Microsoft Security Bulletins For February 2012 Released
Microsoft today has released this month's security updates. A total of nine security bulletins have been released, of which four address vulnerabilities with a maximum severity rating of critical. This means that at least one Microsoft product is affected critically by the vulnerability. Six bulletins fix issues in the Windows operating system, two in Microsoft Office and one each in Internet Explorer, Microsoft Server Software, Microsoft Silverlight and the Microsoft .Net Framework.
Both Windows 7 and Windows Vista are affected by four critical and one important vulnerability each, while Windows XP is only affected by three critical and two important vulnerabilities.
Here are the bulletins for February 2012:
- MS12-008 - Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2660465) - This security update resolves a privately reported vulnerability and a publicly disclosed vulnerability in Microsoft Windows. The more severe of these vulnerabilities could allow remote code execution if a user visits a website containing specially crafted content or if a specially crafted application is run locally. An attacker would have no way to force users to visit a malicious website. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes them to the attacker's website.
- MS12-010 - Cumulative Security Update for Internet Explorer (2647516) - This security update resolves four privately reported vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted web page using Internet Explorer. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-013 - Vulnerability in C Run-Time Library Could Allow Remote Code Execution (2654428) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted media file that is hosted on a website or sent as an email attachment. An attacker who successfully exploited the vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-016 - Vulnerabilities in .NET Framework and Microsoft Silverlight Could Allow Remote Code Execution (2651026) - This security update resolves one publicly disclosed vulnerability and one privately reported vulnerability in Microsoft .NET Framework and Microsoft Silverlight. The vulnerabilities could allow remote code execution on a client system if a user views a specially crafted web page using a web browser that can run XAML Browser Applications (XBAPs) or Silverlight applications. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-009 - Vulnerabilities in Ancillary Function Driver Could Allow Elevation of Privilege (2645640) - This security update resolves two privately reported vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to a user's system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit the vulnerabilities.
- MS12-011 - Vulnerabilities in Microsoft SharePoint Could Allow Elevation of Privilege (2663841) - This security update resolves three privately reported vulnerabilities in Microsoft SharePoint and Microsoft SharePoint Foundation. These vulnerabilities could allow elevation of privilege or information disclosure if a user clicked a specially crafted URL.
- MS12-012 - Vulnerability in Color Control Panel Could Allow Remote Code Execution (2643719) - This security update resolves one publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a legitimate file (such as an .icm or .icc file) that is located in the same directory as a specially crafted dynamic link library (DLL) file. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-014 - Vulnerability in Indeo Codec Could Allow Remote Code Execution (2661637) - This security update resolves one publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a legitimate file (such as an .avi file) that is located in the same directory as a specially crafted dynamic link library (DLL) file. An attacker who successfully exploited this vulnerability could run arbitrary code as the logged-on user. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. If a user is logged on with administrative user rights, an attacker could take complete control of the affected system. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-015 - Vulnerabilities in Microsoft Visio Viewer 2010 Could Allow Remote Code Execution (2663510) - This security update resolves five privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted Visio file. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
You can access the bulletin summary here on this page.
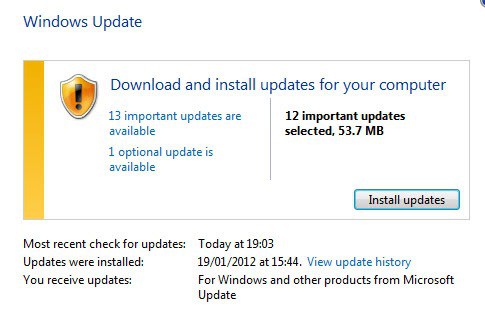
Windows Update has already picked up the new updates. You may need to run a manual check for updates though. Windows Vista and Windows 7 users can open the control panel either by pasting Control Panel\All Control Panel Items\Windows Update into an Explorer window, or by searching for Windows Update in the start menu.
A click on Check for Updates there retrieves the most recent update information from Microsoft.
Users who do not want to or cannot update via Windows Update find all security updates at Microsoft's official download repository.
Update: Microsoft has posted the Bulletin Deployment Priority chart and the Severity and Exploitability Index. Images below.
You can read up on this month's bulletins at the Microsoft Security Response Center.
Update: The February 2012 Security Release ISO Image is available now as well.
Advertisement
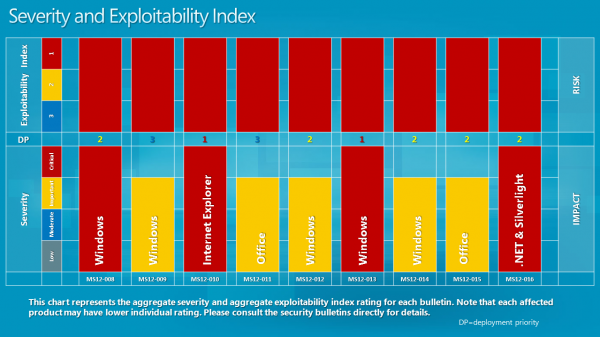
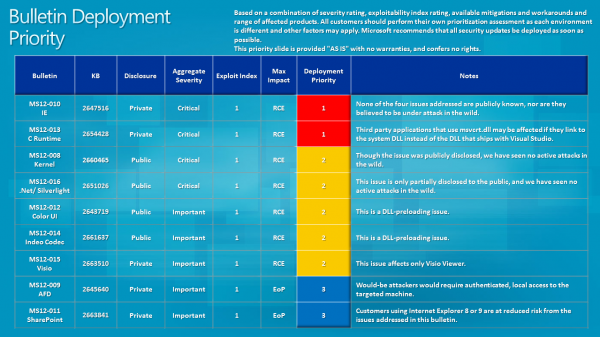

















Thanks again Martin, For again a ferry understandably (also thru the graph) update article.