Microsoft Security Bulletins For September 2013 overview
Microsoft has released this month's security updates for Microsoft Windows, Microsoft Office and other company products just a second ago.
This month's updates bring 13 bulletins that fix a total of 47 vulnerabilities.
Four bulletins have received the highest severity rating of critical. This means that at least one product is affected critically by at least one of the vulnerabilities that the bulletin addresses.
The remaining ten bulletins have all received a maximum severity rating of important. Again, this means that at least one product is affected by it at this severity level.
The vulnerabilities in eight bulletins may allow remote code execution on affected systems, while three may enable an elevation of privileges, two the denial of service, and one for information disclosure.
Operating System Distribution
This section looks at individual operating system versions, and how each supported operating system is affected by this month's bulletins.
Microsoft has released a total of 13 bulletins in September 2013, of which seven affect at least one version of Microsoft Windows.
Windows XP is again the operating system with the highest count of critical vulnerabilities. All newer Microsoft operating systems share the same amount of critical vulnerabilities. As far as important rated vulnerabilities go (the second highest rating): Windows 7 takes the lead here followed by Vista and Windows 8, and then Windows RT.
It looks similar on the server side of things. Windows Server 2003 is the only server operating system affected by a critical bulletin. All other server products are only affected by important and moderate bulletins, with Windows Server 2008 R2 affected by one additional important rated bulletin.
- Windows XP: 2 critical, 3 important
- Windows Vista: 1 critical, 3 important
- Windows 7:Â 1 critical, 4 important
- Windows 8:Â 1 critical, 3 important
- Windows RT: 1 critical, 2 important
- Windows Server 2003: 1 critical, 3 important, 1 moderate
- Windows Server 2008: 3 important, 1 moderate
- Windows Server 2008 R2: 4 important, 1 moderate
- Windows Server 2012: 3 important, 1 moderate
Office Distribution
Microsoft has released seven Office-related bulletins in September 2013. The distribution indicates that Office 2010 is the operating system with the largest number of vulnerabilities, followed by Office 2007. Both Office 2003 and Office 2013 share the same low number of vulnerabilities.
- Microsoft Office 2003: 2 important
- Microsoft Office 2007: 1 critical, 3 important
- Microsoft Office 2010: 1 critical, 4 important
- Microsoft Office 2013: 2 important
- Microsoft Office for Mac: 1 important
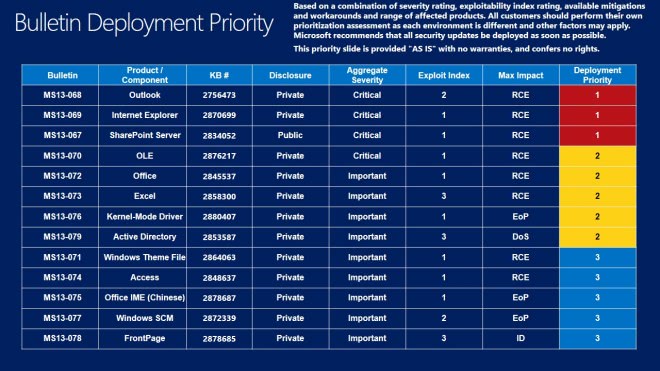
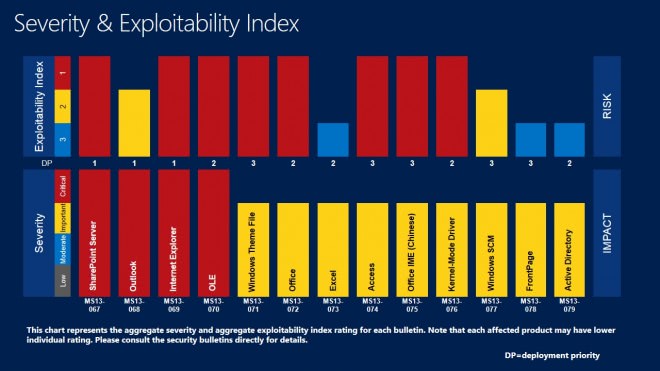
Deployment Guide
Microsoft releases a deployment guide each month that system administrators and individual users can use as a guideline to determine the update priority.
While it is usually sound to start with the critical updates and then the lesser severe updates, it may be important to distribute updates in a certain order, for instance to fix issues first that are exploited in the wild.
Priority 1 updates: MS13-068 Outlook, MS13-069 Internet Explorer and MS13-067 SharePoint Server
Priority 2 updates: Ms13-070 OLE, MS13-072 Office, Ms13-073 Excel, Ms13-076 Kernel-Mode Driver and Ms13-079 Active Directory
Priority 3 updates: Ms13-071 Windows Theme File, Ms13-074 Access, Ms13-075 Office IME (Chinese), Ms13-077 Windows SCM and Ms13-078 FrontPage.
Security Bulletins
- MS13-067Vulnerabilities in Microsoft SharePoint Server Could Allow Remote Code Execution (2834052)
- MS13-068Vulnerability in Microsoft Outlook Could Allow Remote Code Execution (2756473)
- MS13-069Cumulative Security Update for Internet Explorer (2870699)
- MS13-070Vulnerability in OLE Could Allow Remote Code Execution (2876217)
- MS13-071Vulnerability in Windows Theme File Could Allow Remote Code Execution (2864063)
- MS13-072Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (2845537)
- MS13-073Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution (2858300)
- MS13-074Vulnerabilities in Microsoft Access Could Allow Remote Code Execution (2848637)
- MS13-075Vulnerability in Microsoft Office IME (Chinese) Could Allow Elevation of Privilege (2878687)
- MS13-076Vulnerabilities in Kernel-Mode Drivers Could Allow Elevation of Privilege (2876315)
- MS13-077Vulnerability in Windows Service Control Manager Could Allow Elevation of Privilege (2872339)
- MS13-078Vulnerability in FrontPage Could Allow Information Disclosure (2825621)
- MS13-079Vulnerability in Active Directory Could Allow Denial of Service (2853587)
Other Security related updates
Security Update for Windows 8, Windows Server 2012, Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB2862973)
MS13-057: Security Update for Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2803821)
MS13-057: Security Update for Windows Media Format Runtime for Windows Server 2003 and Windows XP (KB2834902)
MS13-057: Security Update for Windows Media Format Runtime 9.5 for Windows XP (KB2834903)
MS13-057: Security Update for Windows Media Format Runtime for Windows Server 2003 and Windows XP (KB2834904)
MS13-057: Security Update for Windows Media Format Runtime 9.5 for Windows XP (KB2834905)
MS13-066: Security Update for Windows Server 2012, Windows Server 2008 R2, and Windows Server 2008 (KB2843639)
Non-security related updates
Update for Windows 7 and Windows Server 2008 R2 (KB2574819)
Update for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2 (KB2834140)
Update for Microsoft .NET Framework 4 on Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2836939)
Update for Microsoft .NET Framework 2.0 SP2 on Windows Server 2003 and Windows XP (KB2836941)
Update for Microsoft .NET Framework 3.5.1 on Windows 7 and Windows Server 2008 R2 (KB2836943)
Update for Microsoft .NET Framework 2.0 SP2 on Windows Server 2008 (KB2836945)
Update for Microsoft .NET Framework 3.5 on Windows 8 and Windows Server 2012 (KB2836946)
Update for Windows 7 and Windows Server 2008 R2 (KB2853952)
Update for Windows 8, Windows RT, Windows Server 2012, Windows 7, Windows Server 2008 R2, and Windows Server 2008 (KB2868116)
Update for Windows 8, Windows RT, and Windows Server 2012 (KB2871389)
Update for Windows 8, Windows RT, and Windows Server 2012 (KB2871777)
Update for Windows 8, Windows RT, and Windows Server 2012 (KB2876415)
Windows Malicious Software Removal Tool - September 2013 (KB890830)/Windows Malicious Software Removal Tool - September 2013 (KB890830) - Internet Explorer Version
Update for Windows 7 and Windows Server 2008 R2 (KB2592687)
System Update Readiness Tool for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB947821)
How to download and install the September 2013 security updates
The common way to install the updates is via the operating system's built-in automatic update feature. While that is comfortable to do, it does not provide you with many controls. You cannot for instance decide the order in which updates should be installed.
The easiest way to open Windows Update is to tap on the Windows-key, enter Windows Update, and select the entry from the list of results that opens up.
You can download all patches from Microsoft's Download Center either individually, or as a monthly ISO image. An alternative to that are third party tools that you can use to download patches and updates to your system.
Additional information are available on Microsoft's MSRC blog.
Advertisement




















I cannot install KB2868116 and KB2872339 and from what you have said above I should wait and Microsoft will resolve the issue with the installation?
“Many users seem to have issues with the updates. It is likely that Microsoft will provide patches eventually”.
I have spent a lot of time on these patches.
Regards
On reading the responses i see that someone else had the same error 800whatever but his was win7. Did he run the troubleshooter and fix the problem?
I had difficulties downloading and installing this month on two different laptops this month besides taking a long time before the download would start. On one I had to ask for a fix as administrator twice (and on the other once) for what looked like the same problem besides the restart and update process crashing after rebooting and processing some of the updates on that one: the screen flashed black and white again and again: I let it do that for an hour and a half as you are suppose to shut down while updates are being processed before i forced it off. It booted normally and started to process updates but on checking for updates after that many were still to be downloaded and installed. I was about to do a backup when i let it update. Next time i will do the backup first. In the end all was well and i did the backup
Did anyone else have problems like this?
The one one two fixes was running Win8 and the other Win8Pro
Once again, thank you very much Martin for your detailed article and Ilev for your comment post on this month Microsoft Updates :)
In my case, I always have Automatic Updates turned off and get the patches directly from Microsoft Download Center, and install them at least one or two weeks after their release, while keeping an eye to these GHacks articles for warnings about troublesome updates. This way I can avoid Microsoft Update or Automatic Updates issues (updates being reoffered endlessly, “optional Bing what-ever updates” being pushed to users…) or updates causing trouble (blue screens, crashes…).
Thank you very much :)
On the “Other security related updates”, you may want to clarify:
– KB2803821 applies to Windows XP/2003 and Vista with WMP9.
– KB2834902 applies to Windows XP/2003 with WMP10 only.
– KB2834903 applies to Windows XP/2003 with WMP10L only.
– KB2834904 applies to Windows XP/2003 with WMP11 only.
– KB2834905 applies to Windows XP Media Center only.
They all have to be v2 (i.e: KB2834905 v2), because the ones release on August were causing trouble to some programs and games using Windows Media Format videos.
Ok Martin
Thanks Martin did as you asked got
message “do you want to install the following windows software update?
Security update for Windows (KB2872339)
YES NO ”
I clicked yes
The fix then began download and asked do you want to run or save?
I say run
Then get
“Some updates were not installed
The following updates were not installed
Security update for Windows (KB2872339)
Many users seem to have issues with the updates. It is likely that Microsoft will provide patches eventually. Sorry that I cannot be of more help to you.
Actually windows 7 32 bit
I’d try and download the update manually from Microsoft’s Download Center.
Hi Martin I’m having trouble trying to install KB2872339 I get error 80070490 each time I try to install ..robin
Are you running Windows 8?
Hi Martin no I’m running windows 7
Hallo Martin, Many thanks from me again for helping me once again with main 24 Ms o.s. updates understanding! :-)
With all the outer updates like Sun-Java, Flash player, shockwave player, etc. and making a backup and after all that, the fragmentation its was once again a few hours work. ;-)
Trying to update now, normally no problem, have encountered an unknown error whilst checking for updates (twice tried).
Error(s) found: Code 80072EE2.
No…it’s OK, has downloded.
I luv u guys!!
Having problems getting the Excel 2003 update installed so wuauclt.exe just keeps running. I’m going to have to shut it down and ban MSUpdates for now. Oh well, won’t be the first time.
The two updates KB2810009 and KB2836942 fail to install on my Windows 7 64-bit system. One is a security update for Microsoft Office 2013, the other an update for Microsoft .Net Framework 3.5.1. Not sure why though.
They tried to sneak this one in again under Optional Updates:
Bing Bar 7.2 (KB2673774) Download size: 10.3 MB
– even though I “hide update” every time.
Patch Tuesday 2013
MS13-067 / KB2834052 – Vulnerabilities in Microsoft SharePoint Server Could Allow Remote Code Execution
MS13-067 addresses ten vulnerabilities in SharePoint server, and affects SharePoint 2003, 2007, 2010, and 2013, along with Office Web Apps 2010. The patch addresses multiple elevations of privilege vulnerabilities that could allow an attacker to execute code in the context of another SharePoint user. In certain situations where the default authentication mechanism has been changed, an attacker may be able to take control of the server. Safeguarding sensitive data is critical, so make sure to get this patch rolled out as soon as possible.
MS13-068 / KB2756473 – Vulnerability in Microsoft Outlook Could Allow Remote Code Execution
MS13-068 fixes a critical privately reported vulnerability in Outlook, which an attacker could use to execute arbitrary code in the context of the current user. It affects both Outlook 2007 and 2010. Attackers can exploit this without specific user interaction by crafting malicious S/MIME messages and sending them to target users. When the malicious message is opened, the exploit is triggered, and the vulnerable system is compromised – enabling the attacker to run code in the context of the user. The attack vector makes it urgent to apply this patch as soon as possible
MS13-069 / KB2870699 – Cumulative Security Update for Internet Explorer
MS13-069 is the latest cumulative security update for the Internet Explorer Web browser. The update applies to all supported versions of Internet Explorer, but none of the underlying flaws affects all versions of the browser. This patch should be deployed as quickly as possible, though, because any of these vulnerabilities can be used in drive-by exploits allowing the attacker to execute code in the context of the current user.
MS13-070 / KB2876217 – Vulnerability in OLE Could Allow Remote Code Execution
This update fixes a privately reported bug in the Windows operating system that could allow an attacker to execute remote code. If a user opens a file containing a specially crafted malicious OLE object, the system will be compromised, and the attacker will be able to execute code with the same rights as the user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS13-071 / KB2864063 – Vulnerability in Windows Theme File Could Allow Remote Code Execution
Some users love to download and apply cool themes to customize the look and feel of Windows. The vulnerability addressed by this patch can be exploited through a specially crafted malicious Windows theme. One mitigating factor is that the user must download and apply the malicious theme in order for the attack to work, so educating users against using suspicious or shady themes is advised as well.
MS13-072 / KB2845537 – Vulnerabilities in Microsoft Office Could Allow Remote Code Execution
This update resolves a smorgasbord of privately reported vulnerabilities in Microsoft Office – 13 in all. The more severe vulnerabilities can be exploited through a specially crafted file being opened in an affected version of Microsoft Office. The attacker may be able to execute remote code in the context of the user. As with other similar issues, one way to mitigate the threat is to limit user privileges and not allowing users to log in with administrative privileges.
MS13-073 / KB2858300 – Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution
This update is similar in scope and impact to MS13-072, but more specific to Microsoft Excel. It resolves three privately reported vulnerabilities which could allow remote code execution in the context of the user if successfully exploited. Again, limiting user privileges on the system can minimize the threat or impact of these flaws.
MS13-074 / KB2848637 – Vulnerabilities in Microsoft Access Could Allow Remote Code Execution
This security update resolves three privately reported vulnerabilities in Microsoft Office – specifically Microsoft Access. As with MS13-072 and MS13-073, a specially crafted malicious Microsoft Access file could be used to exploit the flaws. A successful attack could allow the attacker to execute code with the same rights and privileges as the currently logged in user.
MS13-075 / KB2878687 – Vulnerability in Microsoft Office IME (Chinese) Could Allow Elevation of Privilege
This update only impacts Microsoft Office IME – a Chinese version of the productivity suite. If an attacker launches Internet Explorer from the toolbar in Microsoft Pinyin IME for Simplified Chinese, they may be able to run arbitrary code in kernel mode. A successful exploit could enable an attacker to install malicious software, and add or remove user accounts with administrative privileges. Only implementations of Microsoft Pinyin IME 2010 are affected by this vulnerability. Other versions of Simplified Chinese IME and other implementations of IME are not affected.
MS13-076 / KB2876315 – Vulnerabilities in Kernel-Mode Drivers Could Allow Elevation of Privilege
This update resolves seven privately reported vulnerabilities in Microsoft Windows. The potential threat is minimal because an attacker must have valid logon credentials, and be logged on locally to exploit these vulnerabilities. A successful exploit could allow the attacker to elevate their privileges on the compromised system.
MS13-077 / KB2872339 – Vulnerability in Windows Service Control Manager Could Allow Elevation of Privilege
This update fixes one privately reported flaw in Microsoft Windows. The threat is minimal because the attacker must either have valid logon credentials and be logged on locally to the vulnerable system, or trick a user into running a specially crafted application that triggers the exploit. If an attack is successful, the attacker could gain elevated privileges on the compromised system.
MS13-078 / KB2825621 – Vulnerability in FrontPage Could Allow Information Disclosure
Companies using Microsoft FrontPage could be at risk of information disclosure as a result of this privately reported vulnerability. The exploit cannot be triggered automatically, but if a user is tricked into opening a specially crafted FrontPage document, the attacker may be able to access restricted or sensitive information.
MS13-079 / KB2853587 – Vulnerability in Active Directory Could Allow Denial of Service
An attacker can create a denial-of-service condition in Active Directory by exploiting this vulnerability. A specially crafted Lightweight Directory Access Protocol query could cripple Active Directory.
14 releases ? I count 13, 4 critical and 9 important.
Microsoft had projected 14 security bulletins for September, but only 13 were released. One has been having some issues.
Ah, that explains why I had 14 on my list.
As usual every month, more patch problems :
http://www.zdnet.com/update-for-outlook-2013-breaks-folder-pane-7000020512/
http://social.technet.microsoft.com/Forums/office/en-US/0eedb198-f8b1-490d-8c9e-732b4094d0ef/kb2810009-issue
Microsoft : During some additional testing after advance notification, we determined one of the updates was not quite ready. We have not detected any attacks against this issue, or any of the others addressed today, and we’ll continue to work on the bulletin and release it once it is ready, through our regular bulletin release process.
You are right, 13 it is.
Cheers Martin, good work btw, I really appreciate your overview in planning our releases.
Glad that this is not only useful to me ;)
Any updates applicable to Windows 8.1?
I get one Flash Player security update for Internet Explorer, and one definitions update for Windows Defender. That’s it.