Microsoft Security Bulletins For March 2013 Released
Yes it is this day of the month ago. Microsoft has just released this month collection of updates and patches for its products. A total of seven security bulletins have been released this month that resolve security related issues in programs such as Microsoft Office, Windows, Internet Explorer and Microsoft Server Software.
Four of the seven bulletins have received a maximum severity rating of critical, the highest rating available for vulnerabilities, while the remaining three received one of important, the second highest rating available. What this means is that at least one affected product has received the rating, while other products may have received the same, a lower, or no rating at all if they are not affected by the vulnerability.
Operating system distribution
Here is the list of bulletins by operating system. First the desktop systems and then the server operating systems. Note that only two of the bulletins affect the Windows operating system or products that run on it. The remaining bulletins are for Office products and other Microsoft software.
- Windows XP: 1 critical, 1 important
- Windows Vista: 1 critical, 1 important
- Windows 7:Â 1 critical, 1 important
- Windows 8:Â 1 critical, 1 important
- Windows RT: 1 critical
- Windows Server 2003: 1 important, 1 moderate
- Windows Server 2008: 1 important, 1 moderate
- Windows server 2008 R2: 1 important, 1 moderate
- Windows Server 2012: 1 important, 1 moderate
Deployment Guide
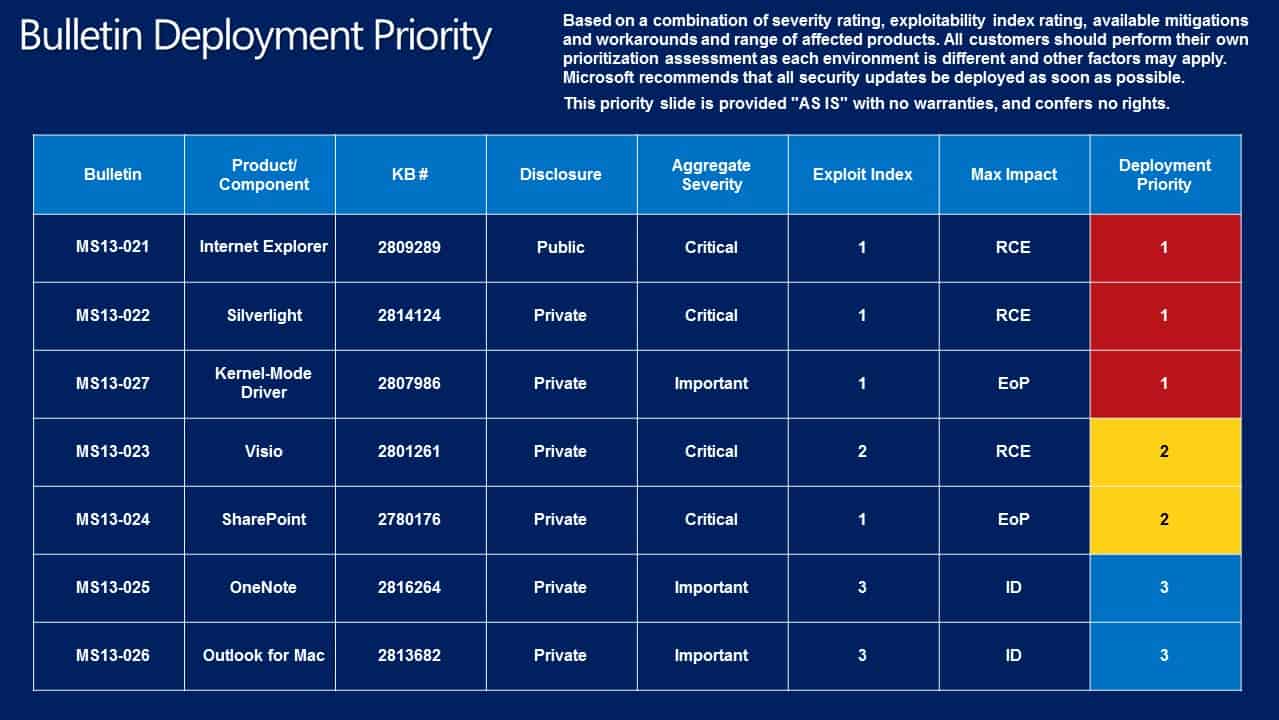
The Bulletin Deployment Priority table provides guidance to system administrators in regards to the order in which bulletins should be installed on affected computer systems. Microsoft suggests to start with MS13-021, MS13-022 and MS13-027 first and in that order, then with MS13-023 and MS13-024, before deploying MS13-025 and MS13-026. It goes without saying that these bulletins only need to be deployed on systems the products run on.
The March 2013 bulletins
- MS13-021 - Cumulative Security Update for Internet Explorer (2809289) - This security update resolves eight privately reported vulnerabilities and one publicly disclosed vulnerability in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-022 - Vulnerability in Silverlight Could Allow Remote Code Execution (2814124) - This security update resolves a privately reported vulnerability in Microsoft Silverlight. The vulnerability could allow remote code execution if an attacker hosts a website that contains a specially crafted Silverlight application that could exploit this vulnerability and then convinces a user to view the website. The attacker could also take advantage of compromised websites and websites that accept or host user-provided content or advertisements. Such websites could contain specially crafted content that could exploit this vulnerability. In all cases, however, an attacker would have no way to force users to visit a website. Instead, an attacker would have to convince users to visit a website, typically by getting them to click a link in an email message or in an Instant Messenger message that takes them to the attacker's website. It could also be possible to display specially crafted web content by using banner advertisements or by using other methods to deliver web content to affected systems.
- MS13-023 - Vulnerability in Microsoft Visio Viewer 2010 Could Allow Remote Code Execution (2801261) - This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Visio file. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-024 - Vulnerabilities in SharePoint Could Allow Elevation of Privilege (2780176) - This security update resolves four privately reported vulnerabilities in Microsoft SharePoint and Microsoft SharePoint Foundation. The most severe vulnerabilities could allow elevation of privilege if a user clicks a specially crafted URL that takes the user to a targeted SharePoint site.
- MS13-025 - Vulnerability in Microsoft OneNote Could Allow Information Disclosure (2816264) - This security update resolves a privately reported vulnerability in Microsoft OneNote. The vulnerability could allow information disclosure if an attacker convinces a user to open a specially crafted OneNote file.
- MS13-026 - Vulnerability in Office Outlook for Mac Could Allow Information Disclosure (2813682) - This security update resolves one privately reported vulnerability in Microsoft Office for Mac. The vulnerability could allow information disclosure if a user opens a specially crafted email message.
- MS13-027 - Vulnerabilities in Kernel-Mode Drivers Could Allow Elevation Of Privilege (2807986) - This security update resolves three privately reported vulnerabilities in Microsoft Windows. These vulnerabilities could allow elevation of privilege if an attacker gains access to a system.
Non-Security related updates
In addition to security related updates, Microsoft has also made available non-security related updates this month:
- Internet Explorer 10 for Windows 7 and Windows Server 2008 R2 (KB2718695)
- Update for Windows 7 and Windows Server 2008 R2 (KB2775511)
- Update for Windows 8 (KB2781197)
- Update for Windows 8 and Windows Server 2012 (KB2790907)
- Dynamic Update for Windows 8 and Windows Server 2012 (KB2791338)
- Update Rollup for Microsoft Windows MultiPoint Server 2012 (KB2791647)
- Update for Windows 7 and Windows Server 2008 R2 (KB2791765)
- Update for Windows Server 2008 R2 x64 Edition (KB2806748)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2811660)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2812822)
- Update for Internet Explorer Flash Player for Windows 8, Server 2012 and Windows RT (KB2824670)
- Windows Malicious Software Removal Tool - March 2013 (KB890830)/Windows Malicious Software Removal Tool - March 2013 (KB890830) - Internet Explorer Version
- Platform Update for Windows 7 and Windows Server 2008 R2 (KB2670838)
- Internet Explorer 10 for Windows 7 and Windows Server 2008 R2 (KB2718695)
How to download and install the March 2013 updates
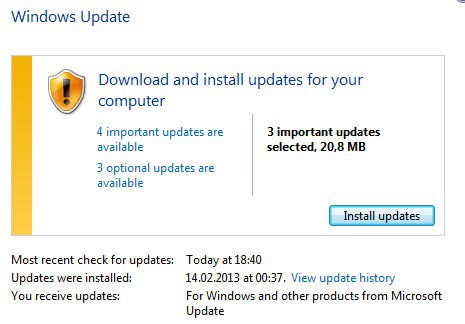
The recommended way to install these updates for home users is to use Windows Update. You can run a manual check for updates via the start menu. If you are using Windows 8, do the following instead:
On Windows 8 you tap on the Windows key to get to the start screen interface, enter Windows update, select Settings on the Charms Bar, and then Check for updates in the results listing.
Here you can click on check for updates to run a manual update check. Windows should pick up the new updates right away so that you can download and install them to your system.
The updates are also available on Microsoft's Download Center where they can be downloaded as individual updates to the local system. That's useful if they need to be deployed on a company network for example, or if you want greater control over the updating process itself.
Advertisement



















Miguel,
Thanks for clarification.So I guess I’ll wait for a few weeks.
Don’t know why KB2775511 wasn’t offered trough WU.
It’s not uncommon for “service packs” to have been published a few weeks before they appear in Windows Update, it’s the way Microsoft has been done it in the past, if I remember well.
Probably they do it this way so they don’t get their servers overloaded with a massive number of downloads, and have their enterprise customers to get it first before they release it to WU and everyone gets it automatically…
Ilev,
do you know something about this?
http://news.softpedia.com/news/Download-the-Official-Windows-7-Service-Pack-2-Replacement-337004.shtml
I’m not Ilev, but I’ll try to reply:
I think the update they are talking about in that article is the “Hotfix rollup” that Ilev had on his comment as “KB2775511 – Enterprise hotfix rollup (Windows 7 SP1 and Server 2008 R2 SP1). (…)” and Martin had in his article as “Update for Windows 7 and Windows Server 2008 R2 (KB2775511)”.
This update install a lot of “hotfixes” for Windows 7 that were released after SP1. They correct problems not related to security that were not previously published on Windows Update. It’s kind of a “service pack”, but it only contains some “hotfixes” (it does not contain all previosly security updates like “service packs”).
So far, all people I’ve seen that have written about having installed it, told that there were no problems, but I’ll wait a few days (or weeks) to install “service packs” or “hotfix rollups” and such (they are not security updates, so no hurry…). This way, if any problem arises, it’ll probably be known because of news articles about it in websites like GHacks ;)
Patch Tuesday: March 2013
MS13-021/KB2809289 – Cumulative Security Update for Internet Explorer (IE 6, 7, 8, 9 and 10). This update addresses nine vulnerabilities that could be exploited to allow an attacker to gain the same rights as the currently logged-on user, due to the way IE handles objects in memory. It’s rated Critical for IE on Windows clients and Moderate for IE on Windows servers. It impacts all Windows client and server operating systems except Windows 7 SP1 and Server 2008 R2 SP1 running IE 10 and also does not impact Server Core installations.
MS13-022/KB2814124 – Vulnerability in Silverlight that could allow Remote Code Execution (Silverlight 5 installed on any supported release of Windows client and Windows server or installed on Mac, including Developer Runtime). This update addresses one vulnerability that could allow an attacker to remotely execute code on a computer that visits a web site containing a specially crafted malicious Silverlight application. It is rated Critical on all operating systems that have Silverlight installed.
MS13-023/KB2801261 – Vulnerability in Visio Viewer 2010 (Visio Viewer 2010 SP1 32 and 64 bit, Vision 2010 SP1 32 and 64 bit, Office 2010 Filter Pack SP1 32 and 64 bit). This update addresses one vulnerability that could allow an attacker to remotely execute code on a computer when the user opens a specially crafted malicious Visio file either in Visio itself or in the viewer. It is rated Critical for all supported editions of Visio/Visio Viewer 2010. It does not impact Visio 2003, 2007 or 2013.
MS13-024/KB2780176 – Vulnerabilities in SharePoint (SharePoint Server 2010 SP1, SharePoint Foundation 2010 SP1). This addresses four vulnerabilities that could allow elevation of privileges if a user clicks a specially crafted URL that leads to a targeted SharePoint site. It’s rated Critical for all supported editions of SharePoint 2010 and Important for SharePoint Foundation 2010. It does not affect SharePoint Server 2007 SP3, SharePoint Server 2013, Groove 2007 SP3, Groove 2010 SP1, SharePoint Portal Server 2003 SP3, SharePoint Services 2.0 and 3.0 SP3, SharePoint Foundation 2013, or SharePoint Workspace 2010 SP1.
MS13-025/KB2816264 – Information Disclosure Vulnerability in OneNote (OneNote 2010 SP1). This update addresses one vulnerability in OneNote 2010 that could allow an attacker to gain access to a user’s information if the user opens a specially crafted malicious OneNote file. It is rated Important for OneNote 2010. It does not affect other supported versions of OneNote and does not affect Microsoft Web Apps 2010 SP1.
MS13-026/KB2813682 – Vulnerability in Office Outlook for Mac (Office 2008 for Mac, Office for Mac 2011). This update could expose a user’s information if the user opens a specially crafted malicious email message. It’s rated Important for the listed versions of Office for Mac.
Ms13-027/KB2807986 – Vulnerability in Kernel-Mode Drivers (Windows XP SP3, XP Pro SP2, Server 2003 SP2, Vista SP2, Server 2008 SP2, Server 2008 R2 SP1, Windows 8, Server 2012, includes all Server Core installations). This update addresses three vulnerabilities in all supported versions of Windows except Windows RT, which could allow elevation of privilege if an attacker is able to access a system. It’s rated Important for all versions.
Other Updates/Releases
There are ten non-security updates released today, along with the regular monthly update for the Malicious Software Removal Tool (MSRT).
KB2775511 – Enterprise hotfix rollup (Windows 7 SP1 and Server 2008 R2 SP1). This rollup contains fixes released after SP1 and addresses the Windows Client Remote File System, SMB service, TCP protocol, Windows Management Instrumentation (WMI) and processing of Group Policies.
KB2781197 – Anti-malware platform update for Windows Defender (Windows 8). This update for Windows Defender updates services, drivers, and the user interface.
KB2790907 – Compatibility Update (Windows 8 and Server 2012). This update improves the compatibility experience in Windows 8 and Server 2012.
KB2791338 – Dynamic Update (Windows 8 and Server 2012). This update improves the legacy upgrade experience when you upgrade to the latest version of Windows 8.
KB2791342 – Compatibility Update for Web and Media Experience (Windows 8 and Server 2012). This update provides compatibility improvements and improves the web and media upgrade experience.
KB2791647 – Windows MultiPoint Server 2012 General Availability Cumulative Update (MultiPoint Server 2012). This update introduces support for USB-over-Ethernet client devices and drivers and fixes issues with Virtual Desktop templates on UEFI systems and a language problem with MultiPoint Help.
KB2791765 – Application Compatibility Update (Windows 7 and Server 2008 R2). This update improves the compatibility experience in Windows 7 and Server 2008 R2, including the Acer Live Updater, Office Enterprise Suite and BOCOM Internet Banking Wizard.
KB2806748 – Fix for Incorrect Results from AD PowerShell Cmdlets (Windows Server 2008 R2). This update addresses a problem of getting incorrect results when you run AD Windows PowerShell cmdlets on a domain controller running Windows Server 2008 R2.
KB2811660 – Cumulative Update for Windows 8 and Server 2012 (Windows 8, Server 2012). This update addresses reliability of USB 3.0 device initialization, an issue with the on-screen keyboard, a GPO issue, Wi-Fi reliability, and rendering of bold text, as well as a number of other reliability and performance issues.
KB2812822 – System Restart Problem (Windows RT, 8 and Server 2012). This update addresses an issue with Windows RT, 8 and Server 2012 whereby the system may restart and not display the “Choose an Option†screen when you try to restart into the UEFI Firmware Settings using Advanced Startup.
KB890830 – Windows Malicious Software Removal Tool – March 2013 and Internet Explorer Version. (Windows 8, Server 2012, Windows 7, Server 2008/2008 R2, Vista, Server 2003, XP). This is the monthly update to the MSRT.
Updates since the last Patch Tuesday
There were quite a few out-of-band patches released between the February and March Patch Tuesdays.
There were seven updates released on February 26.
KB2819372 – Update for IE Flash Player for Windows 8. (Windows 8, Windows RT, Server 2012). Addresses a vulnerability that would allow an attacker to gain control of a computer running IE Flash Player for Windows 8/RT/Server 2012.
KB2670838 – Platform update for Windows 7 SP1 and Windows Server 2008 R2 SP1 (Windows 7 SP1, Server 2008 R2 SP1). See the February 27 release above. Re-released February 27.
KB2718695 – IE 10 for Windows 7 SP1 and Server 2008 R2 (Windows 7). Updates Internet Explorer in Windows 7 SP1 and Windows Server 2008 R2 to version 10.
KB2781267 – Update Rollup for Windows Server 2012 Essentials (Windows Server 2012 Essentials). Adds new features pertaining to hosted email and the Dashboard, updates .NET Framework and AntiXSSLibrary.dll, resolves seven issues.
KB2794599 – Fonts in console programs too small to read (Windows 8, RT and Server 2012). This fixes a problem whereby, when running a multilingual version of Windows 8, RT or Server 2012, the fonts in all console programs become too small to read – affects Chinese, Central Kurdish and Sindhi languages.
KB2818604 – Microcode update for Windows 8 on AMD processor (Windows 8). This updates the processor microcode for AMD C, E, G and Z-series processors.
KB947821 – System Update Readiness Tool (Windows 8, 7, Vista, Server 2008/2008 R2). Scans for inconsistencies and fixes errors that occur when you run Windows Update.
Thank you very much Ilev and Martin :) Lots of updates this month!
KB2807986 was unchecked as important update.I installed it anyway.
So far everything is OK in Windows 7 SP1 32 bit.
I think I will uninstall Silverlight because it is always disabled and I don’t use it.
Thanks Martin, For explaining where main 11 updates this mount where about.
Could you go over this one a bit more?
Platform Update for Windows 7 and Windows Server 2008 R2 (KB2670838)
I’m not sure what it is and if it has any benefit to me.
Also I’m thinking of just uninstalling Silverlight, I don’t think I’ve ever used it, it’s nothing but security updates month after month and it’s basically just another “Flash” correct? Any reason why I shouldn’t uninstall it? Will IE still function correctly without it and could anything else break?
Lastly I don’t use IE as my browser and I’m fine with just sticking to IE9, and like many I resist change so upgrading to IE 10 just for the sake of it is rather dumb, whats the consensus on this update? Is it worth ignoring for the time being?
@Eli
KB2670838 is a pre-requisite for installing IE10 on Windows 7. It crashes many PCs with IE9
and it is advised to uninstall the update.
Microsoft pushes another botched automatic update
If you’ve encountered blue screens while running Internet Explorer in 64-bit Windows 7, there may be an easy solution
If you had Windows set for automatic updates last Tuesday, Feb. 26, and run 64-bit Windows 7, you may have been hit by the latest bad patch. KB 2670838 — known officially as a “Platform Update for Windows 7 x64-Edition” — appears to be the source of a blue-screen problem, where Internet Explorer 9, in particular, stops working and throws a “PAGE_FAULT_IN_NONPAGED_AREA” error identifying the video driver (the reports I’ve seen cite igdpmd64.sys) as the source of the BSOD….
http://www.infoworld.com/t/microsoft-windows/microsoft-pushes-another-botched-automatic-update-213802
Eli I can’t really tell you anything about that update that you probably do not know already. Microsoft states that it improves the features and performance of the following components:
Silverlight is similar to Flash, right. I would disable it for the time being and browse the Internet for a couple of days this way. If you do not encounter a site where Silverlight is missing, uninstall it. Generally speaking, it is likely that you do not need that plugin at all.
I would update to Internet Explorer 10 as some components in Windows and even third party programs make use of its rendering engine.
As usual, there is a new version of Flash, 11.6.602.180, for IE.
For once Adobe did it before Microsoft !
…
Well, Martin, that’s what I call being on time ! — Thanks.
Microsoft and Adobe are coordinating updates releases.
Did Microsoft fix those 2 zero-day holes in IE10 found at Pwn2own last week ?
Both Firefox and Chrome updates their browser in just 24 hours.
Did Microsoft fix the kernel vulnerably used to hack Windows via Chrome browser ?
It seems like Microsoft patched the kernel vulnerably:
This security update resolves three privately reported vulnerabilities in Microsoft Windows. These vulnerabilities could allow elevation of privilege if an attacker gains access to a system.
http://technet.microsoft.com/en-us/security/bulletin/MS13-027
I just wonder why it’s not selected automatically on my Win 7 64 bit and if I should apply the patch.