Microsoft Security Bulletins For June 2013 overview
Microsoft released a total of five security bulletins addressing 23 different vulnerabilities today of which four affect client and server versions of the Windows operating system while one is affecting Microsoft Office.
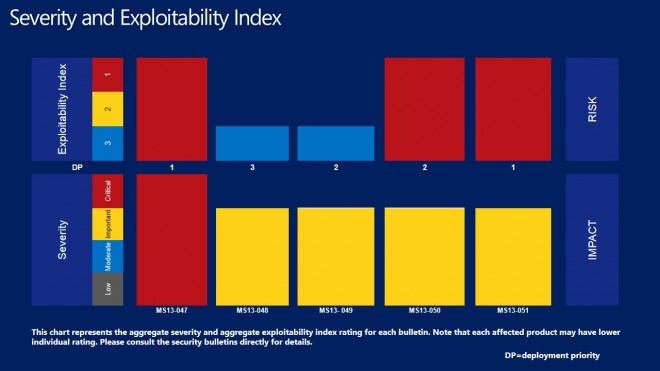
One bulletin has received the maximum severity rating of critical, the highest possible rating, while the remaining four received one of important, the second highest. This does not mean that all versions of Windows or Office are equally affected by those vulnerabilities.
Check out the operating system distribution listing that details how individual versions of Windows are affected this patch day.
Operating System Distribution
Windows editions and versions may be affected in different ways to vulnerabilities. A simple example is a vulnerability in a feature that Microsoft introduced in a later version of the operating system. In this case, all previous versions of Windows would not be affected by the vulnerability at all, as the affected feature would not exist in those versions.
Windows XP is affected the least this time in terms of vulnerabilities followed by Windows RT, then Vista and Windows 7, and finally Windows 8 which is affected most severely.
- Windows XP: 1 critical, 1 important
- Windows Vista: 1 critical, 2 important, 1 moderate
- Windows 7:Â 1 critical, 2 important, 1 moderate
- Windows 8:Â 1 critical, 3 important
- Windows RT: 1 critical, 2 important
- Windows Server 2003: 1 important, 1 moderate
- Windows Server 2008: 2 important, 2 moderate
- Windows server 2008 R2: 1 important, 2 moderate
- Windows Server 2012: 2 important, 1 moderate
Deployment Guide
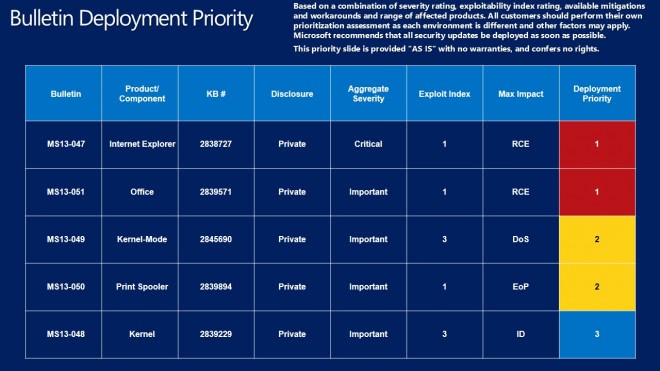
Microsoft recommends to deploy the bulletins in the following order:
- First MS13-047 (Internet Explorer, critical) and then MS13-051 (Office, important).
- Then MS13-049 (Kernel-Mode, important) and then Ms13-050 (Print Spooler, important).
- Last MS13-048 (Kernel, important).
Security Bulletins
- MS13-047 Cumulative Security Update for Internet Explorer (2838727)
- MS13-048 Vulnerability in Windows Kernel Could Allow Information Disclosure (2839229)
- MS13-049 Vulnerability in Kernel-Mode Driver Could Allow Denial of Service (2845690)
- MS13-050 Vulnerability in Windows Print Spooler Components Could Allow Elevation of Privilege (2839894)
- MS13-051 Vulnerability in Microsoft Office Could Allow Remote Code Execution (2839571)
Non-security related updates
- Update for Windows (KB2808679)
- Update for Windows Server 2012 (KB2818604)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2821895)
- Update Rollup for Windows Server 2012 Essentials (KB2824160)
- Update for Windows 7 and Windows Server 2008 R2 (KB2834140)
- Update for Microsoft Camera Codec Pack for Windows 8 and Windows RT (KB2836187)
- Update for Windows 7 and Windows Server 2008 R2 (KB2836502)
- Update for Microsoft .NET Framework 4 on Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2836939)
- Update for Microsoft .NET Framework 3.5 SP1 on Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2836940)
- Update for Microsoft .NET Framework 2.0 SP2 on Windows Server 2003 and Windows XP (KB2836941)
- Update for Microsoft .NET Framework 3.5.1 on Windows 7 and Windows Server 2008 R2 (KB2836942)
- Update for Microsoft .NET Framework 3.5.1 on Windows 7 and Windows Server 2008 R2 (KB2836943)
- Update for Microsoft .NET Framework 2.0 SP2 on Windows Server 2008 (KB2836945)
- Update for Microsoft .NET Framework 3.5 on Windows 8 and Windows Server 2012 (KB2836946)
- Update for Microsoft .NET Framework 3.5 on Windows 8 and Windows Server 2012 (KB2836947)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2845533)
- Windows Malicious Software Removal Tool - June 2013 (KB890830)/Windows Malicious Software Removal Tool - June 2013 (KB890830) - Internet Explorer Version
- Update for Windows 7 and Windows Server 2008 R2 (KB2820331)
- System Update Readiness Tool for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB947821) [May 2013]
How to download and install the June 2013 security updates
The automatic update feature of Windows is the easiest option when it comes to installing security updates.This is an automated process and you do not really need to do anything as updates are installed automatically on your system.
If you want to update manually, do the following instead:
All Windows users can tap on the Windows-key, enter Windows Update and select the appropriate option here to open the updater of the operating system.
Click on the check for updates button first to retrieve the latest updates from Microsoft before you hit the install updates button.
You can browse the updates that Windows has found before you do so, disable some or include others that are not installed automatically.
It is alternatively possible to use Microsoft's Download Center to download and install updates, or third party programs which you find listed on this page.
Advertisement




















Why would I need .NET 3.5… updates if I only have version 4?
After running the last updates on XP I now have to use Foxfire or Chrome to use sites I order products from, everything will not show now.
As always, thank you very much Martin and Ilev for such a complete list/report of this month Microsoft updates, and the direct links to them :)
This month, the “new” Microsoft Download Center appears to be working again, although it takes a few tries to get a page of the downloads lists (it sometimes shows a bing search page and a message saying that there is some problem getting the list page…). Anyway, no need of it if you can get all the information here on GHacks ;)
Thanks,both,I’ll hang fire for time being.
3 unchecked important updates available but Belarc Advisor & PatchMyPC say all updates compliant & up to date so is it good practise to install those anyway?
If you use .NET, so yes.
I won’t be installing them for now. Checked the KB articles briefly and they seem to address – mostly – coding related issues if you use Visual Studio or similar.
Security Patches June 2013
MS13-047/KB2838727 – Cumulative Security Update for Internet Explorer (IE 6, 7, 8, 9 and 10 on Windows XP, Vista, Windows 7, Windows 8, Windows RT and Server 2003, 2008, 2008 R2 and 2012, all editions). This update is rated critical for client and moderate for server operating systems and affects all listed versions of the IE web browser and all currently supported Windows operating systems (server core installation excluded). It addresses nineteen different vulnerabilities that stem from the way IE handles objects in memory, some of which allow remote code execution if a specially crafted malicious web page is visited. A restart is required after installation.
MS13-048/KB2839229 – Vulnerability in Windows Kernel Could Allow Information Disclosure (Windows XP, Vista, Windows 7 and Windows 8, Server 2003, 2008, 2008 R2 and 2012). This update is rated important, and addresses a vulnerability in the way Windows handles page fault system calls, that could allow disclosure of information if an attacker logs on to a system and runs specially crafted software (or convinces a legitimate logged-on user to run such software). Note that the attacker cannot exploit this vulnerability without the ability to log on locally, and it doesn’t allow remote code execution or elevation of privileges. A restart is required after installation.
MS13-049/KB2845690 – Vulnerability in Kernel-Mode Driver Could Allow DoS (Windows Vista, Windows 7, Windows 8, Windows RT, Server 2008, 2008 R2, and 2012, including server core installation). This update is rated Important for Windows RT, 8 and Server 2012, moderate for other affected operating systems. It addresses one vulnerability in the kernel-mode driver, due to the TCP/IP driver’s handling of specially crafted packets that could allow an attacker to create a Denial of Service by sending specially crafted malicious packets. It does not affect Windows XP or Server 2003. A restart is required after installation.
MS13-050/KB2839894 – Vulnerability in Windows Print Spooler Components Could Allow Elevation of Privilege (Windows Vista, Windows 7, Windows 8, Windows RT, Server 2008, 2008 R2, and 2012, including server core installation). This update is rated Important for all affected operating system versions. Windows XP and Server 2003 are not affected. It addresses one vulnerability in the way the Windows print spooler allocates memory when a printer connection is deleted, that could allow elevation of privilege when an authenticated user deletes a printer, but the user must have valid logon credentials to exploit this vulnerability. A restart is required after installation.
MS13-051/KB8239571 – Vulnerability in Microsoft Office Could Allow Remote Code Execution (Office 2003 SP3 and Office for Mac 2011). This update is rated Important for the affected versions of Office. It addresses one vulnerability in the specifically listed versions of Microsoft Office that is based on the way Office parses specially crafted Office files and could allow remote code execution if a user opens a malicious file or opens/previews a message in Outlook, using Word as the email reader. Office 2007, 2010, 2013/2013 RT, the Compatibility Pack SP3 and the Excel and PowerPoint viewers are not affected. A restart may be required after installation.
Other Updates/Releases
There were a whopping 17 non-security updates released today, including the regular monthly update for the Malicious Software Removal Tool (MSRT).
KB2808679 – Update to protect from internal URL port scanning (Windows XP, Vista, Windows 7, Windows 8, Windows RT, Server 2003, 2008, 2008 R2 and 2012). This update protects an external network from verifying whether a URI port on the internal network is open or closed. A restart is not required.
KB2818604 – Microcode update for AMD computers (Windows 7 and Windows 8). This update is for computers that use certain AMD processors (C, E, G and Z series) and updates the processor microcode. There is a Fix It link available as well as instructions for manual installation.
KB2821895 – Servicing stack update (Windows 8, Windows RT, Server 2012). This update contains four improvements and fixes for seven issues in the servicing stack on the listed operating systems. A restart is required after installation.
KB2824160 – Update rollup 2 for Windows Server 2012 Essentials (Windows Server 2012 Essentials). This update rollup includes fixes for server-side issues and also installs the client-side rollup package automatically. Issues that are addressed include a problem with Office 365 integration service crashing, a failed operation when changing user access level or folder permissions and a problem with using PowerShell to enable Office 365. Rollup 2 beta must be uninstalled before installing this final version. A restart is not required after installation.
KB2834140 – “0×00000050″ Stop error (Windows 7 SP1 and Windows Server 2008 R2 SP1). This update addresses a problem that causes a Stop error (PAGE_FAULT_IN_NONPAGED_AREA) when there is a combination of Intel and AMD video cards installed. A restart is not required after installation.
KB2836187 – Update to support camera-specific file formats (Windows 8, Windows RT). This update installs a Microsoft Camera Codec Pack that makes it possible to view RAW image files in the modern UI in Windows 8 and RT and open them with Windows Explorer and Windows-based applications. A restart is required after installation.
KB2836502 – Certain JPEG images cannot be displayed (Windows 7 SP1 and Server 2008 R2 SP1). This update addresses a problem whereby you can’t view certain JPEGs after installing update 270838 when the JPEG is a non-progressive compressed JPEG and its components span multiple scans. A restart is required after installation.
KB2836939 – Update for .NET Framework 4 (Windows XP, Vista, Windows 7, Server 2003, 2008 and 2008 R2). This is an update to the .NET framework that resolves two issues related to a JavaScript error and an ASP.NET problem. A restart is required if any affected files are being used.
KB2836940 – Update for .NET Framework 3.5 SP1 (Windows XP, Vista, Server 2008 and 2008 R2). This is an update to the .NET framework that resolves two issues related to a JavaScript error and an ASP.NET problem. A restart is required if any affected files are being used.
KB2836941 – Update for .NET Framework 2.0 SP2 (Windows XP and Server 2008). This is an update to the .NET framework that resolves two issues related to a JavaScript error and an ASP.NET problem. A restart is required if any affected files are being used.
KB2836942 – Update for .NET Framework 3.5.1 (Windows 7 SP1 and Server 2008 R2 SP1). This is an update to the .NET framework that resolves two issues related to a JavaScript error and an ASP.NET problem. A restart is required if any affected files are being used.
KB2836943 – Update for .NET Framework 3.5.1 (Windows 7 SP1 and Server 2008 R2 SP1). This is an update to the .NET framework that resolves two issues related to a JavaScript error and an ASP.NET problem. A restart is required if any affected files are being used.
KB2836946 – Update for .NET Framework 3.5 (Windows 8 and Server 2012). This is an update to the .NET framework that resolves two issues related to a JavaScript error and an ASP.NET problem. A restart is required if any affected files are being used.
KB2836947 – Update for .NET Framework 3.5 (Windows 8 and Server 2012). This is an update to the .NET framework that resolves two issues related to a JavaScript error and an ASP.NET problem. A restart is required if any affected files are being used.
KB2845533 – Update Rollup http://support.microsoft.com/kb/2836947 (Windows 8, RT and Server 2012). This update package includes improvements to performance and reliability of the listed operating systems and resolves issues with MP4 files generation by Android devices, crashes during hibernation when a device is connected to a USB 3.0 port, inability to sign into the Windows Store and slow updates, as well as a large number of fixes for problems documented in various KB articles. A restart is required after installation.
KB890830 – Windows Malicious Software Removal Tool, June 2013. This is the monthly release of the latest version and definitions for the MSRT, which checks your computer for specific prevalent malware.
KB2859903 – Update for IE 10 (Windows 7 and Server 2008 R2). This update addresses a problem where a “select later†option in KB update 976002 isn’t displayed for new installations of IE 10 on Windows 7 and Server 2008 R2.
Updates since the last Patch Tuesday
There was only one out-of-band update released since the last Patch Tuesday, which came out on May 28:
KB947821 – System Update Readiness Tool (Windows 7, Windows Server 2008 R2, Windows Server 2008 and Windows Vista). The tool addresses an inconsistency in the Windows servicing store that could prevent successful installation of future updates and service packs. It fixes a number of installation errors, such as ERROR_FILE_NOT_FOUND and ERROR_INVALID_DATA, which sometimes occur when using Windows Update.
hi Martin,
suppose i have multiple MSU (KB*********) files in folder, then what should be the order of installing / slipstreaming them.
1. by the name
2. by the release date
or other… please reply…
You can use a script like the one posted here on this board
http://www.msfn.org/board/topic/152020-batch-script-for-windows-software-updates-installation/
thanks!!!
Martin,did you also have 3 unchecked updates for NET framework?
I actually have four of those, yes.
Well that’s nice, (KB2808679) doesn’t even have a working info page… your link is fine but even the update page itself doesn’t have any clue what it does.
The Download Center page for an update (or even the description of the update in Microsoft Update) usually don’t have a complete explanation of what the update does, or just contains some standard descriptions. It’s always better to go to the KB support page to get an explanation about what the update really does.
It sometimes takes a while before all pages are live.
I really miss my good ol’ clean Windows 7 :(
With the first opportunity, I’ll go back to Win7; a clean installation. Would be great a second and last service pack… So many updates to start with…
I’m saying this ’cause the images you post are from Win7. :S
Thanks Martin, For your elaborated explanation again. :-)