OpenDNS DNSCrypt, Increase Security By Encrypting DNS Traffic
Computer users face many dangers when they connect their computer to the Internet, from being attacked while visiting websites over malicious software to man in the middle attacks and traffic snooping.
The popular DNS provider OpenDNS has just announced that they have created another tool for users to protect themselves and their data from a range of DNS-based security threats and issues.
DNSCrypt basically does what SSL does for connections to websites. You may remember that https connections use encryption to block data snooping, for instance by users or administrators who are connected to the same computer network or have access to the network.
In the same way the SSL turns HTTP web traffic into HTTPS encrypted Web traffic, DNSCrypt turns regular DNS traffic into encrypted DNS traffic that is secure from eavesdropping and man-in-the-middle attacks.
One example of a DNS-based attack is cache poisoning, allowing attackers to redirect network clients to alternate servers. A user wanting to visit the official PayPal website could be redirected to a fake site that still shows the official domain name of the site in the browser's address bar.
DNS Crypt has been released as a preview for Windows and Mac operating systems. It only works in conjunction with OpenDNS, which means that users need to change their computer's DNS provider to OpenDNS to make use of the new security feature. The software is not changing the way clients are accessing the Internet, or making modifications to the system that makes it incompatible with Internet services.
Here are the steps to get DNSCrypt working:
- Configure your Internet connection to use OpenDNS as the DNS provider.
- Install Dns Crypt on your system
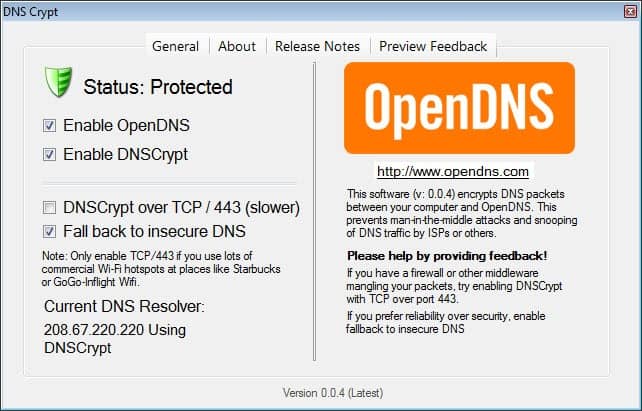
That's it. DnsCrypt adds an icon to the Windows System Tray that indicates whether the operating system is protected by the feature. A double-click, or a right-click and the selection of Open Control Center from the context menu, displays configuration options and a status screen where you can see if OpenDNS and DNSCrypt have been configured properly on the system.
You can use the configuration menu to disable either feature (it does not really make sense to disable OpenDNS only though), disable the fall back option to standard unencrypted traffic, or try the DNSCrypt over TCP 443 option should you run into firewall issues.
The source code of DNSCrypt has been made available on GitHub, so that it can be analyzed before the software is used on a system or in a network.
It needs to be considered that this is a preview release, and while we did not spot any issues running the service, it should still be seen as a beta version.
DNSCrypt can improve security further, especially in situations where you are not the person managing the computer network. If you connect to the Internet on airports, in hotels, or Internet Cafes, you may want to install and use the software to protect your system further from DNS-based attacks. (thanks Vineeth for the tip)
Update: Be aware that the program requires the Microsoft .Net Framework 3.5 to be installed on the system. You can check out our DNSCrypt configuration guide for Windows and our review of Simple DNSCrypt for Windows.




















The best and only non trace able internet connection is to make a none !!! Mad man recording all over the place !!!!
in plain english, is there a good reason for a non wifi desktop computer user, to use dns crypt and why ?
I would not use it on my desktop PC, but would consider using it when using public networks, especially in countries abroad that are known to monitor Internet traffic and all. For home users, I do not really think it is worth it right now.
Oh sorry. I meant to say CPU. Not RAM.
@ Shawn
Percentage-wise … that depends on how much RAM you have.
You failed to mention that this depends on the .Net Framework 3.5
Please be more descriptive and detailed in future reviews.
I can only add those information when I know about them. I add it right to the article.
Of course this idea is probably be useless if there are DNS leaks like OpenVPN is known to be vulnerable to.
IMO OpenDNS isn’t trustworthy. Their EULA and Privacy Policy is written in a way that enables them to keep logs indefinitely.
Encrypting as much traffic as possible is great but you must trust the ones encrypting it.
The problem with using DNSCrypt, in my view, is that it gives OpenDNS an effective means of profiling users. It gives them a tool for building a highly detailed record of your internet usage. If all of your DNS lookups go through OpenDNS (via DNSCrypt), then they know virtually every internet destination you go to anytime you use your computer. Why else would they put so many resources into this kind of project. Yes, DNSCrypt offers a useful purpose. But, at what cost?
At least, this is my perception. Am I being too cynical?
Your observation is correct. But that is true for any DNS provider that you select to use. Even if it is that of your ISP.
I am still confused about what it actually does and what exactly is it encrypting ?
It is encrypting your dns lookups, e.g. you enter http://www.ghacks.net, and the request to lookup the domain is encrypted.
So, does it mean that my ISP would not be able to trace down the site I am visiting ?
No, your ISP still sees the sites, as you make the connections. But someone trying to tamper with DNS can’t do so anymore.
It’s a good idea but a major resource hog. Yes, it uses very little RAM but the moment I launched it the process used and average of 42% Ram. And that’s consistent. Only once did it drop to about 20%.
That’s very high for a “lightweight” app.
I ran it for an hour before shutting it down.
u can help me?