How To Backup True Crypt Data To Be Prepared For Emergencies
I have been using the encryption software True Crypt for years and ran only once into a situation where I nearly lost all the data on one of the partitions. Back then the header of the volume became corrupt, but since I had a backup of the header I was able to restore it so that I could access the data on the volume again.
Generally speaking, you have three different situations that you need to be prepared for: Corrupt or overwritten headers, data loss on the hard drive and forgetting the True Crypt password.
A few years ago a friend of mine accidentally quick formatted a True Crypt encrypted partition on his computer which had the consequence that all data on the disk became inaccessible since he did not have a backup header.
To avoid those horror scenarios, backups are important. Here is what you can do to prepare for True Crypt emergencies:
True Crypt Password
If you forget the password, the data on the True Crypt volume becomes inaccessible. You have two options here to avoid this worst case scenario. You can either write down your password in a secure location, or create a backup header with a different, basic password. Both options are not ideal as it gives attackers more options to discover the password.
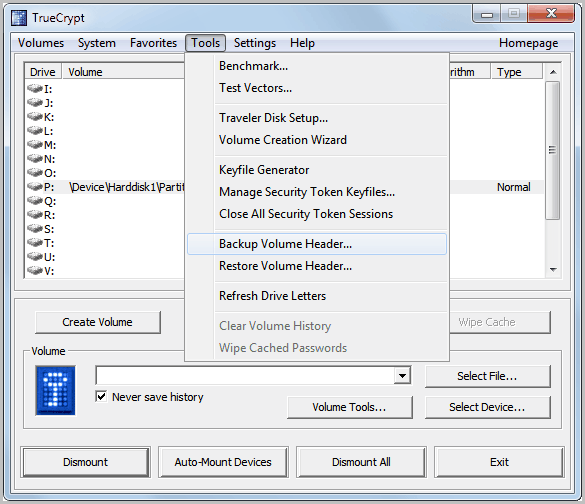
After you create a volume, back up its header to a file (select Tools -> Backup Volume Header) before you allow a non-admin user to use the volume. Note that the volume header (which is encrypted with a header key derived from a password/keyfile) contains the master key with which the volume is encrypted. Then ask the user to choose a password, and set it for him/her (Volumes -> Change Volume Password)
It is generally not advised to create a second header with a different weaker password for emergencies. You could write down the password and store it in a safe location, for instance at your parent's house or a friend's house.
Backing Up True Crypt Headers
True Crypt headers can be backed up and restored. This is important if the partition header becomes corrupt or is changed by malicious code or tools like format that modify the header. A click on Tools in the main True Crypt application window displays the options to backup and restore the True Crypt header.
The header is worthless without the password, keep that in mind. To Backup the header select Tools > Backup Volume Header after selecting an unmounted True Crypt volume (via Select File or Select Device). The Restore Volume Header function works in a similar fashion.
Backup data on a True Crypt volume
The third and final preparation is to backup the data that is stored on a True Crypt volume. True Crypt volumes are affected by hard disk failures just like any other storage device. You should therefor back up important data regularly. Since the data is encrypted, it is recommended to back up the data on another encrypted volume.
The suggested way is to create another encrypted True Crypt volume that matches or exceeds the size of the original volume. You then mount both volumes and copy the data from the old volume to the new volume. It is highly suggested that the new volume is located on another drive, local or network, or backup up on backup media like external hard drives, optical discs or the cloud / ftp servers.
The True Crypt documentation contains a guide on how to backup both standard True Crypt volumes and system volumes.
Closing Words
These three steps ensure that you can restore data or the full True Crypt volume in case of corruption or hard drive failures. Anything to add? Let me know in the comments.
Advertisement












Hi,
I don’t understand some things so I hope you or someone else can sort this out.
1. Should you also back up the header if you have chosen to make individual truecrypt files (containers) and not encrypted an entire hard drive?
2. Can’t you backup the truecryptfiles/containers through regular synchronization backups (copying the truecryptfiles) instead of manually move the files in the original truecryptfilen to another backup truecryptcontainer?
Can you make any suggestions on how I can encrypt my data properly?
I have four hard drives. HD A, HD B, HD C and HD, P. HD A is always connected to the computer while the HD B and C are synchronized with the HD A and moreover, this is done alternately as HD B and C are not in the same location. HD P is a portable small hard drive that I always carry with me with active files I work with. They are also backed up on HD A and Dropbox. HD A, HD B, and HD C, I look more like storage places for materials I have worked with that I then want to save (archive). Most material I want encrypted.
3. Should I stick to whole hard drive encryptions on HD A, B and C, or should I split the contents of several truecrypt containers / files (‘create an encrypted file container’)? Or do you have other tips? And of course I need backup on the encrypted data if a file becomes corrupted.
4. If a file becomes corrupted and I make a backup automatically via a synchronization program how can I go about preventing it to multiply the corrupted file in versions that are saved? The versions are often a maximum number and finally writes the oldest one over with the new one. My thoughts is to do a full backup (the first files are saved on all hard disks in order to have that first backup (version) when you know that everything worked, and then not touch this. Is this the wrong way of thinking or is there something smarter?
Thank you for your reply Martin!
I’m not interested in encrypting my computer and its file system, only external hard driver’s folders/files. The external hard drives work as an archive but is updated from time to time when single file is submitted into the archive.
The problem as I see it is to have many truecrypt containers with passwords to keep track of the various genres which folders are divided in. But at the same time I have to have HD A (which has the ‘new’ information all the time) to backup/copy files to HD B and HD C. If HD A is entirely encrypted as an external hard drive how can I then backup that one to HD B and HD C automatically?
Other problems I see with truecrypt containers that hold different folders instead of encrypting the entire hard drive is to make changes in a container. If I change a file in a truecrypt contain that holds 30GB of files my program that copies the truecrypt container to a different hard drive have to do a full reload as the program doesn’t know what in the container that has changed = might be time-consuming for daily backups.
I have, for example these folders with files to be encrypted:
– Personal 15GB
– Photo 202GB
– Various small backups 10GB
– Media 503GB
(all above should be encrypted)
– Unencrypted 86GB
What is the best solution that allows me to automate backups and making sure that they don’t take several hours to backup?
Well you could in theory sync the file contents once the containers are mounted, which would mean that only changed files are transferred. The same is true if your main hard drive is fully encrypted. You can still sync but need to mount first, not a big problem since you cannot boot the operating system if you do not encrypt first.
I personally do not like juggling around with multiple containers. So you might want to consider going full encryption on your main hard drive. Syncing should not be a problem in this case. You should then either mount the backup locations as well before you start syncing, or use full partition encryption there as well. Still, you would need to mount before you start the synchronization.
Nin, lots of questions.
1. Yes, you need to backup, as the header is part of the True Crypt container in this case. You could alternatively make a backup of the container, but remember that you need to make a new backup whenever the contents change.
2. Yes you can do that. Proper encryption depends on what you want to do. Do you want to encrypt all of your data, or only containers that contain your important files.
3. This again depends on your usage. I prefer full hard drive or partition encryption as it is easier to handle, and ensures that all data is encrypted (including temp files on the hard drive).
4. You cannot, unless you spot the corruption manually before synchronizing the container.
“Since the data is encrypted, it is recommended to back up the data on another encrypted volume.”
——
Huh? Why do I need to backup an already encrypted data file to an encrypted volume?
Right now, all I do is image the partition that the encrypted volume is on. Why is that not a good practice?
Jojo, sure you can create a backup of the full partition or hard drive. Good point.
Hi its a nice tip but i have some few questions hope you have some suggestion
I have a 500Gb external HD ntfs FS. recently i partition it with ext4 so i used gparted linux app. After i started gparted partition tools it took almost a day of running so i decided to kill the app therefore unfinish gparted job. although it seems it create a partition table an ntfs and an raw or no FS partiton. the problem is when i open my truecrypt volume its shows error like undetected or no volume detected. i forgot the exact error msg but the meaning in the truecrypt wiki is corrupt header. I dont have a backup header. my question is..is it possible that the header just change and the password combination change also due to the gparted app(relocating the bytes location from the HD) . Im certainly sure for my password so there no chance a wrong password. Does the data of the truecrypt volume intact for some reason the gparted or partitioning rearrange the HD geometry ‘Is it possible that this is the cause that i cannot open my truecrypt colume”
Thanks for the reply if any.
Well the password does not change unless you did change it. You can try the following. Select the device in True Crypt, then Tools > Restore Volume Header and in the popup window Restore the volume header from the backup embedded in the volume. This is your last chance. If it fails, the data is lost without a backup.
Hi i already try about the procedure you mention restore the backup header from the built-in backup in the volume but still no luck..
For the best of both worlds, use a TrueCrypt volume in combination with DropBox.
You’ll get *very* secure data storage automatically synchronized with all you computers, *and* you’ll get reliable automatic backup in the cloud (as they use Amazon servers), *and* you’ll get incremental backup with automatic revisions…
As long as your TrueCrypt volume isn’t too large, this should work great.
Atle, great tip, provided that the Dropxbox storage is large enough (my TrueCrypt volume is 2TB, hehe).