-restriction Policy hardens Windows systems by limiting the locations that applications can be run from. In addition, it is allowing you to run certain programs with limited rights.
It is a useful program not only for your own systems but maybe also for systems of relatives or friends who are not computer-savvy.
























Nice little utility to have laying around, it’s light, useful and Open-source what more could you ask for really. Thanks Martin.
Portable Version hasn’t been update in awhile, so its the setup for now.
So how does it work? Windows offers something like that through group policies.
Will this program just use the windows feature with a better GUI or does it try to hook the Windows API by itself to (try to) prevent stuff from running? If the second one, what does it hook and how does it try to prevent it from starting.
btw you could do an article on how to run for example Firefox under a differnt user with limited rights and no rights to write anywhere but this user folder (and not on other partitions/hdds for example). Similar topic.
It uses the operating system functionality Software Restriction Policies. See http://softwarepolicy.sourceforge.net/manual/howitworks.php for more details.
Doesn’t Online Armor already do this?
if you use Online Armor you should read this
Emsisoft Online Armor support roadmap
http://blog.emsisoft.com/2015/03/31/emsisoft-online-armor-support-roadmap/
thank you Martin this looks very usefull
Thanks
:)
No, one with an active AV needs this, this is only for people without Firewall (with an HIPS) or an AV without HIPS or what watch starting processes. This peace of software is an relict from Windows XP days, but recently got only an compatibility update for Vista/7.
I don’t see any argument of this software to use, because it not restrict system critical components, which means without any additional protection, malware could still execute stuff from non limited folders. An AV which watch all stuff is much more efficient.
You couldn’t possibly be more wrong. This is basically a user friendly version of SRP, which is one of the most powerful anti-exploit tools available in the Windows world.
AV software has nowhere near this level of protections available to it.
http://www.mechbgon.com/srp/index.html
There’s already wayyyyy tooooo manyyyy productivity-sucking restrictions inherent in the newer Windows Oses.
I could definitely get into something like this (not that I need it, but every extra layer of security can only help) since I only have about 5 actual programs installed, and the other 250+ are under D:/Portable/. And of those 250 odd programs, they’re all fully portable and leave nothing behind (excluding using the users %temp%) except for a small handful of non essential stuff in appdata. I think most don’t even need to use anything in system (bar some dependencies).
It’s like Parental Control option Allow and block specific programs but with more fine tuning. I will try it.