Shady Contacts: Hide communication with contacts in Android
You have certainly a couple of options at hand if you want to protect the data on your phone from being accessed by third parties. The pin code to unlock it is a good start, and if you prefer a more thorough approach, encryption may come to mind. Sometimes though that may not be enough. Say you are asked to unlock your phone at the airport, or forgot to lock it and have it lying around somewhere where someone can access it. Or, one of your friends wants to make a quick phone call or look something up using your phone.
That's where Shady Contacts may come in useful. The Android application hides communication with select contacts in the phone so that someone who accidentally takes a look at it will have a hard time finding those information. I would not go as far to call it a cheating application as there are other harmless uses, but it certainly will have its appeal in this regard. You can use it to make any communication private on the phone, be it with your doctor, priest, mistress or ex-boyfriend.
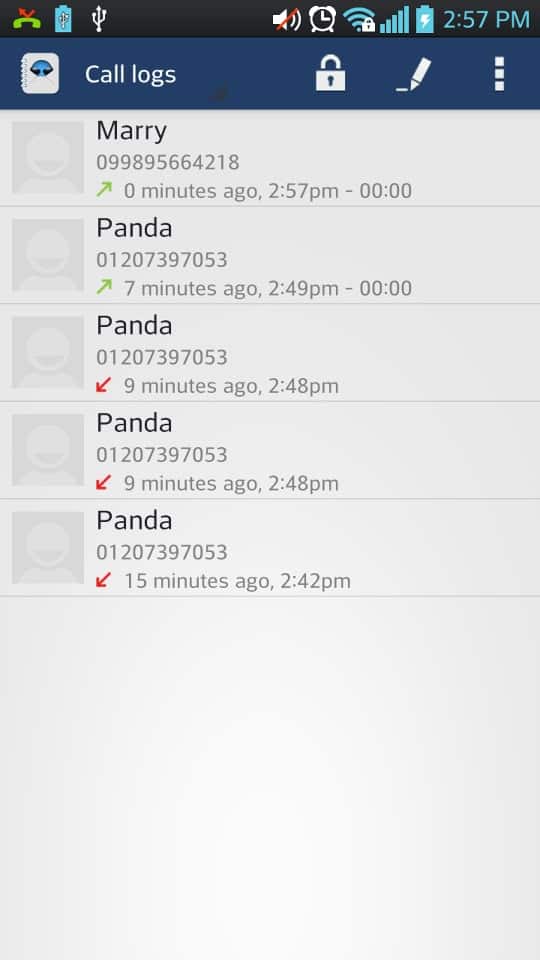
The first thing you do after installation is to create a lock pattern that protects the information on the phone. Once you have done that you can start adding contacts to the contact list. This can be done by selecting numbers from your current call log, from the existing list of contacts, or by setting up custom contacts that are not listed in the default address book.
For each contact you add this way, you can specify a name, phone number, a matching method and notification method. Once a contact has been added this way, all call logs and messages will no longer be available in stock applications as they are automatically moved to the application instead. Note that this includes the existing call and message history of that contact.
The application works more or less automatically from that moment on. You can configure it however to remove the app icon from the launch area of your phone so that no one can accidentally tap on it. While it is still protected by your unlock code if that happens, not showing the apps' icon at all may add another layer of protection to the phone. You can launch the app in this case by dialing ***123456###.
Call logs and messages can be restored at any time, or deleted permanently. There is even a feature to auto destroy the information if the wrong unlock code is entered several times.
Verdict
If you want to hide communication with select contacts on your phone, Shady Contacts is the way to go.While it certainly may be confusing at first to configure the application, you will quickly notice that it works more or less automatic after that initial configuration.



















Building robust, integrated, native applications is quickly becoming a requirement across the enterprise, but not having mobile programming skills in Objective C, Java, Javascript, and/or Mobile J Query no longer has to be a roadblock. All developers can now build, test and deliver data rich, native apps quickly and easily without any mobile programming skills required. Those developers with mobile programming experience can leverage their skills to extend development further and significantly faster than ever before. Read more here
http://bit.ly/XCLuhF
Sorry references noted-
This scare mongering by opposing fanbois has now opened the door for “security” software companies like the above mentioned to create absurd statistics to encourage people to purchase their completely unnecessary and over priced software. They most likely create this malware and post comments with links on articles like this.
The same is said about malware on Windows PC.
@llev
I have been using Android for about 3.5 year’s, have downloaded countless random apps, visited tonnes of shady websites including various hack and porn sites and NOT ONCE have I encountered any malware at all. I do admit that I am cautious and aware of certain risks which I am sure plenty of users would not be but this malware issue is just a massive media hype mostly beat up by useless apple fanboi site’s who are sick of android getting all the good press lately and who are trolling for clicks.
This scare mongering has now opened the door for “security” software companies like the above mentioned to create absurd statistics to encourage people to purchase their completely unnecessary and over priced software. They most likely create this malware and post comments with links on articles like this.
Putting the blame on security companies is just the old Microsoft way, and now yours too.
Just read the FCC vs HTC settlement regarding unpatched Android smartphones.
.. millions of HTC devices compromised sensitive device functionality, potentially permitting malicious applications to send text messages, record audio, and even install additional malware onto a consumer’s device, all without the user’s knowledge or consent. The FTC alleged that malware placed on consumers’ devices without their permission could be used to record and transmit information entered into or stored on the device, including, for example, financial account numbers and related access codes or medical information such as text messages received from healthcare providers and calendar entries concerning doctor’s appointments. In addition, malicious applications could exploit the vulnerabilities on HTC devices to gain unauthorized access to a variety of other sensitive information, such as the user’s geolocation information and the contents of the user’s text messages…..
http://ftc.gov/opa/2013/02/htc.shtm
@llev
I’d like to know where you got these stats from. I have been using Android for about 3.5 year’s, have downloaded countless random apps, visited tonnes of shady websites including various hack and porn sites and NOT ONCE have I encountered any malware at all. I do admit that I am cautious and aware of certain risks which I am sure plenty of users would not be but this malware issue is just a massive media hype mostly beat up by useless apple fanboi site’s who are sick of android getting all the good press lately and who are trolling for clicks.
References please.
One can get viruses, malwares using any platforms/OS.
If they don’t know what they’re doing.
The statistics were published trough out the year. Just read the reports in my post.
The problem with Android is the fragmented way the OS is distributed with phone makers and even telcos rolling their own versions. Neither have any incentive to patch security holes. As much as I’d prefer to stick with Android, my next phone will be from either Apple’s or Microsoft’s closed ecosystems.
Because MS has the best of both world right? (that is their crippled OS and support).
With 10% of Google’s Play store Android Applications being malware,, nothing will help.
More than 350,000 malware applications at the end of 2013. The number will grow to 1 million by the end of 2013.
It took Microsoft’s Windows 15 years to reach this level of malware.
http://www.f-secure.com/static/doc/labs_global/Research/Mobile%20Threat%20Report%20Q4%202012.pdf
http://countermeasures.trendmicro.eu/android-malware-believe-the-hype