Microsoft Security Bulletins For November 2013 overview
Microsoft is about to release this month's security updates and patches for Windows client and server operating systems.
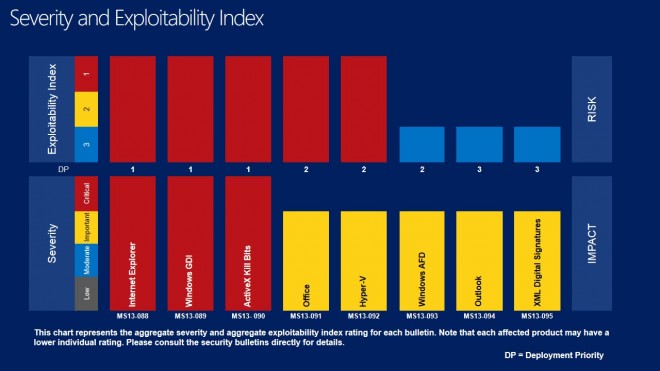
A total of eight bulletins are released this month. Three of the bulletins have received a critical severity rating, the highest possible rating. The remaining five bulletins received a rating of important, the second highest rating.
The eight bulletins patch a total of 19 different vulnerabilities in Microsoft products.
As far as the affected software is concerned, six of the bulletins address issues in Microsoft Windows, and the remaining two vulnerabilities in Microsoft Office.
You find detailed information about the bulletins below. This includes the operating system and Office distribution, deployment suggestions, links to each bulletin to look up additional information, information about non-security updates that were released since the last Patch Day, and finally instructions on how to download those updates to your PC.
Operating System Distribution
The following list displays the bulletin distribution for each client and server operating system that Microsoft is supporting right now.
On the client side, Windows RT takes the crown once again with the least amount of vulnerabilities, followed by Windows 7 and earlier versions of Windows. Windows 8 and Windows 8.1 are affected more than any other client operating system this time.
On the server side of things, all Windows Server versions are affected in the same way by this month's security bulletins.
- Windows XP: 3 critical, 2 important
- Windows Vista: 3 critical, 2 important
- Windows 7:Â 3 critical, 2 important
- Windows 8:Â 3 critical, 3 important
- Windows 8.1: 3 critical, 3 important
- Windows RT: 3 critical, 1 important
- Windows RT 8.1: 3 critical, 1 important
- Windows Server 2003: 1 critical, 3 important, 1 moderate
- Windows Server 2008: 1 critical, 3 important, 1 moderate
- Windows Server 2008 R2: 1 critical, 3 important, 1 moderate
- Windows Server 2012: 1 critical, 3 important, 1 moderate
Office Distribution
Office 2003 is only affected by one bulletin rated important, while all newer versions of Office are affected by an additional bulletin.
- Microsoft Office 2003: 1 important
- Microsoft Office 2007: 2 important
- Microsoft Office 2010: 2 important
- Microsoft Office 2013: 2 important
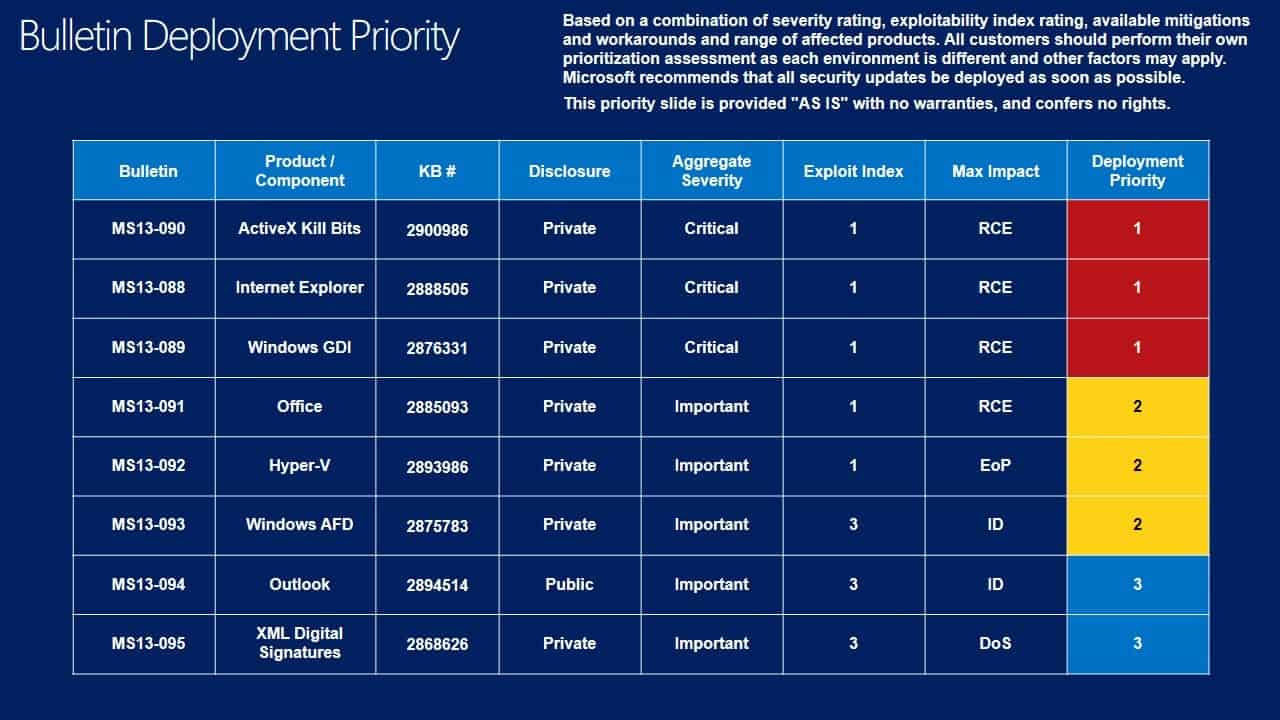
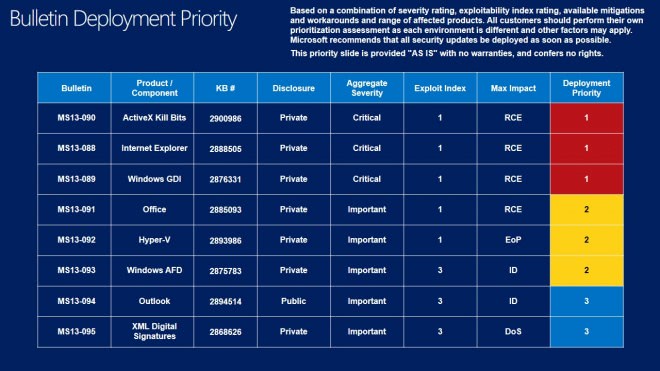
Deployment Guide
Microsoft releases a deployment guide on each Patch Day that offers suggestions for administrators and individual users about the order of deployment of the released Windows updates.
Priorities are assigned to each bulletin using several factors including a bulletins severity rating, whether it is exploited in the wild, and other factors.
While this may not be an issue at all on individual systems, as patches can be installed in a heartbeat on them, companies who do testing before patches are applied may use the information to test and deploy patches in optimal order using the guide.
Click on the images below for a larger version.
- Tier 1 updates: MS13-090 ActiveX Kill Bits, MS13-088 Internet Explorer and MS13-089 Windows GDI
- Tier 2 updates: MS13-091 Office, MS13-092 Hyper-V and MS13-093 Windows AFD
- Tier 3 updates: MS13-094 Outlook and MS13-096 XML Digital Signatures
Security Bulletins
The first three are the critically rated bulletins, the remaining five have all been rated important.
- MS13-088Cumulative Security Update for Internet Explorer (2888505)
- MS13-089Vulnerability in Windows Graphics Device Interface Could Allow Remote Code Execution (2876331)
- MS13-090Cumulative Security Update of ActiveX Kill Bits (2900986)
- MS13-091Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (2885093)
- MS13-092Vulnerability in Hyper-V Could Allow Elevation of Privilege (2893986)
- MS13-093Vulnerability in Windows Ancillary Function Driver Could Allow Information Disclosure (2875783)
- MS13-094Vulnerability in Microsoft Outlook Could Allow Information Disclosure (2894514)
- MS13-095Vulnerability in Digital Signatures Could Allow Denial of Service
Other Security related updates / changes
- MS13-081: Security Update for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2 (KB2862330)
Non-security related updates
- Update for Windows 7 and Windows Server 2008 R2 (KB2830477)
- Language Packs for Windows 8.1 and Windows RT 8.1 (KB2839636)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2882780)
- Update for Windows Small Business Server 2011 Essentials (KB2885313)
- Update for Windows Home Server 2011 (KB2885314)
- Update for Windows Storage Server 2008 R2 Essentials (KB2885315)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2887595)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2889784)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2890140)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2890141)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2890142)
- Update for Windows 8, Windows RT, Windows Server 2012, Windows 7, and Windows Server 2008 R2 (KB2893519)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2897942)
- Dynamic Update for Windows Server 2012 R2 (KB2902816)
- Update for Windows RT 8.1 (KB2903601)
- Update for Windows 8.1 (KB2904594)
- Update for Windows RT 8.1 (KB2905029)
- Windows Malicious Software Removal Tool - November 2013 (KB890830)/Windows Malicious Software Removal Tool - November 2013 (KB890830) - Internet Explorer Version
- Update for Root Certificates for Windows 8.1, Windows 8, Windows 7, Windows Vista, and Windows XP (KB931125)
- System Update Readiness Tool for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB947821) [November 2013]
- Update for Windows 7 and Windows Server 2008 R2 (KB2515325)
- Update for Windows 7 and Windows Server 2008 R2 (KB2647753)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2883201)
- Internet Explorer 11 for Windows 7 and Windows Server 2008 R2 (KB2841134)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2902892)
- Update for Windows RT (KB2885699)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2901549)
- Dynamic Update for Windows RT 8.1 (KB2901630)
- Language Packs for Windows RT (KB2607607)
- Update for Windows 8 (KB2885699)
- Update for Windows 8, Windows Server 2012, Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2890882)
- Microsoft .NET Framework 3.5 Service Pack 1 and .NET Framework 3.5 Family Update (KB951847) x86
- Dynamic Update for Windows 8.1, Windows Server 2012 R2 and Windows RT 8.1 (KB2882342)
- Dynamic Update for Windows 8.1, Windows Server 2012 R2 and Windows RT 8.1 (KB2882351)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2883200)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2884846)
- Dynamic Update for Windows 8.1, Windows Server 2012 R2 and Windows RT 8.1 (KB2890139)
- Dynamic Update for Windows 8.1 and Windows Server 2012 R2 (KB2890660)
- Dynamic Update for Windows 8.1, Windows Server 2012 R2 and Windows RT 8.1 (KB2891213)
- Dynamic Update for Windows 8.1, Windows Server 2012 R2 and Windows RT 8.1 (KB2891214)
- Dynamic Update for Windows 8.1, Windows Server 2012 R2 and Windows RT 8.1 (KB2892082)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2895219)
- Dynamic Update for Windows 8.1, Windows Server 2012 R2 and Windows RT 8.1 (KB2895233)
- Update for Windows 8.1 (KB2895586)
- Update for Windows 8.1 (KB2895592)
- Update for Windows 8.1 (KB2895614)
- Dynamic Update for Windows 8.1 and Windows Server 2012 R2 (KB2898464)
- Microsoft .NET Framework 3.5 Service Pack 1 and .NET Framework 3.5 Family Update (KB951847)
How to download and install the November 2013 security updates
The patches are already available via Windows Update. Most users should receive them via the built-in Windows updating system automatically. Some, who may have configured it to only download patches or do nothing can download them instead from other sources including Microsoft's Download Center.
The option is the most viable for users who want to test the patches before they are deployed on live systems. It can also help save bandwidth considering that updates need to be downloaded only once for deployment, instead of individually for each computer system that needs patching.
These updates can also be downloaded via third party programs that enable you to download all Windows Updates to your system.
Additional information
The Microsoft Security Bulletin Summary for this month is available here. All bulletins are described here in an overview, and with links that you can follow for additional information.
You may also want to check out this month's patch day overview on the Microsoft Security Response Center. Here you may find additional information about the patches.
Advertisement




















KB2830477: Same here, smart card redirection no longer working.
The same here on Windows 7 after Update for Windows 7 (KB2830477) we can’t log into Terminal Server with Smart Card.
I always wonder what Root Certificate updates are, like this one: Update for Root Certificates for Windows 8.1, Windows 8, Windows 7, Windows Vista, and Windows XP (KB931125).
KB2830477—>
according to MICROSOFT:
support.microsoft.com/kb/2830477
this is an update for the RemoteApp and Desktop Connections feature in Windows 7.
while according to SOFTPEDIA:
news.softpedia.com/news/Microsoft-Rolls-Out-Performance-Improvements- for-Windows-7-399741.shtml
These updates (*.msu) provide a collection of performance and reliability improvements that are designed to improve the Windows 7 experience. We recommend that you apply all of these updates as part of your regular maintenance routines. Failure to install all of the packages listed above could leave your machine in an untested state.
whats is going on here:
someone please investigate.
According to Microsoft :
Update for Windows 7 (KB2830477)
Nov 12th, 2013
These updates (*.msu) provide a collection of performance and reliability improvements that are designed to improve the Windows 7 experience.
http://www.microsoft.com/en-us/download/details.aspx?id=41036&WT.mc_id=rss_windows_allproducts
If I remember well from the update last evening, for my Windows 8.1 OS there was in total about 251 MB to be installed. Quite a large number I must say. It surprises me that this volume has to be patched, so shortly after the release of Windows 8.1 OS.
What has Microsoft learned from the Windows 8 experience (and put in the source code of Windows 8.1) ?
I didn’t receive updates for Internet Explorer 11,Windows 7.
Is it supposed to be like that since I installed IE11 a few days ago?
IE 11 has been upgraded to 11.0.1 but only for Windows 8.1
It seems that Microsoft has abandoned IE11 on Windows 7 and 8.
http://support.microsoft.com/kb/2888505
It looks like IE11 for Windows 7 is non-affected software,it doesn’t
need this update (kb2888505).
https://technet.microsoft.com/en-us/security/bulletin/ms13-088
Patch Tuesday: November 2013
MS13-089 Vulnerability in Windows Graphics Device Interface Could Allow Remote Code Execution (2876331)
Graphics Device Interface Integer Overflow Vulnerability (CVE-2013-3940) MS Rating: Critical
A remote code execution vulnerability exists in the way that the Windows Graphics Device Interface (GDI) processes specially crafted Windows Write files in Wordpad. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS13-088 Cumulative Security Update for Internet Explorer (2888505)
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3871) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Information Disclosure Vulnerability (CVE-2013-3908) MS Rating: Important
An information disclosure vulnerability exists in the way that Internet Explorer handles specially crafted web content when generating print previews. This vulnerability could gather information from any page that the victim is viewing.
Internet Explorer Information Disclosure Vulnerability (CVE-2013-3909) MS Rating: Moderate
An information disclosure vulnerability exists in the way that Internet Explorer processes CSS special characters. An attacker could exploit the vulnerability by constructing a specially crafted webpage that could allow an information disclosure if a user viewed the webpage. This vulnerability could view content from another domain or Internet Explorer zone.
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3910) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3911) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3912) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3914) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3915) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3916) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2013-3917) MS Rating: Critical
A remote code execution vulnerability exists when Internet Explorer improperly accesses an object in memory. This vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
MS13-092 Vulnerability in Hyper-V Could Allow Elevation of Privilege (2893986)
Address Corruption Vulnerability (CVE-2013-3898) MS Rating: Important
An elevation of privilege vulnerability exists in Hyper-V on Windows 8 and Windows Server 2012. An attacker who successfully exploited this vulnerability could execute arbitrary code as System in another virtual machine (VM) on the shared Hyper-V host. An attacker would not be able to execute code on the Hyper-V host, but would be able to on guest VMs on the same host. The vulnerability could also allow a denial-of-service in Hyper-V on the same platforms, allowing an attacker to cause the Hyper-V host to stop responding or to restart.
MS13-093 Vulnerability in Windows Ancillary Function Driver Could Allow Information Disclosure (2875783)
Ancillary Function Driver Information Disclosure Vulnerability (CVE-2013-3887) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel-mode driver improperly handles copying data between kernel and user memory.
MS13-095 Vulnerability in XML Digital Signatures Could Allow Denial of Service (2868626)
XML Digital Signatures Vulnerability (CVE-2013-3869) MS Rating: Important
A denial of service vulnerability exists in implementations of X.509 certificate parsing that could cause the service to stop responding. The vulnerability is caused when the X.509 certificate vailidation operation fails to handle a specially crafted X.509 certificate.
MS13-094 Vulnerability in Microsoft Outlook Could Allow Information Disclosure (2894514)
S/MIME AIA Vulnerability (CVE-2013-3905) MS Rating: Important
An information disclosure vulnerability when Microsoft Outlook does not properly handle the expansion of S/MIME certificate metadata. An attacker who successfully exploited this vulnerability could ascertain system information, such as the IP address, and open TCP ports, from the target system and other systems that share the network with the target system.
MS13-090 Cumulative Security Update of ActiveX Kill Bits (2900986)
InformationCardSigninHelper Vulnerability (CVE-2013-3918) MS Rating: Critical
A remote code execution vulnerability exists in the the InformationCardSigninHelper Class ActiveX control, icardie.dll. An attacker could exploit the vulnerability by constructing a specially crafted webpage. When a user views the webpage, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user.
MS13-091 Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (2885093)
WPD File Format Memory Corruption Vulnerability (CVE-2013-0082) MS Rating: Important
A remote code execution vulnerability exists in the way that affected Microsoft Office software parses a specially crafted WordPerfect document (.wpd) files. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Word Stack Buffer Overwrite Vulnerability (CVE-2013-1324) MS Rating: Important
A remote code execution vulnerability exists in the way that affected Microsoft Office software parses specially crafted WordPerfect document files. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Word Heap Overwrite Vulnerability (CVE-2013-1325) MS Rating: Important
A remote code execution vulnerability exists in the way that affected Microsoft Office software parses specially crafted WordPerfect document files. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Thanks Martin, For guiding me through main this mount 14 updates.
Also I would like to mention that I am noticing over the years a steady improvement in your “this mount Microsoft security (updates) bulletins” articles.
Please keep up the good work.
I’m trying my best to add useful information to the article, and remove those that are redundant or not useful.
Update tuesday is back once again… Does anyone else think that while new vulnerabilities won’t be patched for Windows XP once it’s support cycle ends, it’s going to be a relief for XP users to be free of the monthly odds of getting their computer rendered unsuable by some troublesome update?
Anyway, thank you very much for the detailed report on the monthly updates :)
Yes, Miguel. It’s a crap shoot. When Patch Tuesday rolls around I always wonder which of my applications will quit working this time.
Well, yes and no. We need XP to run a somewhat dated automation package at a medium-sized public utility. The automation machines are well-isolated from outside networks, but I wonder how many small industrial and utility installations still run XP, have enabled offsite access in order to keep staffing low, and will, therefore, become more vulnerable to cyber-attack once XP support sunsets?
According to informationweek.com, as of the end of July 2013, 75% of US ATMs were running Win XP.
On a lighter note, my insurance agent recently called up a master database — in DOS. The faster we run, the more often we stagger…
I received only 7 Windows Updates.
Windows 7 SP1 x86,IE11
Does anyone have information about non-security update :
Update for Windows 7 and Windows Server 2008 R2 (KB2830477)
Microsoft Support for this update states : “Sorry, the page you requested is not available.”
I’m just wondering if I should run this update, as I have no idea of what it can concern.
Found Microsoft had auto installed these updates overnight and the PC had re-booted to complete the install. I signed on and as part of the load process a number of apps are loaded including Firefox. Immediately on load, Firefox crashed. Tried to reload Firefox and it crashed immediately. Firefox dump gave absolutely no clues. So I went to see what Microsoft updated. At the same time, I notices there were other suggested, but not downloaded or installed, including KB2830477. I decided I had nothing to lose by installing KB2830477. Once the system was updated and reloaded, the Firefox crash problem was resolved.
Obviously, Firefox is using some part of the server software and apparently there is a dependency with some other update that Microsoft is not aware of.
Works for me however I just posted this onto the TechNet forums:
“Update 2830477 breaks smartcard reader access for RDP sessions:
I just a applied the latest Windows Update patches to my Windows 7 PC and after rebooting found that my Dell smartcard reader keyboard was no longer showing up on my RDP sessions (Windows 2008 R2 Terminal Servers).
After some investigation I discovered that by removing update 2830477 that it returned to normal and my reader appeared again. I also noted that the prerequisite patches, 2574819 & 2857650, are installed as needed.
Is there something we need to do differently with the new version of the RDP client provided by 2830477 as we cannot see any difference in the settings.”
Update for Windows 7 (KB2830477)
Nov 12th, 2013
Microsoft Download Link
These updates (*.msu) provide a collection of performance and reliability improvements that are designed to improve the Windows 7 experience.
http://www.microsoft.com/en-us/download/details.aspx?id=41036&WT.mc_id=rss_windows_allproducts
MS13-090 ActiveX Kill Bits fixs the Zero-Day security bug in IE :
http://blogs.technet.com/b/msrc/archive/2013/11/11/activex-control-issue-being-addressed-in-update-tuesday.aspx
p.s Microsoft hasn’t fixed the TIFF security bug that is targeting Windows PC all over the world.