Microsoft Security Bulletins For November 2012 Released
Today's Microsoft "Patch Tuesday" brings six security bulletins that patch vulnerabilities in Microsoft Windows, Office, Internet Explorer and the Microsoft .NET Framework. It is the first regular patch day for Microsoft's newest operating system Windows 8 and Windows RT. Both systems are affected by three of the five bulletins that affect Windows or software built-in to Windows, just like Windows XP and Windows Server 2003 are. Windows Vista and Windows 7, as well as the server based operating systems Windows Server 2008 and 2008 R2, are addressed by all five Windows-related bulletins.
Four of the Windows related bulletins have received a maximum severity rating of critical, the highest possible rating. This means that at least one version of windows is affected by vulnerabilities describes in the bulletin as critical. The fifth Windows related bulletin has received a vulnerability rating of moderate, while the Office related bulletin one of important.
The following bulletins have been released by Microsoft in November 2012:
Microsoft November 2012 Security Bulletins
- MS12-071 Cumulative Security Update for Internet Explorer (2761451) - This security update resolves three privately reported vulnerabilities in Internet Explorer. The vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-072 Vulnerabilities in Windows Shell Could Allow Remote Code Execution (2727528) - This security update resolves two privately reported vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if a user browses to a specially crafted briefcase in Windows Explorer. An attacker who successfully exploited this vulnerability could run arbitrary code as the current user. If the current user is logged on with administrative user rights, an attacker could take complete control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-074 Vulnerabilities in .NET Framework Could Allow Remote Code Execution (2745030) - This security update resolves five privately reported vulnerabilities in the .NET Framework. The most severe of these vulnerabilities could allow remote code execution if an attacker convinces the user of a target system to use a malicious proxy auto configuration file and then injects code into the currently running application.
- MS12-075 Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2761226) - This security update resolves three privately reported vulnerabilities in Microsoft Windows. The most severe of these vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a malicious webpage that embeds TrueType font files. An attacker would have to convince users to visit the website, typically by getting them to click a link in an email message that takes them to the attacker's website.
- MS12-076 Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution (2720184) - This security update resolves four privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted Excel file with an affected version of Microsoft Excel. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-073 Vulnerabilities in Microsoft Internet Information Services (IIS) Could Allow Information Disclosure (2733829) - This security update resolves one publicly disclosed vulnerability and one privately reported vulnerability in Microsoft Internet Information Services (IIS). The more severe vulnerability could allow information disclosure if an attacker sends specially crafted FTP commands to the server.
By operating system
- Windows XP: 3x critical
- Windows Vista: 4x critical, 1x moderate
- Windows 7: 4x critical, 1x moderate
- Windows 8: 3x critical
- Windows RT:Â 1x critical, 1x important
- Windows Server 2003: 3x critical
- Windows Server 2008: 3x critical, 2x moderate
- Windows server 2008 R2: 3x critical, 2x moderate
- Windows Server 2012: 3x critical
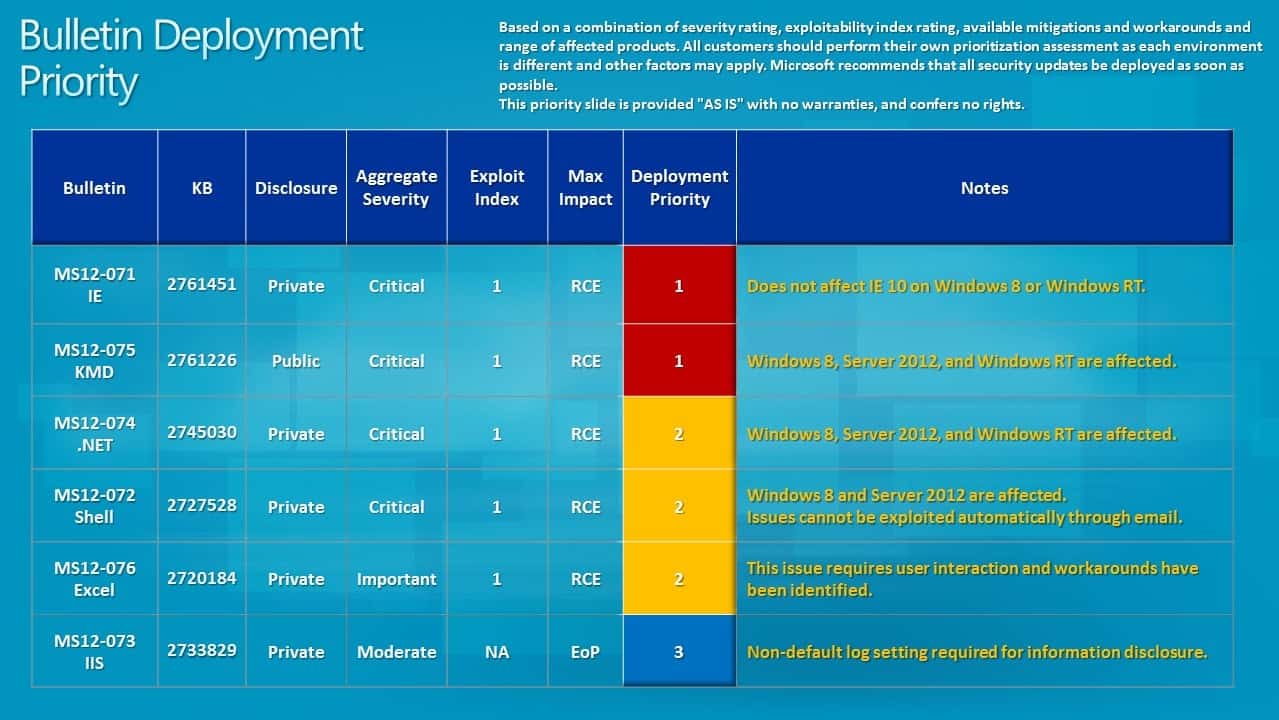
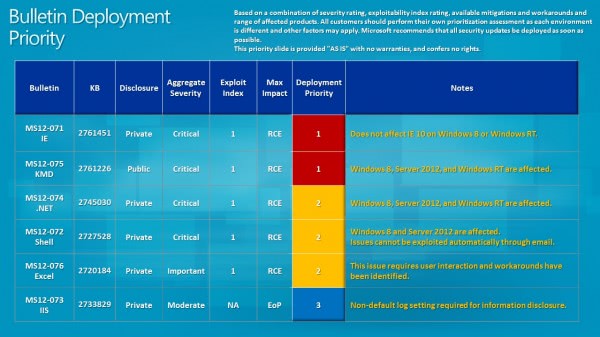
Bulletin Deployment Priority
Microsoft recommends to address bulletins MS12-071 and MS12-075 first, before bulletins MS12-074, MS12-072 and MS12-076 are deployed.
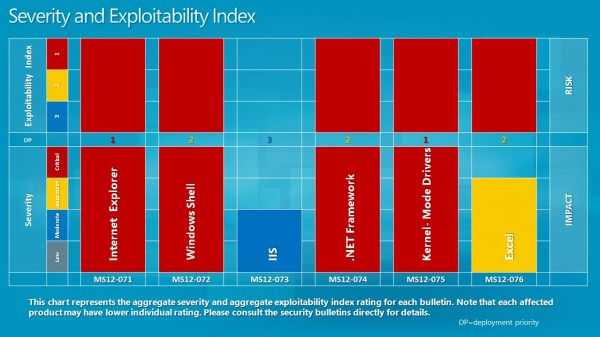
Severity and Exploitability Index
Updating
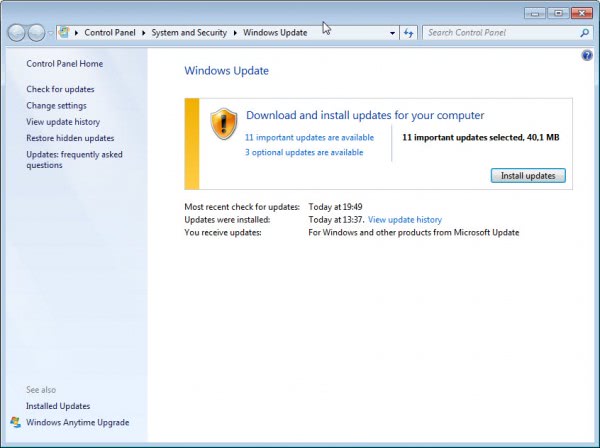
Windows Update should have picked up the available security updates by now. You may need to click on check for updates to run a manual check for updates.
Security updates are not available yet on Microsoft's Download Center. It usually takes an hour or two before all updates are released on the download center for manual download and deployment.
Advertisement





















Thanks Martin, For again making Cristal clear again where main updates ( 18 this mount) where all about.
I know you guys usually only talk about the security side of these updates, but what are these 2 optional updates, Kernel-Mode Driver Framework version 1.11 update & User-Mode Driver Framework version 1.11 update? Worth installing or not?
The Framework is for drivers only that use it. Do you have a previous version of the Framework installed? If you do not, I would not install.
Nope, I don’t think so. But if I don’t have it it’s strange that they would show up in the Windows Updates then.
This is just horrible. Copy & Paste division must be the biggest division
at Microsoft. ALL critical security updates for Windows 8, Windows RT,
Server 2012, were copied from Windows 2000/NT/XP and embedded
in Windows XP, Vista, 7, Server 2003, 2008, 2008r2.
After so many years in IT/ security, I still find this incompetence to be unbelievable.
p.s Starting next month Adobe will release Flash updates on the same date as Microsoft’s
security updates (second Tuesday of the month).